Reduce Risk in Vulnerability Management With the Intelligence Goals Library
Depending on your security role, threat intelligence can look very different, both in form and content. But no matter what it looks like, it’s ultimately only useful when it provides actionable context. Threat intelligence alerts need to be timely, have transparent sourcing, and reliably update you on events you need to know about and not distract you with events you don’t. But manually setting up alerts that meet these criteria can take a lot of time, effort, and experience.
That’s where Recorded Future’s Intelligence Goals Library comes in. It has all the use cases every security role needs, preconfigured and in one place, which makes it simple to search and activate new or relevant alerts, or deactivate them if they’re no longer relevant to your organization.
Intelligence Goals in the library are grouped into seven main security roles — threat analysis, incident response, vulnerability management, security operations, risk analysis, fraud, and security leadership — and there are over one hundred use cases within the Intelligence Goals.
Activating a use case will send you real-time alerts relevant to your organization, including transparency into sources, helping you quickly understand why the alert was sent. Because they’re preconfigured and automated, the focus stays on intelligence requirements already aligned with established best practices rather than the granular details of setting up alerts and custom queries.
And Watch Lists, which are custom, configurable lists of your organization’s assets, are a central point to customize what the alerts are monitoring specific to your organization.
In this blog post, we’ll explore the vulnerability management role category in the Intelligence Goals Library, looking at the different Intelligence Goals and their use cases within it.
Intelligence Goals for Vulnerability Management
For vulnerability management, Intelligence Goals help identify and alert on vulnerabilities directly related to your organization, all in real time (even before a CVSS score is assigned).
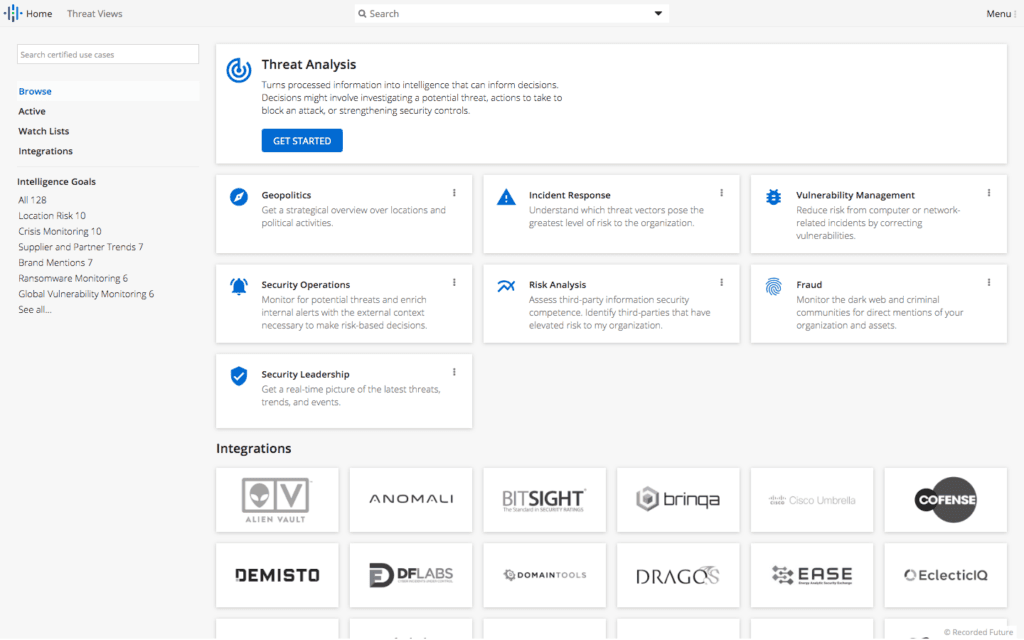
The Intelligence Goals Library home screen.
The goal of vulnerability management is to reduce risk by making your environment more secure. That’s not easy when new vulnerabilities emerge all the time and patching them is time consuming and often results in downtime.
With limited resources, it’s impossible to try to manage vulnerabilities by patching all of them, all the time. Instead, vulnerability management teams need to prioritize which vulnerabilities present the biggest threat, which can wait, and which can be safely ignored. It’s threat intelligence that provides the context needed to perform this kind of assessment.
We’ve compared vulnerability management to fighting fires before — they’re both races against the clock, they both deal with systems that rapidly change and evolve, and they both have the potential for devastating damage if not taken seriously. Responding to an active security incident might be more akin to the act of fighting a fire itself, but prevention is just as important, and that’s what vulnerability management is all about. The sheer number of extant vulnerabilities and threat actors looking to exploit them are like fires constantly burning around us, often making the best course of action figuring out how to avoid getting set ablaze.
