Gone in a Flash: Top 10 Vulnerabilities Used by Exploit Kits

Analysis Summary
- Adobe Flash Player provided eight of the top 10 vulnerabilities used by exploit kits in 2015.
- Vulnerabilities in Microsoft’s Internet Explorer and Silverlight are also major targets.
- Angler is currently the most popular exploit kit, regularly tied to malware including Cryptolocker.
- Identifying targeted vulnerabilities can better inform patch management functions within organizations.
- Some security professionals suggest uninstalling Adobe Flash Player. Enabling “Click to Play” is a stop-gap.
Recorded Future threat intelligence analysis of over 100 exploit kits (EKs) and known vulnerabilities identified Adobe Flash Player as the most frequently exploited product. While the role of Adobe Flash vulnerabilities as a regular in-road for criminals and malware should come as no surprise to information security professionals, the scale is significant.
According to Web analysis from January 1, 2015 to September 30, 2015, Adobe Flash Player comprised eight of the top 10 vulnerabilities leveraged by exploit kits. Other leveraged vulnerabilities affect Microsoft Internet Explorer versions 10 and 11 (CVE-2015-2419) and Microsoft products including Silverlight (CVE-2015-1671).
Background
Exploit kits are crimeware as a service (CaaS) where users pay per install of their malware. Users only need to provide the payload (malware such as Cryptolocker) and a means to distribute the generated URL. This URL can be spread through compromised sites or malicious third-party advertising (malvertising). The teams behind these exploit kits continue to add fresh exploits for software as increased effectiveness in delivering the “customer’s” payload will generate more revenue.
Exploit kit victims load the compromised Web page, malvertisement or unwittingly follow a malicious link to the exploit kit’s landing page. Per Sophos, “the landing page is the starting point for the exploit kit code.” Using a mix of HTML and JavaScript, the EK identifies the visitor’s browser and plugins, providing the kit the information necessary to deploy the exploit most likely to result in a drive-by download.
