South Korea’s Cyber Defense Policy Hasn't Been Effective
As the most wired nation in the world, South Korea serves as an acid test for cyber defense policy. With 81% of the population connected to the internet, cyber and communications systems are particularly vital not only to the infrastructure and the economy of South Korea, but also to its computer-dependent social order.
The benefits of having such a widely connected population are apparent, but it also leaves the country more vulnerable to disruption at the hands of hacker groups.
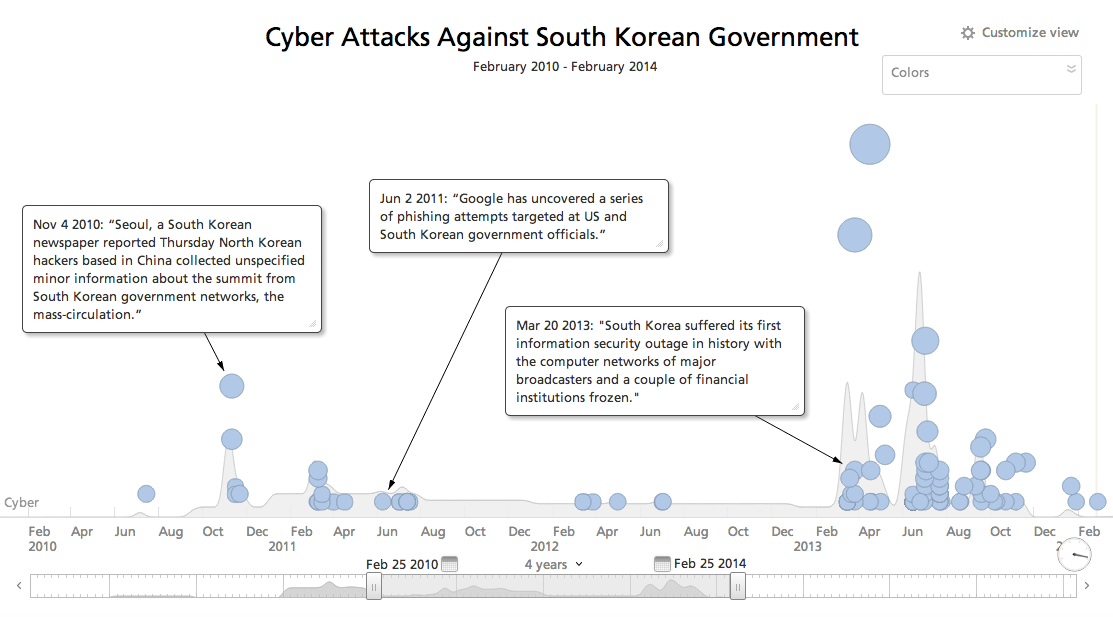
The above timeline references events involving major cyber attacks on corporate and government systems over the past four years. The rates of these attacks steadily increased for three years, culminating in two major attacks last year on March 20, 2013 and June 25, 2013.
These net-bot and malware attacks devastated machines across several industries and government agencies. While much attention was paid to the source of the attacks (either North Korea, a third country, or the hactivist group “Anonymous”) and their possible motivations, far less emphasis was given to the nature of the attacks and how to prevent them from happening in the future.
To their credit, Korean corporations have become quite adept at damage control when it comes to cyber attacks. Within hours of both major strikes in 2013, forensic teams had discovered how the attackers were able to penetrate the system and already had a plan to contain and repair the damage. After one week of both attacks, there were little to no trace an incident had even occurred.
The timeline below shows a focused view of cyber attacks in 2013 so you can see the repair references.
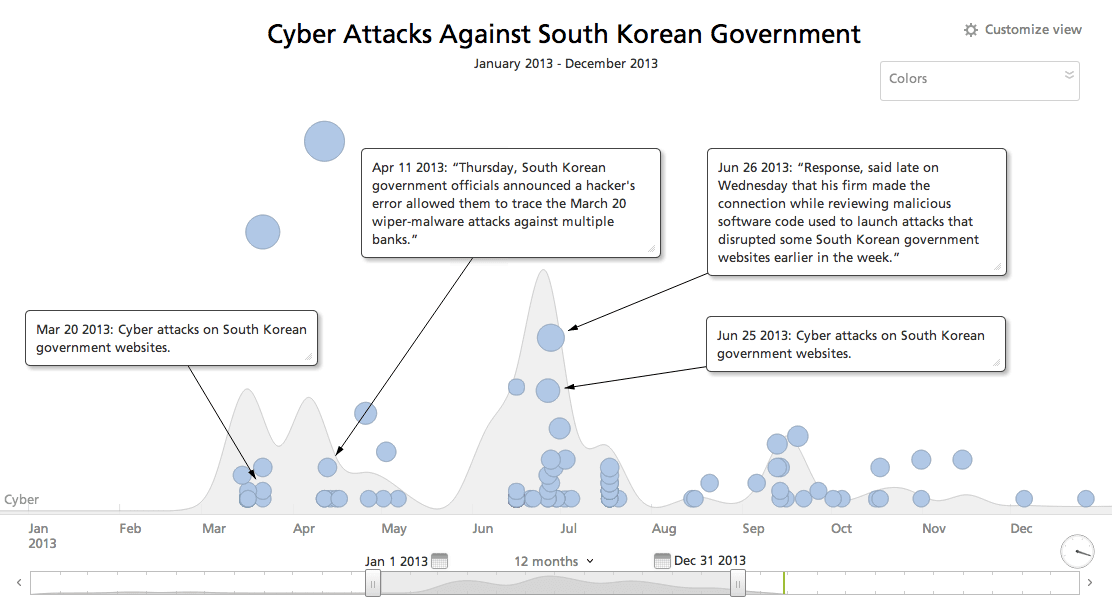
Over the past 13 years, government policy has favored outdated operating platforms and security protocols. In many cases government policy actually forces corporations to use antiquated software. This means after a system patch is deployed, many vulnerabilities which allowed them to be penetrated are still in place. To address the problem, the South Korean government created the National Cyber Security Center, yet policy on operating platforms remains unchanged.
Unfortunately, I believe this ad hoc approach to the issue will only serve to increase the frequency and severity of attacks. As I mentioned above, the number of cyber events increased significantly in 2013 compared to 2010, 2011, and 2012 and I expect this trend to continue in 2014.
Related
