Cyber Threat Landscape: Basic Overview and Attack Methods
This is the first post in our blog series that aims to provide a basic overview of the contemporary cyber threat landscape.
The flourishing synergy between the internet and its beneficiaries, who use it with varying identities, for various intentions and purposes, has had a noticeable impact on the overall outlook of the global cyber threat landscape.
Today’s relatively open and interoperable global digital infrastructure which connects entities such as organizations, businesses, governments, individuals, etc. – that collectively (as constituents) structure the landscape framework – is being challenged in the form of cyber attacks, ranging from petty malware to the whole existential crisis’ emanating from advanced persistent threats. The correlation between these entities, as formulated by conventional or emerging cyber attack trends and techniques, in a global cyber milieu, is what we’ll refer to as “Global Cyber Theatre” ahead.
Cyber Threat Basics
A theme which currently dominates the global cyber landscape is the focus of cyber threats. Organizations, as well as individuals, remain stubborn to the idea they could be subjected to this type of criminal activity.
The truth is various kinds of cyber threats lurk behind ANYTHING using the internet. In most cases, a threat is offensive and harmful in nature. Victims may lose intellectual property, have their online bank accounts exposed, or inadvertently distribute more malware to other machines in their network. At a higher level, hackers can retrieve confidential business information, and even disrupt a country’s critical national infrastructure.
A noteworthy fact is the US Federal Bureau of Investigation (FBI) has put Cyber Crime and Terrorism second only to Counter-Terrorism and Counter Intelligence on its priority list.
Common Attack Methods
The following is a list and brief description of cyber attack methods that will continue to possess an imminent threat to organizations working in both public and private sectors.
Advanced Persistent Threat (APT)
An advanced persistent threat is characterized by more sophisticated and concentrated efforts by coordinated attackers focused on a single target. The aim is to infiltrate a sensitive system, remain undetected for as long as possible, and leave few traces of their success. For these reasons, APTs have become a favorite approach for those who aim to conduct cyber, corporate, and intelligence espionage.
APTs are generally meant to obtain classified/sensitive information and have been used predominantly against technology companies in the US and Europe to obtain valuable intellectual property. No single technology or process will stop an APT, and traditional security methods are proving to be ineffective against these threats. While many organizations are vulnerable to attacks because they have under-invested in security in the past, simply shoring up existing and conventional defenses is not enough. New approaches and increased vigilance are required.
Protecting against APTs requires several layers of defense, knowledge of the threat, and advanced skills to detect and react to ongoing and successful attacks. APTs have also given birth to new cyber protection approaches such as Continuous Persistent Monitoring (CPM). Please refer to this live feed from Recorded Future to learn more about the sophistication, as well as the intensity, of these attacks.
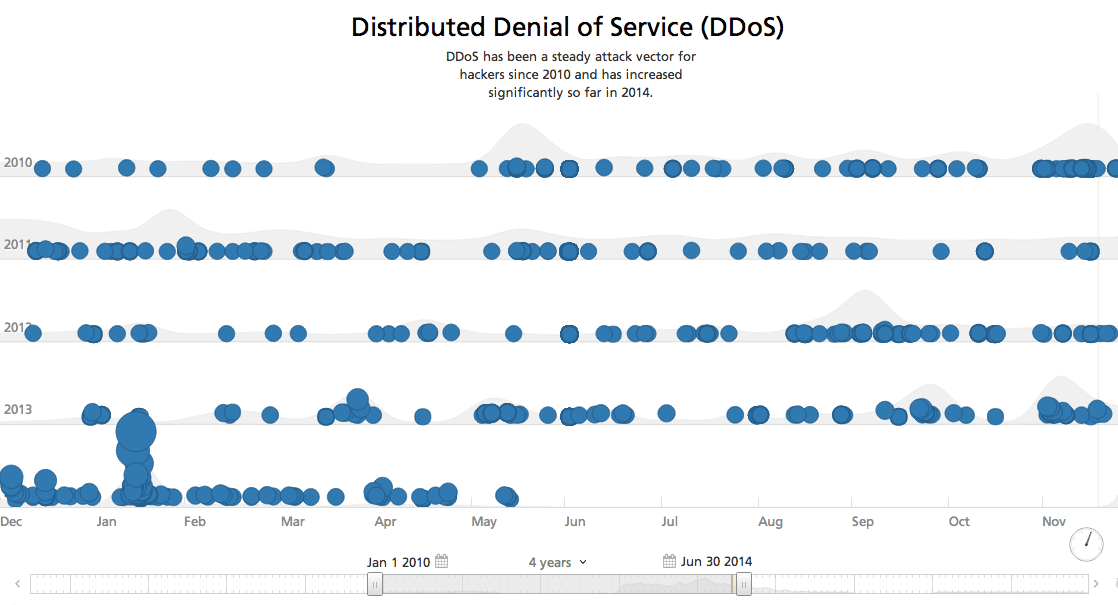
Distributed Denial of Service (DDoS)
DDoS attacks allow hackers to knock off its victims rather than steal information. Although this attack is less technically challenging when compared to others, its effectiveness should not be underestimated. DDoS attacks typically consist of flooding the network with packets of huge amounts of data, thus reaching its limits. As a result, legitimate requests are lost or at least the service becomes too slow to work with.
