Cyber Caliphate: ISIS Plays Offense on the Web
Cyber Caliphate’s attack of US Central Command’s Twitter page on January 12, 2015, got the attention of the United States and the world, and brought the cyber threat of ISIS to the forefront. Questions about ISIS’s cyber capabilities have been asked since summer 2014. According to a Fox News article published right after September 11, 2014:
Islamic militants brag online that it is only a matter of time before they manage to pull off a highly disruptive attack on America’s infrastructure or financial system. In addition, Islamic State, the terror group that claims to have established a caliphate across Syria and Iraq, boast openly of plans to establish a “cyber caliphate,” protected by jihadist developed encryption software from behind which they hope to mount catastrophic hacking and virus attacks on America and the West.
This article will use Web intelligence to analyze ISIS’s cyber jihad. The call for a cyber jihad, in the spirit of true jihad, could be a call for war and perhaps infer that all believers are welcome to join the fight. If this were true then the idea of a cyber caliphate may have a different organizational structure than other organized hacking operations, such as state sponsored operations. The good news story is that to date the attacks attributed or believed to be conducted by ISIS have been embarrassing, but not necessarily complex or sophisticated. The bad news however is not much is known about the structure, personnel, or intentions of ISIS’s cyber force.
Background
Islamic State in Iraq and Syria and Levant, or ISIS/ISIL, initially an al-Qaeda splinter group has a tremendous social media presence which has primarily been used for recruitment and fundraising. According to The Hacker News, “With huge social media presence, ISIS is the most active terror group on Facebook, Twitter, YouTube and Instagram accounts. But unluckily, over dozens of Facebook and Twitter accounts linked to ISIS has recently been taken by the Anonymous group.” The Recorded Future graph below clearly illustrates how after ISIS’s declaration in September 2014 to create a cyber caliphate, it took until January 2015 to begin to see attacks conducted on behalf of ISIS.
