The History of Ashiyane: Iran’s First Security Forum

Scope Note: Recorded Future conducted research on the evolution of Ashiyane Forum, the first and largest security forum in Iran. Sources of this research include the Recorded FutureⓇ Platform, direct forum interaction, open source research, and interviews with a former Iranian hacker who claims firsthand knowledge of Iran’s security forums.
This report will be of greatest interest to organizations seeking to understand the rapidly changing criminal and state-sponsored cyber threats emerging from Iran to better protect their organizations.
Executive Summary
In a previous report, Insikt Group documented the relationship between the Iranian government, contractors used for offensive cyber operations, and the trust communities that begin with Iranian security forums. This report further explores the historical links between Iran’s primary security forum, Ashiyane Forum, and the Iranian government. Recorded Future observed forum posts from over 20,000 Ashiyane Forum members and found a trend in Iranian hacker migration following Ashiyane Forum’s shutdown in August 2018.
Key Judgments
Ashiyane Forum, once the main security forum in Iran, was managed by one of the primary security contractors in Iran with known connections to Iran’s Islamic Revolutionary Guard Corps (IRGC) and has been shut down since August 2018 with no indication of reemergence.
We assess with medium confidence that Ashiyane Forum and its creator, the Ashiyane Digital Security Team, were key sources for Iranian contractors to identify talent and share information on successful offensive tools and tactics.
Ashiyane Digital Security Team founder Behrooz Kamalian has deep ties to the Iranian government and is currently attempting to build new businesses after his short time in prison.
Background
Recorded Future previously reported on the cyber capabilities of the Islamic Republic of Iran in June 2015 and May 2018, describing the country’s cyber prowess, its fight against Saudi Arabia for regional hegemony, and its willingness to conduct offensive campaigns against Saudi Arabia on both occasions. Since at least 2009, Iran has regularly responded to both regional provocations and international sanctions by conducting offensive cyber operations. Primary targets of such attacks have been Saudi Arabia, Israel, and Western organizations, as well as Asian petrochemical and aviation companies. The sophistication of these attacks has ranged from social media hijacking and website defacement to highly destructive campaigns, like the attack on Saudi Aramco and sophisticated espionage campaigns against Western, Middle Eastern, and Asian targets.
Recorded Future has also previously reported that many Iranian state-sponsored operations utilize contractors, and that Iranian government contractors are forced to mine closed-trust communities to find and retain good cyber talent. The following is an account of the genesis and maturation of Iran’s online security community, and the role that Ashiyane Forum played in that history.
In 2002, according to an Insikt Group source, Iranian youth were creating hacker web forums and IRC — Internet Relay Chat channels (online clubs) — to share information. Much activity within these forums involved members defacing rival hacker websites for prestige among their peers. Early forums (among others) included simorgh-ev.com and ashiyane.com. The goal of operating these forums was not financial gain. Rather, forum members exchanged offensive tradecraft and conducted defacements for fun. Within two years, however, Iranian website defacements began including messages with ideological and religious overtones. According to Insikt Group’s source, toward the end of 2007, a small and brief online skirmish broke out between Saudi forums tailored to Wahhabism (Saudi Arabia’s dominant faith) and Iranian forums.
The Iranian government began to take notice of these defacements, translating the cyber activity into formal propaganda — Iranian youth taking up the Shia cause. According to Insikt Group’s source, notoriety came with something akin to an “Iranian defenders” label, and Iranian hackers had a new motive to participate in foreign website defacements.
Multiple data points suggest that Iranian security forums play a role in staffing and knowledge sharing for Iranian contractors. For example, Insikt Group’s source claims that the Iranian Simorgh forum administrator had familial ties to the Islamic Revolutionary Guard Corps (IRGC), a branch of Iran’s Armed Forces involved in cyber operations. Most suspiciously, a handle found in APT33 malware, Xman_1365_x, has also been found as an active member on Ashiyane Forum, the largest and most famous hacking forum within Iran. This forum is managed by an Iranian security contractor with proven ties to IRGC operations. Based on the link between Ashiyane Forum and its namesake contractor, a forum member with ties to APT33, as well as the contractor’s links to the Iranian government, we assess with medium confidence that Ashiyane Forum has provided staffing and knowledge exchange for Iranian state-sponsored contractors.
