Identifying Exploits for Industrial Control Systems
Analysis Summary
Using Recorded Future, you can identify evidence of public exploits in cases where official resources such as ICS-CERT or the National Vulnerability Database claim no public exploits are available or lag weeks behind.
Identifying the existence of publicly traded exploits is a critical component of patch prioritization.
This is particularly relevant to patching industrial control systems, as system downtime can directly impact an organization’s bottom line.
Recorded Future’s Web intelligence platform applies natural language processing and machine learning to the surface, deep, and dark Web (beta). This allows a user to identify evidence of new exploits for their tech stack, in real time. Recorded Future’s tailored alerts can push this information via email or integration, saving considerable time and effort. In the following, we pull mentions of exploits from general Web discussion of a vulnerability affecting an industrial control system (ICS).
Background
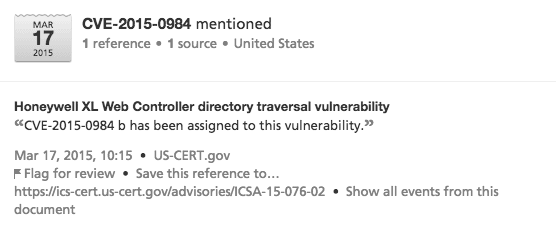
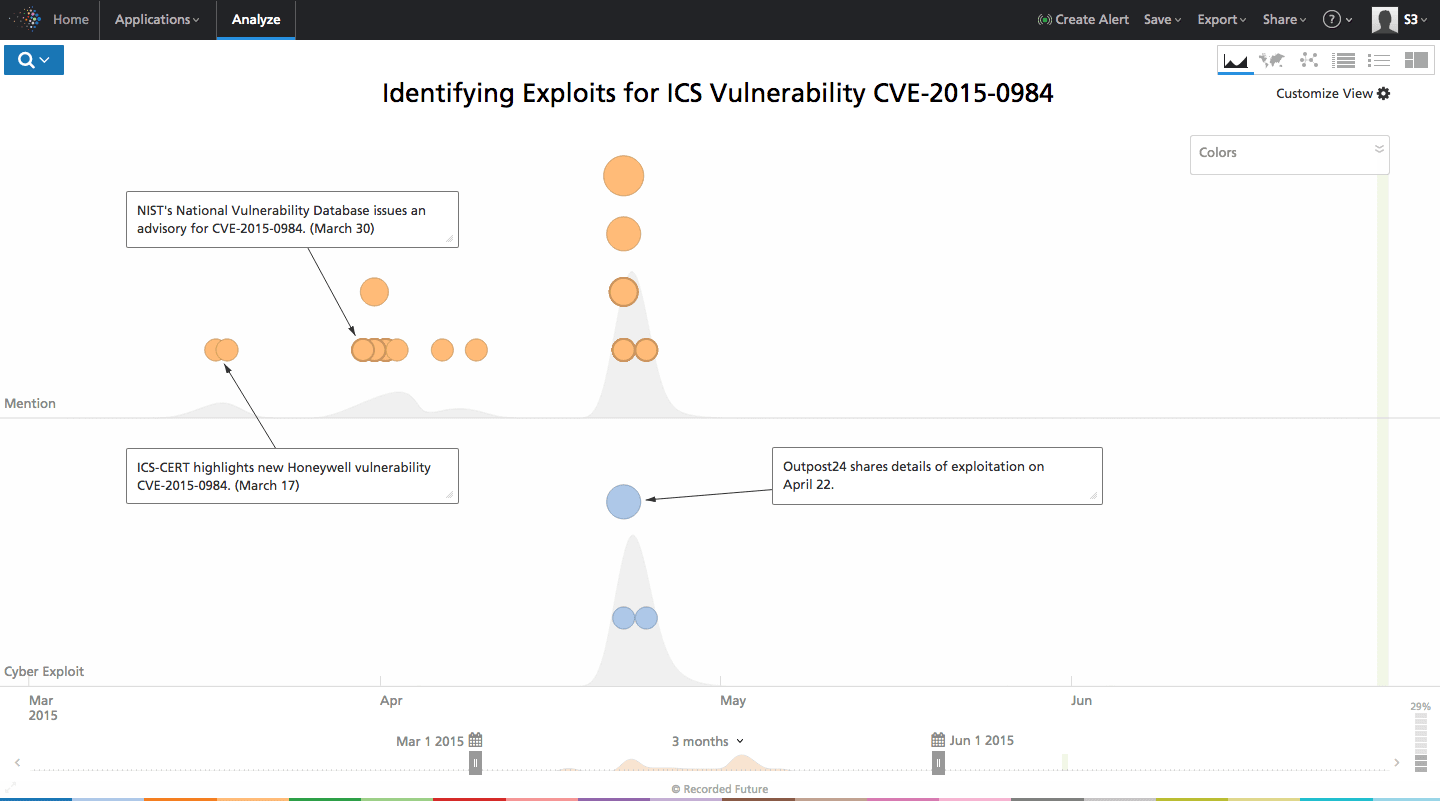
On March 17, 2015, ICS-CERT issued an Advisory (ICSA-15-076-02) for a Honeywell XL Web Controller directory traversal vulnerability. The affected products, XLWeb controllers, are Web-based SCADA systems deployed across several sectors including critical manufacturing, energy, water, and sewage systems. This vulnerability was assigned CVE-2015-0984 and identified by Martin Jartelius of Swedish vulnerability management firm Outpost24.
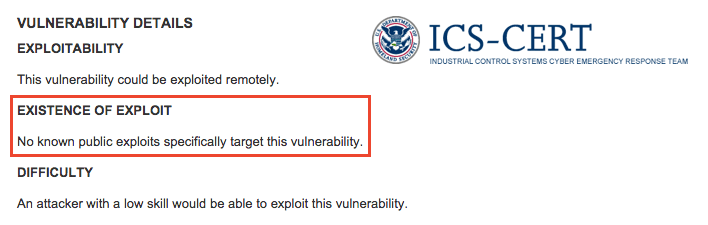
As of June 15, 2015, this ICS-CERT Advisory states that “… no known public exploits specifically target this vulnerability.”
Prior to June 3, 2015, the National Vulnerability Database (U.S. government repository of standards based vulnerability management data) contained no references to a publicly available exploit.
As of June 15, 2015, searching CVE-2015-0984 in Recorded Future identified 52 references to the vulnerability, including the issuance on March 17:
Applying Recorded Future’s Cyber Exploit event type to the query allows a user to identify the references specifically discussing an exploit for this vulnerability.

