Top 6 MITRE ATT&CK Techniques Identified in 2020, Defense Evasion Tactics Prevail [Report]

This report outlines a high-level landscape of tactics and techniques tagged in Recorded Future® Platform data sources as mapped to the MITRE ATT&CK framework over 2020. The data covers January 1 to December 1, 2020. This report is intended for those familiar with the MITRE ATT&CK framework, with particular relevance to security teams that rely on the framework to inform red and blue team exercises, penetration testing, threat hunting, and various security protocol prioritizations.
Executive Summary
In 2020, the six most widely used techniques according to the Recorded Future Platform were T1027 — Obfuscated Files and Information, T1055 — Process Injection, T1098 — Account Manipulation, T1219 — Remote Access Tools, T1082 — System Information Discovery, and T1018 — Remote System Discovery. Additional “Associated Techniques”, or MITRE ATT&CK techniques that were related to the top six, included the following three: T1497 — Virtualization/Sandbox Evasion, T1083 — File and Directory Discovery, and T1036 — Masquerading.
Four of these techniques are categorized under the Defense Evasion tactic, followed by Persistence and Discovery. Seeing Defense Evasion tactics prevail in the data is in line with Insikt Group’s observations that these tactics are becoming more commonplace in malware. Identifying these techniques helps to identify what the cyber threat landscape looked like in the last year: from opportunistic threat actors taking advantage of a remote workforce due to COVID-19 to major expansions of prominent ransomware operators to include exfiltration and extortion. All of the techniques identified were critical to the success of cyberattacks in 2020.
The challenge for defenders is making this information actionable. Detection of some of these techniques can be difficult as more advanced threat actors attempt to hide their true intentions or blend in with normal activities. As mentioned in the MITRE ATT&CK glossary, data should not be viewed in isolation, but rather as a pattern of activity that highlights tactics like Defense Evasion or Persistence. By correlating these techniques with additional high-fidelity events, defenders can find better indications of suspicious activity. We have included detections for both individual malware observed using the highlighted techniques and more high-level detection strategies in this report.
Background
MITRE ATT&CK is a globally accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK framework is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community. With the help of the ATT&CK framework, security teams have a wider picture of adversary behavior, allowing mitigation and detection methods to be tested against the techniques. It has become a useful tool across many cybersecurity disciplines to provide intelligence, track trends in tactics and techniques, perform testing through red teaming or adversary emulation, and improve network and system defenses against intrusions.
The ATT&CK framework has evolved since its publication in 2018, containing almost 200 unique tactics, techniques, and procedures (TTPs). The recent consolidation of the Pre-ATT&CK framework with the main Enterprise ATT&CK framework, as well as the introduction of subtechniques, have only furthered the usability of the framework.
Methodology
In our 2019 report, Insikt Group relied on the Recorded Future Malware Detonation Sandbox as a source for finding top ATT&CK techniques. Based on the changes to the ATT&CK framework and the continued improvement of Recorded Future data, we used three queries in the Recorded Future Platform to aid in identifying the “top” MITRE ATT&CK techniques used in 2020. Data from each query is taken from Insikt Notes, Recorded Future Malware Detonation Sandbox samples, and Attack Vectors as automatically categorized by Recorded Future.
Insikt Group notes cover a wide range of threat intelligence and cyberattacks, which is represented in the first query. The second query, using the Malware Detonation Sandbox sample analysis as a source, provides a technical perspective focused on execution of malware. The third query looks for Cyber Attack events where a MITRE ATT&CK technique was specified as an attack vector to try and capture any additional information. The queries were separated to tune out false positives and to provide a more holistic picture of techniques used.
