New Research Shows Most Vulnerabilities Exploited in About a Week
Recorded Future research published in “Week to Weak: The Weaponization of Cyber Vulnerabilities” identified the short window of time system administrators have before announced software vulnerabilities become a real threat to their operations. As noted in this research, it takes a little more than a week for an exploit leveraging a new CVE to be detected on the open web.
The report, which can be downloaded here, can aid system administrators and cyber threat intelligence managers in their prioritization of patches by helping gauge the time it takes for vulnerability exploit code to appear on the open web.
Analysis contained in “Week to Weak” was made possible by Recorded Future’s new Cyber Exploit event type. Cyber Exploit is the event type used to represent when a known vulnerability (i.e. one which has been assigned some cyber vulnerability identifier such as a CVE or a Microsoft Security Bulletin) has been exploited, either maliciously or as a proof of concept (PoC) to illustrate its potential.
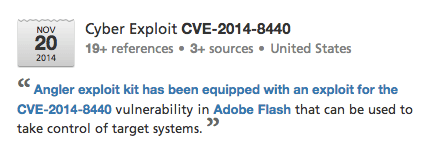
Use of this new event type can support analysis or alerts by linking to newly posted exploit code, or highlighting the use of the vulnerability by malware including exploit kits.
Related
