Impact of Iran Terrorist Designation for Multinational Orgs
On April 8, 2019, the United States designated Iran’s Islamic Revolutionary Guard Corps (IRGC) as a foreign terrorist organization. This new designation triggers economic sanctions and travel restrictions on roughly 100,000 individuals inside Iran that comprise the IRGC.
The Wall Street Journal reported, “The IRGC’s commander, Mohammad Ali Jafari, was quoted as saying by the IRGC’s official news outlet: ‘If the Americans do such stupidity and put our national security at risk, the U.S. Army and security forces in the West Asia region will not enjoy today’s peace.’”
Since at least 2009, the Islamic Republic of Iran has regularly responded to sanctions or perceived provocations by conducting offensive cyber campaigns. Additionally, the Islamic Republic has historically preferred to use proxies when conducting cyberattacks to achieve its policy goals.
Examples of reactionary attacks include the 2012 denial-of-service attacks on America’s largest financial services companies as an immediate response to the sanctions in a campaign dubbed Operation Ababil.
Similarly, a year later in the fall of 2013, Sheldon Adelson (the CEO of Sands Corporation) publicly suggested that the United States should attack Iran with an atomic weapon. In February 2014, Iran launched a destructive attack on the Sands Las Vegas Corporation that caused significant network damage.
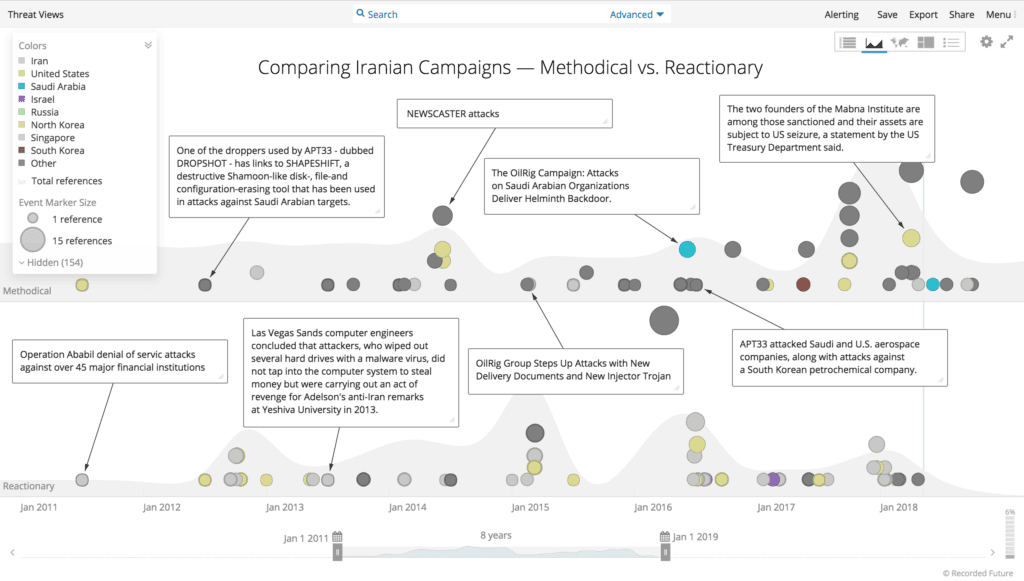
In response to this IRGC terrorist label, and based on historical precedent, it’s logical to anticipate Iran quickly retaliating via cyberattacks. Financial services, energy companies, and military contractors are the most likely targets of Iranian attacks.
Western and Middle Eastern businesses should anticipate attacks — specifically denial of service and/or destructive malware attacks — attempting to disrupt the availability of information.
Iranian sponsored attacks have historically used spearphishing and webshells as the primary mechanisms for establishing unauthorized access.
Related