MISP: The Open Source Threat Sharing Intelligence Platform
As cyber threats grow more sophisticated, the need for powerful threat intelligence platforms like MISP becomes crucial. MISP excels in enabling cybersecurity professionals to share, store, and correlate threat data in real-time.
In this blog post, we will dive into how MISP’s collaborative ecosystem promotes a proactive defense against cyber risks, equipping you with knowledge for operational readiness.
Key Takeaways
- MISP is an essential platform in cybersecurity; capable of malware analysis, incident sharing, and enhancing collaborative threat intelligence efforts by structuring, storing, and disseminating cybersecurity indicators globally.
- The architecture of MISP supports flexible and secure threat intelligence sharing through a complex system of events, feeds, groups, and users, providing controlled distribution options and fostering active community collaboration.
- MISP maximizes threat intelligence by automating analysis, offering advanced filtering, and integrating with existing systems, alongside fostering rapid incident response and exchange of comprehensive threat data across various industries.
What is MISP Threat Sharing?
MISP stands for Malware Information Sharing Platform. It's a powerful tool in cybersecurity that helps with analyzing malware. It can:
- collect
- store
- distribute
- share
What Is Its Role in Cybersecurity?
The importance of cyber security incidents analysis in identifying cyber security indicators and utilizing express threat intelligence, along with cyber threat intelligence, makes it a cornerstone in the industry. Threat intelligence analysts serve as a powerful tool, allowing incident responders to share information about targeted attacks and other cyber threats, and thereby enhancing our collective ability to combat cyber threats through sharing cyber security indicators.
MISP is designed to be a strong and reliable platform. It aims to support the process of discovering, developing, and leveraging threat information smoothly. It’s not just a platform but an ecosystem, fostering collaboration and intelligence sharing among a community of users that spans the globe.
The Architecture of MISP: How It Facilitates Threat Intelligence Sharing
A platform as powerful as MISP requires a solid foundation - its architecture. The structure of MISP is a complex web of events, feeds, groups, and users, all working in unison to facilitate the exchange of threat intelligence. Threat intelligence feeds in MISP are a critical component, utilized to import threat data such as threat reports, indicators of compromise (IoCs), and other relevant information.
The architecture of MISP is designed with sharing in mind, offering flexible sharing group capacity. It provides four distinct options for the distribution of events and their related attributes, ensuring that the scope of sharing is controlled and secure. This intricate design ensures that MISP isn’t just a repository of threat intelligence, but rather an active ecosystem that fosters collaboration and collective defense against cyber threats.
Maximizing Threat Intelligence
Now that we’ve understood the foundation of MISP, let’s dig into how it maximizes threat intelligence. MISP takes threat intelligence to the next level by:
- Automating threat intelligence analysis, automatic correlation finding relationships, and collaboration
- Providing advanced filtering and warning lists to refine data
- Elevating the quality of threat intelligence produced

Collecting and Analyzing Data
MISP is utilized by security researchers and organizations to:
- Gather and exchange data on the most recent vulnerabilities, exploits, and threats
- Stay informed and respond effectively to emerging cybersecurity threats
- Employ MISP as a central repository to collect varied intelligence and analyze it for actionable insights
- Enable a swift response to potential threats, thereby fortifying defense mechanisms.
MISP stores Indicators of Compromise (IoCs) in a structured way, which aids in correlating and automating exports to intrusion detection systems. Furthermore, SOC teams utilize MISP to understand specific campaigns applied to various IP addresses. This, coupled with the platform’s free text import tool, enables organizations to ingest API pull requests on SIEM, configure firewall blacklists, and contribute to the community with shareable feeds and activities.
Sharing and Responding to Threats
In the face of cyber threats, rapid response is paramount. The MISP project leverages its built-in sharing functionality to enable easy threat intelligence distribution. This feature allows trusted partners and groups to engage in real-time sharing and receiving of threat data, facilitating prompt detection and defense against cyber attacks using network intrusion detection systems.
Incident responders can employ MISP for information exchange on ongoing or historical incidents. This not only enhances collective defense but also ensures compliance with regulations. Furthermore, community members can store and exchange comprehensive information about threats, including malware samples and details of attackers and their methods. In essence, MISP makes sharing and responding to threats a collective and efficient process.