History of Ashiyane Forum and Its Founder
Based on archived web page data, Ashiyane Forum initially started as a section of Ashiyane Digital Security Team’s original website, ashiyane.com, in early 2003. The forum expanded into its own website, ashiyane.org, in 2006. Ashiyane.org contained sections for general questions, tool sharing, defacements, training sessions, and news. Many of these original sections persisted as the forum expanded and became one of the largest hacking forums in Iran. In August of 2018, Ashiyane Forum was shut down.
Banner for Ashiyane in 2006.

Banner for Ashiyane Forum proclaiming that it is the “first security forum in Iran.”
Ashiyane Forum was run by Ashiyane Digital Security Team, a “gray hat” network security company. Founded in 2002, Ashiyane Digital Security Team’s initial goal was to educate Iranian users and network administrators on security by finding vulnerabilities within computer networks. Their group members still deface websites for notoriety: in 2014, Ashiyane Digital Security Team handles were found on defaced websites belonging to Thai and Indian government organizations, as well as websites hosted on Italian IPs.
Ashiyane Digital Security Team has attacked hundreds of websites belonging to Israeli and U.S. government organizations, including Mossad and NASA, allegedly due to their lack of respect for Ayatollah Khomeini. When Sunni Arab hackers brought down a major server hosting most Shia religious websites in Iran, Ashiyane Forum responded by bringing down 300 Arabic websites through attacking five of the major servers belonging to the hackers. The Department of Justice and other industry members identified members of Ashiyane Digital Security Team involved in operations on behalf of the IRGC.
Behrooz Kamalian, known as the “father of Iranian hacking,” is the CEO and founder of Ashiyane Digital Security Team. Behrooz is well regarded among the Iranians for his willingness to share his knowledge with younger hackers. Behrooz is also popular among many Iranian actors and actresses who claim he has helped protect their Instagram access, specifically by helping to regain control of previously compromised accounts. When asked about Ashiyane Digital Security Team’s possible involvement with Iranian state-sponsored efforts, Behrouz has claimed that while Ashiyane Forum operates independently and spontaneously, they cooperate with Iranian military apparatuses in advising and improving security, and “have always operated in the framework of the goals of the state.”
Behrooz Kamalian’s Instagram profile.
Ashiyane Forum’s most notorious web defacements revolve around the historic Iran-Saudi conflict. In late 2008, while Saudi Wahhabi groups were retaliating against Iranian web defacements by defacing Iranian sites, Behrooz Kamalian visited prominent cleric Ayatollah Naser Makarem Shirazi. Following that meeting, the cleric publicly requested restraint from Iranian hacking groups to cease further attacks on Wahhabi websites. However, the defacements did not stop; the back and forth was memorialized on zone-h.org, a website that records website defacements. On October 9, 2008, Delta Security (a spinoff of Ashiyane Forum) was compromised by bAd Hack3r, an actor who had a long self-recorded history of defacing Iranian sites.
Insikt Group’s source alleges that in one specific operation, Wahhabi actors deployed spearphishing campaigns with a backdoored version of Putty (a free remote connectivity application for Windows) from compromised Ashiyane Forum email servers. XP-Group, an alleged Wahhabi group, specifically began targeting and defacing Iranian clerical sites with vulgar imagery. Subsequently, XP-Group’s website was defaced in retaliation. For external observers, it was difficult to discern which side escalated initially. An Ashiyane Forum member told Insikt Group’s source that Kamalian created XP-Group and owned the domain. If this is true, XP-Group masqueraded as Wahhabi, but was owned and operated by Kamalian. Ashiyane Forum and XP-Group were essentially one and the same, and Kamalian had manufactured his own religiously motivated cyber conflict. Recorded Future has been unable to confirm secondary validation of these claims.
