Analyze Recent Atlassian Vulnerabilities and Keep Your Infrastructure Protected

For years, software solutions built by Atlassian have found their way to nearly every organization's software stack. Tools such as JIRA, Confluence, Bamboo, and BitBucket are often seen playing a crucial role in various departments across enterprises.
From managing projects or handling organization-wide documentation, to hosting the very code of a product being developed by the organization, the constant reliance upon and amount of historical data held within these applications have turned them into a lucrative target for attackers, expanding the attack surface in the process.
Historical Atlassian Vulnerabilities
Traditionally, vulnerabilities within the Atlassian software stack have originated from different sources, including plugins backed by an extensive marketplace; yet, most have appeared as a result of its aging code stack.
Let's take a look at some of the most critical vulnerabilities and exposures (CVEs) seen in Atlassian software:
- CVE-2017-14589 (2017-12-13) - CVE Score 9.6 (Critical): An attacker who has restricted administration rights to Bamboo, or who hosts a website that a Bamboo administrator visits, can exploit this vulnerability to execute Java code of their choice on systems that run a vulnerable version of Bamboo.
- CVE-2019-3394 (2018-08-29) - CVE Score 8.8 (High): An attacker with permission to edit a page within Confluence Server and Confluence Data Center is able to exploit this vulnerability to read files on the server under the /confluence/WEB-INF directory, which usually contains configuration files which inturn can contain credentials used for integrating services with Confluence.
- CVE-2019-11581 (2019-08-09) - CVE Score 9.8 (Critical): A server-side template injection vulnerability in Jira Server and Data Center inside the ContactAdministrators and the SendBulkMail areas may allow remote code execution.
- CVE-2019-15000 (2019-09-19) - CVE Score 9.8 (Critical): If public access is enabled for a project or repository, attackers can exploit this issue without any need for authentication while being able to read file contents or execute commands by injecting additional arguments via git commands.
As mentioned, plugins from various software vendors have been a constant source of vulnerabilities. Often, 3rd-party plugin developers are to blame for the incorrect implementation of APIs and credential stores, but, at times, vulnerabilities can be caused by plugins developed by first-party developers as well.
Recent Critical Atlassian CVEs
Let's take a look at some of the recent critical vulnerabilities that have affected Atlassian tools.
JIRA, being one of the most popular tools used for software development and IT help desks, has seen quite a few vulnerabilities in the recent past. For example, a recent vulnerability CVE-2020-14179 allowed remote unauthenticated users to view custom fields and custom SLA names by querying the secure
Similar vulnerabilities have allowed unauthenticated users to enumerate users in a JIRA server (CVE-2020-14181 / CVE-2020-36289) by accessing the
Other vulnerabilities allowed threat actors to read of certain system-level files, potentially exposing further information about the JIRA configuration (CVE-2020-29453 / CVE-2021-26086).
For example, an attacker could make GET requests to the
Wherein the
- WEB-INF/web.xml
- WEB-INF/decorators.xml
- WEB-INF/classes/seraph-config.xml
- META-INF/maven/com.atlassian.jira/jira-webapp-dist/pom.properties
- META-INF/maven/com.atlassian.jira/jira-webapp-dist/pom.xml
- META-INF/maven/com.atlassian.jira/atlassian-jira-webapp/pom.xml
- META-INF/maven/com.atlassian.jira/atlassian-jira-webapp/pom.properties
and JIRA would return the contents of these files, exposing certain configurations and other server information stored within them.
JIRA has also been a victim of critical vulnerabilities such as complete authentication bypasses by using specially crafted HTTP requests, scoring a 9.8 (Critical) score on the CVE Scale (CVE-2022-0540). This vulnerability can be exploited through the use of specific plugins, such as Mobile Plugin for Jira, Insight - Asset Management, allowing attackers to execute certain scripts on the server via the job scheduler configuration at the URL:
Looking at another widely used Atlassian tool, Confluence has experienced critical vulnerabilities such as allowing remote attackers to execute code on a Confluence Server (CVE-2021-26084 / CVE-2022-26134) via injection attacks, while other vulnerabilities allowed attackers to view restricted resources on a Confluence Server (CVE-2021-26085), wherein the payload:
${(#[email protected]@toString(@java.lang.Runtime@getRuntime().exec("id").getInputStream(),"utf-8")).(@com.opensymphony.webwork.ServletActionContext@getResponse().setHeader("X-Cmd-Response",#a))}
${(#[email protected]@toString(@java.lang.Runtime@getRuntime().exec("id").getInputStream(),"utf-8")).(@com.opensymphony.webwork.ServletActionContext@getResponse().setHeader("X-Cmd-Response",#a))}
Beyond these application-level vulnerabilities, popular first-party plugins have also seen critical vulnerabilities. Take, for example CVE-2022-26138, which was caused by a widely used plugin named “Questions for Confluence”. Developed by Atlassian, the plugin provides a discussion forum-like experience within Confluence by allowing users to ask questions and interact with each other. In short, the plugin created a user within the system named “disabledsystemuser”, with a hardcoded password, which an unauthenticated attacker with access to these credentials could simply exploit to log in to the Confluence server.
