3 Malware Trends You Need to Know About
I can remember the first time I learned about a computer virus. I can even remember my first encounter with one.
Sure they were irritating, got in the way of playing Solitaire or Hearts, but jump 20 years ahead to the present and it seems the domain of malicious software, or malware for short, is as much a common thread throughout the online landscape as is checking one’s e-mail.
(Which could very well lead to such an infection if you’re not careful.)
This article is not about how to stay safe from such cyber attacks, but rather a look into the consistent rise in use, sophistication, and spread of such digital diseases.
Malware comes in many flavors and variants. From backdoor files or trojans, to phishing and spear-phishing e-mail campaigns, to the ever so popular and relatively new playground for malware authors: mobile operating system platforms.
Must-Know Malware Trends
To run down the list of the heavy hitters over the past few years would be enough to fill a small library. I want to review three of the biggies that are most certainly cementing their presence. In short, this analysis will look at malware trends; including inception, infection, variations, and destruction as they progress through the net and into the lives of so many of us.
1. The Citadel Trojan
The Citadel Trojan, and its most recent variation, Citadel Rain, has been a widely discussed and tracked piece of malware. Following the heritage of banking based trojans, its roots stem from the Zeus lineage of malware. While its deployment in the wild has mostly been discovered in Western Europe, due to the fact of it targeting banking information and it’s relatively smaller footprint in later variants, the assumption of it being adopted as it morphs and adapts is one that can be considered very likely.
While it cannot be said with 100% accuracy, if we take a look at the timeline graphic between 2011 and 2013, there appears to be a concentration during the middle months of each year. One assumption could be made since this malware goes after financials, this timespan does have a relationship connection to travel, end of work seasons, high spending of consumers. Perhaps it is because people are on vacation, away from their homes.
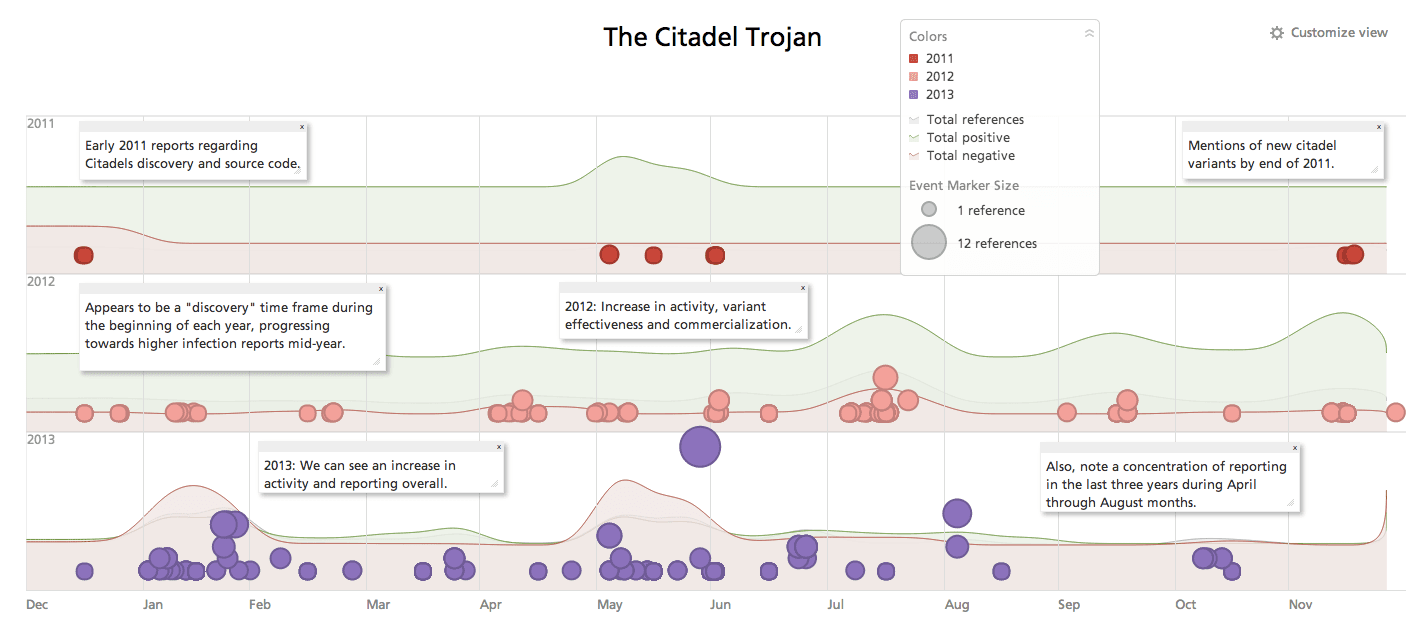
Or maybe they open an e-mail and inevitably check their bank accounts while abroad from an unsafe network. If the assumption holds merit, it could be plausible a resurgence will be seen come mid-2014, as well as a speculation of a more wide-spread contamination area.
