GRU's BlueDelta Targets Key Networks in Europe with Multi-Phase Espionage Campaigns

Insikt Group tracks the evolutions of GRU's BlueDelta operational infrastructure, targeting networks across Europe with information-stealing Headlace malware and credential-harvesting web pages. BlueDelta deployed Headlace infrastructure in three distinct phases from April to December 2023, using phishing, compromised internet services, and living off the land binaries to extract intelligence. Credential harvesting pages targeted Ukraine's Ministry of Defence, European transportation infrastructures, and an Azerbaijani think tank, reflecting a broader Russian strategy to influence regional and military dynamics.
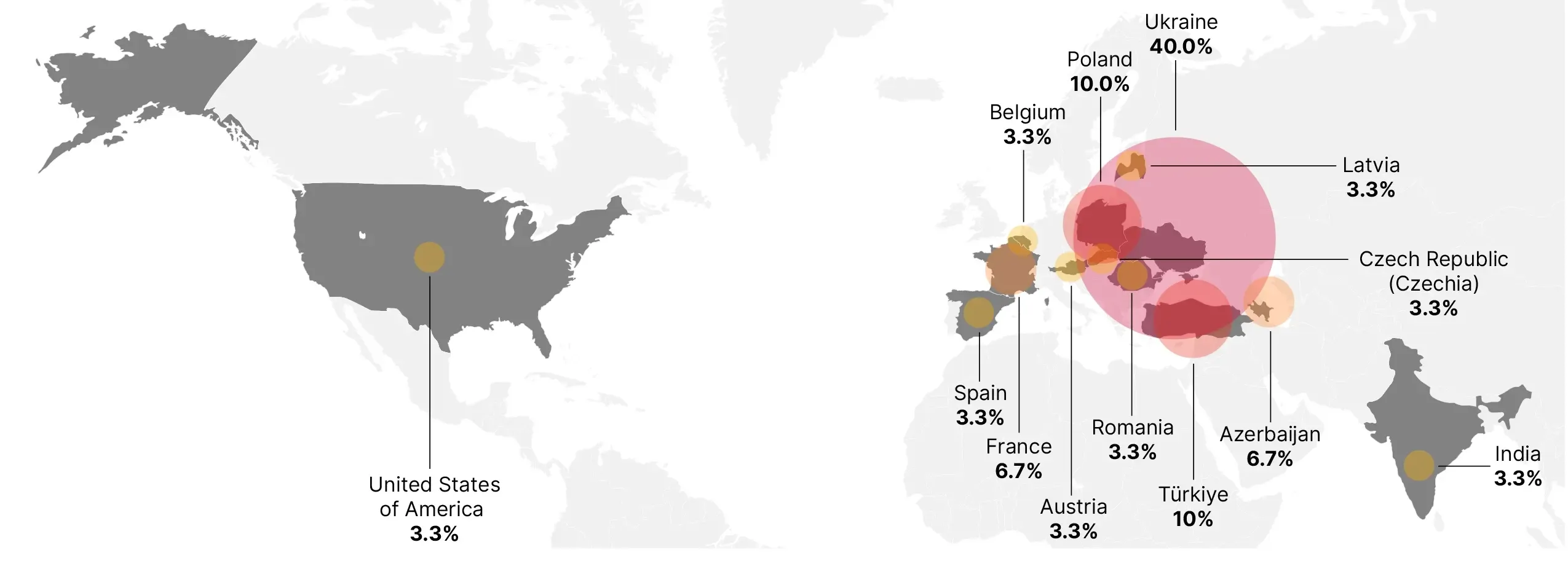
GRU's BlueDelta Espionage Campaigns Across Europe
Russia’s strategic military intelligence unit, the GRU, continues to conduct sophisticated cyber-espionage operations as geopolitical tensions persist. Insikt Group’s latest findings highlight the actions of BlueDelta, which has systematically targeted key networks across Europe using custom malware and credential harvesting.
From April to December 2023, BlueDelta deployed Headlace malware in three distinct phases using geofencing techniques to target networks throughout Europe with a heavy focus on Ukraine. Headlace malware is deployed using phishing emails, sometimes mimicking legitimate communications to increase effectiveness. BlueDelta exploits legitimate internet services (LIS) and living off-the-land binaries (LOLBins), further disguising their operations within regular network traffic. This sophistication makes detection difficult, increasing BlueDelta’s success when compromising networks.
