Dos and Don’ts for Charting Your Security Intelligence Journey

Editor’s Note: The following is an excerpt from the second edition of our popular book, “The Threat Intelligence Handbook: Moving Toward a Security Intelligence Program.” Here, we’re looking at chapter 12, “Your Threat Intelligence Journey.” To read the entire chapter, download your free copy of the handbook.
For many organizations, moving toward a comprehensive security intelligence philosophy begins with threat intelligence. Yet as we’re exploring throughout this series, threat intelligence is extremely versatile with myriad applications. This means your intelligence journey will also be unique, and should reflect your organization’s specific needs and goals.
Perhaps you’ve decided to start small by gaining some actionable context around an indicator of compromise on your network, or by integrating elite security intelligence with one of your existing security tools to achieve some quick wins. Or, maybe you’re utilizing intelligence to compile a 100,000-foot-view report for your executive team and board to help them understand the organization’s overall security risk posture.
The right intelligence empowers security teams throughout the organization to make better, faster decisions and amplify their impact — from security operations and incident response, to vulnerability management, to fraud prevention, risk analysis, and other high-level security staff.
As you chart your organization’s unique security intelligence journey, there are some “rules of the road” to follow that will enable you to stay the course and avoid potential roadblocks and detours. We’ll explore these do’s and don’ts in this chapter, which has been edited and condensed for clarity. Read on to review ways to clarify your intelligence goals, examine key success factors that contribute to effective intelligence programs, and find helpful tips for getting started.
One of the themes we’ve focused on throughout our book is how versatile threat intelligence can be. Threat intelligence can be as simple and immediate as some quick context around an indicator of compromise on your network, or as broad as a report meant to influence policy at an organizational level. Many of the chapters of this book are spent looking at the various ways different security teams can apply threat intelligence — how it helps incident response teams find threats faster, vulnerability management teams prioritize risks, and security leadership make planning and investment decisions, to name a few.
What this suggests is that anyone starting on a journey toward incorporating threat intelligence into their security program needs to have their final destination in mind before they take their first step. What teams in your organization will benefit the most? What are the types of threat intelligence your organization should focus on producing? And what threat intelligence solutions will best fulfill these needs?
This can feel like a daunting task with so many variables to consider. When assessing the qualities of different solutions, it’s best not to think of them as a vehicle for delivering these results, but as a road toward your goals. The purpose of a road is to mark a clear path between two places. There are certain universal qualities that make for a good road: they should make it safer and easier to get from one place to another by providing context in the form of signage and road markings, and they should reduce friction to let you travel more efficiently, for example. Bad roads are convoluted or poorly maintained. They slow you down or mislead you, or they’re unsafe to travel on. But no matter what, roads accommodate travelers of all speeds and destinations.
There are some basic, universal qualities to look for in a good threat intelligence solution, too — “rules of the road,” as it were. In this chapter from our new book, “The Threat Intelligence Handbook,” we’ll explore what to look for.
Don’t Start With Threat Feeds
In the first chapter, we discussed several common misconceptions about threat intelligence, including that it is mostly about threat data feeds. In fact, many organizations begin their threat intelligence programs by signing up for threat data feeds and connecting them with a SIEM solution.
This may seem like a good way to start because many threat data feeds are open source (and free), and the technical indicators they deliver appear useful and easy to interpret. Since all malware is bad, and every suspicious URL could be used by an attacker, the more clues you have about them the better, right?
Well, in reality, the vast majority of malware samples and suspicious URLs are not related to current threats to your enterprise. That’s why feeding large volumes of unfiltered threat data to your SIEM will almost certainly create the kind of alert fatigue we examined in Chapter 3.
Clarify Your Threat Intelligence Needs and Goals
Because threat intelligence provides value to so many teams in cybersecurity, it is important to develop priorities that reflect the overall needs and goals of the enterprise.
Answer These Questions
Rather than assuming that any one team, data source, or threat intelligence technology should have priority, you should develop a clear set of goals by determining the needs of each security group in your organization and the advantages that threat intelligence can bring to them.
Begin by considering these questions:
What are your greatest risks?
What are the ways that threat intelligence can help address each of those risks?
What is the potential impact of addressing each risk?
What gaps need to be filled by information, technology, or human resources to make threat intelligence effective in those areas?
Answering these questions will help you clarify where threat intelligence can deliver the biggest gains in the shortest time. It will also guide your investigation of which threat intelligence sources, tools, and vendors can best support you and what staff you need to strengthen your program.
Identify Teams That Can Benefit Most From Threat Intelligence
Teams across your security organization can benefit from intelligence that drives informed decision making and offers unique perspectives. Intelligence that is comprehensive, relevant, and easy to consume has the potential to revolutionize how different roles in your organization operate day to day. The image below shows examples of how teams inside organizations can use threat intelligence.
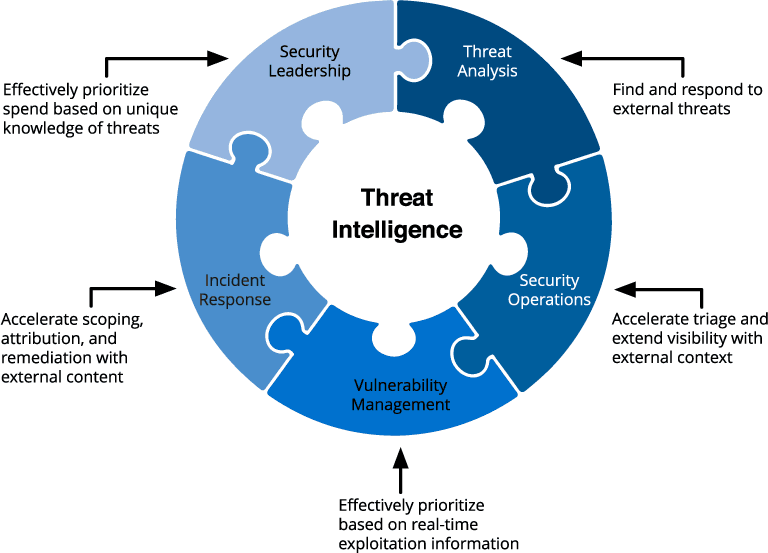
How security teams use threat intelligence.
