Investigating Cyber Vigilantes in #OpAntiISIS

Analysis Summary
Cyber vigilantism against pro-ISIS social media accounts and terrorist forums are gaining momentum, moving beyond standard DDoS tactics to bounties and release of alleged personal information.
Temporal analysis identified pro-ISIS social media site “5elafabook” as one of the latest successful takedowns in #OpAntiISIS operations.
Using Recorded Future threat intelligence, we found #OpAntiISIS discussions in a broad array of outlets including Russian-language media and hacking forums.
As the civil war in Syria has intensified on the ground, so has the battle between ISIS supporters and those who seek to stop their efforts online. Recent articles in the New York Times and Newsweek describe the work of cyber “vigilantes” targeting and disrupting pro-ISIS social media, including the release of over 26,000 Twitter accounts that openly promote ISIS efforts.
Using Recorded Future to track ISIS efforts online identified an explosive growth in ISIS supporter Arabic-language tweets and #CyberCaliphate activity, where ISIS supporters have taken the offensive on the Web. Most recently, the so-called “Cyber Caliphate” claimed responsibility for targeting France’s TV5Monde in a wide-ranging cyber attack on Wednesday, April 8.
The latest shift in the online Syrian conflict to cyber vigilantism is representative of two long-term trends: the widespread adoption of new technology by terrorist sympathizers, and rapid online operations following offline political events. In response to this past activity and in an effort to abate its continued development, cyber vigilantes have taken to crowd-sourced efforts, organized by several key influencers and disseminated through common hashtags, to take down accounts and websites sympathetic to ISIS operations.
ISIS and the ‘Cyber Caliphate’
Terrorist groups have long taken to online forums, websites, and social media to promote their attacks and recruit followers. The latest efforts by ISIS and its sympathizers have taken these online efforts to the next level. Previously, with groups like al-Qaeda, online operations were primarily focused on distribution of media and recruiting members from the West through various forums and even proprietary encryption tools.
Currently, ISIS and its sympathizers have taken the next step and moved toward offensive operations. Following offline attacks, like those against the Charlie Hebdo offices in Paris, ISIS supporters were responsible for hacking over 19,000 French websites. Other notable hacks include the hijacking of major US military social media accounts, including CENTCOM, to broadcast pro-ISIS messages.
These operations have been crude in technical capability but quite effective at gaining mass media coverage and challenging the defenses of Western military websites and social accounts.
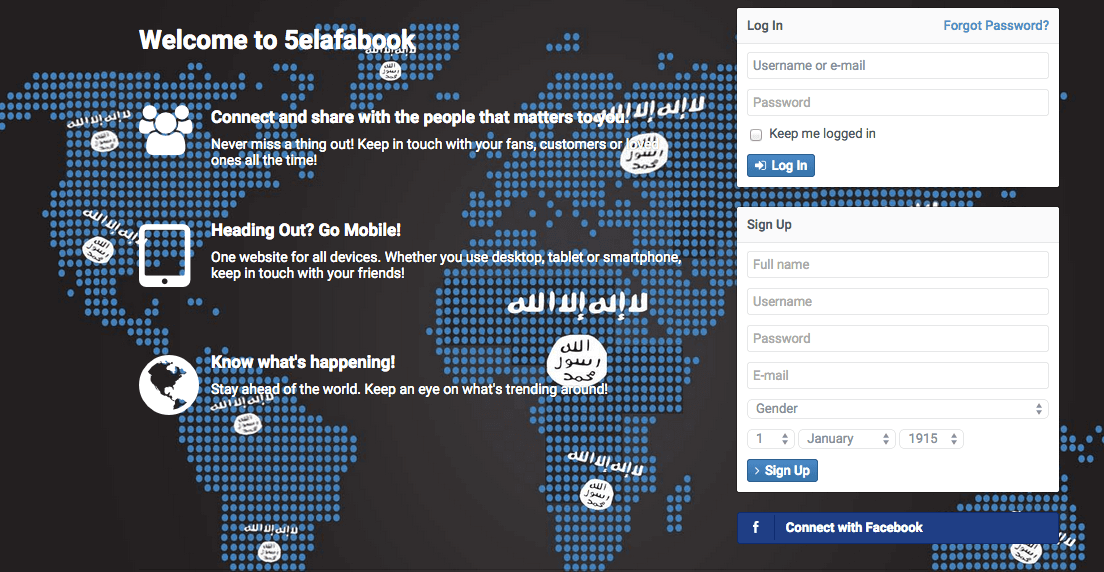
Figure 1: Home page of “5elafabook,” a now defunct ISIS site modeled after Facebook.