In 2009, the government issued a directive to blacklist all Iranian hacking sites in response to the Iranian Green Movement, during which Iranian government sites like khamenei.com were attacked. Ashiyane Forum was one of the only hacking forums that remained, and according to Insikt Group’s source, the Iranian hacking community speculated that Kamalian essentially struck a sole-source deal with the Iranian government. Ashiyane Forum had become the primary forum connecting to the new generation of Iranian hackers.
Following the peak of the Green Movement, government-sponsored offensive cyber campaigns were disorganized. In 2010, the Stuxnet worm was successfully victimizing Iran’s uranium enrichment plants, and the IRGC, reporting to Ayatollah Khamenei, realized the need for expedited, offensive cyber competency. As the premier hacking group aligned with state interests, Behrooz and Ashiyane Forum were well positioned to help. One member of the Ashiyane Digital Security Team participated in an IRGC-led distributed denial-of-service (DDoS) campaign against U.S. financial institutions in December 2011, lasting over 176 days. Additionally, Kamalian’s status with the IRGC was further cemented after he appeared on an EU sanctions list in 2011.
Threat Analysis: Ashiyane Forum Content
As one of the only Iranian hacking forums organized by a security company that clearly cooperated with Iranian nation-state cyber forces, Ashiyane Forum attracted a cumulative membership of approximately 20,000 active users. By collecting and analyzing Ashiyane Forum threads for the past 12 years, Recorded Future determined general trends within the forum. The majority of the content posted within Ashiyane Forum focused on web exploitation. Cross-site scripting, DDoS attacks, SQL, and other browser-based code injections have been the primary subjects since the forum’s inception. Additionally, Android exploits were a consistently popular topic over the past four years, possibly due to the steady increase in the number of mobile devices within the region, from 26.72 percent of total device market share in January 2014 to 37.85 percent in April 2015.
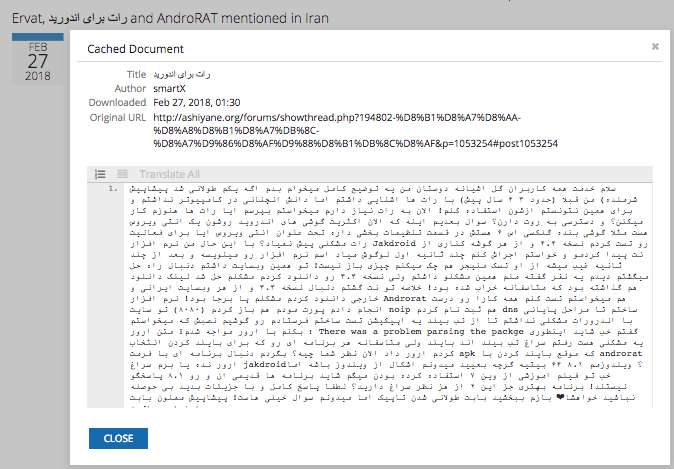
An Ashiyane Forum post requesting assistance deploying AndroRAT. (Source: Recorded Future)
In 2015, the top tools advertised included Android remote access trojans (RATs), such as AndroRAT and Dendroid RAT, and Citroni Ransomware. In 2016, content on the forums shifted to exploits for consumer electronics and Android devices, as well as exploits for internet protocols. Android malware DroidJack, PC trojan njRAT, and USB malware PoisonTap became popular, as did questions about DDoS and SQL injection attacks. In 2017, while similar themes to those discussed in 2015 and 2016 were popular, many posts revolved around Linux products and enterprise content management, as well as Android devices. Because Ashiyane Forum was one of the most famous hacking forums within Iran, these posts likely represent a consistent stream of new, less experienced members registering on the forum and asking similar questions about simple web vulnerabilities on newer web browsers and technologies.