When determining how to move your threat intelligence strategy forward, it’s important to identify all the potential users in your organization and align the intelligence to their unique use cases.
Key Success Factors
We have observed several factors that frequently contribute to effective threat intelligence programs.
Generating Quick Wins With Monitoring
Monitoring threat information can provide quick benefits with relatively modest investments. The key is to look for a few types of data that are particularly meaningful for your business and information security strategy and will help you anticipate emerging threats or provide early warning of actual attacks. Your activities might include things like:
Checking for new vulnerabilities that affect your most important software packages, servers, and endpoints
Tracking threat trends that pose potential risks to your business operations
Watching for any leaked corporate credentials, data, or code appearing on public or dark web sites
There are probably a few data types that are vitally important to your business and that you can monitor without investing in new infrastructure or staff. Monitoring them can generate quick wins, demonstrate the advantages of threat intelligence, and build enthusiasm for the program.
Automating as Much as Possible
Effective threat intelligence programs typically focus on automation from the beginning. They start by automating fundamental tasks like data aggregation, comparison, labeling, and contextualization. When these tasks are performed by machines, humans are freed up to work on making effective, informed decisions.
As your threat intelligence program becomes more sophisticated, you may find even more opportunities for automation. You will be able to automate information sharing among a larger group of security solutions and automate more workflows that provide intelligence to incident analysis and response and fraud prevention teams. You will be able to offload more of the “thinking” to your threat intelligence solutions, for example, by having the software automatically correlate threat data and produce risk scores.
Integrating Threat Intelligence With Processes and Infrastructure
Integrating threat intelligence tools with existing systems is an effective way to make the intelligence accessible and usable without overwhelming teams with new technologies.
Part of integration is giving threat intelligence tools visibility into the security events and activities captured by your other security and network tools. Combining and correlating internal and external data points can produce genuine intelligence that is both relevant to your business and placed in the context of the wider threat landscape.
The other critical aspect of integration is delivering the most important, specific, relevant, and contextualized intelligence to the right group at the right time.
Threat intelligence solutions can be integrated with SIEMs and other security tools either through APIs or interfaces developed in partnership with the security tool vendors.
Getting Expert Help to Nurture Internal Experts
The value you get from threat intelligence is directly related to your ability to make it relevant to your organization and apply it to existing and new security processes.
You can reach these goals faster if you work with a vendor or consultant that provides both technical capabilities and expertise to empower your organization to get the most from threat intelligence. As time goes on, working with such a partner will enable members of your team to become threat intelligence experts in their own right, so that your capabilities in the field can grow organically.
Start Simple and Scale Up
We hope this book has shown you that threat intelligence is not some kind of monolith that needs to be dropped onto the security organization all at one time. Instead, you have options to draw on a wide range of data sources and then process, analyze, and disseminate threat intelligence to every major group in cybersecurity.
That means you can start simple with your current staff (instead of a dedicated threat intelligence group), a few data sources, and integration with existing security tools like SIEM and vulnerability management systems. You can then scale up to dedicated staffing, more data sources, more tools, more integration, and more automated workflows, as shown in the image below.
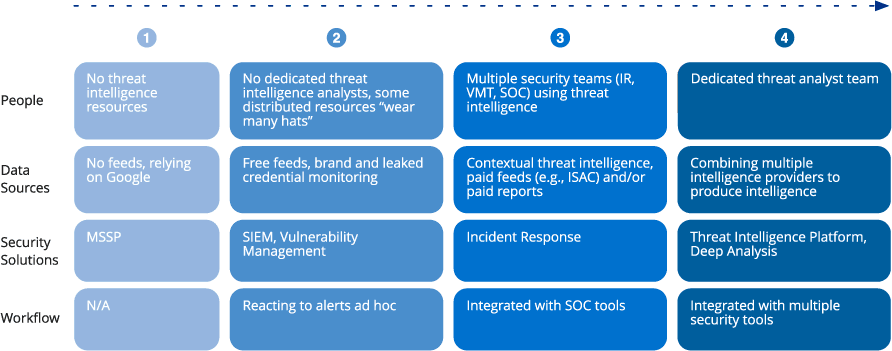
Four stages of maturity for threat intelligence programs, from no internal resources, to limited sources and tools, to a fully staffed, highly automated threat intelligence program.
Start the journey by researching the needs of each group in your cybersecurity organization and seeing how threat intelligence can help them achieve their objectives.
Then, over time, you can build toward a comprehensive threat intelligence program that
Scours the widest possible range of technical, open, and dark web sources
Uses automation to deliver easily consumable intelligence
Provides fully contextualized alerts in real time with limited false positives
Integrates with and enhances existing security technologies and processes
Consistently improves the efficiency and efficacy of your entire security organization
Get ‘The Threat Intelligence Handbook'
You’ll find more resources in the full chapter of the book that will give even more information on the best practices for applying threat intelligence, as well as helpful charts, diagrams, and tips on where to read further. The other chapters of the book also give a good sense of how different teams in your organization can use threat intelligence, exploring different use cases and more. Download your free copy of “The Threat Intelligence Handbook” today.
Related