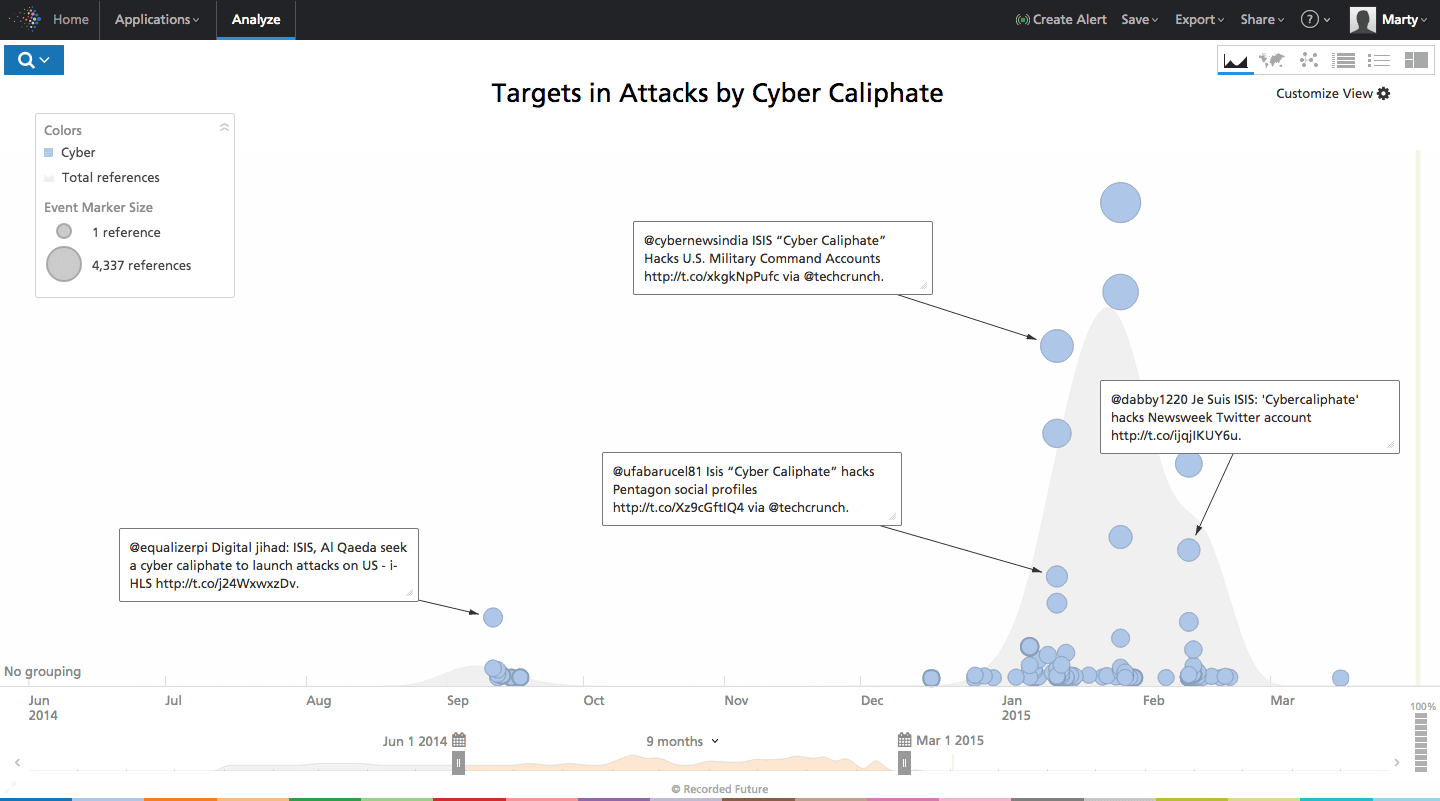
Click image for larger view

Cyber Caliphate
The Cyber Caliphate (#CyberCalipHATE) has been hacking websites and posting extremist propaganda on defaced websites since early 2015. The group launched itself into the spotlight timing its attack on the Twitter and YouTube account of CENTCOM with President Obama’s cyber security speech. Cyber Caliphate also hacked the Twitter handle of Newsweek and the International Business Times website in February. Cyber Caliphate has hacked at least two local US news stations, a non-profit group supporting military spouses, and directly threatened the first family.
According to Web intelligence, ISIS is also responsible for 19,000 French websites being hacked in January 2015, post its attack on the Charlie Hebdo magazine in France.
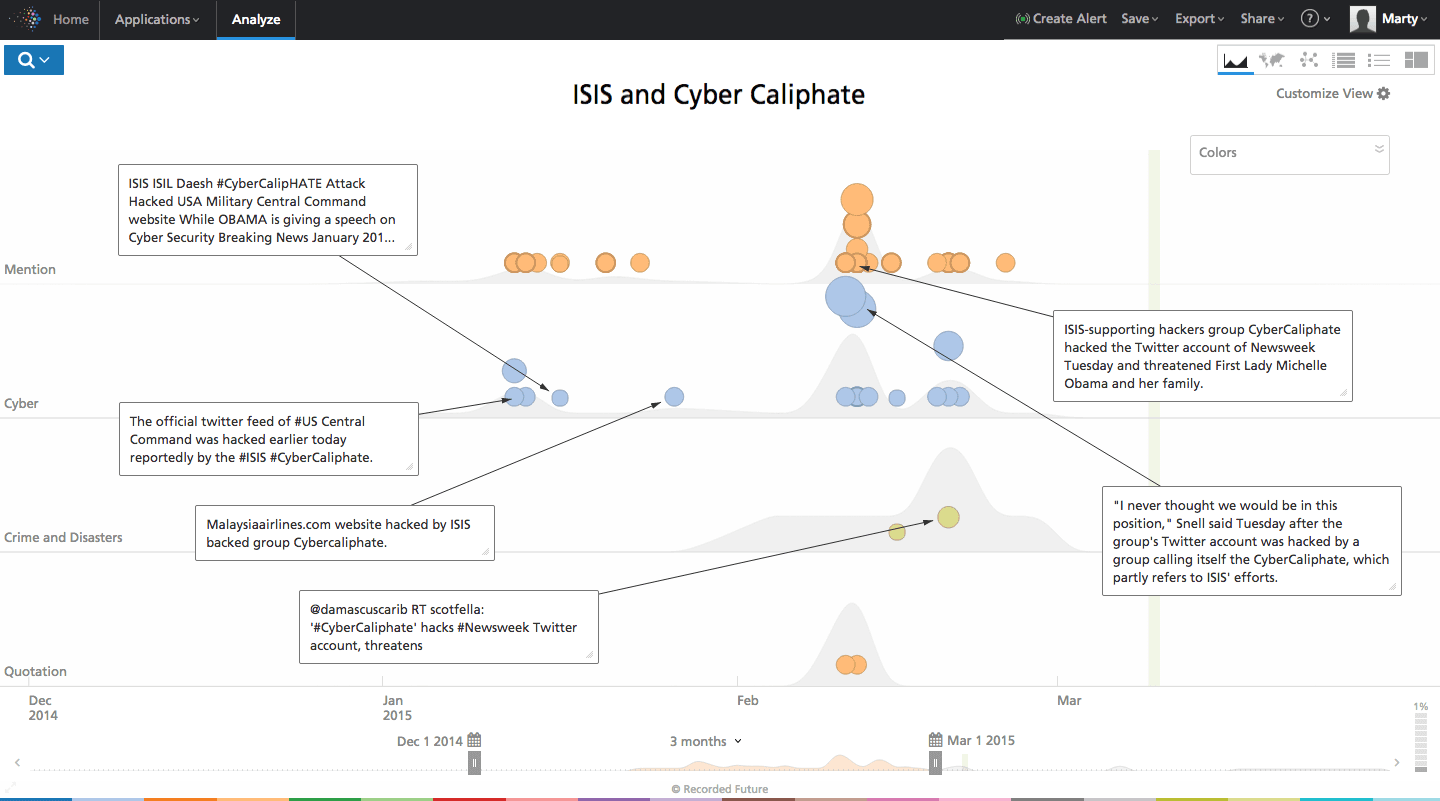
Click image for larger view
In December 2014 alleged ISIS hackers conducted a spear-phishing attack against a Syrian group, Raqqah is being Slaughtered Silently (RSS), focusing on ISIS human rights abuses in city of Ar-Raqqah. According to Infosecurity Magazine:
The unmasking attack took the form of an unsolicited spearfishing email that was carefully worded, and contained references specific to the work and interests of RSS. It contained a download link to a decoy file, which in turn contained custom malware that profiled the victim’s computer and beaconed its IP address to an email account under the attacker’s control.
The attack infects a user who views the decoy “slideshow,” and beacons home with the IP address of the victim’s computer and details about his or her system each time the computer restarts. This behavior strongly suggests that the function of this malware is to serve as a beacon.
