Hidden Link Analysis Reveals 92% of Suspicious IPs Not Blacklisted

Immediately Available: Download your free copy of this report now.
Blacklists are a useful and common tool for enterprises actively looking to keep suspicious IP addresses and URLs off their network and away from their infrastructure. Traditional blacklists are populated with information from intelligence feeds, intrusion detection systems, honeypots, and log files. But we at Recorded Future posit that traditional blacklists can be bettered by incorporating threat intelligence from deep and dark Web sources.By scouring the entire Web for mentions of known malware related to specific domains, we were able to identify nearly 1,400 instances of malware-infested domains that were not recognized on established blacklists. Recorded Future analyzed 890,000 documents that mention malware (including Web pages, tweets, and pastes) from nearly 700,000 Web sources that we track with the Recorded Future Web index. This means that 92% of the suspicious IP addresses identified in our project were not found elsewhere on other blacklists!
It’s important to note that in this particular test, the criteria for inclusion was two instances of malware mentions. When looking for suspicious domains with only one associated malware, the number of potential threats increases. Increasing the mentions of malware, we believe, increases the accuracy of the findings, meaning organizations can improve their threat intelligence and threat detection capabilities, and drive down risks.
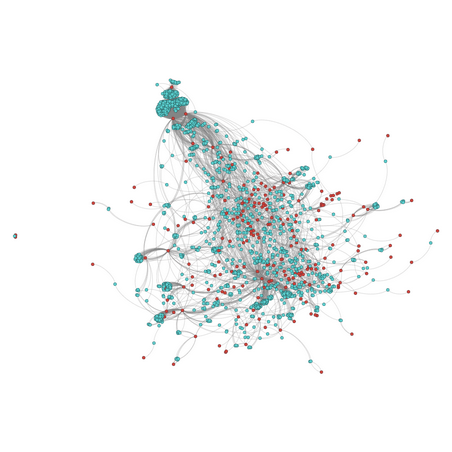
Network graph of 1,521 IP addresses (blue) and 198 malware (red).
To learn more about this threat intelligence research using hidden link analysis, please download the full report "Two Shady Men Walk Into a Bar" or contact us for more information.
Related