Understanding what vulnerabilities are targeted by exploit kits can better inform patch management functions within organizations.
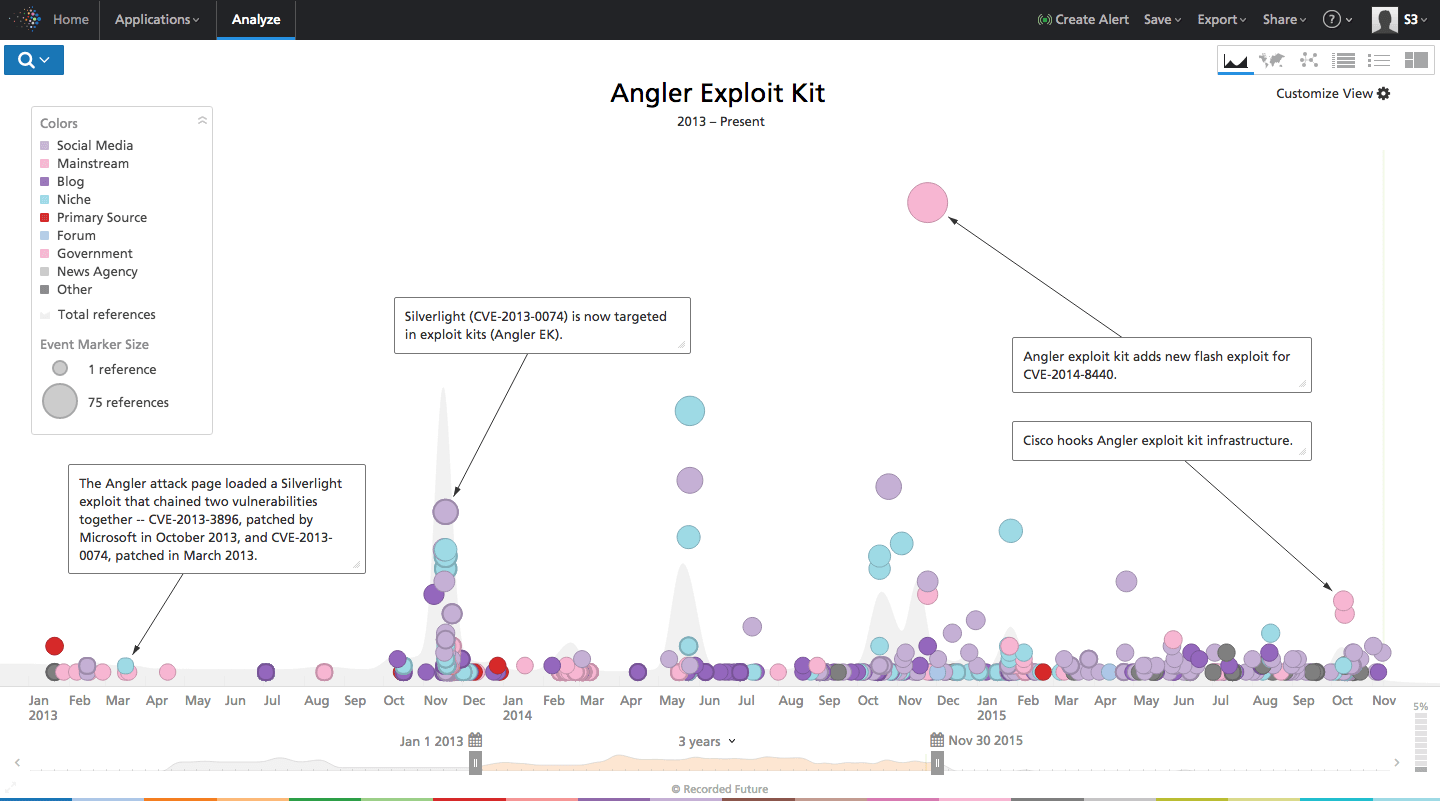
Angler Exploit Kit in Focus
Angler is one of the most popular and well-known exploit kits, linked to several high-profile malvertising and ransomware campaigns. First appearing in 2013, it quickly overtook Blackhole as a favorite of cyber criminals, likely due to the rapid pace of new exploit adoption and its ability to evade many antivirus products.
Recorded Future analysis of Web sources including social media, forums and technical reporting highlighted Angler payloads including Cryptowall, AlphaCrypt, Necurs, and Bedep malware.
Click image for larger view.
In October, Cisco claimed to strike a blow to Angler as they found a large batch of Angler proxy servers which accounted for up to 50 percent of the exploit kit’s activity. This infrastructure reportedly targeted up to 90,000 victims a day and generated over $30 million a year.
Methodology
Recorded Future analyzed thousands of sources from the Web including .onion site, criminal forums and social media. Analysis focused on exploit kit and vulnerability discussion from January 1, 2015 to September 30, 2015. As part of this research, Recorded Future utilized a list of 108 exploit kits which included well-known EKs such as Angler, Neutrino, Nuclear Pack, etc. Top EK exploited vulnerabilities were ranked by the number of Web references linking them to an exploit kit.
Recorded Future did not reverse engineer any malware mentioned in this analysis and instead performed a meta-analysis of available information from information security blogs, forum postings, etc. Exploits for dozens of other vulnerabilities are currently employed by EKs and this article’s intent is to highlight top targets of popular exploit kits.
Results
Using this methodology, Recorded Future identified the top vulnerabilities used by exploit kits. Adobe Flash Player vulnerabilities dominated this list with thousands of references.