Infosecurity Magazine noted the lack of a Remote Access Trojan (RAT), commonly used by Syrian regime-linked malware, suggesting it is intended for identifying and locating a target. Infosecurity Magazine quoted Citizen Lab in their article:
Further, because the malware sends data captured by the malware to an email address, it does not require the attackers maintain a command-and-control server online. This functionality would be especially useful to an adversary unsure of whether it can maintain uninterrupted Internet connectivity.
The use of TempSend.com to host the malware to deliver to the target suggests the intruder is unsophisticated. As Citizen Lab noted, the use of many executable files is unusual. Furthermore, the large number of files included significantly increases the likelihood the malware would be detected. The malware uses 7zip SFX (Self-Extracting Archive) to install on target which also suggests a lack of sophistication. Finally, the file paths utilized by the malware on disk (C:Users[Username]AppDataLocalMicrosoftWindowswin32.tmp) are crude and immature. A sophisticated actor would not make use of a directory named win32.tmp in this location.
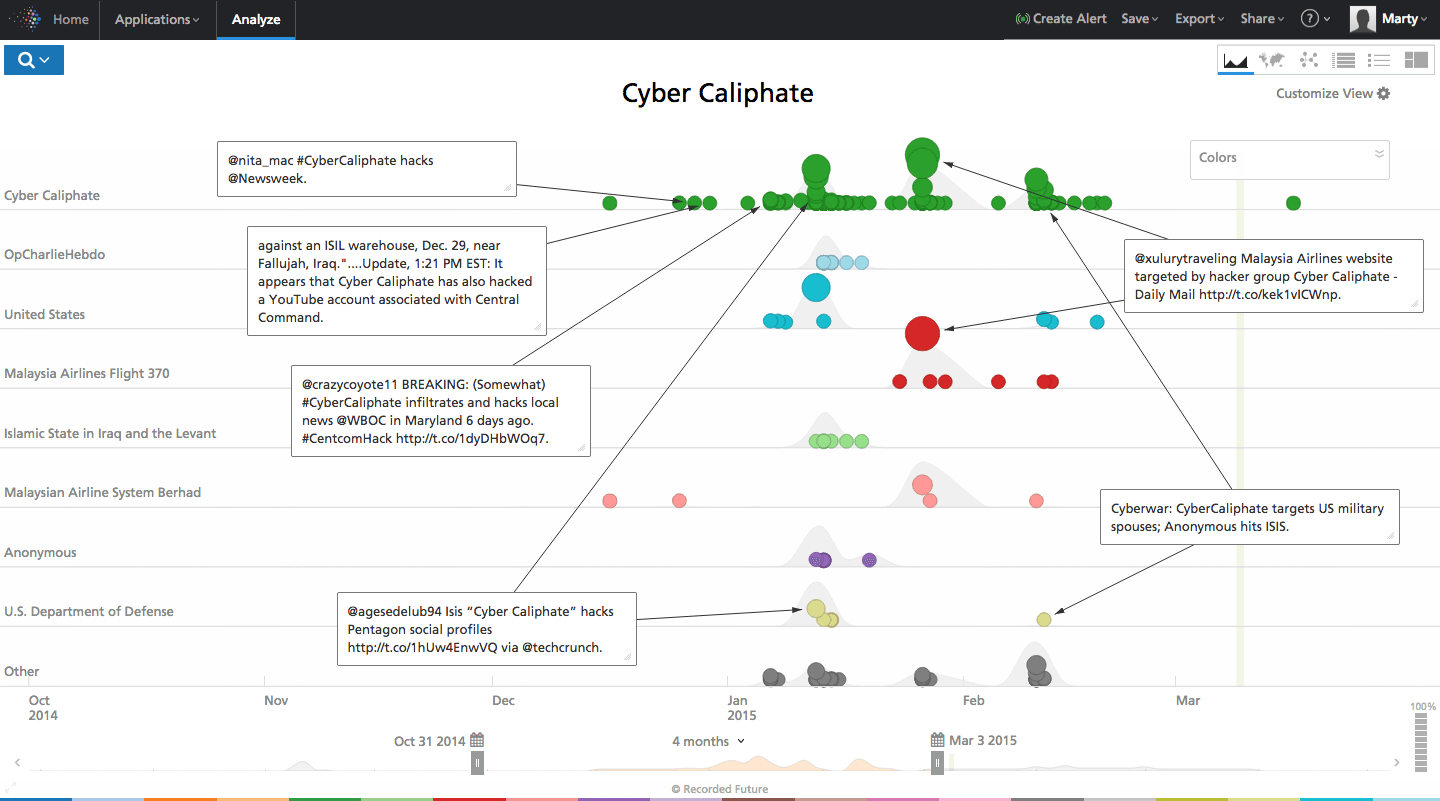
Click image for larger view
According a March 9 article on the Christian Science Monitor’s website, the series of small businesses across the US and UK being defaced in the name of ISIS may not be the work of ISIS radicals, and may instead by kids playing politics and using the name of ISIS to gain media attention and magnify fear.
Are the Cyber Caliphate Attacks Done by ISIS?
The question remains whether or not those attacks, often displaying the words “I Love You ISIS” on the defaced pages, is truly the work of an emerging Islamic Cyber Caliphate. According to the Daily Beast:
There are early signs that the Cyber Caliphate may be more of a ruse than a group of hardline Islamic extremists. One of the seven Twitter accounts it followed was “Andrew Jackson Jihad,” a folk punk band from the American Southwest.
