North Korea-Aligned TAG-71 Spoofs Financial Institutions in Asia and US

Insikt Group has discovered malicious cyber threat activity spoofing several financial institutions and venture capital firms in Japan, Vietnam, and the United States. The group responsible, referred to as Threat Activity Group 71 (TAG-71), has significant overlaps with the North Korean state-sponsored APT38. Between September 2022 and March 2023, Insikt Group discovered 74 domains and 6 malicious files associated with TAG-71's activities.
TAG-71 has previously been observed spoofing domains belonging to financial firms and cloud services in Japan, Taiwan, and the United States. In March 2022, Insikt Group identified 18 malicious servers tied to TAG-71, which were also linked to the publicly reported CryptoCore campaign. These servers were used for malware delivery, phishing, and command and control operations, often impersonating popular cloud services and cryptocurrency exchanges.
The North Korean government has a history of financially motivated intrusion campaigns, targeting cryptocurrency exchanges, commercial banks, and e-commerce payment systems worldwide. TAG-71's recent activities align with this pattern, indicating North Korea's ongoing efforts to generate funds while facing international sanctions. The spoofing of investment banking and venture capital firms poses risks such as exposure of sensitive information, legal consequences, disrupted negotiations, or damage to strategic investment portfolios.
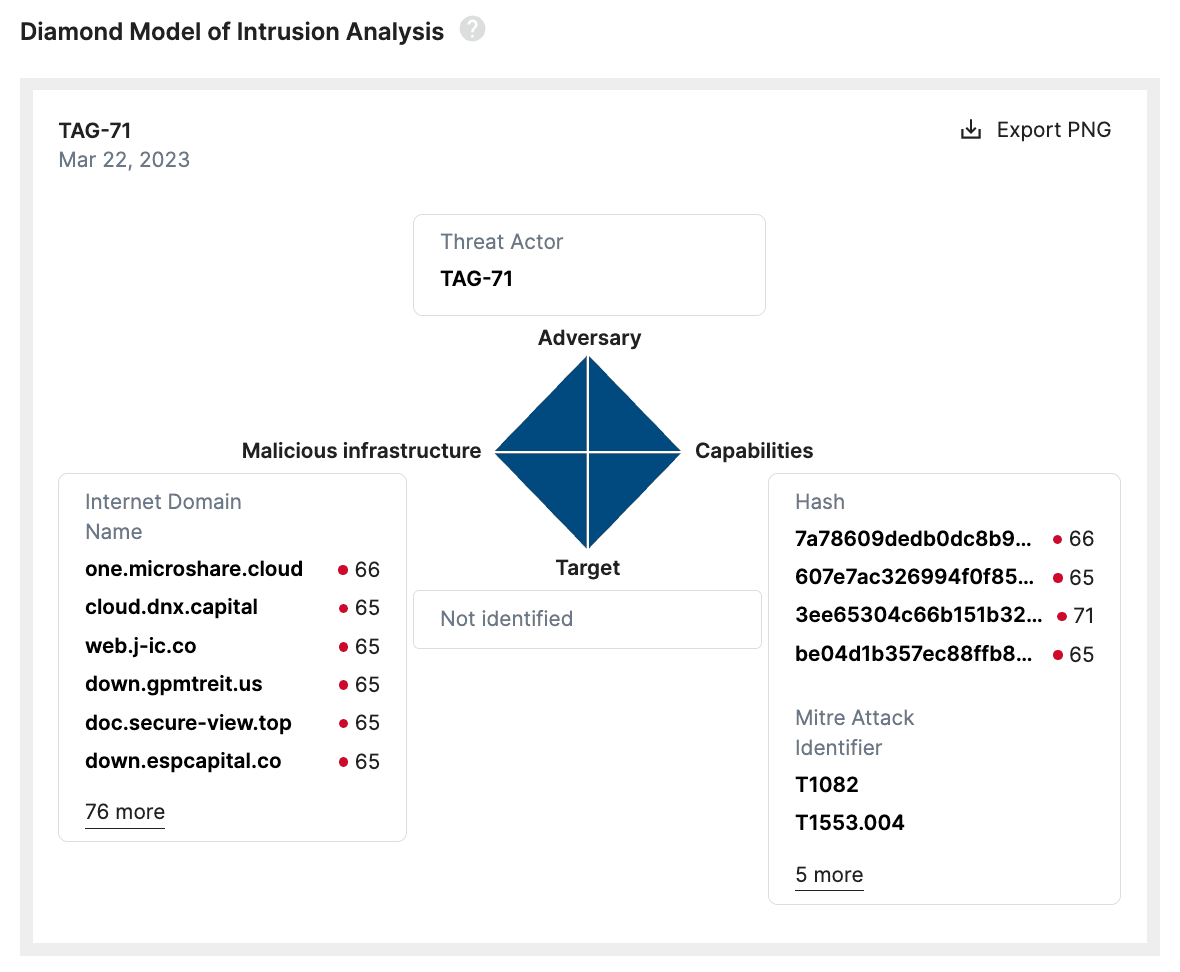 Select IOCs for TAG-71 mapped to the Diamond Model of Intrusion Analysis in the Recorded Future Intelligence Cloud
Select IOCs for TAG-71 mapped to the Diamond Model of Intrusion Analysis in the Recorded Future Intelligence Cloud
To mitigate TAG-71's activities, Insikt Group recommends configuring intrusion detection systems to block connections to the IP addresses and domains associated with the group. Clients of Recorded Future, Insikt Group's parent company, should also block command and control servers logged in the Command and Control Security Control Feed. Additionally, organizations should enforce security awareness among employees and customers to recognize phishing attempts, suspicious domains, and fraudulent documents. Monitoring for domain abuse and initiating takedowns of fraudulent domains through Recorded Future's Brand Intelligence module is also advised.
Overall, TAG-71's campaign aligns with North Korean state-sponsored threat actors' past activities, posing risks to financial and investment firms and their customers. Implementing the recommended mitigation measures can help protect organizations from these malicious activities.
To read the entire analysis with endnotes, click here to download the report as a PDF.
Related
