Who’s Got Your Data? 2 Steps to Managing Third-Party Risk (Infographic)
You shake hands with new business partners to seal the deal — and end up with their germs. Third parties help our teams grow, but they also introduce new risks.
That’s why we developed our Third-Party Risk module, a powerful add-on to our core platform. It’ll help you know when to wash your hands (and when to stay home altogether).
Just why, exactly, has doing business with other organizations become more dangerous lately, and what are the specific risks? We’ve put together an infographic below to highlight the key facts and statistics you need to know about third-party risk.
Quantifying Third-Party Risk With Threat Intelligence
But first, the “why” — what’s changed in the last few years? The answer has to do with the process of digital transformation that many leading companies across industries are undergoing.
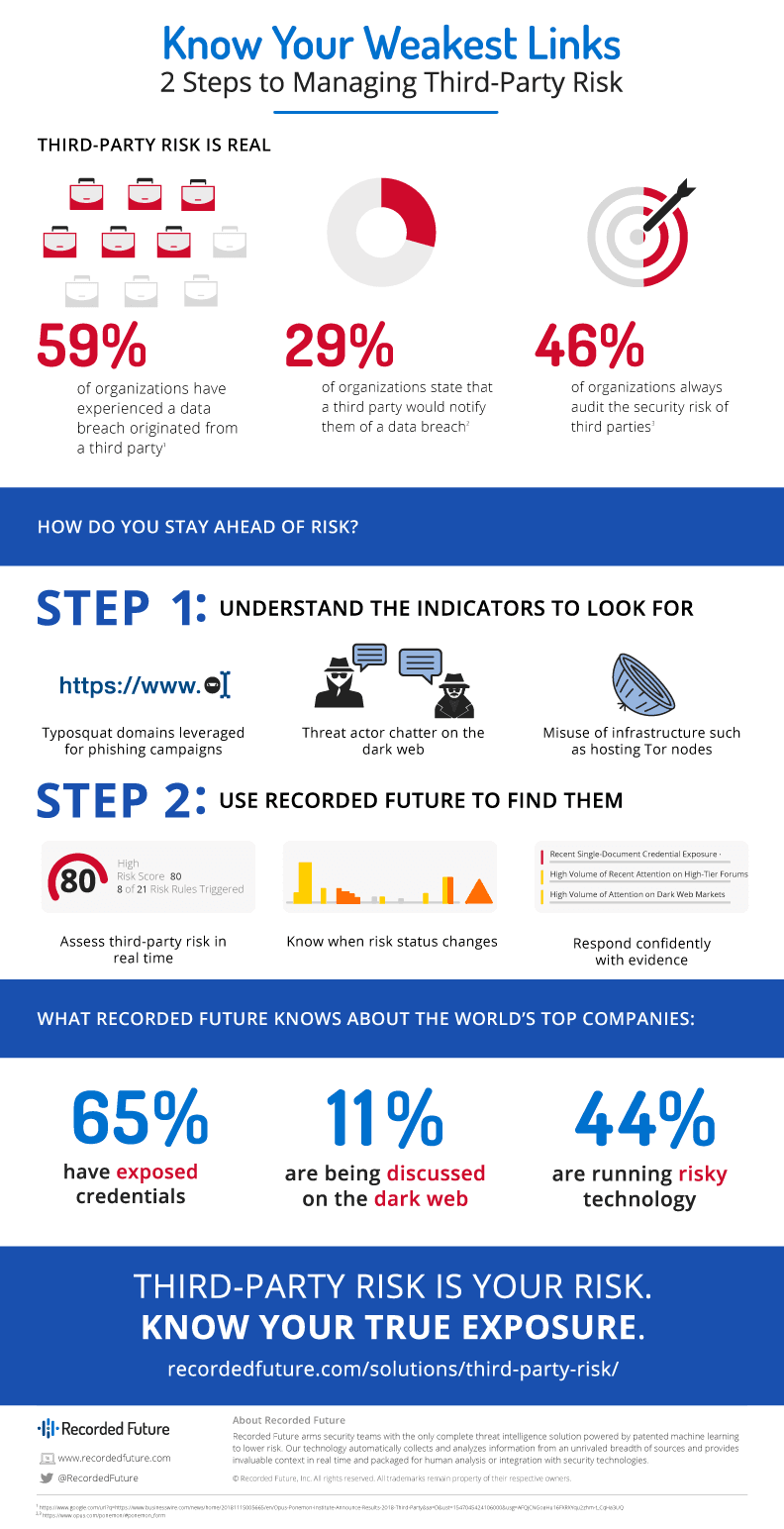
Countless organizations are transforming the way they do business through digital processes. They’re moving data from internal networks to the cloud, and gathering more information than ever before. That data has more value, too. Financial statements, private health records, industrial control data, and increasingly detailed and nuanced consumer statistics are all stored off-site.
Making data easier to collect, store, and analyze is certainly transforming many industries for the better, providing the raw material that’s undergirding revolutions in fields like statistical analysis and machine learning. But this free flow of information comes with a price. It means that to assess the risk of our own organization, we have to consider the security of our partners, vendors, and other third parties as well.
Threat intelligence is one way to do just that. It can provide transparency into the threat environments of the third parties you work with, providing real-time alerts on threats and changes to their risks and giving you the context you need to evaluate your relationships.
Get More Information on Third-Party Risk
In a recent report, ESG examined the most common third-party risk management practices employed today and determined that many of the current processes used are lagging behind security requirements. Many groups rely on static assessments of risk like financial audits and security certificate verifications — important parts of determining risk, but lacking any information on what threats are actually out there.
The report also details further how Recorded Future’s real-time threat intelligence provides a critical supplement for any security teams looking to monitor third-party risk, so download your complimentary copy today.
Related