Looking into vulnerabilities within the software stack itself, CVE-2022-26134 is a good example of an Atlassian case in point wherein the vulnerability existed right within the application. Using an Object-Graph Navigation Language (OGNL) injection, an unauthenticated attacker could execute arbitrary code on a Confluence Server. This vulnerability allowed any code or /command to be executed on a vulnerable server hosting Confluence, allowing the compromised server to be used for malware distribution, cryptocurrency mining, and ultimately any other security threat.
Identifying Vulnerable Atlassian-based Vulnerabilities on Your Infrastructure
The process of identifying vulnerabilities within an organization's infrastructure is seen as a never-ending, complex task. However, the process of scanning infrastructure has been simplified over the years with the introduction of various open-source and free-to-use tools, yet knowing “what to scan” and “what vulnerabilities to scan for” remains a major challenge.
With frequent new CVE announcements, keeping one's scanning tools up-to-date with the knowledge of these new CVEs is seen as one of the biggest hurdles for security researchers.
Using the Recorded Future Attack Surface Intelligence module ensures complete end-to-end automation of your organization's security needs:
- Automated scans of your infrastructure without missing a single host during the scanning process
- Your hosts are also scanned for the latest CVEs and known vulnerabilities
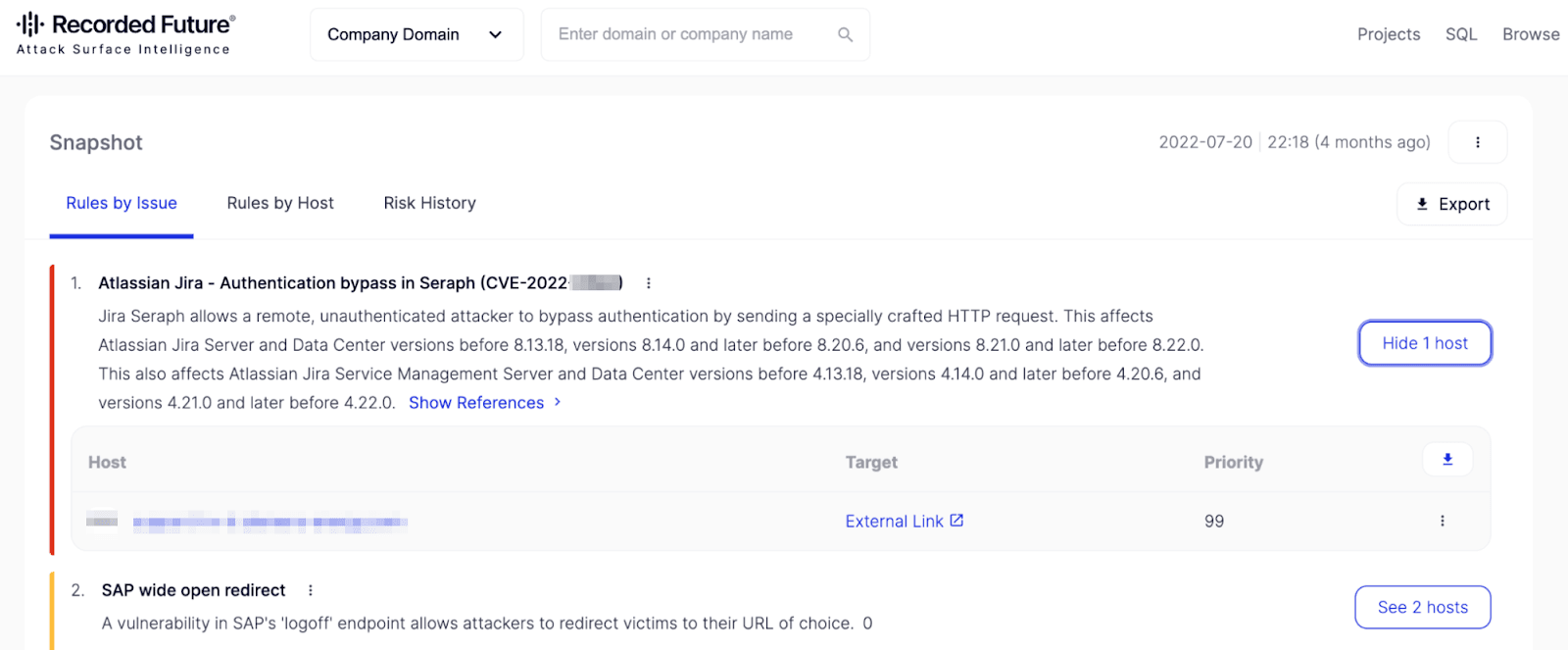 As shown below, Recorded Future Attack Surface Intelligence can seamlessly identify any Atlassian infrastructure in your environment and alert you to its potential vulnerabilities — even the latest CVEs.
As shown below, Recorded Future Attack Surface Intelligence can seamlessly identify any Atlassian infrastructure in your environment and alert you to its potential vulnerabilities — even the latest CVEs.