Another perplexing dynamic is Cyber Caliphate’s connection and co-hacking with Lizard Squad. A few of Lizard Squad’s members also identified themselves with Cyber Caliphate on their Twitter information back in early January. Cyber Caliphate attacked pop-star Taylor Swift’s Twitter page on January 27 and tweeted her millions of followers to follow a leader of Lizard Squad. Lizard Squad hacked Malaysian Airlines website with the image of a Lizard, but later wrote “The official Cyber Caliphate” on the page as well.

Elusive Actors
ISIS hackers have been difficult to identify. While Anonymous has taken ISIS into its crosshairs in the wake of the Charlie Hebdo attacks, and identified and taken offline more than 800 social media accounts on Facebook and Twitter linked to the terrorist group. Despite this massive takedown, Anonymous has not published leaders or key members in the Cyber Caliphate or other ISIS hackers. Identifying ISIS hackers may prove challenging in the near future as Twitter suspended over 2,000 accounts of suspected terrorists associated with ISIS.
Despite the takedown on social media, one possible ISIS hacker has been identified as Junaid Hussain, believed to be a key player or leader of Cyber Caliphate and ISIS-related attacks. Hussain was arrested in the UK in 2012 for hacking into Tony Blair’s email account. He reportedly left the UK and has since moved to Syria and joined ISIS. Junaid Hussain was part of teamp0ison, active back in 2012. He has gone by the online monikers Abu Hussain al-Britani, TriCk, and his latest Twitter account, UmmHussain103, has been suspended.

Conclusion
Web analysis of ISIS and its cyber capabilities shows if it wants a Cyber Caliphate, it is likely still in its infancy and lacks the sophistication, training, and cohesion needed to pull off a major cyber threat to U.S. infrastructure. However, where there is a will there is a way, and for the most technologically and social media aware terrorist group to date, achieving this capability is likely something for which ISIS will continue to strive.
Related