The mid-year revision of the ATT&CK framework, which included Pre-ATT&CK and subtechniques, created what we believe to be a more accurate and detailed representation of the Cyber Kill Chain from Reconnaissance to Exfiltration and beyond. Insikt Group notes cover pre- and post- exploitation tactics (Reconnaissance, Initial Access, Impact, and so on) by nature of the fact that they cover finished intelligence or “hearsay” (for example, a threat actor claiming to have access to credentials). Malware Detonation Sandbox results, however, are focused on exploitation tactics (such as Execution, Persistence, or Privilege Escalation) based on dynamic analysis of the malicious samples submitted. Attack Vector results are based on Recorded Future’s processing and classification of tactics used in cyberattacks globally, which varied substantially.
Because Insikt Notes, Malware Detonation Sandbox results, and references to Attack Vectors cover different ranges of tactics, the three queries together better capture the full lifecycle of what core techniques were used in cyberattacks in 2020.
Each column below is populated with the top-referenced MITRE ATT&CK techniques per appearance in Insikt Notes, appearance in our Malware Detonation Sandbox source, or association with Attack Vector entities in the Recorded Future Platform. The lists in this table are ordered in descending order of reference count.
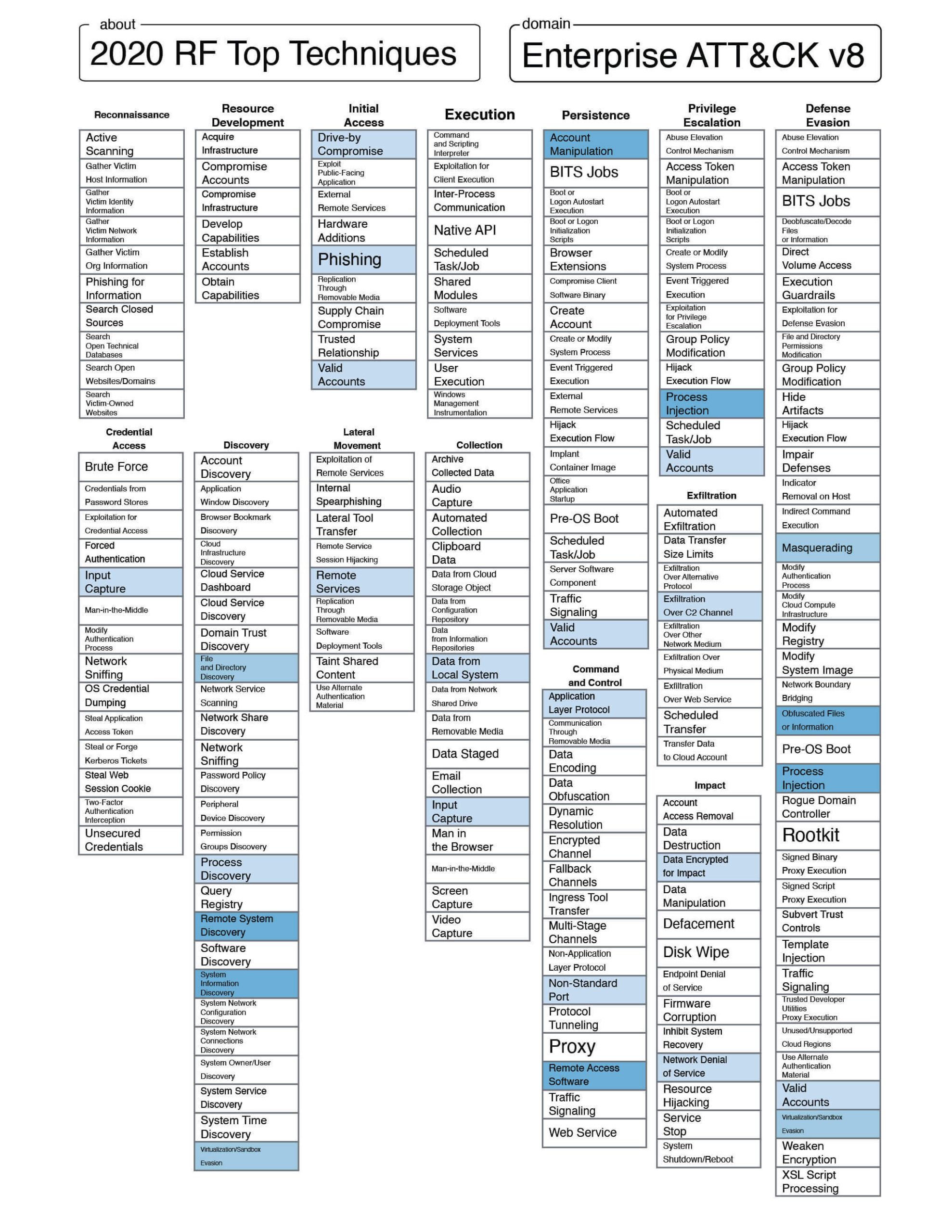
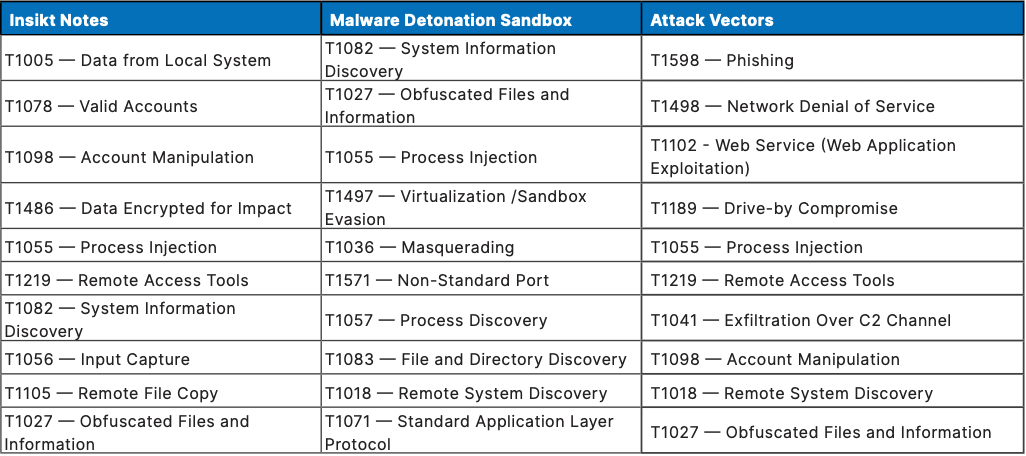
Table 1: Top 10 MITRE ATT&CK Techniques categorized by query (Source: Recorded Future)
Top Six ATT&CK Technique Analysis
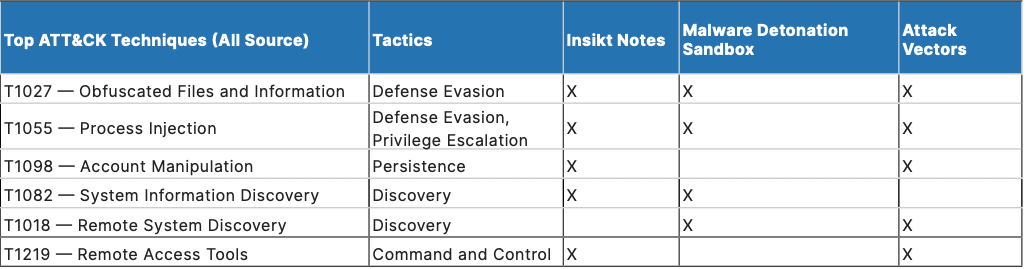
Table 2: Overall Top Six ATT&CK Techniques in 2020 (Source: Recorded Future)
We identified six techniques that were observed in two or more sources, and of those, only two techniques were present in all three source groups: _T1027 — Obfuscated Files and Information_and T1055 — Process Injection. These two techniques, which fall under the Defense Evasion (TA0005) and Privilege Escalation (TA0004) tactics, respectively, have such prolific use among threat actors because they are essential to most successful cyber threat operations, unlike specific techniques such as T1486 — Data Encrypted for Impact, which is only useful to ransomware operators.
