When Access Goes Wrong: The Dangers of Exposed Login Panels

The remarkable growth of web technologies has undeniably created enthralling opportunities for businesses to engage with customers and sustain a thriving remote workforce. But with this expansion came the need for added simplicity in supporting the dizzying array of services the modern internet had to offer. For instance, to many in the IT operations stage, the arrival of web-based controls and admin consoles meant a more straightforward and consistent way to support the demand for round-the-clock administration without the much-dreaded element of locality.
Security professionals, however, tasked with keeping a watchful eye on an already divergent attack surface, cringe at the possibility of an unsecured admin panel lurking in an organization's public-facing digital inventory, waiting to be discovered and exploited by cybercriminals at any time. This blog post reveals the hidden—and not-so-hidden—dangers of these weak or unsecured assets, the security implications of neglecting their adequate protection, and the role of Attack Surface Intelligence in mitigating these threats. Let's dive in.
Perils of Exposed Admin Panels
Web-based admin panels and similar examples fall well within the rubric of remote access connectivity. This terminology entered the lexicon on the heels of now-almost-forgotten siblings like remote serial consoles, used to monitor, manage, and troubleshoot distant infrastructure, giving administrators a virtual presence across many disparate systems. In a prominent display of usability, they retained access to log information and other essential performance indicators even through systemic network outages.
Nowadays, companies can rapidly construct robust and intuitive websites and mobile applications, enhancing the customer experience and driving greater engagement. Moreover, the advent of cloud computing, machine learning, and artificial intelligence has empowered businesses to automate different processes, improving efficiency and scalability.
As influential as these technologies have been, the so-called digital transformation era has placed further demands on the remote admin front. For example, hardware is no longer the sole recipient of remote access solutions. What started as a trickle only a few years ago with high-end devices is now a steady stream of entire software-based platforms, applications, and portals requiring this kind of control, opening the door to more and more vulnerabilities as other frameworks come online.
To recall a subset of the dangers, we need only to look at some of the consequences associated with unsecured admin-type logins:
- Unauthorized access: Allowing unprivileged parties to access and manipulate sensitive information, including user data, financial transactions, and other confidential material.
- Malware injection: The potential for threat actors to host malicious code on a compromised website or application, extending their reach to unsuspecting visitors.
- Defacement: An attacker's ability to modify a website's appearance or content, causing reputational damage to the organization and significant financial losses.
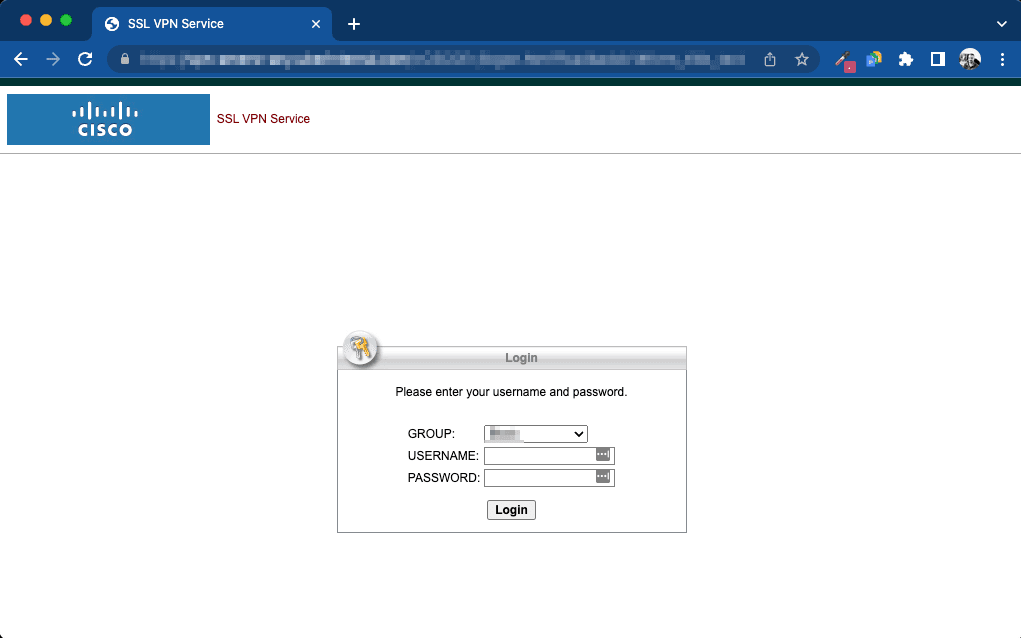 An exposed Cisco ASA VPN login interface detected by Recorded Future’s Attack Surface Intelligence
An exposed Cisco ASA VPN login interface detected by Recorded Future’s Attack Surface Intelligence
Gaining access to a web-based admin interface could also be as simple as scanning for the existence of common paths, such as /login, /admin, or /administrator. Alternatively, attackers may use tools to brute force server content or examine source code for links to administrator functionality. Server and application documentation may also reveal information on default configurations and passwords—even prior data breaches may be the basis for future attempts.