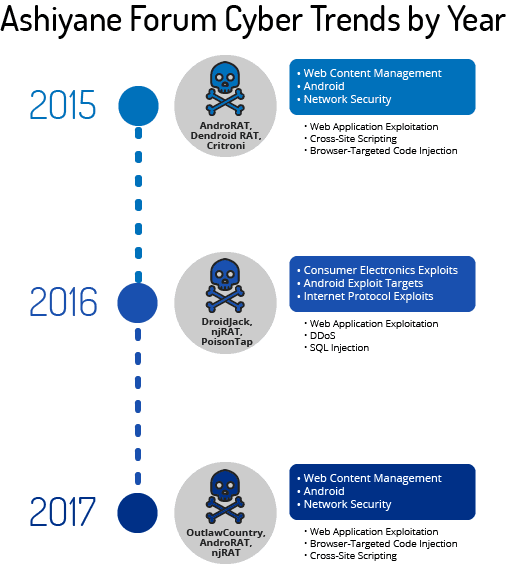
Visual of Ashiyane Forum cyber trends by top three recent years.
Insikt Group believes that Ashiyane Forum also had its fair share of experienced hackers as forum veterans, shown by the speed at which new, highly sophisticated vulnerabilities were shared among forum members. For example, a proof of concept for CVE-2015-0313, an Adobe Flash use-after-free (UAF) vulnerability, as well as a similar post for CVE-2015-0311, an Adobe Flash remote code execution (RCE) vulnerability, were shared only months after the vulnerabilities were recorded on NVD. Furthermore, when CIA hacking tool OutlawCountry was released on WikiLeaks on June 29, 2017, Ashiyane Forum members were sharing and discussing the tool only five days later.
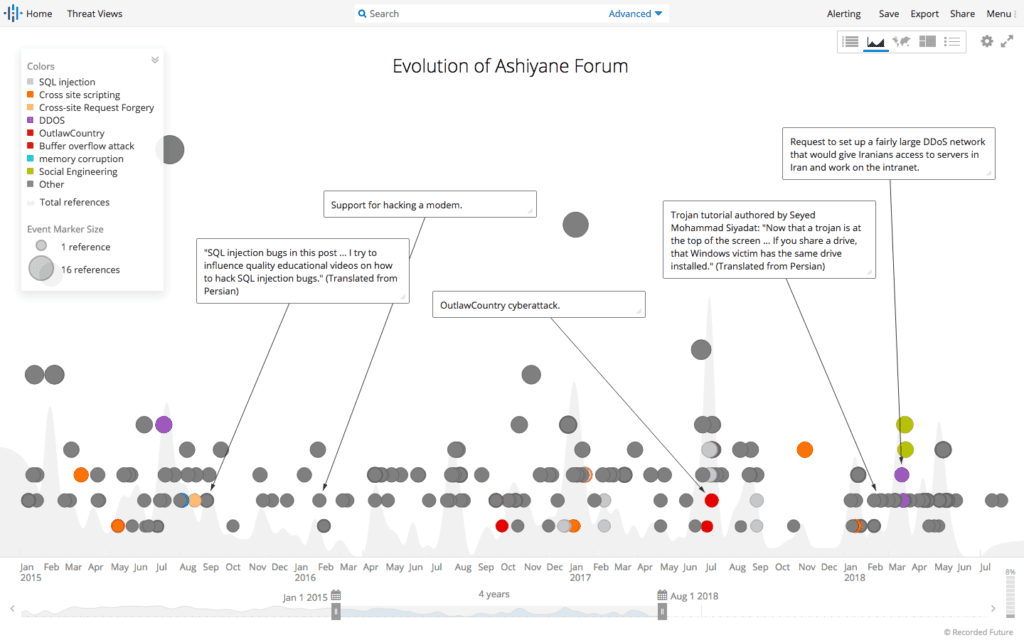
Advertisements on Ashiyane Forum since 2015. (Source: Recorded Future)
The Shutdown of Ashiyane Forum and Iranian Hacker Migration
On March 12, 2018, the official Ashiyane Digital Security Team channel stated that the Iranian court had ordered them to shut down all of their activities until further notice. While the announcement gave no reason as to why the shutdown had occurred, sources in Iran confirmed that Ashiyane Forum was operating gambling websites, which is dangerous due to the penalties, including life imprisonment or death. Ashiyane Forum was previously linked to gambling in 2013, when a portion of Ashiyane Forum’s database was leaked online. According to Insikt Group’s source, the username used for Ashiyane Forum’s database support was linked to the creation of multiple poker sites operating in Iran under the moniker “persianpoker.”
