Locking up Europe With Ransomware: Origination, Targeting, and Payment
Analysis Summary
- Ransomware infections are on the rise in Europe, and former Soviet states are frequently associated with ransomware.
- Critical infrastructure and business operations are at risk.
- A proactive security stance is needed, and secure backups are a necessity for both private persons and organizations.
Ransomware infections have been abundant in the news for the past few months. Two hospitals in Germany publicly declared that they were affected in February, for example, very shortly after news that the U.S.-based Hollywood Presbyterian Medical Center paid a $17,000 dollar ransom in February to regain access to their systems.
While most of the highly publicized cases have involved U.S. corporations, there’s a growing respect for the dangers of ransomware within the European community. ESET recently published the results of a survey stating that “84 percent of companies would be crushed if infected by ransomware and 31 percent would have no choice but to pay the hackers.”
Before we dive into our analysis, it’s worth noting there are two main categories of ransomware:
| Lockers | Makes an entire computer system unavailable to users until the demanded ransom is paid to the attacker. |
|---|---|
| Crypters | Encrypts files and requires payment for the key needed to regain data access; often leaves the system operational. |
Analysis
Using Recorded Future’s API, which provides a seven year archive of data, we can illustrate the growth of ransomware (including known ransomware families) over time:
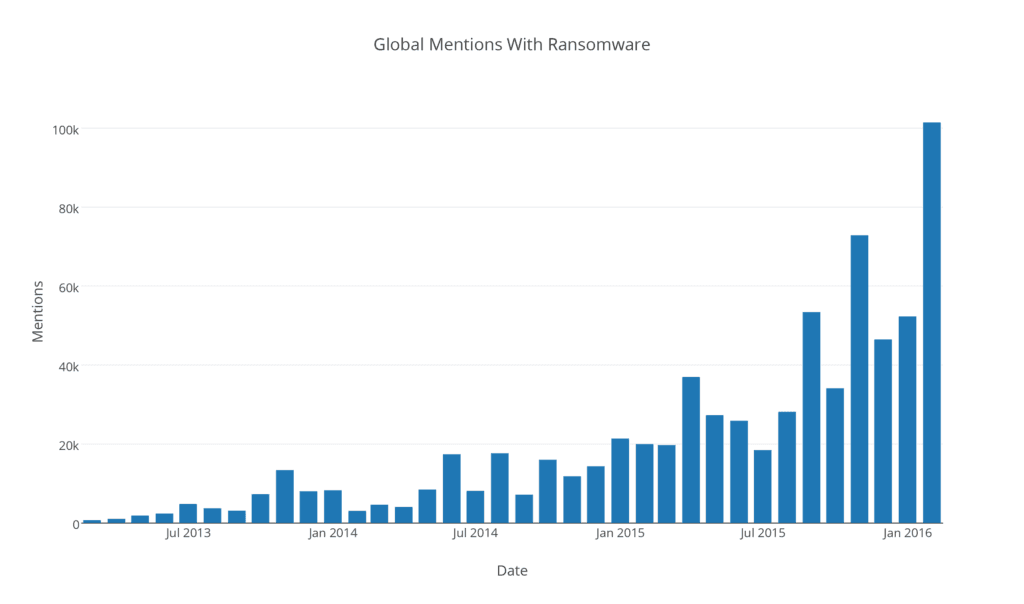
While ransomware wasn’t well known in 2012, there has been a steady increase in the amount of chatter, with a few peaks representing major news events.