Since the rediscovery of variants in the wild during 2013, one of the key features is how it appears to be localizing the credentials it harvests from victims. In a quote from Etay Maor, trusteer fraud prevention solutions manager, “They have a different way of storing data and have built databases for regions. That makes me think they’re going to sell the information rather than use it,” Maor said.
Localized credentials, for example, have more value than a scattered list of usernames and passwords. “For people who sell credentials, it’s a big difference to say they have 100 Italian credentials. For example, it doesn’t help to have American account information if you’re working in Italy. You can use it, but you need an accomplice who knows the local rules.”
Maors opinion derives from seeing a rather small indication of black market sales. While other popular malware strains “fly off the shelves” so to speak, modern Citadel kits appear to indicate the authors are holding back from an “everything must go” attitude. One could discern from that, the intention would therefore be to keep business afloat, mitigate its use through purchase thus potentially adding length to its survival in the wild.
Mobile Malware on the Rise
While not one specific piece of malware, attacks on the mobile platforms such as iOS and Android are steadily increasing. Let’s face it, many people turn to their phones which essentially can do a lot of tasks one would normally do from a PC or laptop, which draws the attention from malware authors.
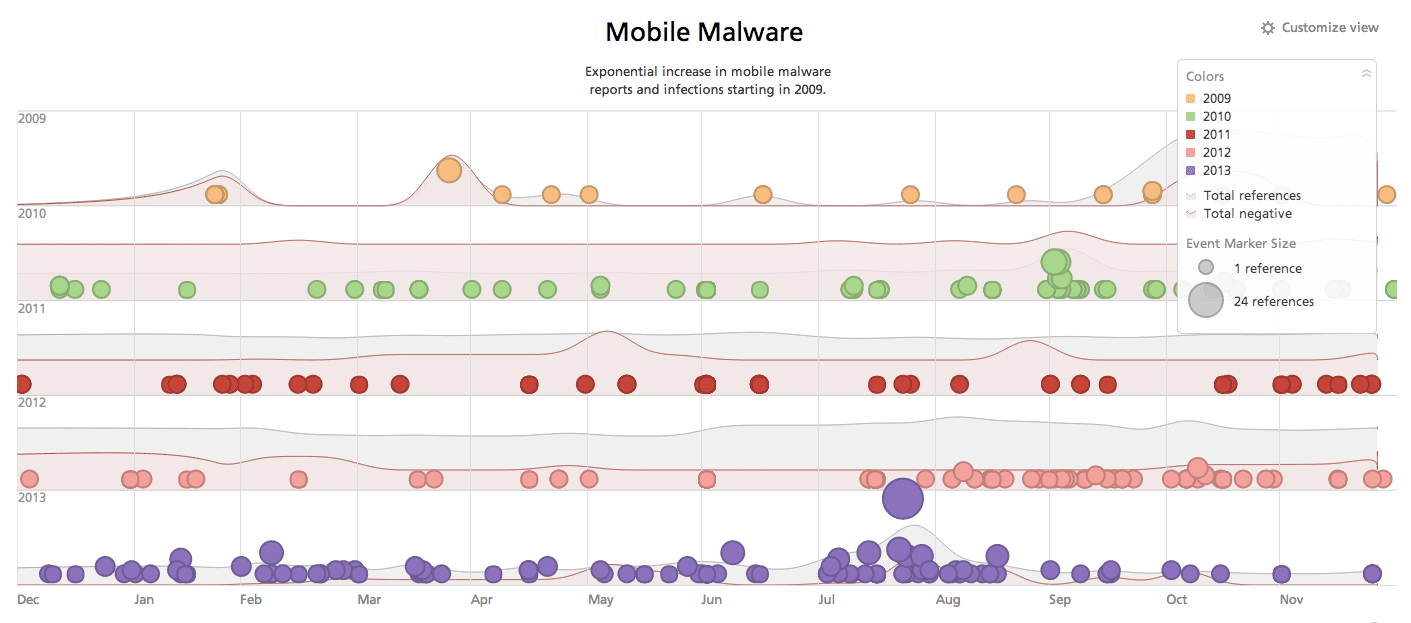
“Macs have no viruses.” Remember when people used to say that? Well, despite that being untrue even in those times, we know without argument they do. One reason for the increase in OSX-based malware design was the increase in usership. Hence, the reality that draws malware designers to mobile devices is the same. We all have one, we all use them, we are all at risk with them.