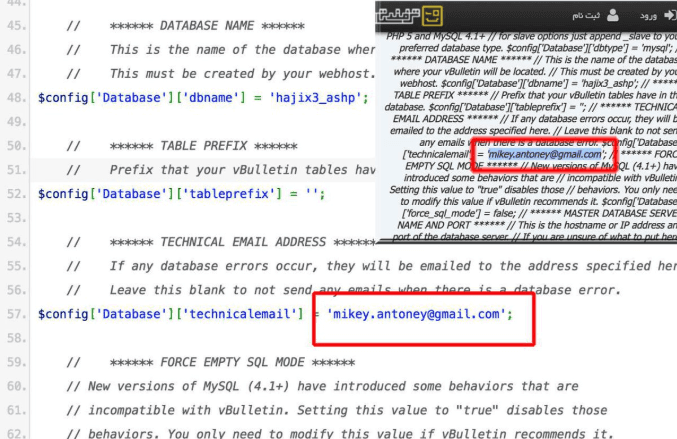
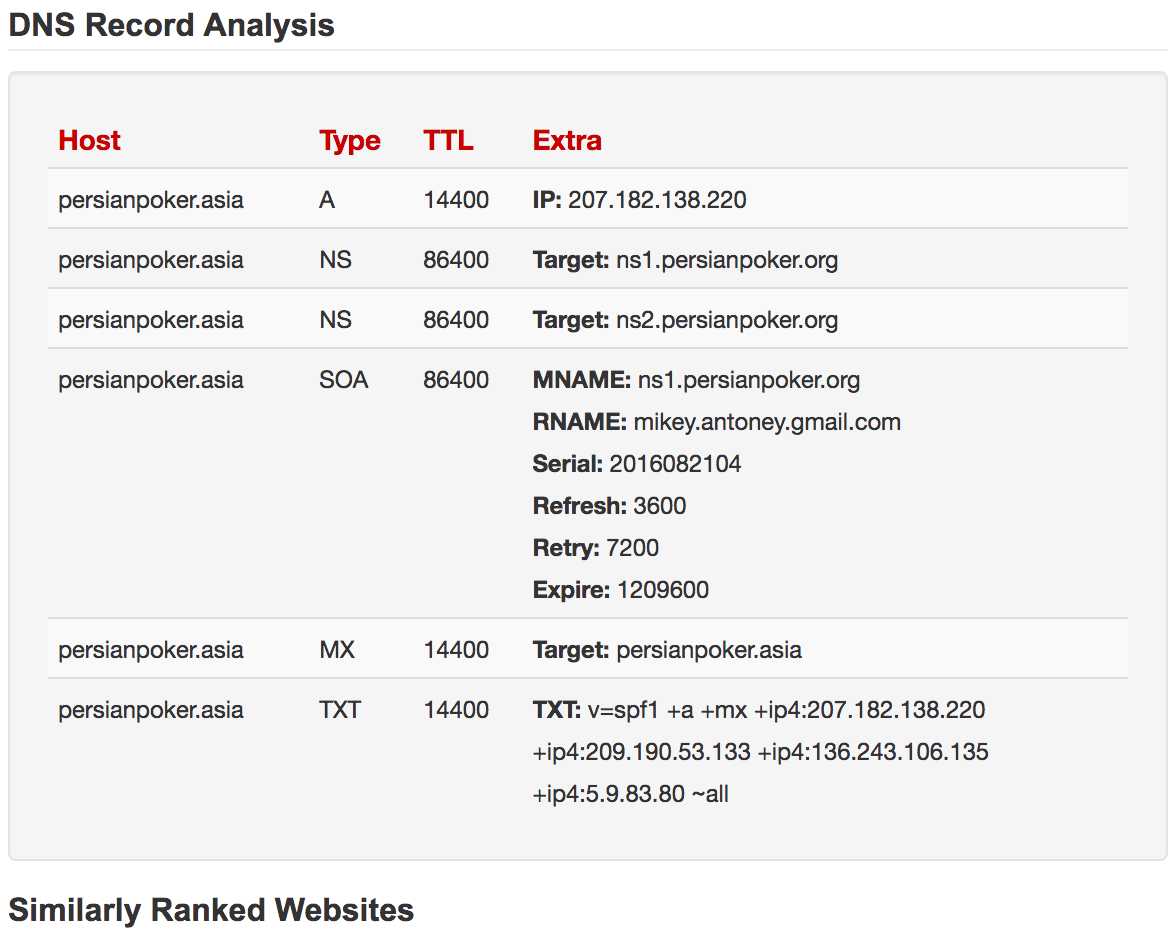
Pastebin of an Ashiyane Forum dump from 2013, correlated with DNS records for persianpoker[.]asia.
According to Recorded Future data, Ashiyane Forum went offline on August 5, 2018. Forum members circulated rumors that the site had been hacked or forcibly shut down. On October 31, 2018, an Iranian hosting specialist tweeted, “I have been worried lately. I do not know who would be in charge now that Behrooz is not around.” Insikt Group’s source and posts on Ashiyane Forum between mid-April and July 2018 state that Behrooz had been arrested. However, Behrooz was out of prison by early November, and on November 8, 2018, he posted an Instagram video where an Iranian actor thanked Behrooz for regaining access to his Instagram account after the account had been compromised. Instagram users have left comments on Behrooz’s more recent posts asking about Ashiyane Forum’s shutdown, but Recorded Future has not observed Behrooz engage with those posts.
Online poker is both a profitable and dangerous enterprise. According to Insikt Group’s source, there are over 3,000 gambling websites within Iran that are short lived and are blocked daily. While Insikt Group has been unable to find secondary verification on the statistics themselves, Insikt Group can confirm that running gambling operations in Iran or any Islamic country is a dangerous act due to its harsh punishments. Instead of receiving life imprisonment or the death penalty, Behrooz was able to leave prison in only a few months, possibly due to his existing relationships with the Iranian