If we filter the same data to mentions where Europe (and any of the countries therein) is found in the same sentence as ransomware, we see:
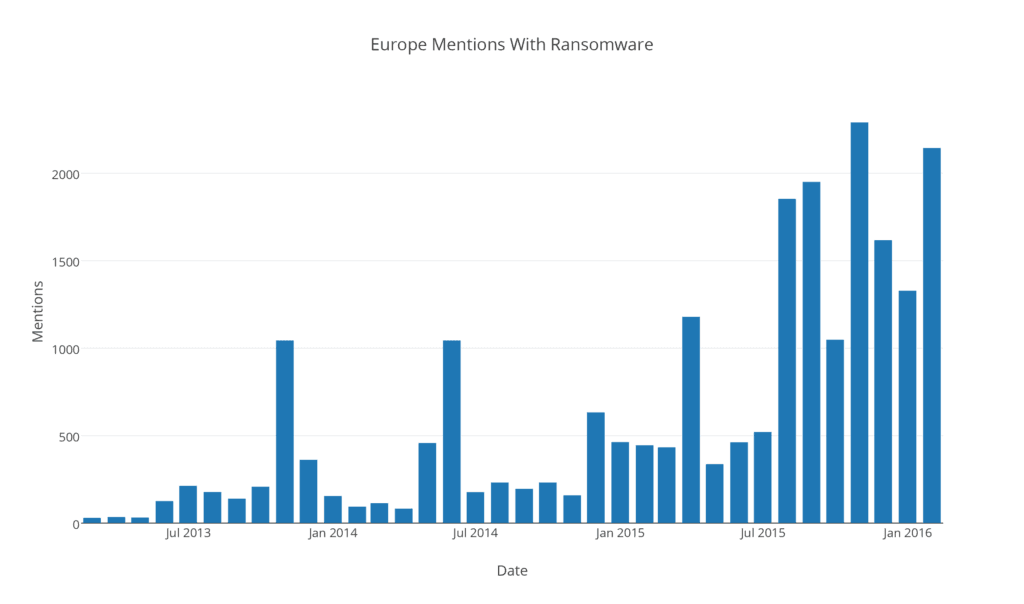
While the volume here is much smaller, we can see a few diffuse reference spikes and a sustained increase in discussion starting in August 2015.
Next, we enumerate which European countries are most frequently mentioned together alongside the term “ransomware”:
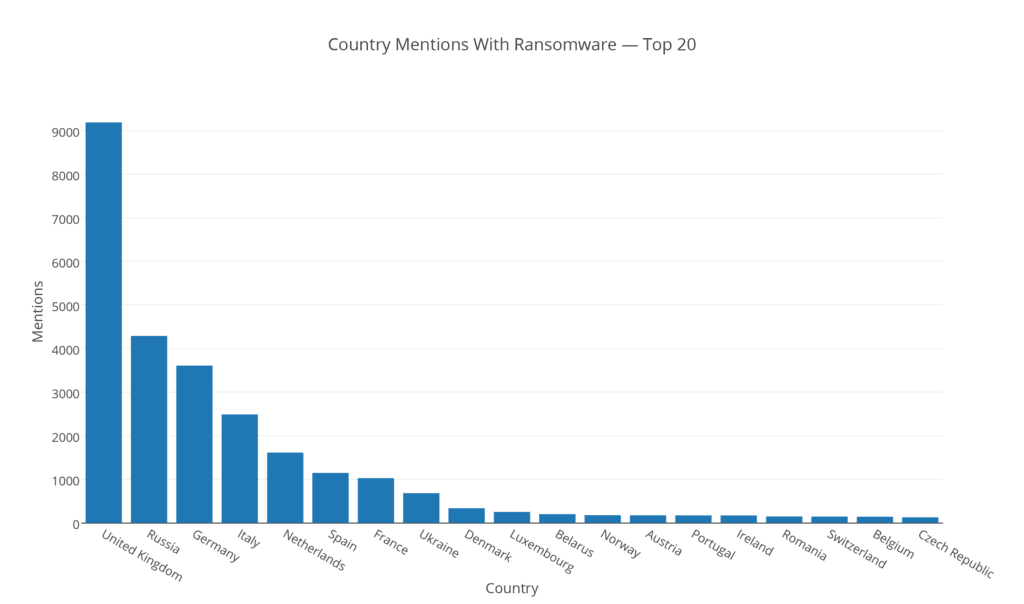
While this mostly aligns with what we might expect (e.g., larger and richer countries are discussed more frequently), a different view is returned if we normalize the mentions of a country together with “ransomware” against the overall mentions of each country:
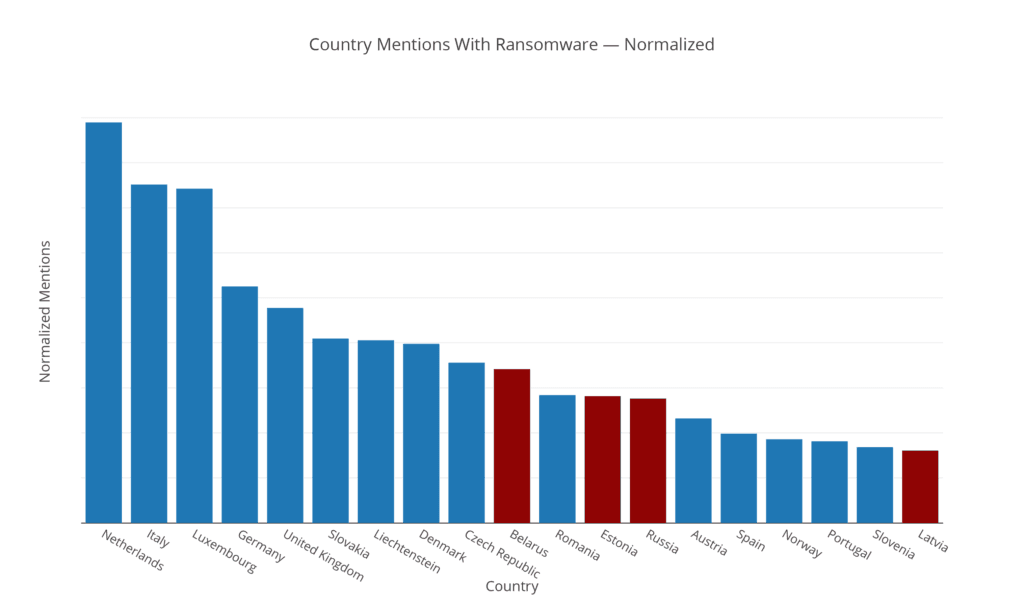
We can see a few new countries making an appearance, where countries in former Soviet Union (highlighted in red) appear disproportionately together with ransomware.
