Identify, investigate, and prioritize cyber threats
Identify your threat landscape and take action on relevant threats to prevent and mitigate attacks.

More than 2,200 cyber attacks occur daily. Which are relevant to you? Recorded Future's Threat Intelligence powers your company with actionable intelligence on your threats. Enable your security team with capabilities to search, identify, alert, and prioritize threats in real-time and reduce risk to your business.

Identify your threat landscape to reduce risk
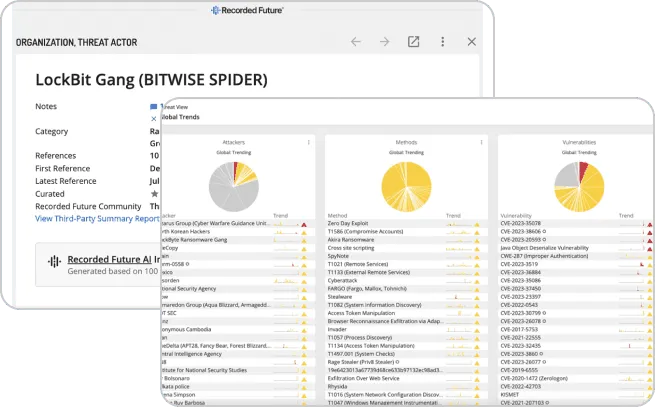
Enable your cyber threat intelligence (CTI) team and security analysts the ability to easily search relevant threats, and quickly obtain the intelligence you need to protect your organization.
Confidently prioritize relevant threats
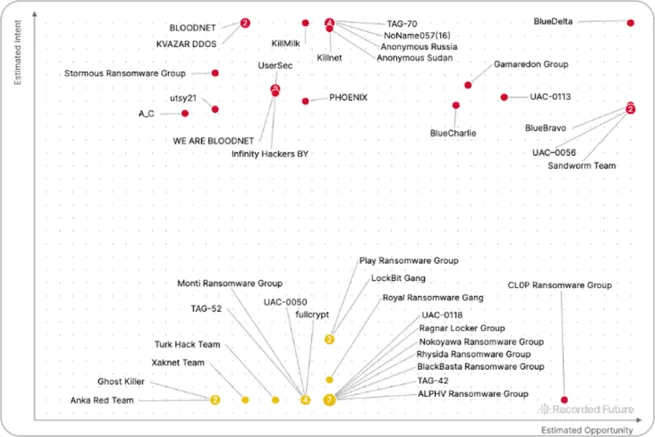
It's difficult to identify which threats are relevant when you are dealing with thousands of alerts daily. Quickly gain insights into your industry, geography, and build risk parameters to focus on relevant threats enabling your analysts to focus efficiently and with confidence.
Enhance remediation and mitigation of threats
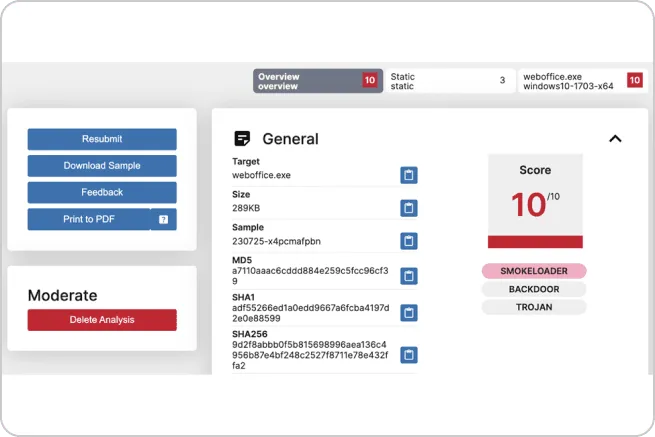
With context like IOCs, sandbox analysis, and hunting packages, get the “so what” you need to take action, power remediation and mitigate threats directly or integrate the intelligence into your existing security tools.

Key capabilities
- Threat landscape visualizations
- Advanced search capabilities
- Curated intelligence on threat actors, malware families, and IOCs
- Ransomware dashboard
- Real-time alerting and notification
- Integrations and API endpoints