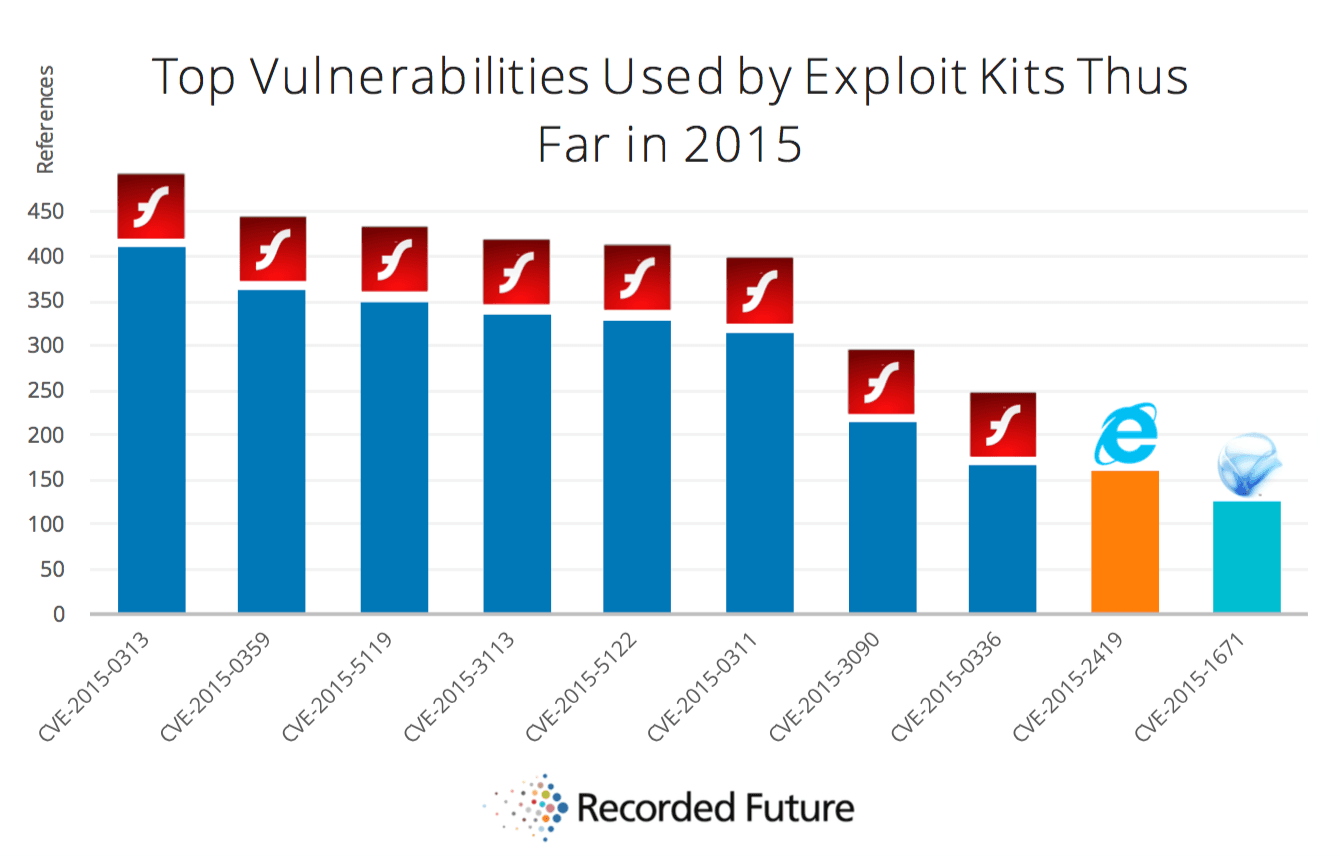
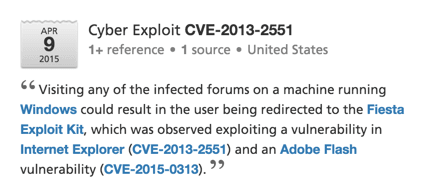
The top vulnerability CVE 2015-0313 – affecting Flash Player 16.0.0.296 and identified by Adobe as critical – was patched on February 2, 2015 and seen as a zero day exploit as early as December 2014. Recorded Future observed 410 references of CVE-2015-0313 tied to an exploit kit in 2015. This vulnerability has recently been seen in the Hanjuan, Angler and Fiesta EKs.
