Shedding Light on STTEAM
Researchers from Fidelis Security in February reported a newly identified cyber campaign dubbed STTEAM (PDF) found to be targeting oil and gas companies in the Middle East.
The Fidelis team provided in-depth analysis of the ASP Shell backdoors, specifically “Zehir ASP Shell” and “K-Shell/ZHC Shell 1.0/Aspx Shell,” used so far in the STTEAM campaign. We recommend it for our more technical readers.
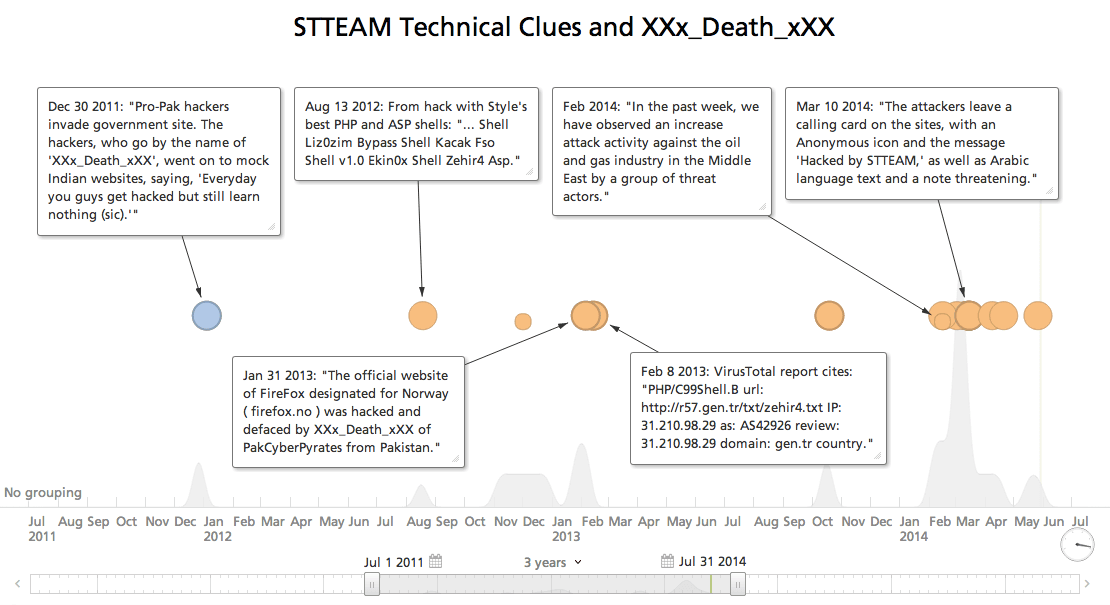
Web intelligence allows us to better understand the history of malware and known indicators of compromise. Even if modified for the STTEAM campaign, the Zehir4 ASP Shell has been available in some form since at least 2012.
Middle East technology website ITP.net recalls attacks on RasGas and Aramco during 2012 while noting that the STTEAM attacks thus far bear little resemblance to those attacks, which wiped large amounts of data from each company. Instead, the Zehir4 ASP shell has been used to “obtain system information, connect to SQL databases, list tables and execute commands, browse directories, perform file manipulations, and perform folder manipulations.”
Fidelis’ discovery of malicious backdoors being installed by STTEAM hackers following their defacement of websites significantly elevates the known capabilities several well-known threat actors. Website defacement might be disruptive to business and require the attention of PR and system admins, but the potential for data to be siphoned out of the enterprise makes this threat one to watch closely.

The report identifies “two persons going by the handle of XXx_Death_xXX and ZHC” as responsible although we believe that to actually be one individual and their group affiliation.
We find the alleged hackers XXx_Death_xXX and Zehir to be affiliated with well-known hacker groups. Respectively, they are associated with the pro-Pakistan ZCompany Hacking Crew and TurkHackTeam. Analyzing open source intelligence (OSINT) on those groups’ past activities shows the attacks reported by Fidelis to be a significant shift in capabilities as the two groups were typically associated with website defacements of political organizations.