Integrating MISP with Existing Systems
MISP isn’t just a standalone platform. It can be integrated into existing systems using its REST API, which can be accessed programmatically via the PyMISP library. This seamless integration ensures that organizations can leverage MISP’s capabilities while maintaining their existing workflows.
Numerous security tools and platforms offer pre-built integrations with MISP, ensuring a smooth transition. Additionally, MISP supports integration with various commercial threat intelligence sources, which aids in sharing and managing intelligence from diverse sources.
MISP also integrates with threat intelligence frameworks like the Cyber Kill Chain, MITRE ATT&CK, and The Diamond Model of Intrusion Analysis, enhancing defensive strategies against cyber threats. In essence, MISP’s flexible integration capabilities make it a valuable addition to any cybersecurity toolbox.
MISP Integration with Recorded Future
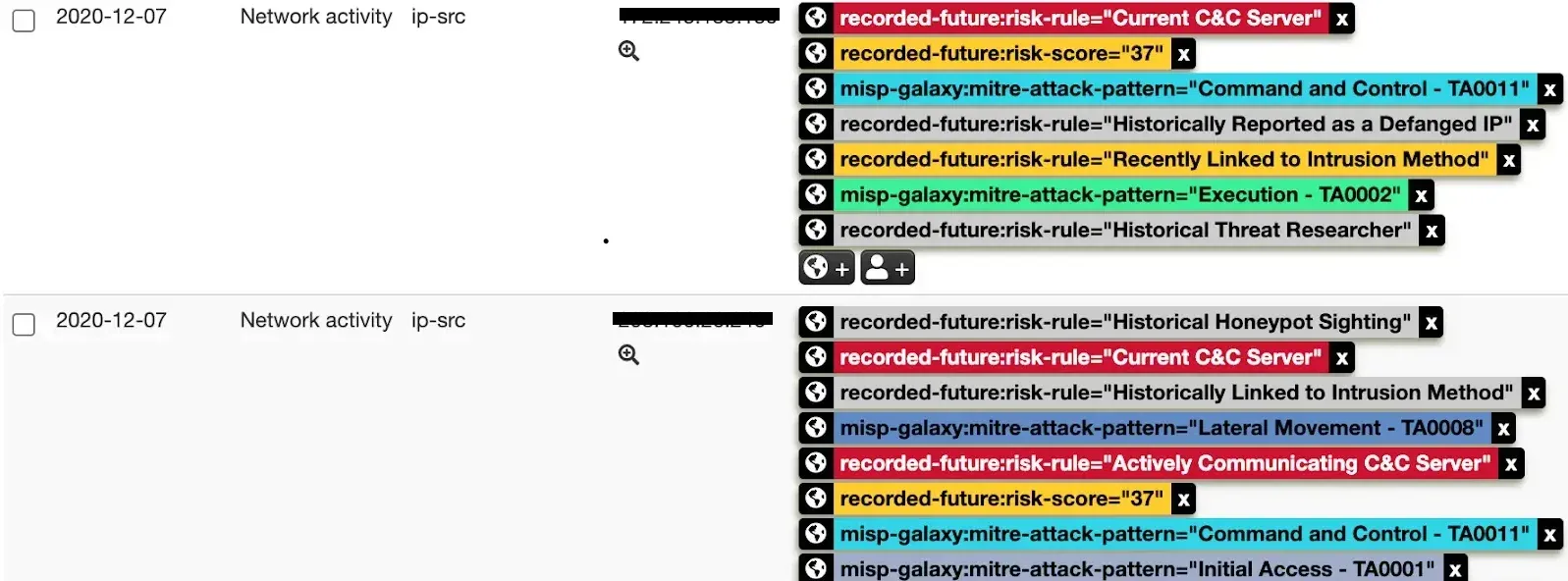
MISP includes an integration with Recorded Future, providing real-time intelligence to enhance threat detection and response capabilities. This integration allows security teams to respond quickly with transparency and context, maximizing the investment in existing security tools while improving overall efficiency. By leveraging MISP Galaxies for malware and threat actors, event correlation is significantly enhanced.