Other efforts, as seen in Figure 1, have taken on a more direct approach that has inspired vigilante backlash. ISIS online propaganda and recruitment efforts have been increasingly worrisome, to the level that officials, including Rep. Ed Royce, Chairman of the House Committee on Foreign Affairs, have deemed a “virtual caliphate.”
The “virtual caliphate” is particularly a strong push for recruitment in constructing online spaces that mirror the extremism found offline in occupied territory in Iraq, Syria, and other battlegrounds. Specifically, pro-ISIS supporters have been active in a range of activities, from building large followings on mainstream outlets like Twitter to building proprietary social sites, where pro-ISIS media is supposedly more protected.
First registered on March 9, 5elefabook.com was built as a Facebook clone for ISIS supporters to join safely, following a significant number of pro-ISIS accounts banned across Instagram, Twitter, and other mainstream platforms.
The “khelafa book” site, named after the Arabic term for “caliphate,” was only up for a short period before being taken offline and replaced with a shutdown notice. The English site name transliteration, and the English notice seen in Figure 2, is notable as the trend for terrorist media sites tends to be multi-language with a Western focus to attract recruits and Western media attention. The Whois information remains unchanged and registered with GoDaddy, cited below, with a clear call to “Islamic State Mosul” but with clearly fake information on the postal code and phone number.
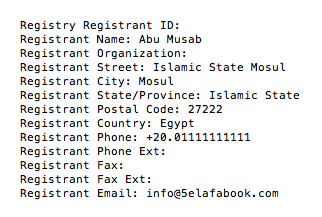

Figure 2: English language shutdown notice following attacks by #OpAntiISIS on the site.
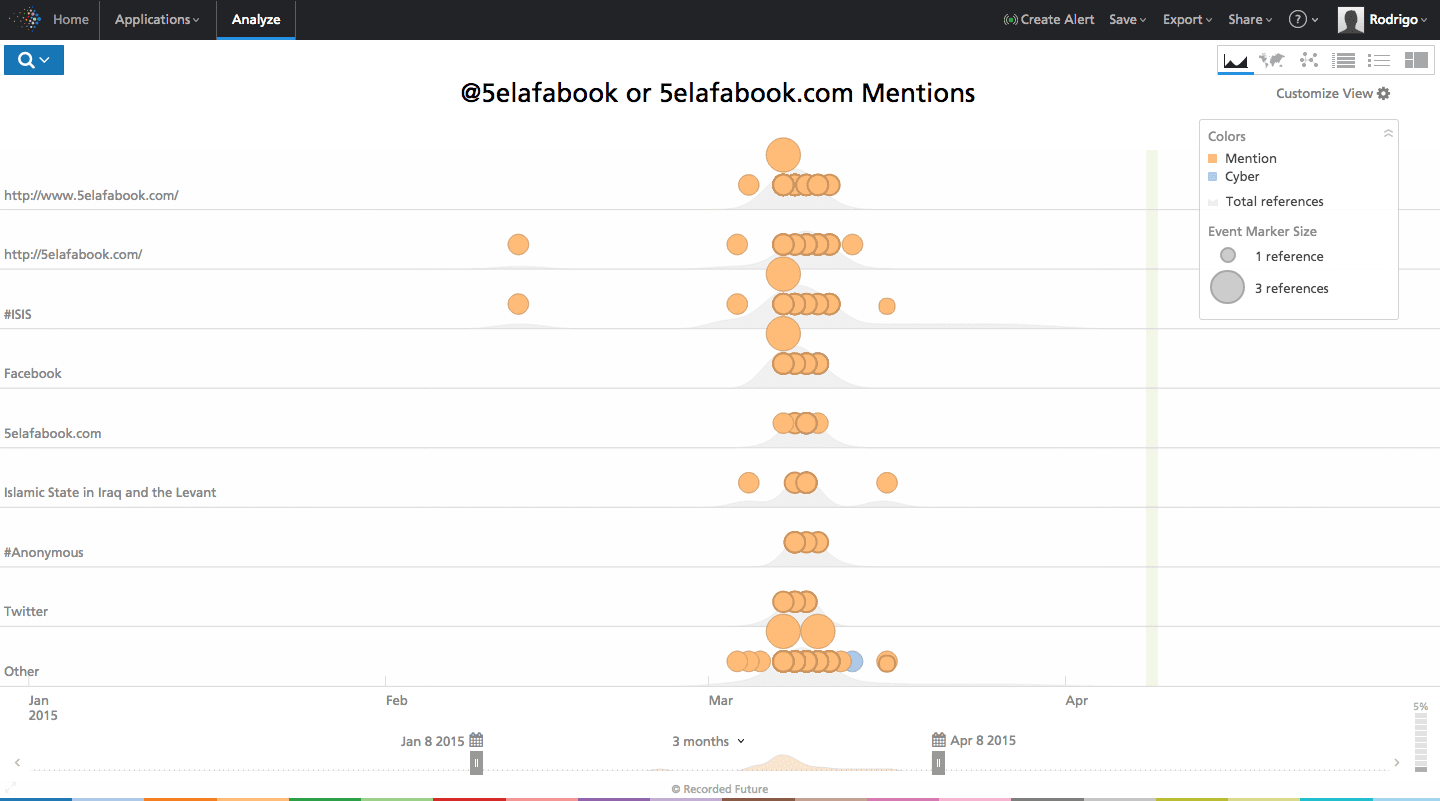
Click image for larger view
Figure 3: 5elafabook.com and @5elafabook rapidly suspended following #OpAntiISIS threats.