Top software products that shouldn't have admin panels exposed
From a visibility perspective, the timely identification of vulnerable infrastructure—framed by the onerous idea that exposed admin panels convey—is pivotal to maintaining a secure digital environment. The challenge of keeping up with an increasing number of endpoints makes this activity all the more complex.
Enter Attack Surface Intelligence.
Whether it's a web-based admin panel or any external risk derivative, Recorded Future’s Attack Surface Intelligence can identify blind spots, misconfigurations, and vulnerabilities in an organization's infrastructure that traditional monitoring tools may overlook. For example, as of today, 37% of all our scanned projects show some form of publicly-visible admin panel for both VPN and Firewall-based enterprise software. In short, Attack Surface Intelligence's detection capabilities can provide organizations with the necessary knowledge and insight to swiftly and efficiently respond to potential cyber threats, even those arising from exposed admin panels, irrespective of the platform type or classification.
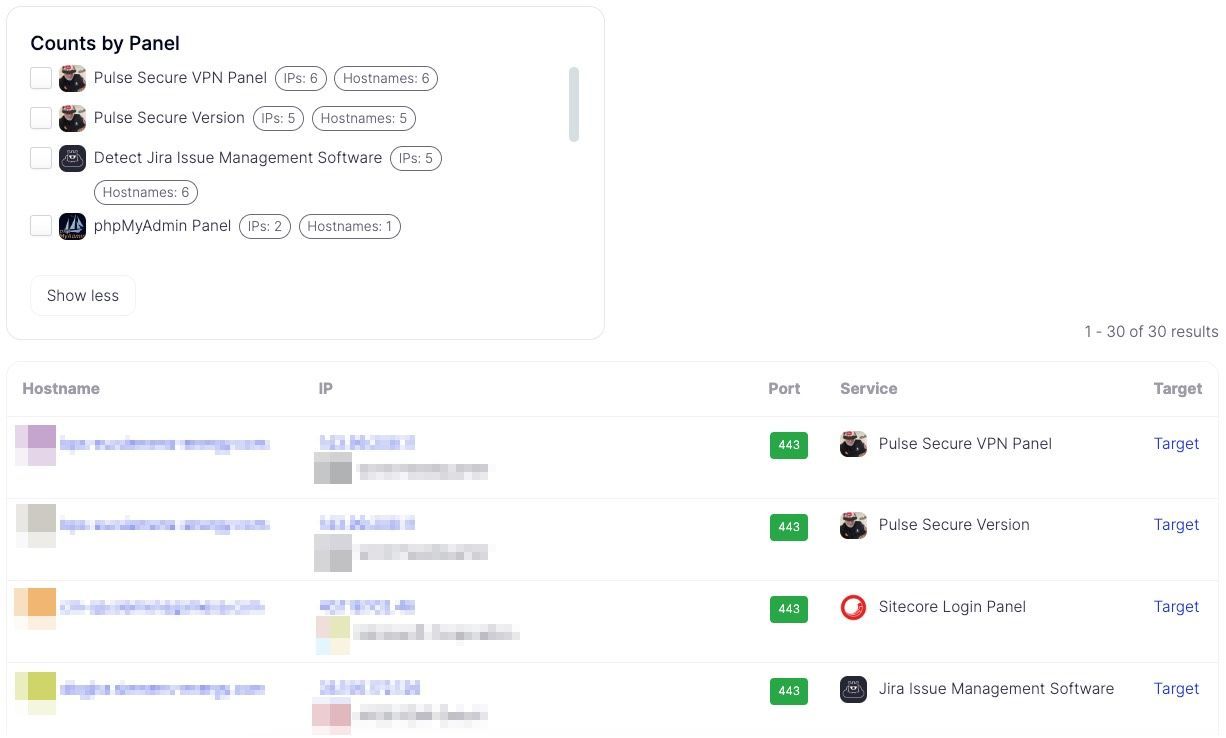 Recorded Future’s Attack Surface Intelligence ‘Admin Panels’ showcasing enterprise software panels exposed to the public.
Recorded Future’s Attack Surface Intelligence ‘Admin Panels’ showcasing enterprise software panels exposed to the public.