Key benefits of this integration include:
- Respond quickly with transparency and context
- Maximize your investment in existing security tools
- Improve security team efficiency
- Reduce manual research time
Additionally, the integration supports IP, domain, hash, URL, and vulnerability risk lists, broadening use cases and functionality for end users. Real-time risk scoring for indicators of compromise enables faster analysis of high risks, streamlining threat response processes. In essence, MISP’s flexible integration capabilities make it a valuable addition to any cybersecurity toolbox. Learn more about the Recorded Future + MISP integration.
Installing Your Own MISP Instance
Getting started with MISP requires setting up your own instance. The process includes the following steps:
- Update existing packages on your Linux system.
- Ensure that the installation is performed by a user with sudo permissions, not as the root user.
- Install MISP using the provided install scripts. The scripts cater to different needs, including core, module, full, or unattended installations.
Following installation, the MISP instance can be accessed via a provided URL using the default credentials. The platform features an intuitive user interface that assists analysts in efficiently navigating between events and correlations for analysis of cybersecurity incidents. However, be aware of potential technical hurdles such as issues during the creation of the GPG key, often related to insufficient system entropy.
Installation guides for various Linux and BSD distributions are available on the official website.
Real-World Applications of MISP Across Industries
The versatility of MISP allows it to be used across various industries. In the financial sector, Operators of Essential Services use MISP to manage risks and comply with the EU’s NIS Directive, which mandates notification of significant incidents to competent authorities. Moreover, MISP aids in fraud detection and prevention by providing a collaborative environment to analyze and share information on cybersecurity threats and fraud indicators.
MISP also facilitates cross-border cooperation in the financial sector, enabling a collective response to cyber crises. With designated sharing groups accessible to various members per sector, MISP enhances tailored threat intelligence for the financial sector. Evidently, MISP’s applications span beyond cybersecurity, proving its utility across various fields.
Enhancing Collaboration Through MISP's Flexible Data Model
Collaboration is key in the world of cybersecurity, and MISP’s flexible data model serves as a catalyst for it. MISP employs a structured data model for classifying and organizing threat intelligence that includes events, attributes, and objects such as attack patterns and malware characteristics. This model not only allows for the articulation of complex threat intelligence but also enables the linking of objects together, enhancing the effectiveness of shared information.
MISP includes intrinsic sharing functionalities that endorse multiple distribution methodologies. With automatic event and attribute synchronization across different MISP instances, MISP ensures that information sharing adheres to organizational sharing policies. Moreover, MISP’s open taxonomies can be applied across varied software applications, facilitating the structuring and sharing of threat intelligence.
Advanced Features of MISP for In-Depth Analysis
MISP is packed with advanced features that facilitate in-depth analysis. Its event graph allows analysts to visualize and establish relationships between various objects and attributes, enhancing the analysis of complex threat data. Furthermore, through independent Python 3 modules, MISP allows users to customize and expand its functionality for specific needs in expansion, import, and export services.
MISP, an open source threat intelligence platform, also integrates galaxy clusters and supports CTI taxonomies like MITRE ATT&CK, providing analysts with a common language and predefined classifications to aid in the meticulous analysis of threats. Moreover, the threat intelligence platform supports exporting threat indicators into a variety of formats, such as OpenIOC, STIX (XML and JSON), and CSV, to facilitate sharing and collaborative threat analysis.
Security Measures in MISP
With all the data sharing and collaboration, how does MISP ensure the security of shared intelligence? Firstly, MISP users can employ PGP to receive signed and encrypted notifications, safeguarding the privacy of communications within their networks. The platform’s design also ensures the protection of anonymized contributions, maintaining the confidentiality of both source and recipient identities.
Incorporating SSL certificates and PGP keys within MISP aligns with cryptographic control recommendations. The platform also complies with international security communications standards, specifically ISO/IEC 27010:2015, which offers controls for inter-organizational and inter-sector exchanges. Furthermore, an integrated event logging system enables MISP administrators to effectively track the distribution and internal use of shared threat intelligence.