Using the Recorded Future threat intelligence platform, we can see the short burst of activity in Figure 3 around the domain and associated Twitter handle, with nothing following as the site was quickly targeted by a joint DDoS attack organized by #OpAntiISIS and Anonymous followers. Pivoting to the vigilantes, we can next try to derive insights into their targets, techniques, and key influencers.
#OpAntiISIS Bytes and Bounties
In a deep dive on the cyber vigilante groups responsible for much of the takedowns and direct action against ISIS online, several key influencers and organizing sites emerge from Web intelligence. Seen below in Figure 4, xrsone.com (now redirected to luckytroll.club) has been the central organizing site for vigilante efforts, including media mentions, massive pro-ISIS account lists, and new targets.
Figure 4: Xrsone.com (luckytroll.club) is the #OpAntiISIS operational site.
The site designates several key accounts, including @CtrlSec and @Iridium_Black. CtrlSec has been mentioned in several of the media articles, and as seen in Recorded Future results, is a consistently active and influential in vigilante discussions across social media. The timeline is organized both by accounts, @ctrlsec and their automated @ctrlsec0 bot, and the #CtrlSec hashtag to capture their influence across vigilante discussions.
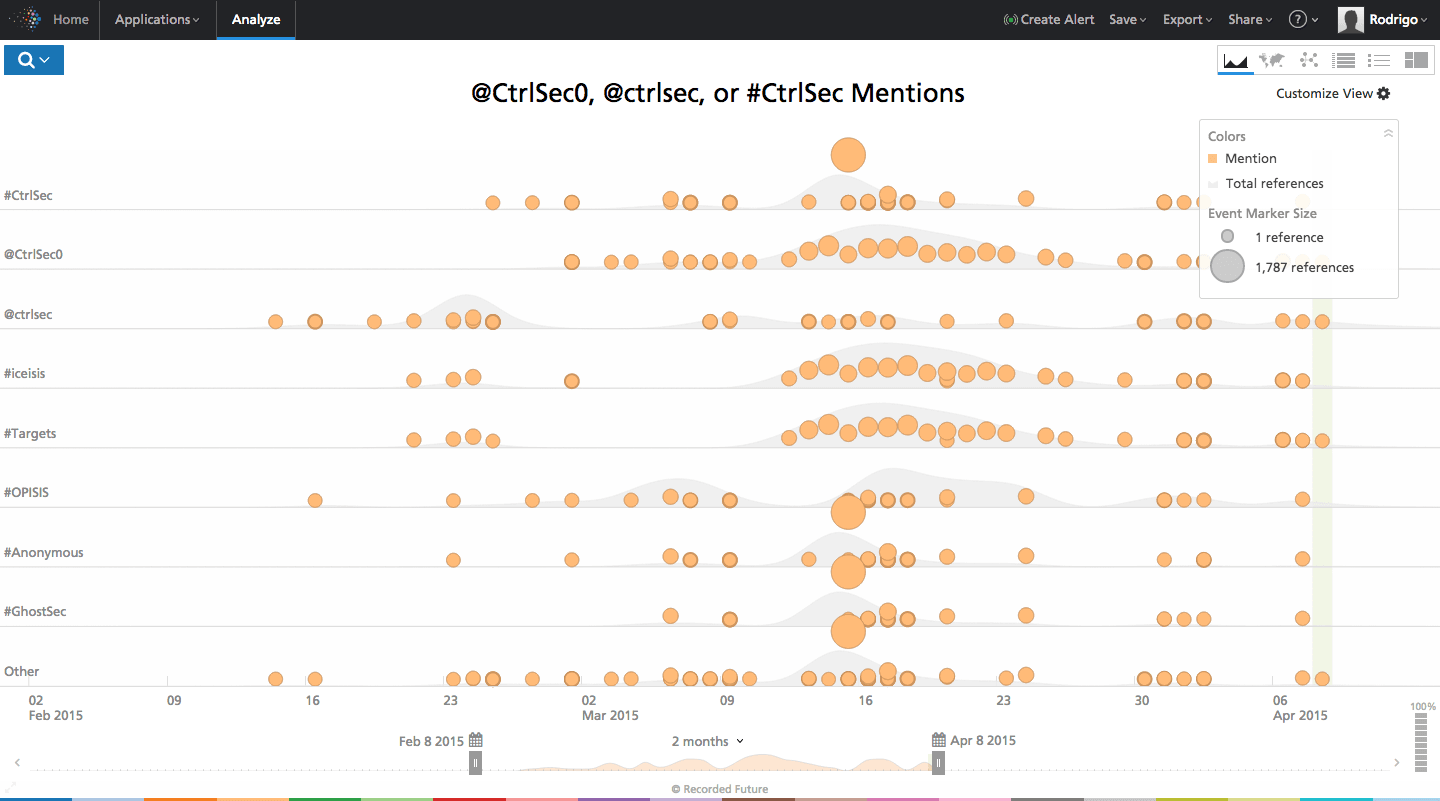