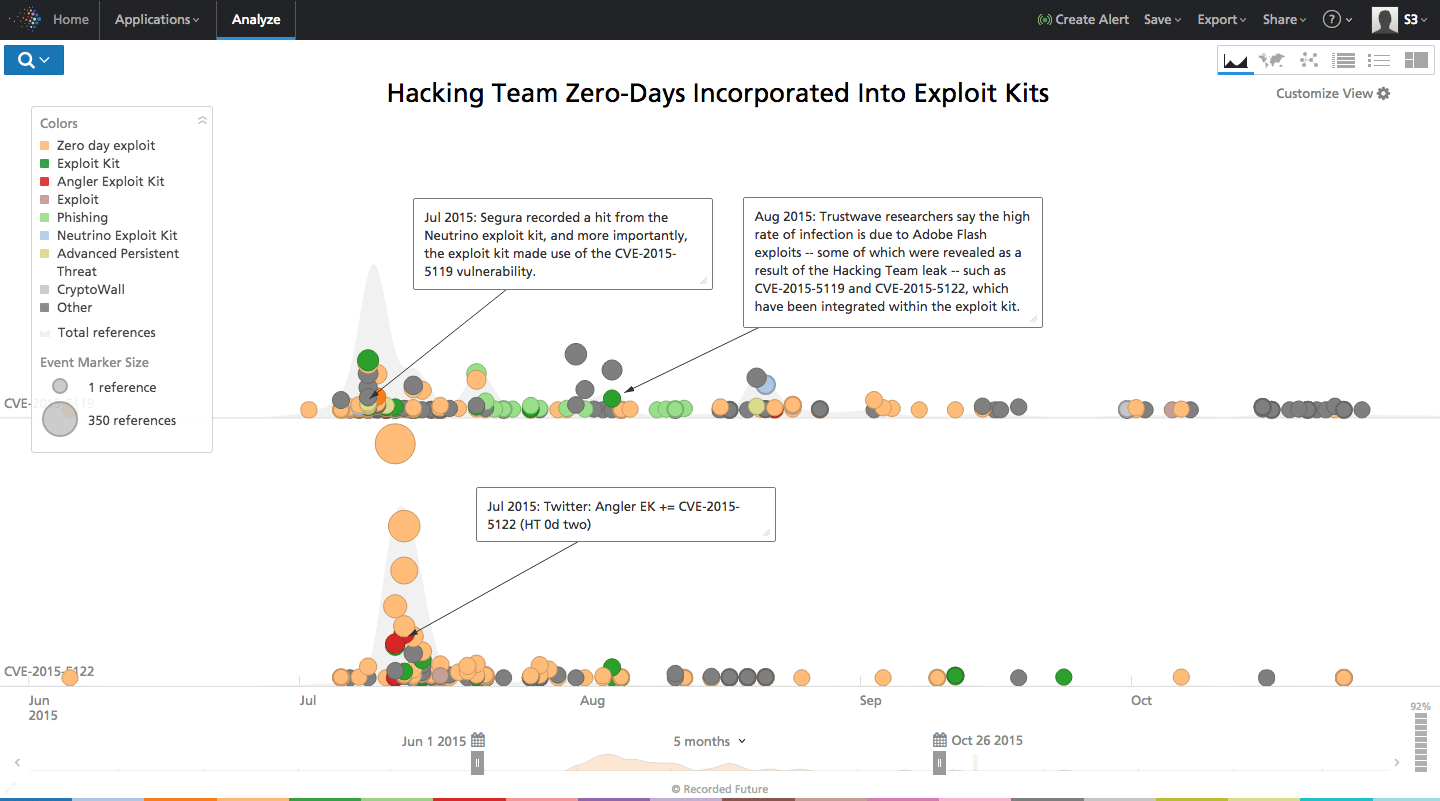
Exploits tied to the third and fifth most mentioned vulnerabilities (CVE-2015-5119, CVE-2015-5122) were immediately added to EKs including Angler following their disclosure as a Adobe Flash zero-days in the July 2015 Hacking Team leak.
Click image for larger view.
Impact
Popular due to compatibility across browsers and operating systems, Adobe Flash Player’s recent string of vulnerabilities, and popularity with APT groups such as Pawn Storm, calls into question Flash’s place in a secure operating environment.
Flash versions older than 19.0.0.226 (or 18.0.0.255 on older machines) are now actively restricted from running on Apple OS X. Brian Krebs recently wrote about going a month without Flash. In July, WIRED discussed the Occupy Flash movement and detailed its long line of issues.