MISP’s synchronization protocols provide secure information transfer options, including air-gap exchange protocols for environments with strict security controls. Various distribution settings in MISP allow users to manage the sharing of threat intelligence in alignment with the classified nature of incidents. However, during MISP installation, the challenge of depleted entropy necessary for GPG key generation can be a technical hurdle. Thankfully, this can be addressed through solutions like rng-tools or specific command-line operations to generate adequate entropy for secure processes.
Leveraging Community Knowledge
The strength of MISP doesn’t just lie in its features and capabilities, but also in the vibrant community that supports it. MISP is backed by a global community of users and organizations that create and maintain diverse threat information sharing communities. Community members can collaborate via the platform’s forums, discussion threads, or by contributing through the MISP API, user-interface, or instance synchronization.
MISP also fosters specialized communities catering to specific groups such as FIRST’s incident response teams or CIRCL’s community focused on private and financial organizations. This highlights the platform’s adaptability and its ability to cater to a wide range of needs. The FIRST community exemplifies the diverse nature of information sharing by supporting both technical and non-technical content exchange regarding malware, attackers, and incidents.
Tailoring MISP to Meet Specific Organizational Needs
Organizations often have unique security concerns, and MISP offers the flexibility to cater to these needs. Organizations can develop custom taxonomies and classification schemes in MISP, enabling them to appropriately categorize and manage risks and incidents in line with their unique security concerns. The customization capabilities of MISP allow organizations to refine their threat intelligence according to specific operational requirements.
MISP instances can also be configured with customized ‘Terms & Conditions’ to stipulate clear principles and guidelines for sharing and coordinating on threat intelligence. Furthermore, MISP supports the implementation of industry standards like ISO/IEC 27010 by leveraging its extensible tagging system and structured sharing mechanisms, promoting best practices in information management and exchange.
Frequently Asked Questions
What is MISP and what role does it play in cybersecurity?
MISP, which stands for Malware Information Sharing Platform, plays a crucial role in cybersecurity by enabling the sharing of cybersecurity indicators and threats, thereby enhancing collective combat against cyber threats. It's an open-source threat intelligence platform that collects, stores, distributes, and shares cybersecurity information.
How does MISP's architecture facilitate threat intelligence sharing?
MISP's architecture facilitates threat intelligence sharing by incorporating elements such as events, feeds, groups, and users that work together to enable efficient collaboration and information exchange.
How can MISP be integrated with existing systems?
You can integrate MISP with existing systems using its REST API, accessible through the PyMISP library. Many security tools and platforms already offer pre-built integrations with MISP for a seamless transition.
What are some of the advanced features that MISP offers for in-depth analysis?
MISP offers advanced features such as event graph visualization, independent Python 3 modules, integration with galaxy clusters and CTI taxonomies, and support for various export formats, all of which facilitate in-depth analysis. These features enhance the overall quality of threat intelligence.
How does MISP ensure the security of shared intelligence?
MISP ensures the security of shared intelligence by using PGP, SSL certificates, cryptographic controls, and secure synchronization protocols, while aligning with international security communications standards. It also provides secure information transfer options, including air-gap exchange protocols for strict security environments.
Recorded Future for MISP
MISP is a cornerstone of cybersecurity, fostering global collaboration and intelligence sharing. Its robust features and vibrant community make it an essential tool for combating cybercrime and enhancing cyber defenses. Leverage this dynamic platform to transform your security operations.
Recorded Future enhances MISP by integrating real-time intelligence into your existing security systems. This integration helps analysts quickly detect and respond to threats by providing comprehensive, contextual intelligence from a mix of open source, dark web, and proprietary sources.
Operationalize and prioritize threat data effectively with our combined solution—book a demo today to see how you can improve situational awareness and accelerate your threat response.

Esteban is a seasoned security researcher and IT professional with over 20 years of experience, specializing in hardening systems and networks, leading blue team operations, and conducting thorough attack surface analysis to bolster cybersecurity defenses. He's also a skilled marketing expert, specializing in content strategy, technical SEO, and conversion rate optimization. His career includes roles as Security Researcher and Head of Marketing at SecurityTrails, before joining the team at Recorded Future.
Related