Click image for larger view
Figure 5: Timeline of CtrlSec related-activity shows thousands of references over the last month.
Pivoting from accounts, we can also investigate the operative hashtags like #OpAntiISIS and #OpIceISIS to find insights on the kind of methods, apart from denial of service attacks, and targets the vigilantes seek out.
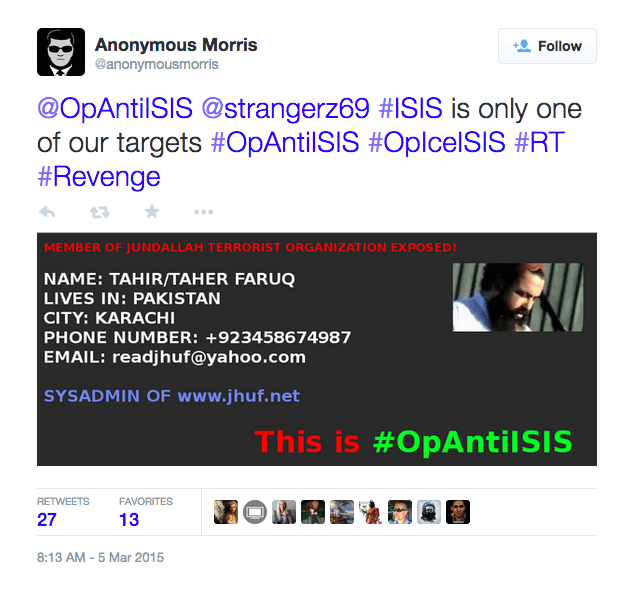
Figure 6: Anonymous releases alleged personal information on terrorist forum admin.
While much of the activity against ISIS accounts is naming accounts to suspend on social media and downing sites, Figure 6 shows more non-traditional tactics. While other vigilantism online, particularly Anonymous operations, focus on crude tactics, setting cash bounties via PayPal is relatively new. Figure 6, the alleged personal information on a JHUF admin, shows #OpAntiISIS followers are expanding their scope to also focus on known terrorist forums.
Online Reactions From Republicans to Russian Hackers
Seen below in Figure 7, social engagement around online ISIS vigilantism has spread to disparate sources. Discussions of CtrlSec, a major influencer in #OpAntiISIS, have spread to outlets like the conservative US media site Breitbart. More interesting is the awareness across Russian media sites and hacking forums, like Exploit.in, which have discussions and news topics about the cyber operations against ISIS.
