Patch or Pay: 4 Recent Vulnerabilities Tied to Ransomware
Analysis Summary
- Patching recent vulnerabilities (Adobe Flash Players’ CVE-2015-7645, CVE-2015-8446, CVE-2015-8651, and Microsoft Silverlight’s CVE-2016-0034) can significantly blunt the impact of ransomware delivered by exploit kits (“drive by” attacks).
- Adobe Flash Player and Microsoft Silverlight vulnerabilities remain key in-roads for exploit kits delivering ransomware.
- Ransomware has recently impacted North American and European municipal medical and police computer systems in likely untargeted attacks. Poor patching and overall disappointing security hygiene put local public safety and government computer systems at risk.
- Malvertising campaigns utilizing the Angler exploit kit recently targeted NYTimes.com visitors with ransomware.
- Upcoming Recorded Future analysis will further examine ransomware in Europe and alternative methods of delivery including malicious macros.
Hollywood Presbyterian Medical Center’s February ransomware attack was a wake-up call as a likely random attack significantly impacted a 434-bed acute-care facility. Ransomware locked “systems responsible for CT scans, documentation, lab work, pharmacy functions, and electronic communications were out of commission.” Hospital officials reportedly paid the 40 bitcoin (circa $17,000) ransom to regain access to their electronic medical record system. The hospital’s CEO Allen Stefanek told KNBC that it was “… not a malicious attack; it was just a random attack.”
While organizations readily monitor for targeted threats, “target of opportunity” ransomware attacks — found on high-traffic sites including NYTimes.com — can impact an organization just the same. As many are increasingly becoming aware, ransomware either locks a user out of their computer files or encrypts the files. A ransom (typically an amount low enough to frustrate a user into simply paying and avoiding the hassle) is demanded to unlock the computer or decrypt the files.
Ransomware (such as Cryptowall, TeslaCrypt, and Bedep) is often delivered by an exploit kit. Victims can find their way to an exploit kit via an unseen redirection to an exploit kit landing page. As in the case of the recent attack affecting NYTimes.com (and others), these redirections often occur on websites with compromised advertising serviced by third-party providers.
Patch or Pay
While ad-blockers and uninstalling software targeted by exploit kits (EK) can often prevent attacks, organizations — for many reasons — cannot uninstall popular targets such as Adobe Flash Player, Oracle’s Java, or Microsoft Silverlight.
This article highlights key vulnerabilities for patching to help mitigate the impact of exploit kits, and thus many indirect ransomware attacks.
Exploit Kits Play the Odds, Target Popular Software
Recorded Future previously identified top vulnerabilities tied to exploit kits. This report highlighted the regular exploitation of Adobe Flash Player vulnerabilities in multiple campaigns (including ransomware). This updated analysis focused on the time period following our November 2015 research.
Recorded Future’s Web analysis identified four recent vulnerabilities exploited by exploit kits delivering ransomware. As with the previous analysis, Adobe Flash Player and Microsoft Silverlight vulnerabilities are popular targets for exploit kits delivering this payload.
As of March 16, 2016, these are the four vulnerabilities Recorded Future has identified:
- CVE-2015-7645: (Adobe Flash Player) Incorporated into Angler, Neutrino, Magnitude, RIG, and Nuclear exploit kits.
- CVE-2015-8446: (Adobe Flash Player) Incorporated into Angler exploit kit.
- CVE-2015-8651: (Adobe Flash Player) Incorporated into Angler, Neutrino, Nuclear exploit kits.
- CVE-2016-0034: (Microsoft Silverlight) Incorporated into Angler exploit kit.
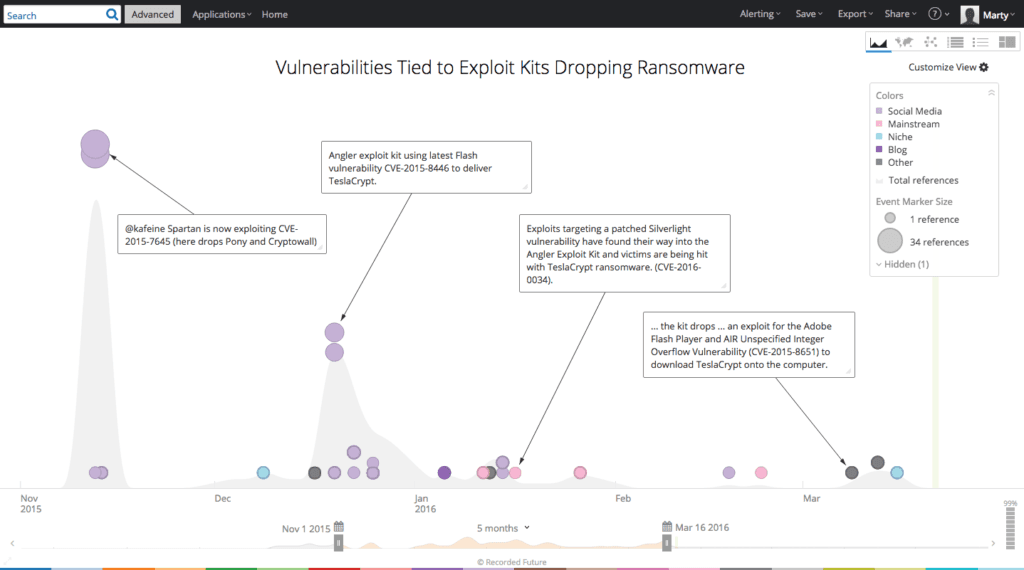
The above visualization highlights the different areas of the Web that were analyzed to pull this information. Recorded Future structures over 720,000 open, deep, and dark Web sources. Focusing on the November 1, 2015 – March 16, 2016 time period, we isolated 162 references to exploit kits and ransomware where vulnerabilities were discussed. This analysis drew upon research from forums, tweets, blogs, and other information security resources.