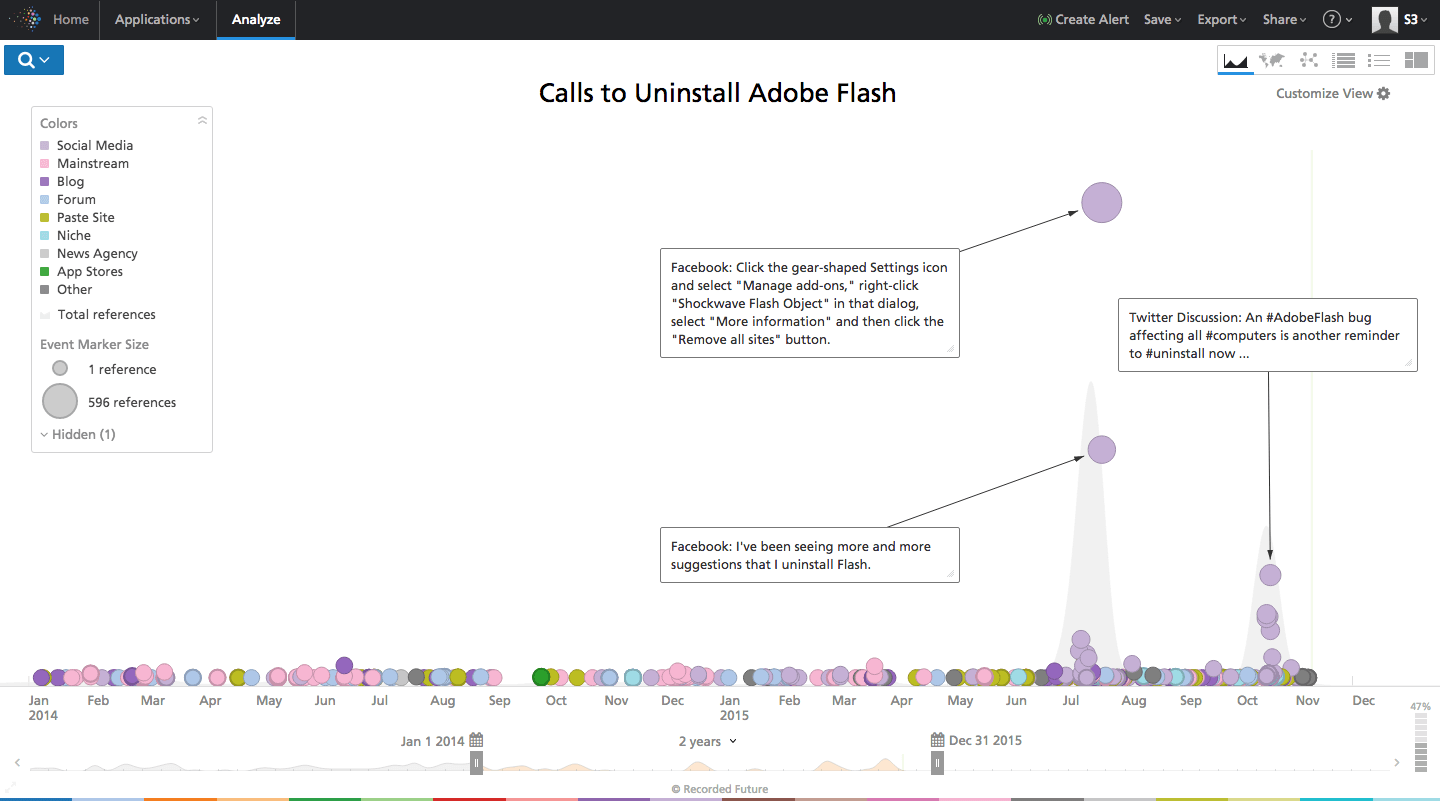
Click image for larger view.
Conclusion
While each organization needs to decide for itself if installing the steady stream of Adobe Flash updates is feasible, steps can be taken as a stop-gap to Adobe exploits. This includes enabling “Click to Play” which provides a check on use of Adobe Flash Player in an unknown environment.
Related