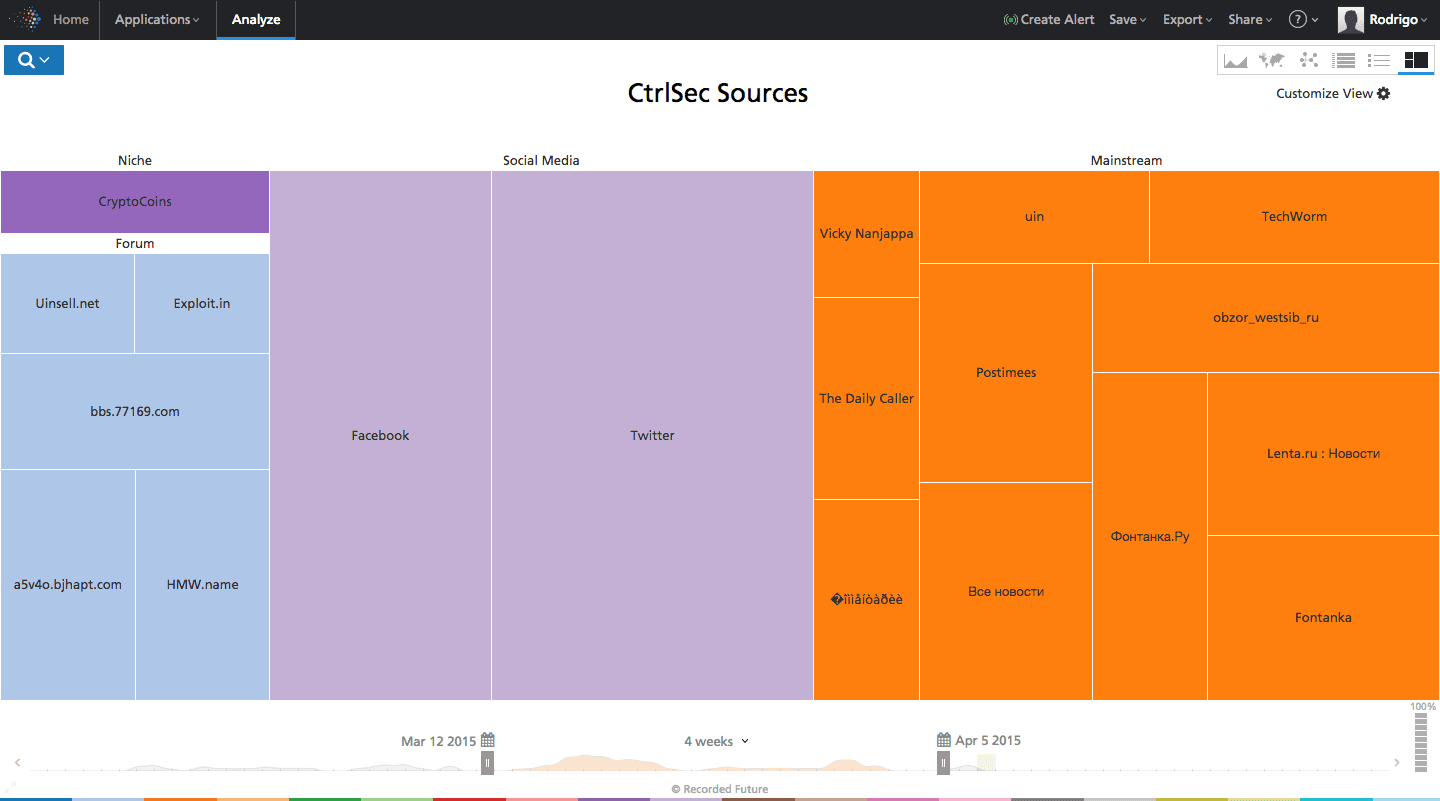
Click image for larger view
Figure 7: Sources discussing CtrlSec, an influencer in #OpAntiISIS.
ISIS social media activity and the vigilante response point to several key conclusions. First, that ISIS, like al-Qaeda, continues to see significant value in maintaining a strong digital presence for recruitment and propaganda, particularly for the West. Similar to proprietary encryption tools, building their own spaces for social media beyond the usual aligned terrorist forums enables them to capture new interest that mirrors Facebook or Instagram social experiences.
The vigilante response, however, is representative of a much broader trend in digital media and security. Using offline political events, especially terrorist attacks, to capture online sentiment and operationalize it is an increasingly powerful tactic. With ISIS, and specific events like the Charlie Hebdo attacks, non-state actors can amass serious capacity through crowd-sourced DDoS attacks, or use the viral discussions to take the next step and distribute malware. With cash bounties and leaking personal info on alleged terrorist forum administrators, the online conflict also takes on a far more personal nature than much of the low-level attacks found in Anonymous-affiliated political operations.
Online vigilantism will play an increasingly powerful role as the ISIS conflict continues to unfold, and it will likely be a greater part of other violent political events in the future.
Related Articles
Recorded Future previously covered the explosive growth in ISIS supporter Arabic-language tweets, and #CyberCaliphate activity, where ISIS supporters have taken the offensive on the Web.
Recorded Future has also covered the emergent trend of online offensive operations utilizing offline political and terrorist-related events like #JeSuisCharlie to spread malware online.
Related