How SITA Uses Threat Intelligence to Protect the Aviation Industry
Cybersecurity is often likened to a game of chess — attackers and defenders locked in a constant strategic battle, with each side trying to outsmart the other. But one security expert describes the “game” in slightly different terms.
In October 2019, we held our eighth annual RFUN: Predict conference in Washington, D.C. During the conference, attendees were treated to a presentation on intelligence-led cybersecurity by David Ockwell-Jenner, senior manager of security threat and operational risk management (STORM) at SITA, a multinational IT and telecom provider to the aviation industry.
In case you haven’t heard of SITA, Ockwell-Jenner provided a succinct explanation of what they do: “We have technology in nearly every major airport in the world. Almost every aspect of an air travel journey at some point passes through one of our systems.”
During his presentation, Ockwell-Jenner explained how SITA has built its entire cybersecurity program around threat intelligence, and what benefits they have seen as a result.
Playing Chess With Cheaters
SITA’s experience with cybersecurity is unusual because — unlike most organizations — they do business with almost every country, including some traditionally seen as home to significant cyber threat activity. This poses a variety of challenges, as Ockwell-Jenner explained:
“We can’t think about ‘good guys and bad guys,’ because we do business with everyone. Instead, we think in terms of people, some of whom occasionally do bad things. It can be challenging because some of the defensive strategies that other organizations can use don’t work for us — we can’t block traffic just because it comes from a specific location.”
And when you’re responsible for cybersecurity under these conditions, the chess analogy given above doesn’t quite ring true. That’s why Ockwell-Jenner thinks about it in slightly different terms:
“Cybersecurity is often likened to a game of chess. But really, it’s more like playing multiple games of chess at the same time, without knowing all the rules — and the opposing team is always cheating.”
This description matches the experience of most cybersecurity practitioners. Just when you think you’ve worked out what threat actors are doing, they change tactics. Critically, there’s no “fairness” in the game being played — threat actors will do anything to achieve their objectives, and security experts have no choice but to roll with the punches.
According to Ockwell-Jenner, this is where threat intelligence must enter the picture, as a tool to help security teams identify what their opponents are going to do, so they can prepare for it in advance.
