How to Build Trust When Assessing Third-Party Risk

Threat intelligence is powerful — it can be used to separate true threats from false positives, find threats before they damage your business, and understand risks originating in an organization's ecosystem. But in order for consumers of threat intelligence to be confident in the decisions they make based on it, they must trust the intelligence they use.
If the purpose of threat intelligence is to provide context that allows security practitioners to make more confident decisions, then it’s essential that consumers of threat intelligence can actually trust that the context is reliable.
There are multiple ways that users of threat intelligence can establish trust in intelligence, but many of these ways are indirect, like relying on the trustworthiness of the source and provider of the intelligence, or on third-party recommendations or community consensus on the value of a source. However, nothing builds trust and confidence in threat intelligence more than transparency into the sources, collection, and analysis of threat intelligence — this allows users to see for themselves “how the sausage gets made” and form their own opinions of threat intelligence coming from different sources and vendors.
For Threat Intelligence, the Key to Trust Is Transparency
Transparency is one of the attributes at the core of our approach to providing threat intelligence that can be trusted to make confident decisions in all areas of security, including security operations, vulnerability management, threat analysis, and vendor risk management. We prioritize transparency so that our clients can trust the intelligence we provide and use it to have maximum impact on the business, informing decisions, reducing overall risk, and proactively preventing attacks.
Earlier this year, we launched our Third-Party Risk module to support teams working in threat intelligence and vendor risk management in their quest to understand the cyber risks associated with their partner ecosystem. Alongside our own customized research, this new offering provides unique insights into threat activity related to third parties, as well as threat actors targeting third parties. All of this information is collected, analyzed, and delivered in our company Intelligence Cards™, which include dynamic risk scores and full transparency into the sources and evidence for each risk score.
Managing Third-Party Risk With Increased Transparency
Now, we’ve taken our commitment to transparency one step further, introducing the ability for organizations to add their own comments and insights into their calculated risk scores. Any client of Recorded Future can add important risk mitigation comments on their own company’s Intelligence Card™, and those insights will be seen and available to all Recorded Future Third-Party Risk clients.
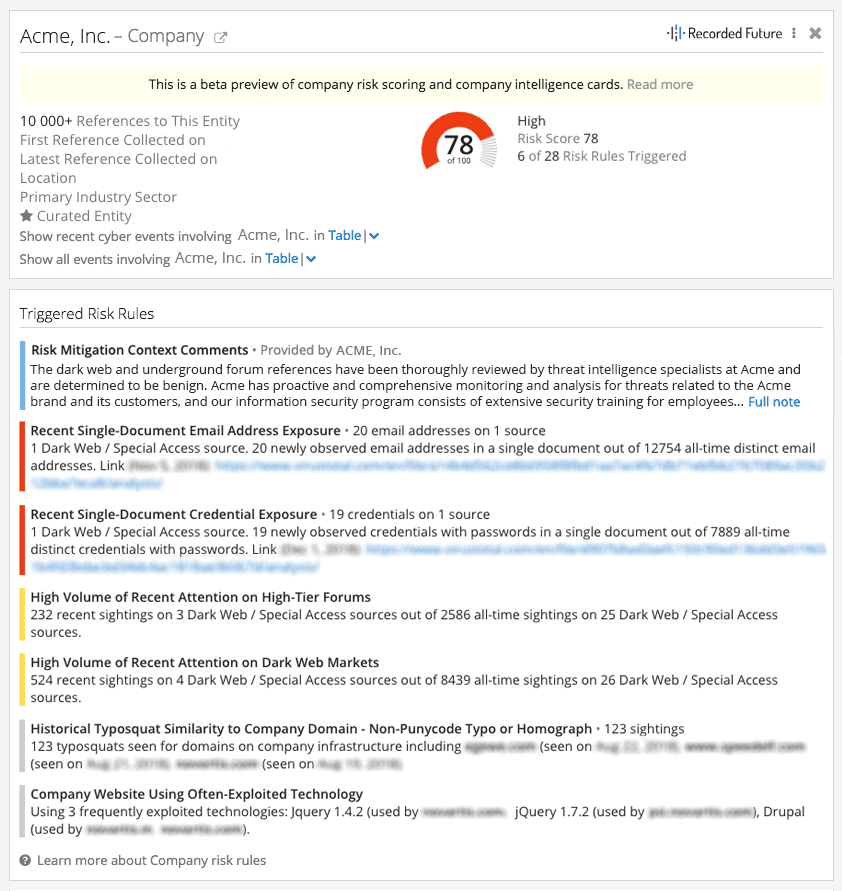
For example, if a company has a known vulnerability in their tech stack that’s raising their risk score, they can note that they have completed patching of the vulnerabilities and provide any other pertinent details. If they are aware of specific threats but have researched, analyzed, and mitigated the risk, then they can note an explanation for interested parties to review.
With this new feature, our clients can transparently communicate their risk mitigation efforts, and for clients assessing risks originating from their third parties, they can better understand the tactics and strategies partners have put in place. Overall, this transparency reduces the time and friction involved with evaluating and addressing risks from third parties. Client comments give them a voice in the presentation of risk information within the Intelligence Card™.
Third-Party Risk clients that are concerned with other clients will see risk rule evidence on their Third-Party Risk Intelligence Cards™ — this risk rule evidence has already been remediated (for example, two-factor authentication has been enabled after a compromise exposed credentials data) and this information can now be communicated directly.
Stay Tuned
The introduction of Risk Mitigation Comments is just one of many new features we have planned for our Third-Party Risk module. Stay tuned for more exciting features coming soon, and in the meantime, feel free to request a personalized demo of Recorded Future.
Related