A successful DDoS attack blocks access to an internet domain (often a very large one) but it doesn’t impact an organization’s internal computer system. If companies follow basic security best practices, their financial payment processing, trading networks, and other core infrastructure won’t be sitting wide open on the internet, vulnerable to an attack. DDoS tactics are political stunts. The platforms most vulnerable to these attacks tend to be symbols of important infrastructure, not the infrastructure itself.
Cross-Platform Malware (CPM)
Malware is no longer exclusive for Windows operating systems only. The economic incentive to build cross-platform malware for cyber criminals rises with the growing number of systems using different operating systems such as iOS. This would inevitably result in an increased number of CPM attacks. For detailed observations and analysis, please refer to this previous post on cross-platform malware.
Metamorphic and Polymorphic Malware
This category of malware keeps changing its code so each of its succeeding versions is different than the previous one. Metamorphic and polymorphic malware pose the single biggest threat to organizations across the world because it easily evades detection and conventional anti-viruses programs. It’s worth noting polymorphic malware is more difficult to write since it requires complicated techniques like register renaming, code permutation, code expansion, code shrinking, and garbage code insertion. However, that’s rarely an issue for larger entities comprising of dedicated and well-supported hackers.
Also, more and more businesses rely on open source web applications which paves the way for susceptibility towards metamorphic and polymorphic malware. Hootsuite, for example, is an open source platform available for public download that many businesses use to manage their Twitter accounts. Since attackers have easy access to platforms like this it’s much easier to learn all about its default settings, and write code accordingly to evade security and conduct espionage.
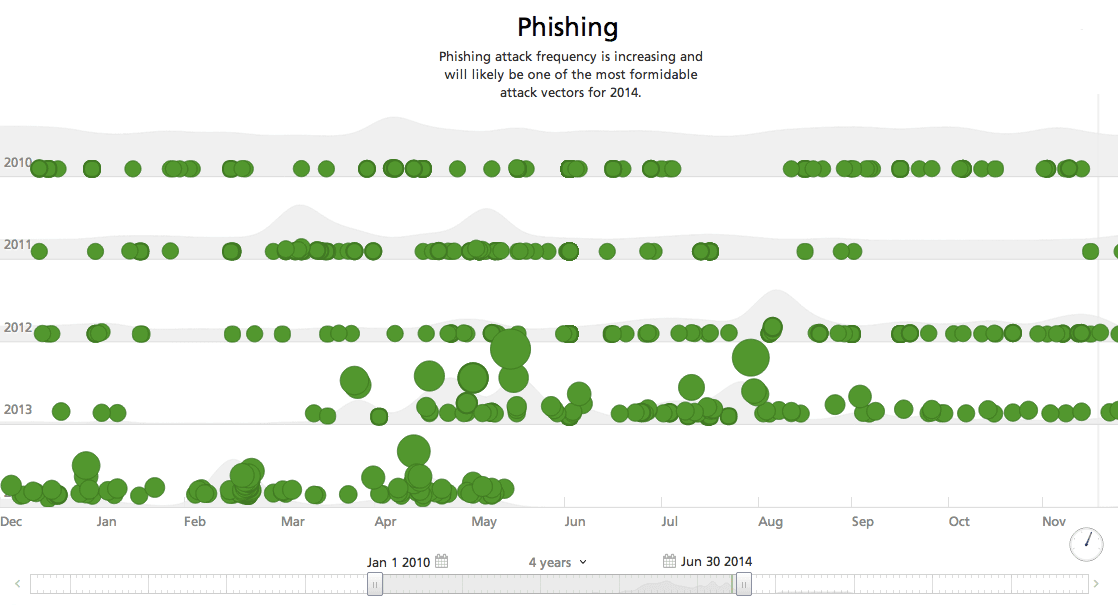
Phishing
This vector generally operates via email, and the idea of email is based in the principle of non-exclusive communication, which essentially means it allows anyone to contact anyone else (and vice-versa) regardless of who they are. While people would generally expect to be contacted by those who are authorized, most of them are unlikely to filter out communicants in the first instance of outreach because doing so would destroy the whole purpose of email.
This assumption creates a loophole where an aspiring attacker may exploit a feature which makes non-exclusive communication possible. The email protocols (RFC) do not provide any authentication of the “From” address making email a favorite medium for spear phishing. Although, tools such as Pretty Good Privacy (PGP) and Sender Policy Framework (SPF) attempt to fix this, but they remain pretty ineffective as they are not generally accepted by most end users.
Now that I’ve finished providing a basic overview of the current cyber threat landscape and explained common attack methods, I’m ready to dig a little deeper. In my next article, I analyze hacker groups including attacker profiles, major operations, techniques, and targets.
Related