Doing so effectively takes knowing when new vulnerabilities that affect you appear and when they’re being exploited. The Intelligence Goals Library provides just that by having all the alerts you’ll need to effectively identify vulnerabilities already set up as use cases. These use cases are automatically updated whenever new sources are added, meaning it no longer takes an experienced analyst to set up, configure, and reassess alerts — it’s as simple as turning them on or off in the Intelligence Goals Library.
We’ll look at a few use cases within the Intelligence Goals present in the vulnerability management section of the Library to explore how exactly they help reduce risk.
Vulnerability Management Intelligence Goals and Their Use Cases
There are nine different Intelligence Goals within the vulnerability management role section of the Intelligence Goals Library, which include nearly 40 use cases. We’ll dive into a few examples of use cases within those goals.
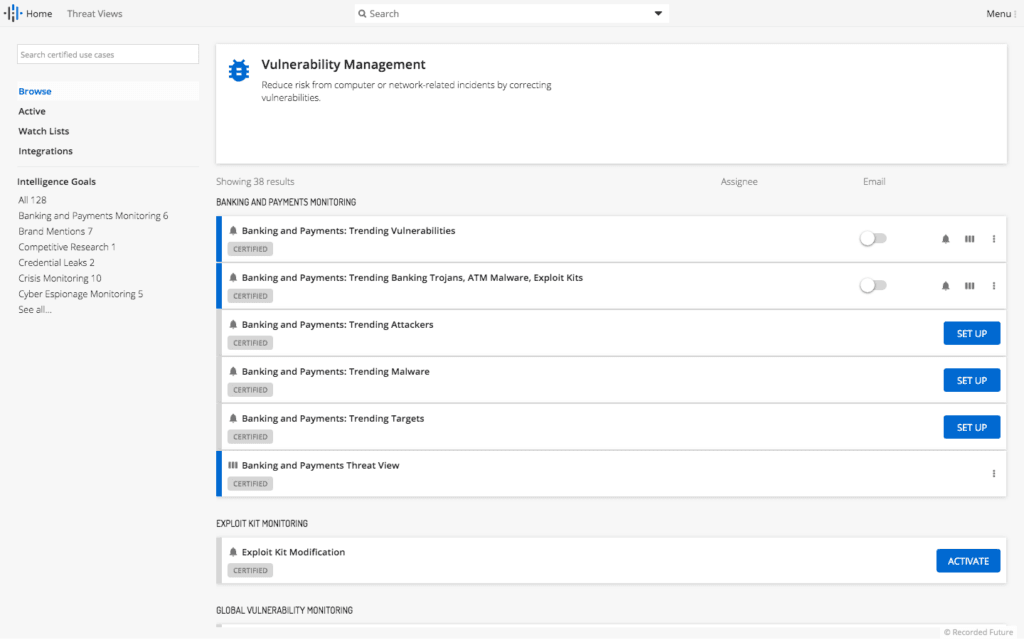
The vulnerability management category within the Intelligence Goals Library.
1. Global Vulnerability Monitoring
Rely on use cases within this category to set up alerts around new exploit chatter, information recently linked to pentest tools or malware, new vulnerabilities that haven’t been classified by the NVD yet, and more. Similar kinds of alerts can also be customized based on what you put in your Watch Lists so that you always get relevant updates.
New vulnerabilities are usually exploited within a matter of weeks, if they’re exploited at all, and the NVD is not always quick enough classifying and publicly releasing information on new vulnerabilities for affected parties to respond in time. These kinds of alerts help teams responsible for vulnerability management stay aware of the threat landscape in real time.
2. ICS/SCADA Malware Tracking
Industrial control systems present a unique security environment with its own set of challenges. Small changes in these environments could have cascading effects for systems that control essential infrastructure, and many of them rely on legacy software and hardware. That makes the task of updating and patching these systems more challenging than the usual IT environments — one that takes a lot more experience and caution.
Use cases in this category make threat intelligence alerting for industrial control systems far more accessible. Alerts in this category will keep you updated on trending ICS malware, RATs, attackers, targets, and more.
3. Ransomware Monitoring
Like we’ve mentioned before, ransomware will continue to trend as a popular method of attack in 2019. The use cases in this category set up alerting around ransomware topics like trending exploit kits, targeted software, or the addresses of payment sites and command and control (C2) domains associated with ransomware attacks. Transparency into these threats makes it much easier to know which vulnerabilities to prioritize patching.
Learn More
Last week, we also looked at how the Intelligence Goals Library helps with security operations. We’ll look at risk analysis next.
Do you want to see firsthand how the Intelligence Goals Library makes threat intelligence easy? Take a tour now.
Related