government and the IRGC. If this is the case, Behrooz’s lenient sentencing may suggest that his role in the domestic hacker community is of great importance to the Iranian government. However, Ashiyane Forum remains offline and Behrooz has rebranded himself as the hacker that assists celebrities on social media. There is no evidence that Behrooz will attempt to recreate the Ashiyane Digital Security Team and Forum in the future.
Twitter reactions to the Ashiyane Digital Security Team shutdown.
Ashiyane Forum Member Migration Activity
As one of the largest and most prominent forums within the Iranian hacking community, Ashiyane Forum’s closure will likely leave hackers searching for new communities that provide the same topical discussions and interactions, or rely increasingly on other already established — albeit less popular — forums.
Recorded Future reviewed posts from over 20,000 Ashiyane Forum members from 2014 to 2018. Of the 18,060 users active before Ashiyane Forum shut down, only four percent of users had monikers with exact matches on other Persian, Arabic, Russian, or English forums. Of these exact matches, two stood out in particular: VBIran.ir and Persian Tools forum. The below graph shows the number of exact Ashiyane Forum username matches on other forums, separated by the date of their first post. Recorded Future attempted to ascertain whether a majority of the usernames were created before the Ashiyane Digital Security Team channel shutdown announcement in March 2018 (during the period between the announcement and the forum shutdown), or after Ashiyane Forum’s shutdown on August 5, 2018.