Building a Cybersecurity Program With Threat Intelligence
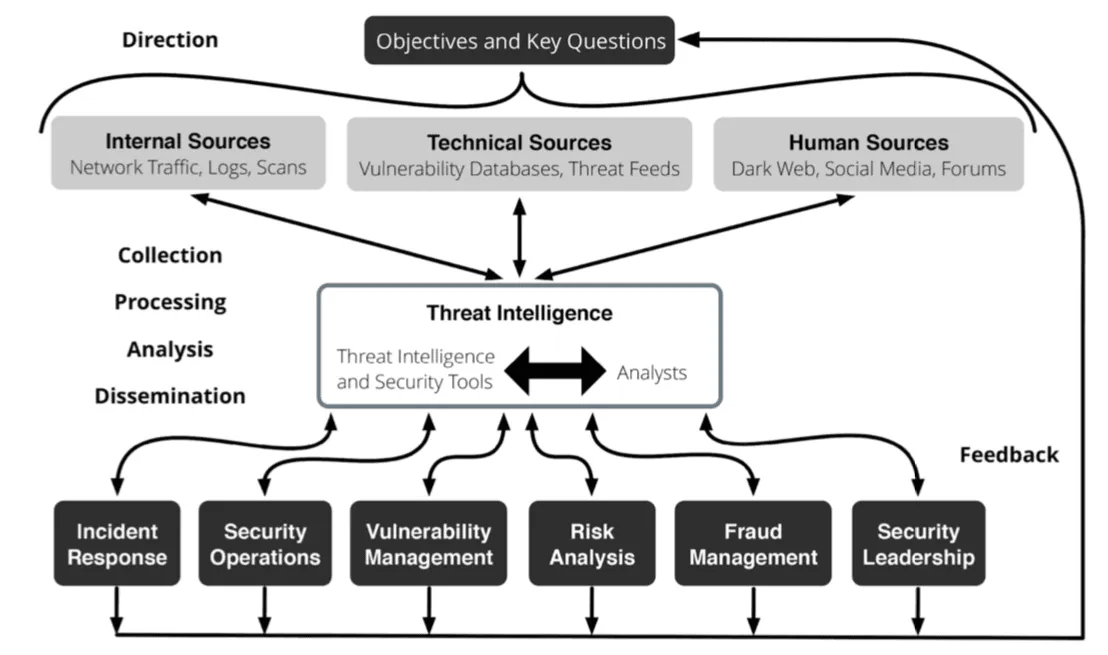
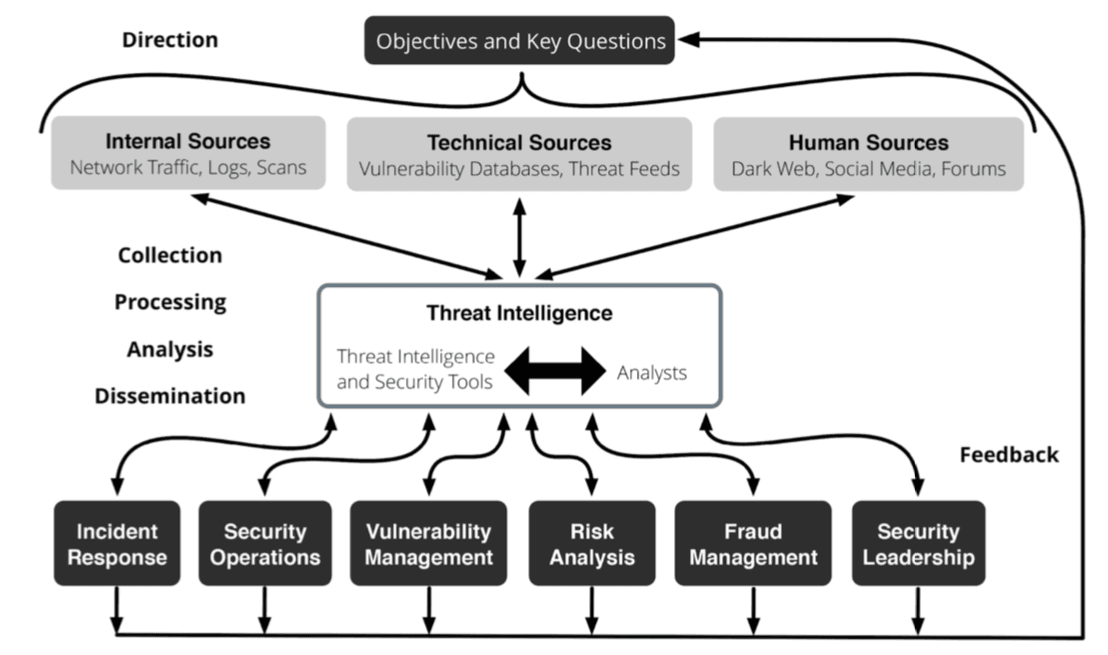
Ockwell-Jenner explained that threat intelligence is not something that sits off to the side of a cybersecurity program — it is the program.
Source: Recorded Future
Since no organization has a big enough budget for all the technology, people, and processes needed to completely secure against all threats (if that were even possible), they’re forced to prioritize. Specifically, they have to determine which threats pose the greatest risk to the organization and mitigate those first.
Since the aviation industry is renowned for its low profit margins, SITA definitely doesn’t have the luxury of wasting resources on low-risk threats. They need to determine which threats consistently pose the greatest risk and design a security program that addresses them.
SITA’s Intelligence-Led Program
Ockwell-Jenner explained during his presentation that threat intelligence plays a central role in every aspect of SITA’s cybersecurity program. SITA consumes and shares threat intelligence with a variety of partners from across the industry and beyond, including Recorded Future.
1. Incident Response
In incident response, time is critical. The longer it takes to identify and triage a threat, the more damage could be done. To illustrate the impact of threat intelligence on their incident response function, Ockwell-Jenner told a story.
One of SITA’s customers had contacted them because something seemed to be wrong in their environment. Since SITA had a server inside the customer’s environment, they agreed to take a look. After a brief search, they identified a malware — ZombieBoyTools.exe — which nobody on the team had encountered before.
On running the malware through Recorded Future, it appeared to be linked to an APT called Iron Tiger. SITA routinely tracks APTs that are active in the aviation industry, but had not previously been aware of this group. Vitally, Recorded Future also provided a variety of contextual data on the malware, which included a hash value that could be used to hunt for signs of compromise within the customer’s environment.
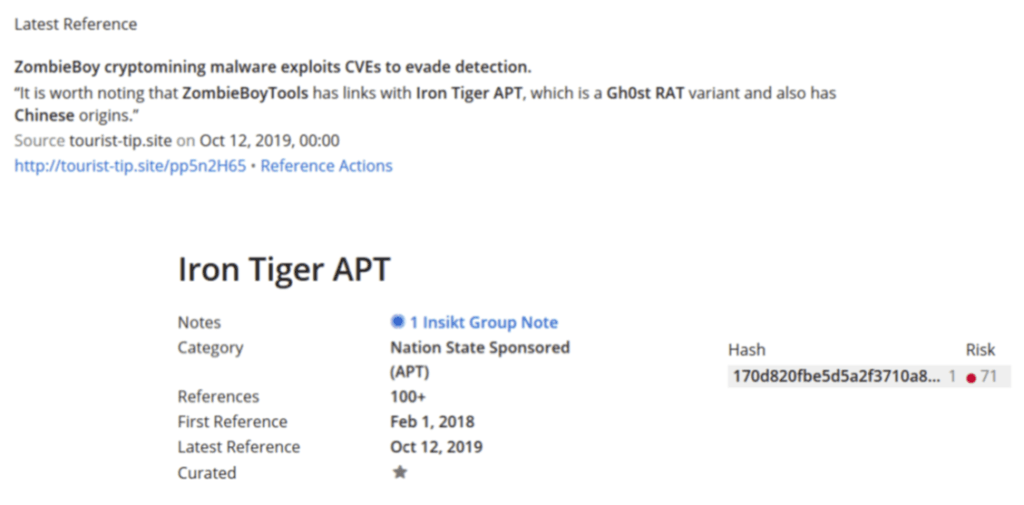
Source: Recorded Future
“We started finding more and more things within their environment that shouldn’t be there,” Ockwell-Jenner explained. “When we spoke to the customer, they thought maybe one or two machines had been compromised. We broke the news to them that they had a much larger problem, and advised them to get professional help. So they called in the big IR teams, did their investigation, and the rest is now media history.”