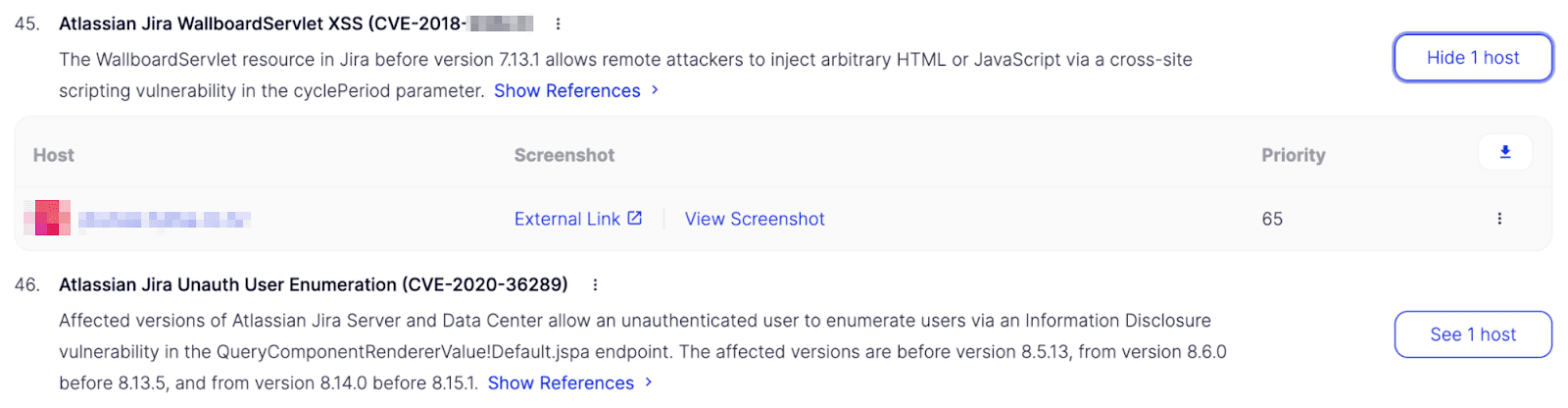 Here’s a brief overview of the 23 most critical Atlassian CVEs detected by our engine, at the time of this writing:
Here’s a brief overview of the 23 most critical Atlassian CVEs detected by our engine, at the time of this writing:
| CVE | CVE Score | Affected Atlassian Tool |
| CVE-2021-26084 | 9.8 (Critical) | Confluence Server and Data Center |
| CVE-2022-0540 | 9.8 (Critical) | Jira Seraph |
| CVE-2022-26134 | 9.8 (Critical) | Confluence Server and Data Center |
| CVE-2022-26138 | 9.8 (Critical) | Atlassian Questions For Confluence |
| CVE-2019-11580 | 9.8 (Critical) | Atlassian Crowd and Crowd Data Center |
| CVE-2019-11581 | 9.8 (Critical) | Jira Server and Data Center |
| CVE-2019-3396 | 9.8 (Critical) | Confluence Server and Data Center |
| CVE-2019-8442 | 7.5 (High) | Jira Server and Data Center |
| CVE-2019-8451 | 6.5 (Medium) | Jira Server and Data Center |
| CVE-2020-9344 | 6.1 (Medium) | Subversion ALM |
| CVE-2017-9506 | 6.1 (Medium) | Atlassian OAuth Plugin |
| CVE-2018-20824 | 6.1 (Medium) | Jira Server and Data Center |
| CVE-2019-3402 | 6.1 (Medium) | Jira Server and Data Center |
| CVE-2018-5230 | 6.1 (Medium) | Jira Server and Data Center |
| CVE-2020-14179 | 5.3 (Medium) | Jira Server and Data Center |
| CVE-2020-14181 | 5.3 (Medium) | Jira Server and Data Center |
| CVE-2020-29453 | 5.3 (Medium) | Jira Server and Data Center |
| CVE-2020-36289 | 5.3 (Medium) | Jira Server and Data Center |
| CVE-2019-3401 | 5.3 (Medium) | Jira Server and Data Center |
| CVE-2021-26085 | 5.3 (Medium) | Confluence Server and Data Center |
| CVE-2021-26086 | 5.3 (Medium) | Jira Server and Data Center |
| CVE-2019-8446 | 5.3 (Medium) | Jira Server and Data Center |
| CVE-2015-8399 | 4.3 (Medium) | Confluence Server and Data Center |
Summary
Atlassian tools such as JIRA, Confluence, Bamboo, and BitBucket play critical roles within organizations. From software development and tracking to documentation, CI/CD, and Git hosting solutions, the amount of historical and confidential data processed or stored within these applications can be extensive; hence they have become a popular target for attackers.
With recent vulnerabilities highlighting security flaws not only in the application stack itself but also within widely used first-party plugins, it has become critical to stay ahead of attackers with automated scanning and detection capabilities.
Recorded Future Attack Surface Intelligence simplifies the task of staying ahead of cybercriminals. With automated and continuous scanning, aided by the knowledge of the latest CVEs and emerging exploits, you have the intelligence you need at your fingertips — and/or in your SOAR automations — to take preventive actions that ensure the safety of your organization's valuable data and infrastructure. Book your free demo today.
Related