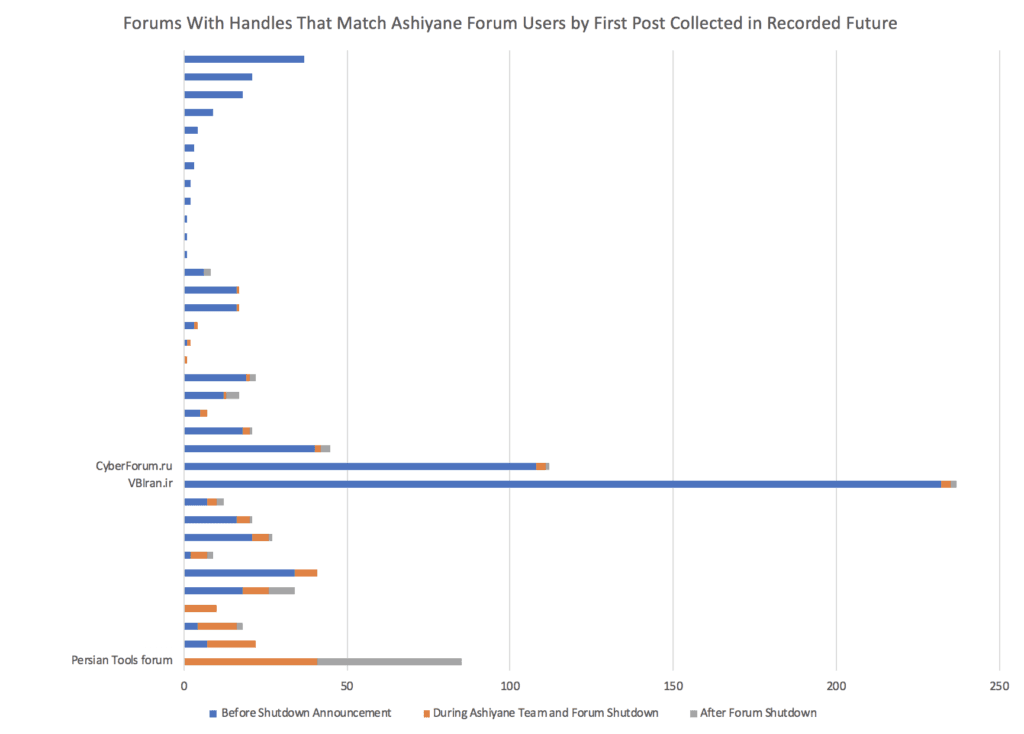
Forums with overlap in Ashiyane Forum membership. (Source: Recorded Future)
With 237 exact Ashiyane Forum username matches, VBIran.ir had the most users in common overall, and most of the users had posted on the VBIran.ir forum prior to any Ashiyane Forum shutdown announcement. Persian Tools forum, on the other hand, had no usernames in common prior to the Ashiyane Forum announcement — all 85 users registered either during or after the shutdown period. While CyberForum.ru also had a large number of Ashiyane Forum username matches, a majority of the matches were false positives due to commonly used usernames.
After removing likely false positives and looking for common entities, Recorded Future concluded that usernames with exact matches to Ashiyane Forum members consist of approximately seven percent of total membership on VBIran.ir — one out of every 14 members is a former Ashiyane Forum member. Exact matches to Ashiyane Forum usernames also now constitute 3.5 percent of total membership on Persian Tools forum, up from from zero percent in March 2018. Interestingly, there was almost no overlap in Ashiyane Forum usernames between the two forums, suggesting that after Ashiyane Forum shut down, hackers that migrated to other forums split into two factions.
