Vulnerability Cards
Vulnerability Intelligence Cards (aka Vulnerability Cards) provide an on-demand summary of essential information related to a specific Vulnerability, and are updated in real time as Recorded Future collects new information. You can use Vulnerability Cards as a starting point when assessing whether this Vulnerability poses a specific risk to your organization, and further can be used in identifying associated indicators of compromise. Vulnerability Cards are also pivot points during investigations that start with another indicator, a malware, or a threat actor.
Descriptions of several common components of the Vulnerability Card are found in the Overview of Intelligence Cards; the details below are specific to the Vulnerability Card:
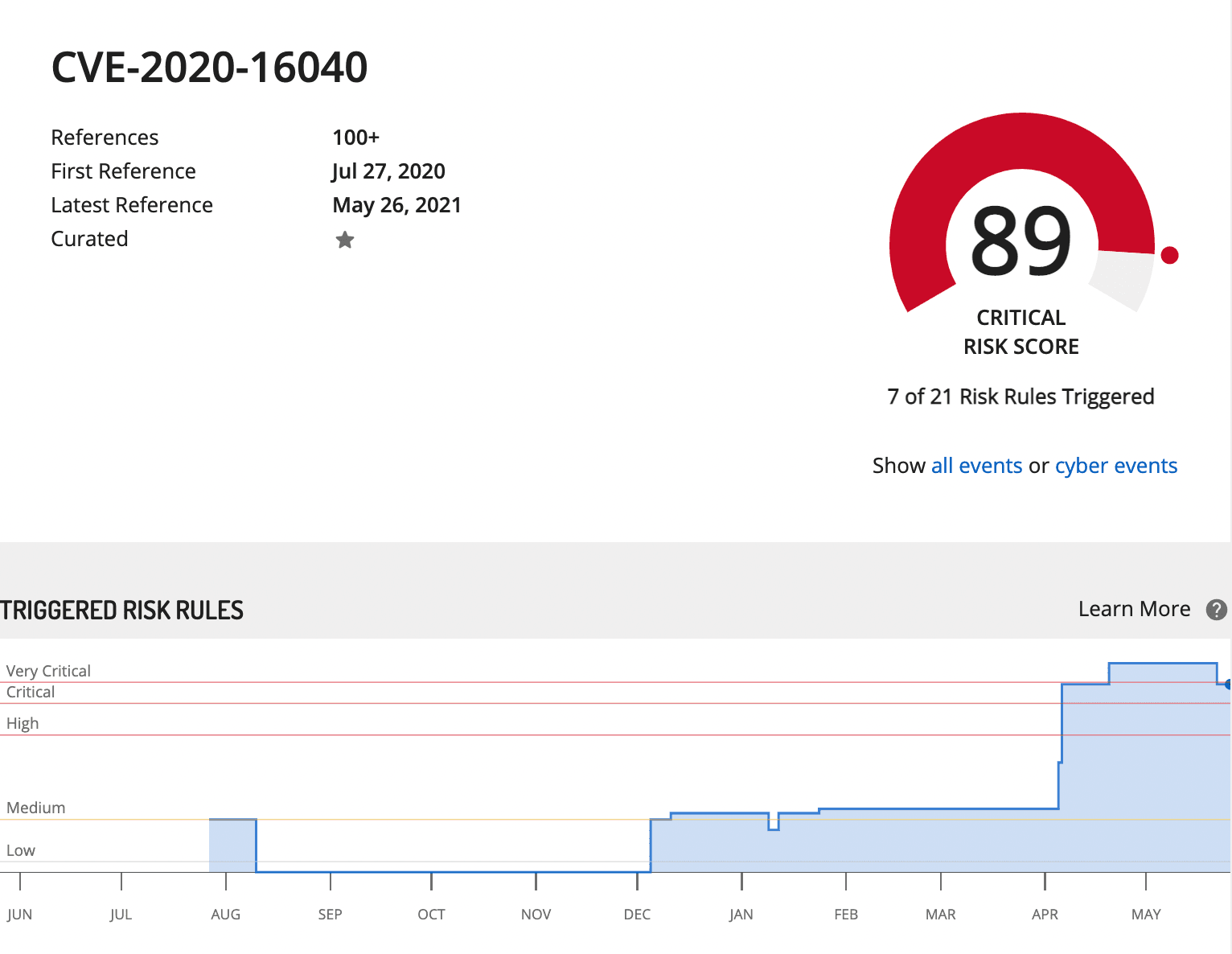
Risk Score and Risk Score History Graph:
For CVEs, the Vulnerability card presents a vulnerability risk score determined by several factors that Recorded Future considers, including the CVSS. More information can be found by looking at the Vulnerability Risk Rules.
|
Each CVE will include a graph that visualizes how the CVE’s risk score has changed over time. Hovering over any day in the graph will display the risk score for the CVE on that given day and indicate the criticality of the CVE on that given day. Using the risk score history graph can help investigate and determine an effective patch prioritization strategy.