This additional context on hacktivist methods and past targets based on their public pronouncements can serve as a complement to Fidelis’ technical analysis.
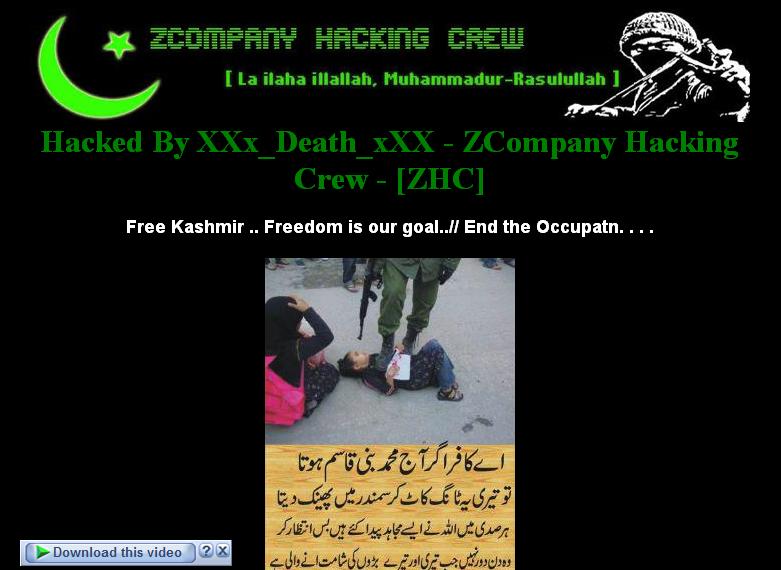
The above image shows a defacement claimed by the hacker XXx_Death_xXX during mid-2011. You’ll notice the tag ZHC used to describe the hacker’s affiliation with the ZCompany Hacking Crew. This leads us to believe the STTEAM campaign, which was attributed initially to two persons (XXx_Death_xXX and ZHC) to be a single hacker with the “ZHC” tag indicating that individual’s affiliation.
Looking back at the attacker’s nom de guerre, XXx_Death_xXX, as well as the the group ZHC we find a regular cause: advocacy for “Free Kashmir” and “Free Palestine”. Interestingly, the targeting of both individual and group has typically focused on political organizations rather than corporations. This includes past targeting of assets in the Middle East such as a website defacement of the Indian Passport and Visa Application Center in Bahrain.
They’ve not wholly ignored going after companies – websites of Fiat and Billabong have both been defaced – but targeting has been primarily focused on political opposition and regional media channels.