The query quickly identifies an exploit for CVE-2015-0984, posted April 22, 2015 – 36 days after the issuance of the Advisory. Outpost24’s Jartelius, who originally identified the vulnerability, now felt comfortable sharing details of the exploitation as it was “more than a month after disclosure by the ICS-CERT” and a patch was available. This proof of concept was posted to seclists.org (a Web archive of full exploit disclosure mailing lists) and shared via forum postings, Twitter, and a public-facing Facebook page over the next two days.

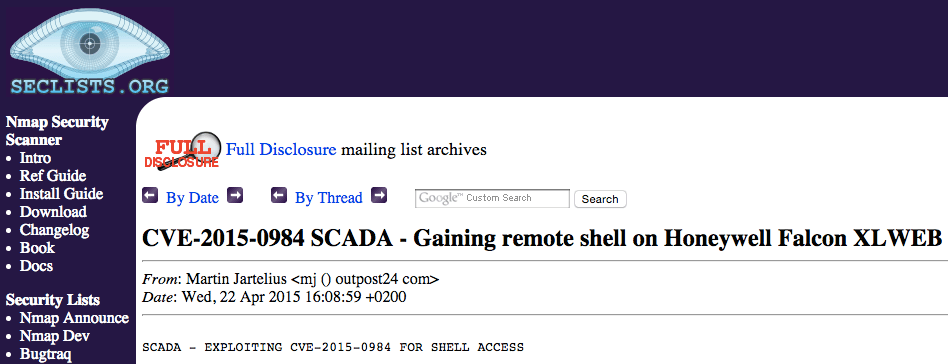
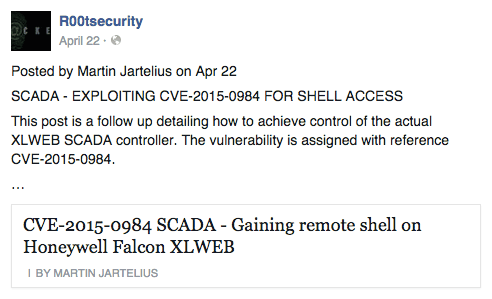
Click image for larger view
Potential Impact
Outpost24 claimed that exploitation of CVE-2015-0984 enables… “full system compromise of the SCADA system, leading to a remote access to the SCADA networks where the devices are deployed, as well as… (potentially) the entire network.” Jartelius notes that “… such a setup puts the organization at risk for suffering the same form of targeted attacks as Target was a subject of, where attackers entered via a network connected HVAC system.”
Conclusion
Incomplete information and considerable lag plague official sources of information for vulnerabilities. The evidence of publicly available exploits is a critical component of patch prioritization. Recorded Future’s Cyber Exploit event type and real-time alerting made users aware of this exploit minutes after it appeared on the open Web.
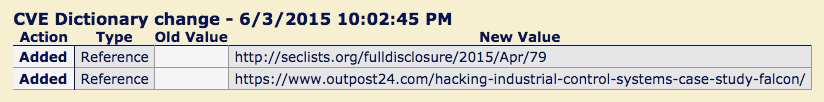
The National Vulnerability Database’s most recent June 3 update included links to the identified seclists.org posting and Jartelius’s original case study on outpost24.com. This is almost two weeks after the exploitation details were posted and extensively shared on social media and forums.
Now What
Recorded Future alerts can be tailored to company specific technology. As demonstrated here, they can be further tailored to mentions of exploits. Minutes, or in some cases, just seconds after the first appearance of an exploit for a new vulnerability, a user will be alerted.

Pushing real-time updates to threat intelligence analysts can counteract the inconsistent updating and considerable lag tied to official resources. Identifying the existence of publicly traded exploits is a critical component of patch management.
In the case of ICS, this must be carefully gauged, as system downtime can directly impact an organization’s bottom line. Similarly, system security is critical for the health and safety of employees who work alongside machines and processes controlled by Web-connected machines.
For more information on Recorded Future’s Cyber Exploit event type, please see our “Week to Weak: The Weaponization of Cyber Vulnerabilities” report.
Related News & Research