Methodology and Exploit Kit Links to Ransomware
Utilizing Recorded Future’s Analyze function, we can quickly identify these vulnerabilities by asking what vulnerabilities are linked to “ransomware” (a malware category entity, in Recorded Future, containing over 200 types of ransomware).
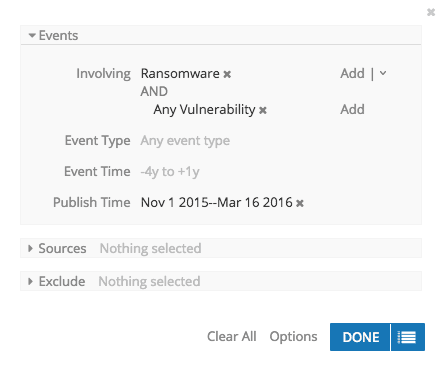
(A strong case can be made that we should focus on vulnerabilities tied to exploit kits versus the payload, ransomware. However, for this analysis we wanted to focus on examples where ransomware was specifically observed. For the record, similar Recorded Future searches on exploit kits specifically returned similar results.) Analyzing the returns, the four vulnerabilities and their links to ransomware attacks become immediately apparent.
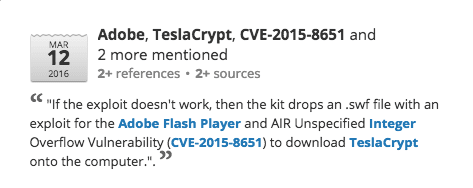
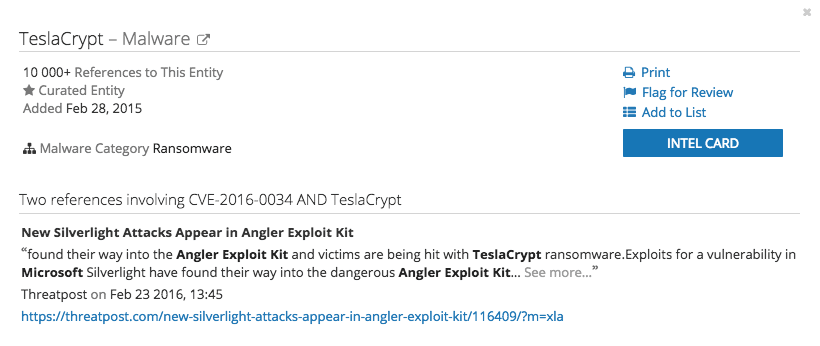
Analyzing the Microsoft Silverlight vulnerability (CVE-2016-0034) using Recorded Future’s Intel Card, we can see the original linkage between TeslaCrypt and the vulnerability.
What Next?
Patching vulnerabilities has real business impact because patching may cause downtime and incompatibility. Prioritizing patches is therefore essential to a successful patch management program. Linking vulnerabilities to current threats and their respective capability and intent ratings can support an effective patch management and risk mitigation plan. Monitoring the Web for target threats is central to a threat intelligence program, however for-profit, targets of opportunity will continue to rise as more business functions are linked to the Web.
Suggested Actions
- Patch all vulnerabilities identified in this post (Adobe Flash Players’ CVE-2015-7645, CVE-2015-8446, CVE-2015-8651, and Microsoft Silverlight’s CVE-2016-0034) and those previously identified in “Gone in a Flash.” Remove the affected software if it doesn’t impact key business processes. Patch browsers.
- Enable “click to play” for Adobe Flash Player.
- Utilize browser ad-blockers to prevent exploitation via malvertising.
- Ensure frequent system backups, particularly of shared files which are regular targets of ransomware.
Related