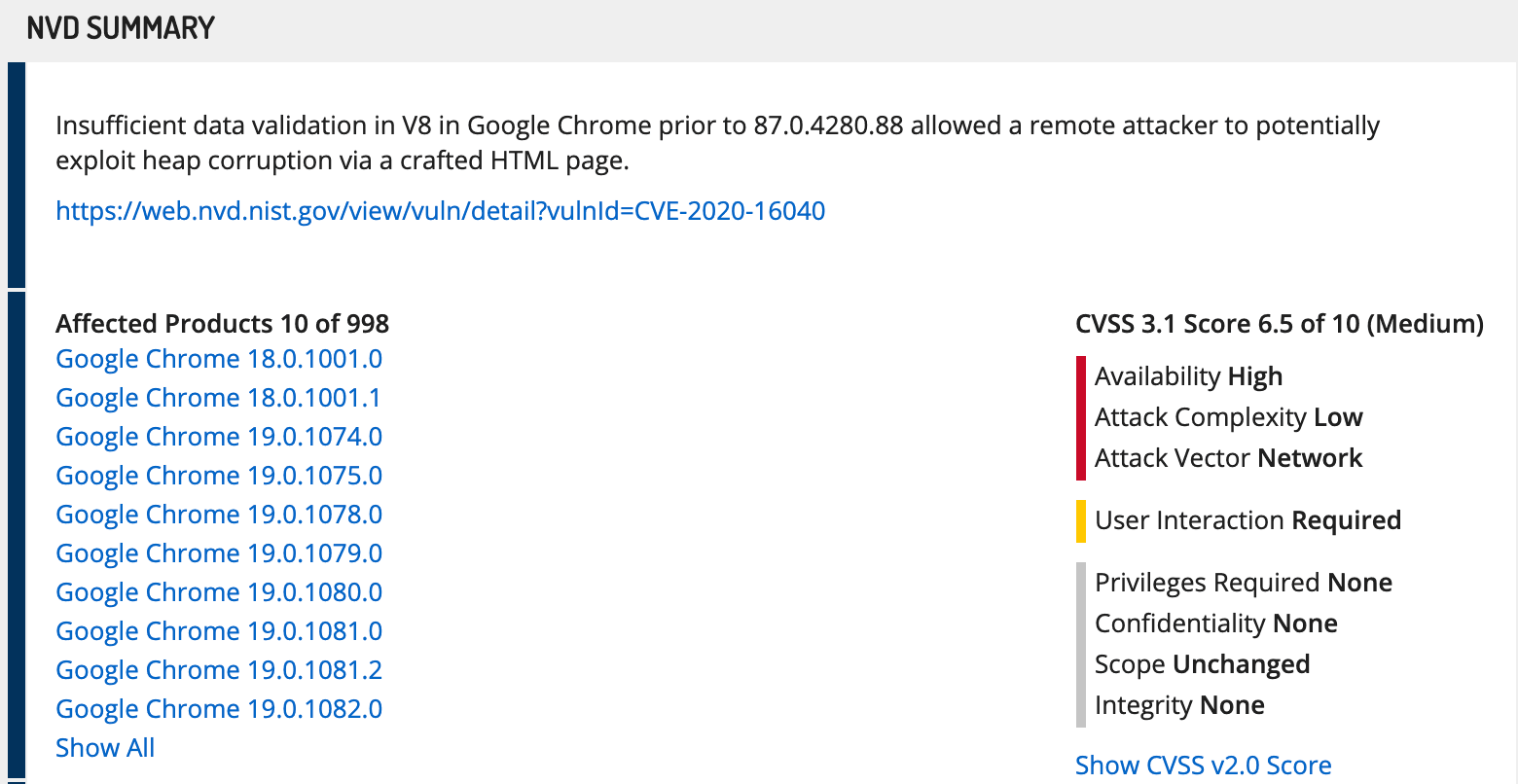
Risk Evidence, NVD Summary, Affected Products, and Notable Links
For CVEs, the Vulnerability card includes the latest information about the CVE published by NIST NVD. This includes the text summary of the vulnerability, the set of affected products in the CPE (Common Platform Enumeration), and notable links as identified by NVD. Affected Products are shown with human-readable names, and you can click on any Product Identifier to see the corresponding CPE identifier and CPE well-formed name.

