Building a Comprehensive Open Source Record on Malware

We recently launched Recorded Future Cyber to help analysts monitor the pulse of information security events reported on the web. Behind the analytic and visualization components is a detailed ontology of about 12,000 malware street names.
The scope of this ontology grows daily, and reporting on malware from hundreds of thousands of open web sources can be investigated using Recorded Future.
We’ve scaffolded the data in a way that allows for both threat intelligence research on specific malware as well as monitoring and analysis of entire malware categories. How does this work?
Here are two examples: open source information on Android.Enesoluty would be returned through a broad query in Recorded Future on “Trojans”; similarly, Multiboot.me would be represented in queries for information on “Botnets.”
Our malware ontology includes both specific street names, categories of malware like Trojan, and categories of exploits like XSS and SQLi. This structure enables analysts to complete a variety of “big question” threat intelligence tasks in short order.
Quickly Summarize Malware Targets
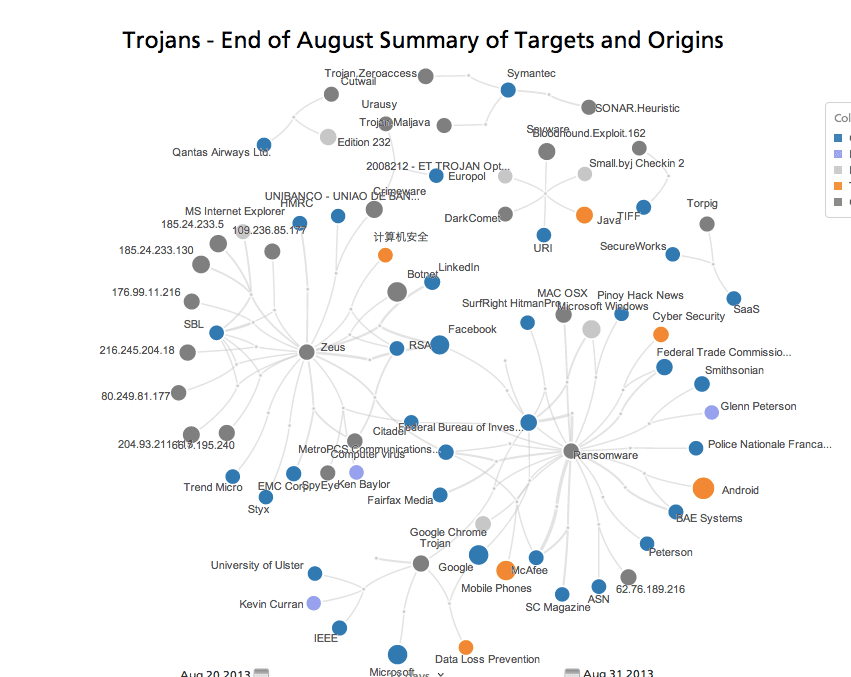
Click the image above for an interactive view.
The above network shows entities mentioned with malware categorized as a “Trojan” during two weeks in August 2013. You’ll notice the related entities range in their category from organizations and products affected by ransomware to technical IP addresses related to a new strain of Zeus.