The additional techniques, T1098 — Account Manipulation, T1219 — Remote Access Tools, T1082 — System Information Discovery, and T1018 — Remote System Discovery, were present in only two of the three source types. These techniques represent a small fraction of the cyber landscape of 2020, including opportunistic threat actors taking advantage of a remote workforce due to COVID-19 and major expansions of prominent ransomware operators to include exfiltration and extortion.
In line with 2019’s results, the top tactic these techniques share is Defense Evasion. Threat actors deploying ransomware, remote access tools (RATs), or infostealers, will all look to evade detection whether that is through obfuscated files that remain undetected by static file detections, or masquerade as legitimate services through process injection techniques.
Insikt Group has compiled relevant examples of each of the six techniques from the past year, including associated malware, threat actors, and associated techniques. Suggestions for mitigations and detections for each malware mentioned are linked in line.
Additional ATT&CK Technique Analysis and Detections
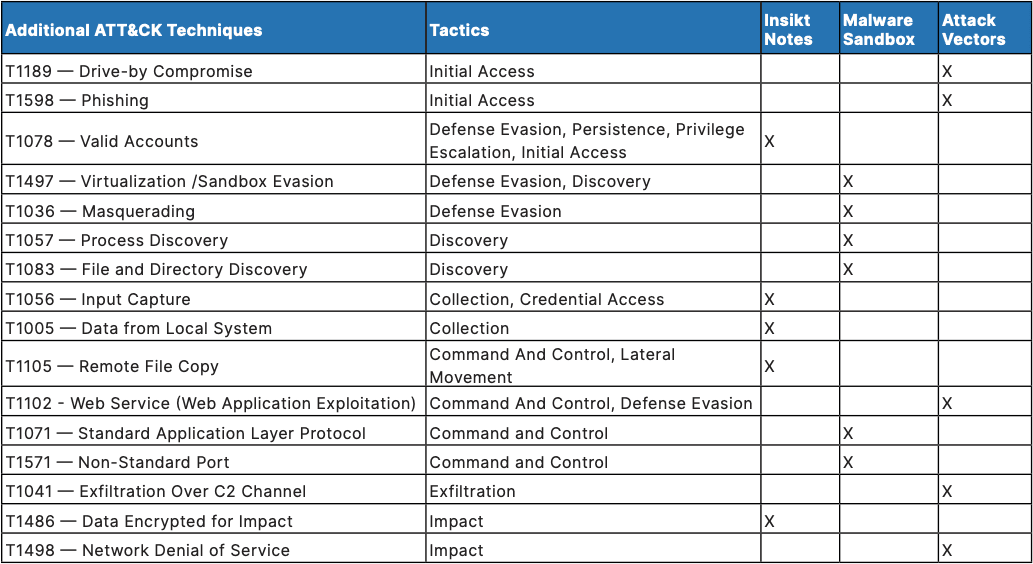
Table 3: Remaining MITRE ATT&CK Techniques as displayed in Methodology (Source: Recorded Future)
Insikt Group identified 16 additional MITRE ATT&CK techniques (Table 3) that were widely used by threat actors in 2020. While they were identified within one of the three queries’ “Top 10” list, they were not present in more than one of the queries and therefore not detailed in the “Top Techniques Analysis” section above.
Some of these are referenced in the “Associated Techniques” subsections, including three techniques mentioned more than once: T1497 — Virtualization /Sandbox Evasion, T1083 — File and Directory Discovery, and T1036 — Masquerading. These techniques, categorized under Defense Evasion and Discovery tactics, derive their references from the Malware Sandbox query.
Detection of these techniques can be difficult as all three incorporate some attempt to hide their true intentions or blend in with normal activities. As mentioned in the MITRE ATT&CK glossary, data should not be viewed in isolation, but rather has a pattern of activity that highlights tactics like Defense Evasion or Persistence. By correlating these techniques with additional high-fidelity events, defenders can find better indications of suspicious activity.