|
It is common for a very recently disclosed vulnerability to include partial information, while NVD is vetting and confirming portions of the disclosure.
National Venerability Database Summary:
|
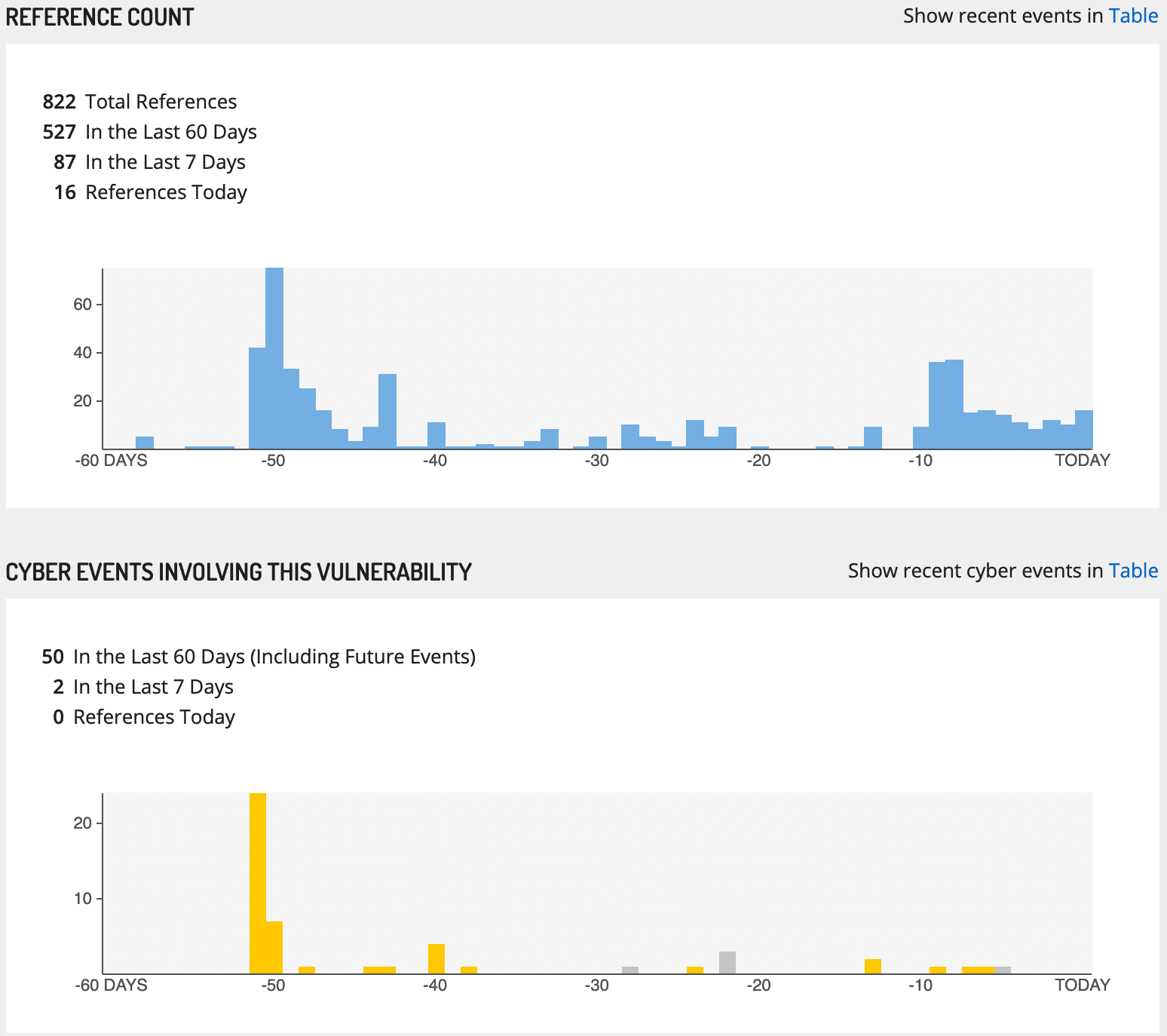
Timelines
Vulnerability Cards may show two timelines. The first timeline, colored in blue, summarizes all reported events involving this entity in the last 60 days. The second timeline summarizes reported Cyber Attack and Cyber Exploit events specifically. Each day in the cyber event timeline is color-coded by the criticality of the Cyber Threat signal for this entity on that date.