It’s unclear why there’s a heightened appearance of ransomware in these countries. They might be frequently accused of originating ransomware, or an alternative explanation could be that organized Russian gangs are targeting their neighbors (for example Estonia suffered a CryptoLocker [allegedly written by a Russian hacker] outbreak in 2014).
However, an interesting counterexample to this theory is the Cerber Ransomware that makes an active attempt at not infecting computers located in these countries: Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, Tajikistan, Ukraine, and Uzbekistan.
Specific Ransomware Families
Finally, if we switch our focus to the specific ransomware families that are mentioned together with Europe compared to the global perspective, we can see that there are differences:
| Number | Europe | Global |
|---|---|---|
| 1 | Cryptolocker | Cryptolocker |
| 2 | CoinVault | CryptoWall |
| 3 | TorrentLocker | TeslaCrypt |
| 4 | Svpeng | Vundo – VirtuMonde |
| 5 | CryptoWall | CoinVault |
How Ransomware Differs From Traditional Malware
Most aspects of ransomware are similar to botnets. For example, the malware needs to propagate to new hosts, and once an infection has occurred, control needs to be established. However, there’s a key difference: once a victim’s machine is infected with ransomware, there’s an immediate data loss or loss of control.
Payment options vary, but according to Symantec (Page 23):
In general, we found that crypto ransomware tend to favor cryptocurrencies as the preferred payment method whereas locker ransomware prefer to use payment voucher systems.
One issue with highly publicized ransom payments is that distributing ransomware becomes more attractive to somewhat technical individuals looking to earn a quick buck, and the barrier of entry is constantly being lowered with the advent of ransomware-as-a-service (RaaS) products (Tox is one such service, charging a 20% “service charge” on any ransom amount).
Ransomware also necessitates maintenance of a payment system — to pay the attacker, on the victim’s side, and to receive payment on the attacker’s. The victim must also, somewhat ironically, put some level of trust in the attacker and have faith that once the ransom is paid, the attacker will give back access to or control of the data or systems hijacked in the attack.
The need to establish trust with the victim has led to criminal operators of ransomware investing in “customer support.”
Defending Against Ransomware
An active security posture (and an active lookout for threats against your organization and industry) will allow your organization to defend against any type of malware. To ensure your organization is not caught without access to your data in the event of a ransomware attack, roll backups to a secure location (and disable delete access).
Finally, no defense is perfect; if your company is affected and doesn’t maintain dependable backups, the business will most likely have to weigh the cost of the ransom against the cost of re-generating the data (if at all possible). That said, as Andrey Pozhogin at Kaspersky Lab says:
Paying the ransom is unwise; primarily because it does not guarantee that the corrupted data will be decrypted. There are also a number of ways things can go wrong even if one decides to pay the ransom, including bugs in the malware itself that make encrypted data unrecoverable.In addition, if the ransom is paid, this validates to the cybercriminals that the ransomware is effective. As a result, cybercriminals will continue to find new ways to exploit systems and could lead to additional infections targeting that individual user or company.
Further Reading
The US-CERT has published a short overview of ransomware, including some recommendations on how to protect yourself or your organization against ransomware.
Symantec has published an authoritative report on the evolution of ransomware, describing the different types of ransomware as well as statistics on which countries are being targeted the most based on their telemetry. An academic paper published in 2015 analyzed 1,359 ransomware samples outlining the similarities between different families as well as some novel ideas regarding how to detect an infection by monitoring file system activity.
Related