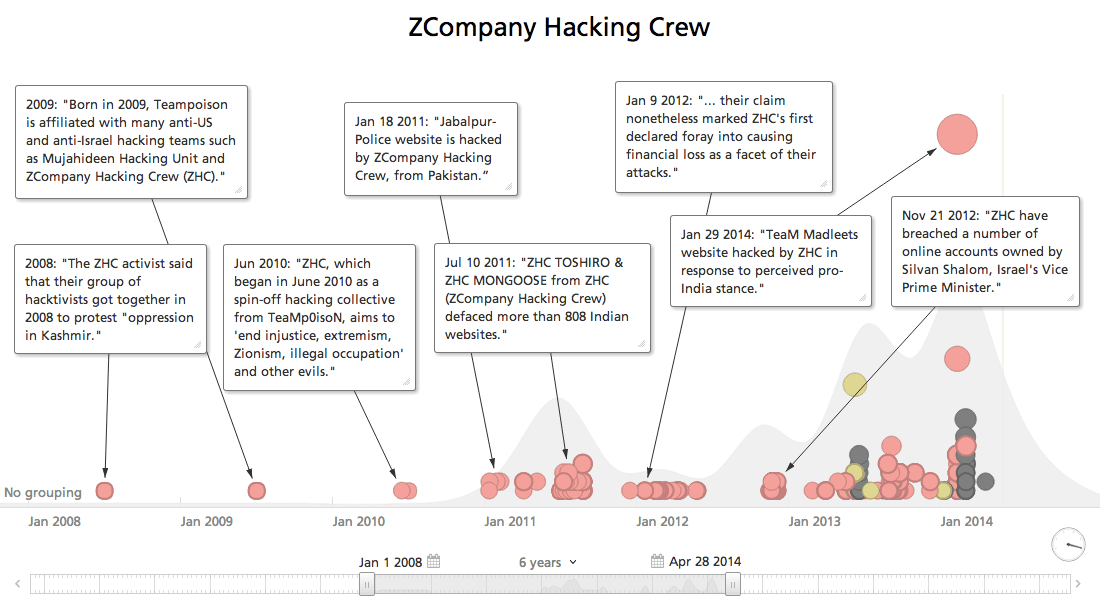
The fight over Kashmir remains a regional flashpoint outside of cyberspace. But the ZHC aims to raise awareness outside of the region through website defacement. At the beginning of 2013, ZHC_Hawk, who is a believed founding member of ZHC, gave an interview to The Hackers Post:
There are people around the world who haven’t even heard about Kashmir. Our defacing is a kind of raising awareness among people to fight for their rights and to support those who are fighting for their rights.
Similarly, hackers affiliated with the TurkHackTeam appear to typically be more focused on political causes rather than corporate espionage or d0xing.
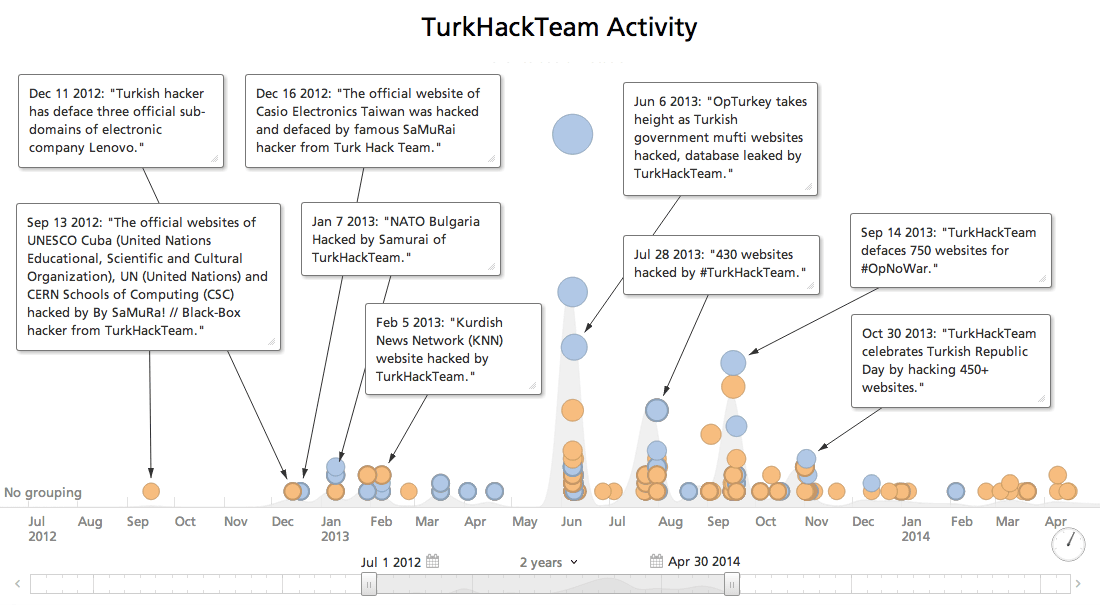
The elevated severity of these attackers’ goals might explain the relative quiet of both hackers and their collectives since the Fidelis report was published in February.
Recorded Future’s Intelligence Desk will continue to monitor this threat to energy organizations and political groups; this post will be updated if the backdoor tools surface elsewhere or these threat actors are found to have gone after new types of targets. Learn more about Recorded Future’s solutions for threat intelligence analysis.
Related