|
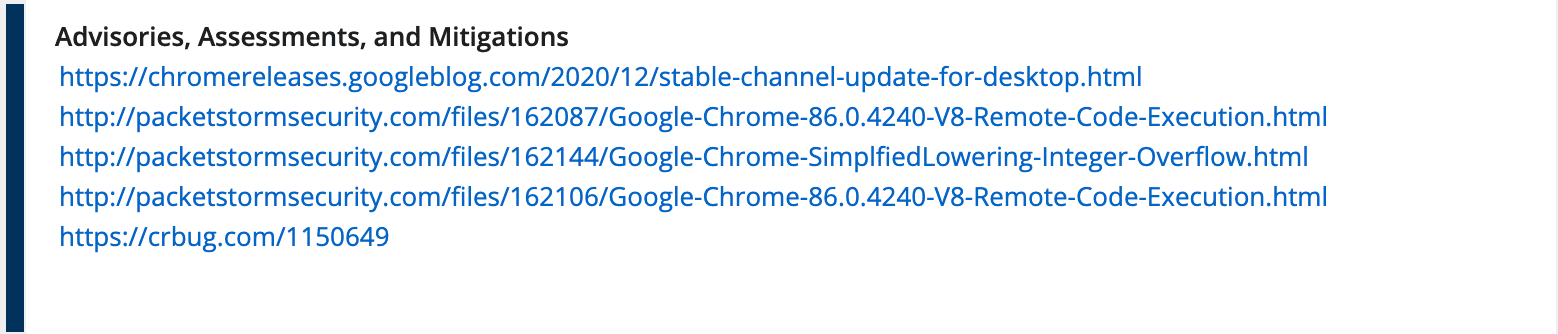
External Links
This section includes links to pages with more information about the vulnerability, specifically around patches and remediations.
|
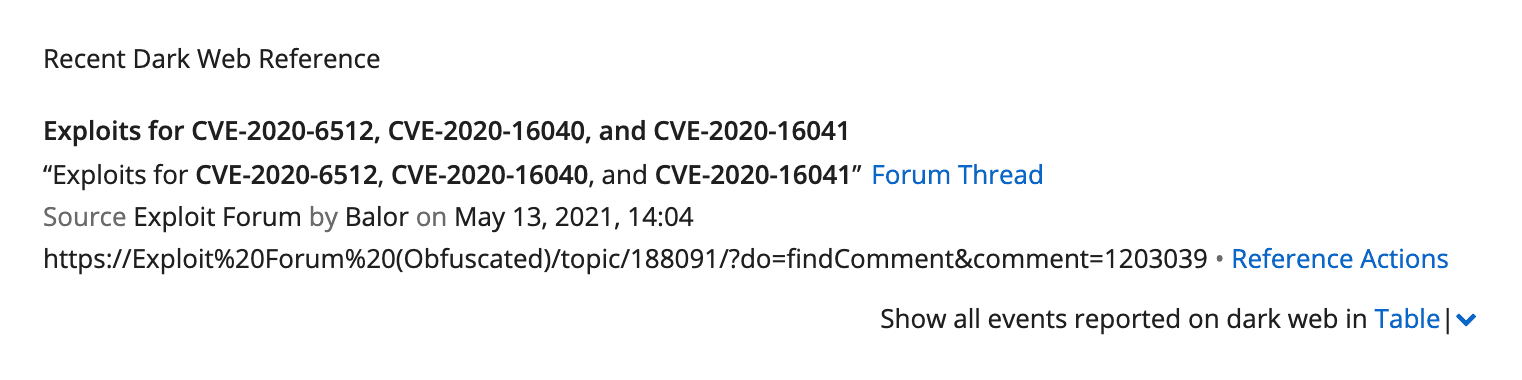
Recent Reference
Helpful lookup of a recent references on the Dark Web for this vulnerability.
|