T1497 — Virtualization/Sandbox Evasion is not a new technique, but its use grew last year, manifesting in malware variants like Pysa Ransomware or BABAX Stealer. Detection of T1497 — Virtualization /Sandbox Evasion techniques can be performed with the YARA rule Antidebug_antivm from The Yara Rules Project. This Yara rule detects only a subset of Virtualization/Sandbox Evasion tactic and should be considered a starting point or used in conjunction with other detection techniques or tools.
Detection of both techniques T1083 — File and Directory Discovery and T1036 — Masquerading can be done by monitoring for suspicious activity in your monitoring tools. For T1083 — File and Directory Discovery, there are certain commands typically executed when a threat actor is actively enumerating a network. JPCERT has outlined some of the more common commands abused by adversaries. The commands most relevant to file discovery and enumeration are “dir”, “type”, “net view” and “net use”.
Detections of the commands such as “dir”, “type”, “net view”, and “net use” alone are not enough to alert you of malicious activity, as they are also used by system administrators. However, the execution of those commands combined with the activity of downloading a file from a remote drive within 30 minutes of each other, for example, would be better indicative of malicious activity. In addition to this, a threat actor will likely use multiple Discovery tactics including T1082 — System Information Discovery and T1018 — Remote System Discovery, as we observed in the “Associated Techniques” category.
Similar to T1083 — File and Directory Discovery, detection for T1036 — Masquerading relies on identifying improper use of legitimate applications and tools. The Sunburst malware is a good example of masquerading malware as the code is executed under SolarWinds processes and the code also uses the SolarWinds Orion Improvement Program (OIP) for its C2 communication. Detection of this activity requires understanding the normal behavior of such tools and then identifying anomalies. While the Sunburst malware uses sophisticated techniques for masquerading, detection could still be possible by monitoring outbound connections, or monitoring for activity from SolarWinds processes, users, or hosts indicative of credential harvesting or privilege escalation.
Outlook
The ATT&CK framework is designed to map the lifecycle of a cyberattack to a set of TTPs acknowledged by the cybersecurity community. Defenders can map cyberattacks to this framework to prioritize which techniques to defend against. As network and endpoint defense technologies adapt to the most novel threats, attackers will continue focusing on creating innovative ways to evade detections put in place by defenders. The constant struggle between attackers and defenders is why Defense Evasion remains the most prevalent tactic each year.
While defenders should prioritize tooling and detections to identify attackers during the Initial Access phase to stop the attack before it infects the victim, that is not always possible or easy to do. Defenders should also prioritize the 37 techniques encapsulated by the Defense Evasion tactic, specifically the ones outlined in this report that were most common in 2020. One challenge defender’s face when building detections for a particular Defense Evasion technique such as T1140 — Deobfuscate/Decode Files or Information is the wide variety of implementations attackers use. In these cases, it is more important to focus on the underlying detectable artifacts and behavior hidden underneath the specific technique than the technique itself.
In line with last year’s findings, the second most common tactic after Defense Evasion was Discovery in 2020. The extensive use of the Discovery tactic highlights the common goal among almost all attackers to discover and steal sensitive information. This includes ransomware operators such as those behind Netwalker discovering and exfiltrating data for extortion purposes, info stealers such as FickerStealer looking for Bitcoin wallets, and RATs such as SDBbot running network scans for future lateral movement. Many of the techniques used by threat actors to perform Discovery have legitimate uses, as described above, so defenders should focus on building detections to identify improper use of these legitimate applications and tools.
Identifying techniques encapsulated by the Defense Evasion and Discovery tactics often gives the defender the opportunity to detect an attack during an active operation, which is crucial to mitigating damages. Although these two tactics should be prioritized by defenders, it is still important to build detections for the other 12 tactics. Every time an attacker uses another technique in the ATT&CK matrix, a new opportunity is presented to the defender to detect the malicious activity. Using the mitigations, as prescribed in each section, publicly available ATT&CK-mapped detection mechanisms, and Insikt Group Hunting Packages, defenders can stay up to date with defenses against the latest TTPs.
Related