Of course, not every incident response story has a happy ending. This one ended in a highly publicized breach; but by using high-fidelity threat intelligence from Recorded Future, the team at SITA were able to very quickly identify and scope their customer’s security incident, and provide timely advice on what to do next.
2. Security Operations
One of the biggest problems faced by security teams is the huge volume of incoming alerts and indicators. We’ve written about this problem many times before, and during his presentation, Ockwell-Jenner explained how threat intelligence helps the SITA team identify and process only the most valuable indicators.
SITA faced the same challenge faced by all security teams — they had too many indicators, and not enough capacity to process them effectively.
“Everybody has indicators. Hands up if you would like more indicators? Nobody wants more indicators … They want better indicators.”
To solve this problem, the team needed context. This is where threat intelligence comes in — Recorded Future integrates directly with the team’s security analytics platform and automatically enriches indicators with context, further information, and other relevant indicators. So, whenever a genuine security incident does arise, the team quickly develops a full picture of what’s going on.
3. Vulnerability Management
Historically, SITA — like many global organizations with complex IT environments — had challenges with its vulnerability management program.
This is understandable when you realize that SITA has just 5,500 total staff, and runs IT in nearly every airport in the world. Doing everything simply isn’t an option — they have to be selective.
Initially, Ockwell-Jenner’s team tried to solve the problem by making a “big deal” about critical vulnerabilities, and doing their best to capture the attention of the teams responsible for vulnerability management.
“Our definition of critical at that time was, ‘Is it in the nightly news?’ So, Heartbleed, Meltdown, and so on,” he explained. “Which was good. It got people motivated, and they started to deploy things. Unfortunately, it also created a monster. Unless we made a fuss about something, patching was handled inconsistently.”
Of course, being in the nightly news doesn’t necessarily make a vulnerability high-risk for a specific organization. To rectify this, the SITA team adopted threat intelligence from Recorded Future to help them identify and prioritize the highest risk vulnerabilities for their organization. If a vulnerability poses a real threat — for example, because it’s being actively exploited — it’s prioritized. If it doesn’t, it’s left to the business as usual VM program.
4. Risk Management
Ockwell-Jenner spends a lot of his time advocating for cybersecurity as a critical component of business resiliency. When it comes to cybersecurity in the aviation industry, bad things do happen.
“You would not believe the cost when an airport goes down, or a flight is delayed,” he explained. “When most businesses have an outage, I don’t want to downplay it — it’s inconvenient. If an airline has an outage, there’s a very strong chance they will go out of business.”
To illustrate his point, Ockwell-Jenner described the events that followed a ransomware attack on Bristol airport in the U.K. The attack had taken down all of the flight display screens, so customers had no idea which gate to go to. Attempting to solve the problem, staff set up a WhatsApp group for passengers so they could broadcast gate announcements.
“There were staff running around with clipboards trying to tell people where to go. This is where the risk lies in our industry. We’ve become completely reliant on technology for even the simplest things.”
SITA operates on behalf of the aviation industry and works to help other companies understand the threats they face. Threat intelligence is what fuels their analysis and provides the content for the security communications they send.
5. Fraud Management
One of the longest-running security issues for the aviation industry is air mile fraud. This is where organized criminal groups use air miles to launder money, by buying them and selling them on. Cybercriminals are also involved in stealing air miles — regardless of which company issued them — because they’re easy to sell.
Naturally, airlines are always looking for ways to identify and stop these activities. To address this need, SITA uses Recorded Future to track phishing scams, domain squatting, and imposter websites that are used by cybercriminals to harvest login credentials for official air mile accounts.
Solving the Right Challenges With Threat Intelligence
According to Ockwell-Jenner, of all the ways that SITA uses threat intelligence, its role in security leadership is most important.
Threat intelligence is one of the main mechanisms SITA uses to identify its top threats and challenges. And as a natural follow-on from this, they also use it to determine and justify cybersecurity resource allocation. This is what Ockwell-Jenner calls “intelligence-influenced investment.”
“We can’t defend against everything. Nobody has the resources for that. But we can figure out what’s likely to happen to us and then defend against that.”
This is the core of Ockwell-Jenner’s approach to cybersecurity. During his presentation, he repeatedly stressed the importance of security teams working to solve the challenges they have, not the ones they know how to solve. Many teams do the latter because it’s easy, but it adds little value to a security program. Instead, they need to focus on recognizing their organization’s most pressing threats and challenges, and identifying the best available solutions to them.
“None of this is rocket science,” he summarized. “We have a small team at SITA, and a very large footprint to cover. If we can pull it off, I’m sure many of you can too.”
Related