Looking at the landscape, however, most people agree that the criticality level is directly proportional to the exposed application type. For example, a publicly-accessible ICS (Industrial Control Systems) administrative panel is orders of magnitude more dangerous (in terms of risk exposure) than, say, a Magento-based e-commerce website with only a handful of customers. Similarly, we cannot equate admin access to a WordPress site to that of a security platform or resource holding sensitive company records.
Networking/Firewalls
One must understand that exposing administrative panels or management interfaces for firewalls and networking devices is a reckless and foolhardy decision tantamount to handing over the keys to the castle to all sorts of malicious actors. Such a careless action could easily compromise the entire network, with attackers able to exploit vulnerabilities in these systems to gain access and carry out further malicious activities. Examples of such products that involve some sort of web-based admin interface include PaloAlto Networks GlobalProtect, IBM Security Access Manager, and Aruba Networks ClearPass Policy Manager.
VPNs
One plausible reason for not exposing a VPN admin panel to the internet in the first place is that they are a frequent target for scanners looking for default settings. In other words, unfettered access to an enterprise network through an unsecured VPN web-based admin panel often results from inadvertently leaving default user credentials on, inevitably bringing about potential attackers. Examples of VPNs exhibiting some form of admin interface include FatPipe IPVPN®, SonicWall Virtual Office SSL VPN, and Cisco ASA VPN.
Enterprise Software
As is often the case, enterprise software serves specific business needs or user groups. In this case, an exposed admin panel could give unauthorized users access to sensitive information or the ability to make damaging changes to the software or system. Some notable examples include Atlassian Crowd, Splunk Enterprise, and Oracle Peoplesoft Enterprise.
DevOps
The cultural (agile) shift represented by DevOps is also known for bringing about a host of traditional security risks, including information leakage or a general lack of control over who can access your system or data. Unsafe DevOps is also associated with the exposure of source code and other valuable company resources otherwise not advertised via production systems. Some DevOps technologies include GitHub Enterprise, RedHat Satellite, and Argo CD.
ICS/OT
ICS (Industrial Control Systems) and its more extensive OT (Operational Technology) counterpart are the lifelines of the industrial and manufacturing conglomerates. As such, their operational integrity is pivotal to the proper functioning of entire governments and societies—in essence, exposing ICS technology to the internet without proper oversight can be catastrophic (and life-threatening) in most cases. These systems include Tectuus SCADA Monitor, SCS Landfill Remote Monitoring Control, and Honeywell XL Web Controller.
Email Services
Disabling or preventing external access to email functions that require administrative privileges is not only advisable but required. For example, MS Exchange Admin Centers are notoriously known for being highly vulnerable to a series of critical 0-days, exposing any web-based functionality to an even greater danger of being targeted and exploited. Other platforms include Horde, SquirrelMail, and Zimbra Web Client.
Databases
Exposing web admin database panels can be a hazardous enterprise, as it can lead to unauthorized access using methods such as SQL injection or brute force attempts on weak login credentials. Furthermore, unauthorized access via web admin panels can allow attackers to modify, delete or insert new data into the database with little to no effort. The best examples in this area include phpMyAdmin, Grafana, and MongoDB Ops Manager.
Web Hosting
There is no shortage of web hosting admin-related infrastructure exposed to the internet, typically due to poor security practices hoisted by a backdrop of equally-poor coding techniques and vulnerabilities. There are also plenty of publicly available manuals and documentation to find helpful information on which to pivot to carry out additional attacks. These technologies include WHM cPanel, DirectAdmin, and Openvz Web, just to name a few examples.
Mitigation techniques
As hinted, web-based admin interfaces are frequently beset by insufficient security and hardening measures, resulting in unnecessary exposure to risk—a massive concern since a single breach could potentially expose hundreds, if not thousands, of additional targets. And although some exploits embrace a level of sophistication only achievable by more advanced threat actors, the reality is that most vulnerabilities can be easily handled in-house by applying any corresponding patches.
Additional measures or mitigation techniques may include:
- Requiring VPN access or only allowing internal IPs to access admin functionality
- Using server-based IP allow/deny rules (works with Nginx, Apache, and many others)
- Setting up HTTP Auth (not really recommended, but better than nothing)
- Using a password manager to avoid sharing and typing your passwords
In addition to these technical measures, educating users about good security practices is essential. Most importantly, having a persistent view of digital assets is pivotal for enabling your organization to detect any exposed admin panels, and that’s where Attack Surface Intelligence comes in.
Uncover exposed admin panels and other attack surface blind spots by booking a demo today.
Related