Compare Timing and Shifts in Affected Targets
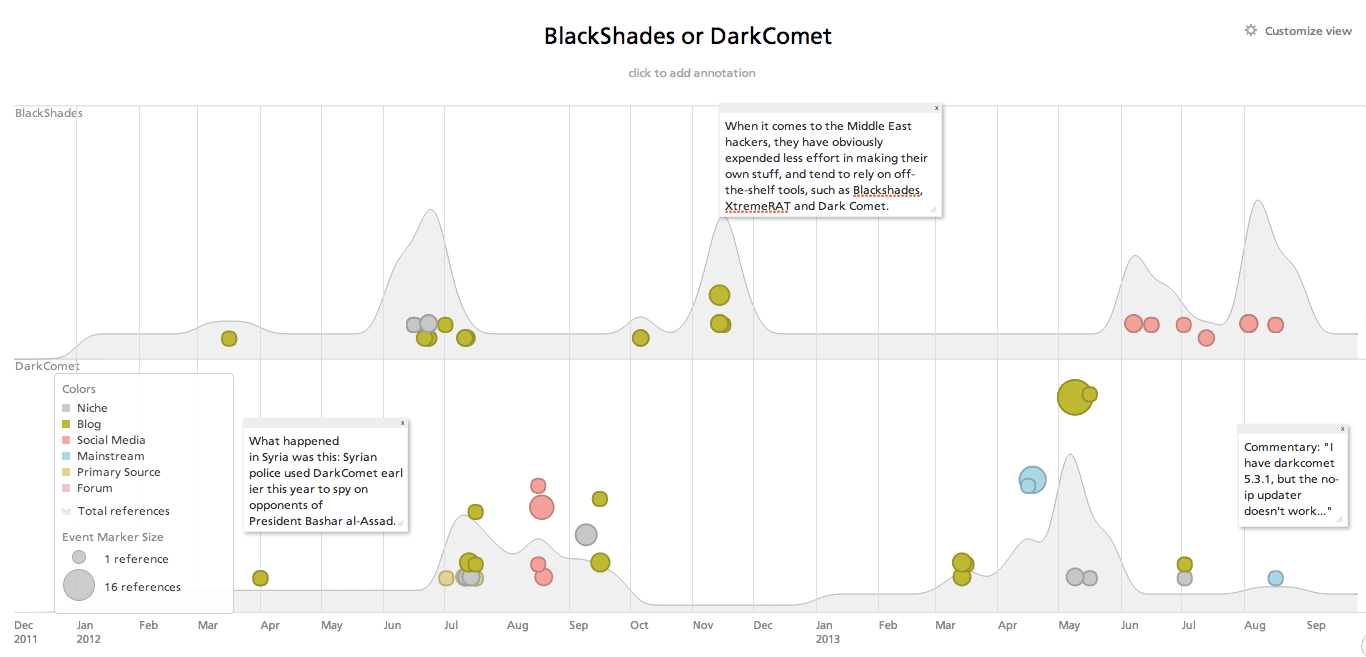
Click the image above for an interactive view.
Answering questions related to patterns is where our five-year archive of data and temporal understanding becomes particularly useful. Above, we see a timeline of two remote administration tools, BlackShades and DarkComet, and their mentions related to Syria, Middle Eastern hackers at large, and a specific discussion forum post.
Aggregate and Link OSINT on Technical Indicators
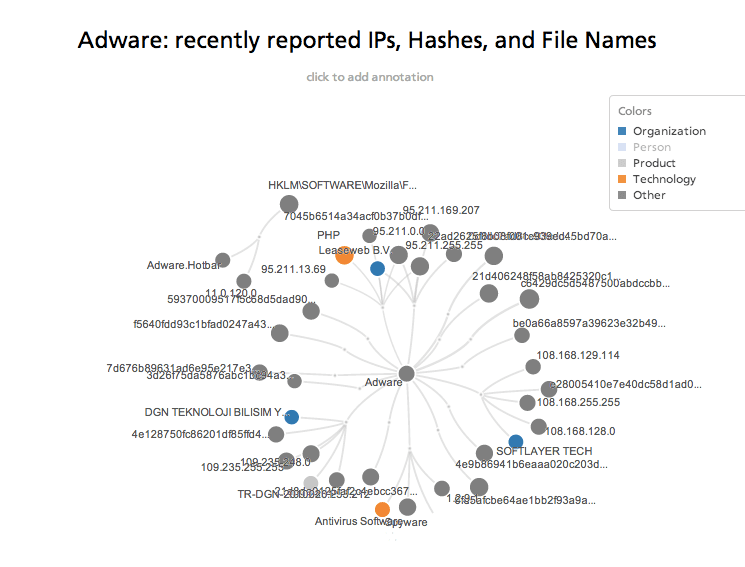
Click the image above for an interactive view.
There is an immense amount of technical information related to malware scattered about open web sources from practitioner blogs to grey hat forums to social media. Several months ago, we began teasing out mentions of technical indicators such as IP addresses, file hashes, CVE identifiers, and more for analysis in Recorded Future.
Perhaps even more interesting for threat intelligence teams, we’ve taken early steps to pipe Recorded Future malware and cyber attack data into investigative environments such as Maltego and Splunk. You can view demonstrations and descriptions of the specific implementations into those tools by watching recent webinar available on our events page.
Demo of Recorded Future Cyber
Want to learn more or experience Recorded Future yourself? Request a demo of Recorded Future Cyber.
Related