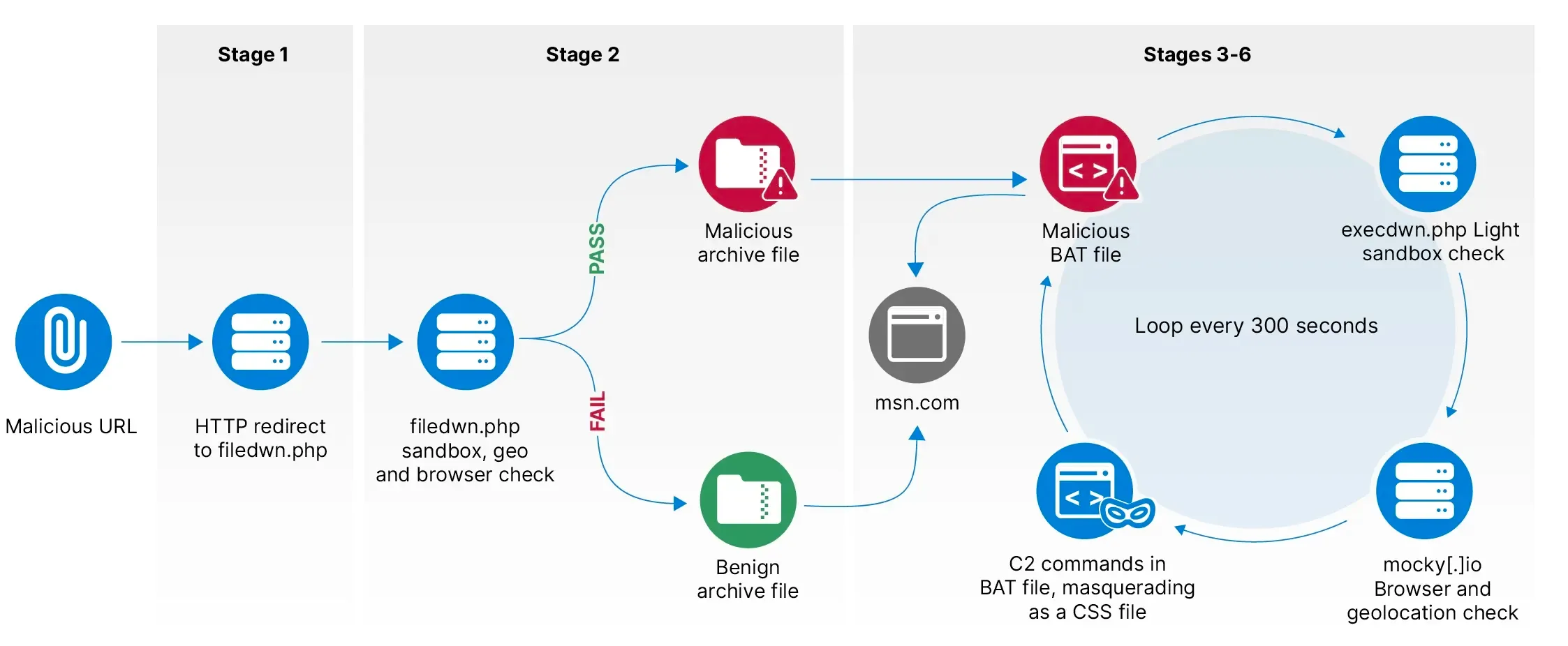
One notable aspect of BlueDelta’s operations is its focus on credential harvesting pages. Targeting services like Yahoo and UKR[.]net, it employs advanced functions capable of relaying two-factor authentication and CAPTCHA challenges. Recent operations have targeted the Ukrainian Ministry of Defence, Ukrainian weapons import and export companies, European railway infrastructure, and a think tank based in Azerbaijan.
Successfully infiltrating networks associated with Ukraine’s Ministry of Defence and European railway systems could allow BlueDelta to gather intelligence that potentially shapes battlefield tactics and broader military strategies. Moreover, BlueDelta’s interest in the Azerbaijan Center for Economic and Social Development suggests an agenda to understand and possibly influence regional policies.
For organizations within government, military, defense, and related sectors, the rise of BlueDelta’s activities is a call to bolster cybersecurity measures: prioritizing the detection of sophisticated phishing attempts, restricting access to non-essential internet services, and enhancing surveillance of critical network infrastructure. Continuous cybersecurity training to recognize and respond to advanced threats is essential to defend against such state-level adversaries.
To read the entire analysis, click here to download the report as a PDF.
Related