Sadly, when it comes to mobile malware specifically, one of the means attackers use to spread infection is through the medium we get our applications from. The Google Play Store and App Store from Apple have failed repeatedly to thoroughly check what is being offered.
Another popular mechanism is through SMS. Yes that’s right, text messages.
SMS spam is big business, and attackers who spend time understanding social engineering and craftsmanship for phishing style text messages, get what they would consider a successful “click-through” rate. As a result, the last two malware epidemics we’ll review deal with mobile malware.
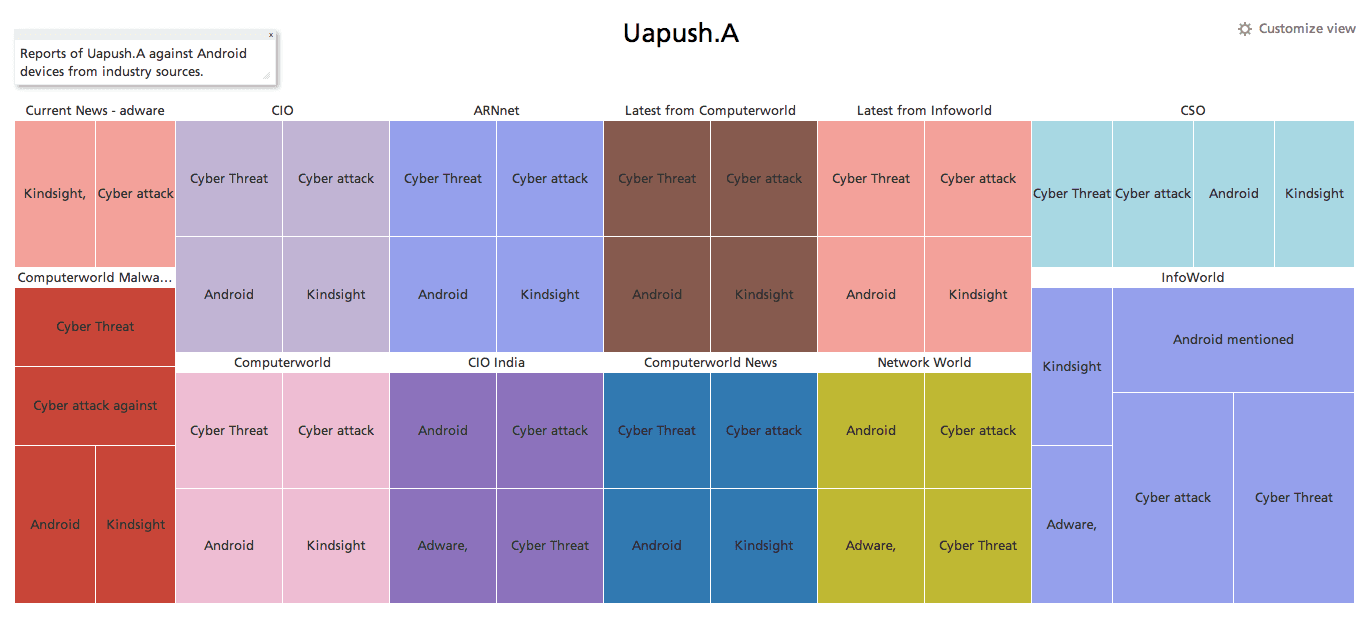
2. Uapush.A
In 2013, one of the most prevalent Android-based malware pieces was the Uapush.A adware trojan. According to Symantec, it was first discovered in March 2013. It operates by infecting users through backdoor apps which then sends premium SMS messages (usually during the night) and harvests information off the infected device.
Since it is considered adware, meaning the infection operates by using a form of unethical marketing and spam, its ability to damage the device or severely affect the user’s financial or personal information is relatively low.
However, given signatures were made to combat this threat around April 2013, and the infection climb by July 2013 was incredibly large, it is safe to assume users without proper security mechanisms on their devices such as a firewall, SMS protection and anti-malware apps – all from recognized vendors mind you – are still at risk for infection.
3. ObadH
For another look at Android malware, its debatable Obad, otherwise known technically as Backdoor.AndroidOS.Obad.a, is perhaps the most vicious seen yet. While it includes the ever so popular technique of service abuse, meaning it sends premium SMS messages against the users consent, it shows sophistication methods similar to malware one would normally see on a Windows operating system.
Obad, not only abuses the SMS feature, but due to the permissions it is granted upon installation on the device it also downloads other forms of malware and can then distribute them via bluetooth to neighboring devices, as well as perform console based commands through the console remotely.
Obad goes for administrator privileges on the device which means two things.
For Android users who do not root their phone, the malware should not be able to proceed in terms of privileges past the point of “device administrator.” For users who do root their phone, well sorry to say, but this malware does have in its command list the instructions to gain total root privileges.
Related