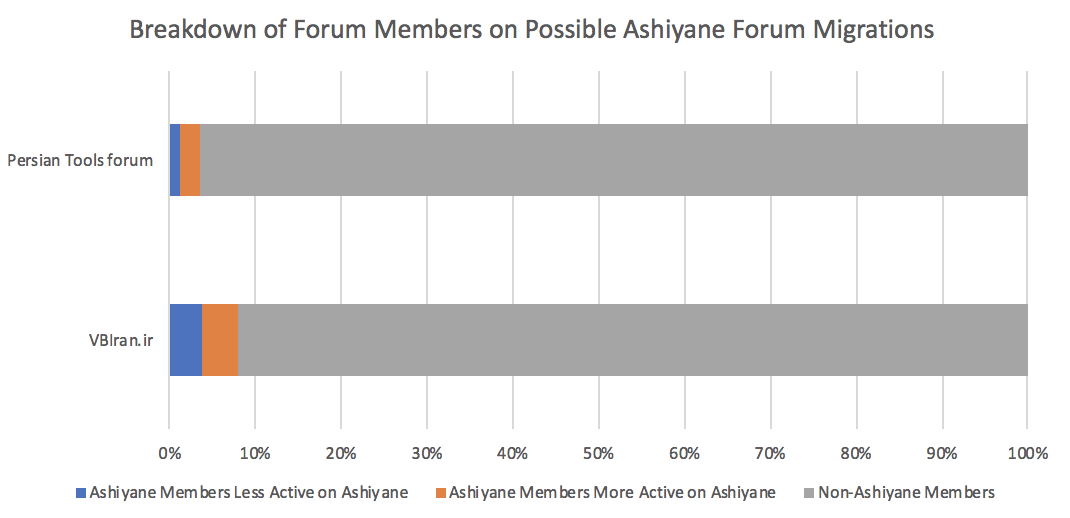
Breakdown of membership on possible Ashiyane Forum migrations. (Source: Recorded Future)
VBIran.ir and Persian Tools Forum
While both of these forums have approximately one-tenth of Ashiyane Forum’s membership, they share some similarities with Ashiyane Forum itself. Both forums contain primarily Farsi posts, similar to Ashiyane Forum, and offer fairly large forums to conduct offensive tactical discussions. However, Persian Tools forum and VBIran.ir differ widely in terms of content and focus. Most posts on Persian Tools forum are either sales posts or posts related to Iran, hacking, electronics, or even soccer. Forum organization on Persian Tools forum also seems to be similar to that of Ashiyane Forum, before Ashiyane Forum became separate from the Ashiyane Digital Security Team website.
While a section of the Persian Tools forum website exists with subsections on various forms of hacking, Persian Tools forum also offers SSL certificate sales, hosting services, and even website design. VBIran.ir also appears to cater to a more general audience. VBIran.ir posts are primarily discussion or tutorial-based, and cater to topics on both hacking and software development. Furthermore, VBIran.ir does not offer any special services like Persian Tools forum, but instead sells various web development plugins. This is a possible reason as to why there was little overlap between Ashiyane Forum members.
Outlook
Ashiyane Digital Security Team, as the administrator of one of the largest and most prominent forums within Iran’s hacking community, has not announced the reasons behind Ashiyane Forum’s shutdown and has ignored questions about its possible return. The forum is likely offline indefinitely. There does not appear to be a clear Ashiyane Forum replacement, though smaller forums are attracting new members.
We assess that companies with business relationships in Iran, firms operating in Saudi Arabia, and any energy or national defense organization should monitor the evolutions of these newer forums. Iranian contractors who previously relied on Ashiyane Forum as their primary community will continue looking for alternatives.
We also assess that Behrooz Kamalian is a worthwhile individual to monitor for the same previously described organizations because of his relationships inside the Iranian government, as well as his reputation as one of Iran’s premier hackers.
Related