Two Factor Authentication
- Setting up 2FA on your Recorded Future account
- Setting up 2FA when changing phones
- Resetting 2FA
- Experiencing Issues?
- I am unable to implement Two Factor Authentication
- Additional Support Links
Two-Factor Authentication (2FA) is a security feature that requires users to authenticate using a second means of identification in order to access their account. Recorded Future requires 2FA on all accounts where either Single Sign-On (SSO) has not been implemented, or, for Organizations that have extenuating circumstances where 2FA absolutely cannot be implemented.
If you or your organization have concerns about the ability to use 2FA, please fill out this form and your Recorded Future account team will reach out to you.
Recorded Future’s 2FA security is powered by a Time-Based One-Time Password (TOTP). TOTP is a commonly used method for generating one-time-use passwords. Recorded Future supports most authentication apps that comply with the TOTP standard. Recorded Future’s 2FA has been validated to work with the following Authenticator applications.
Setting Up 2FA on your Recorded Future Account
1. After Recorded Future confirms that 2FA is enabled for your organization, log in using a valid username and password. You will be automatically directed to the 2FA setup page.
Screen_Shot_2020-08-19_at_1.03.14_PM.jpg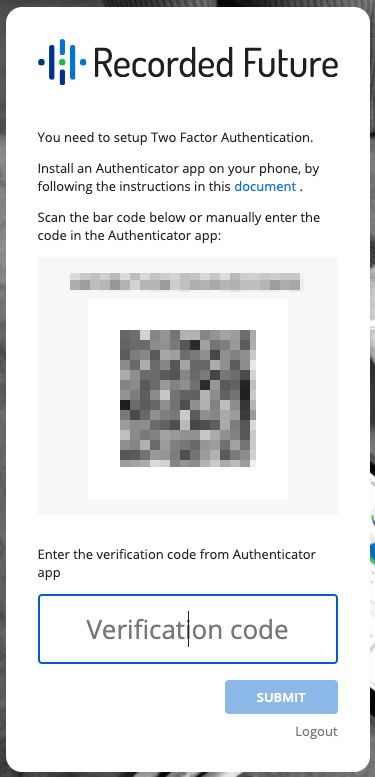
2. Use your TOTP authenticator app to scan the barcode. This stores a shared secret code known to Recorded Future and the authenticator, which is used to generate six-digit verification codes.
3. Your TOTP authenticator will generate a verification code. To confirm receipt of the shared secret, enter the verification code to complete a 2FA setup, and login to Recorded Future.
4. After logging in, you will find scratch codes for your user account in your User Settings page. Scratch codes enable you to reset the 2FA security on your user account if you lose access to the TOTP shared secret.
It is important to store your scratch codes only in a secure, private location.
Setting Up 2FA When Changing Phones
If you're getting ready to change or upgrade your phone, you have the ability to set your new phone up ahead of time for two-factor authentication without any access disruptions.
While logged in to Recorded Future, you have access to scratch codes dedicated to your specific account. You can use these scratch codes and manually enter them into your phone's authenticator application, which can then be used when logging in to Recorded Future at a later date.
While logged in to your account:
- Choose Menu from the top right of your screen
- Click User Settings
- Under User Settings, go to the Security tab
- Once there, your scratch codes will be available below: 
- Use one of the codes in question and enter it as a manual entry in your authenticator application
Resetting 2FA
If you have changed phones and/or forgotten to obtain scratch codes to complete authentication (per the steps above), and there is a Module Enterprise Admin active in your organization, you can request for reset of 2FA. Please follow this process which will alert your enterprise admin to initiate the reset for you.
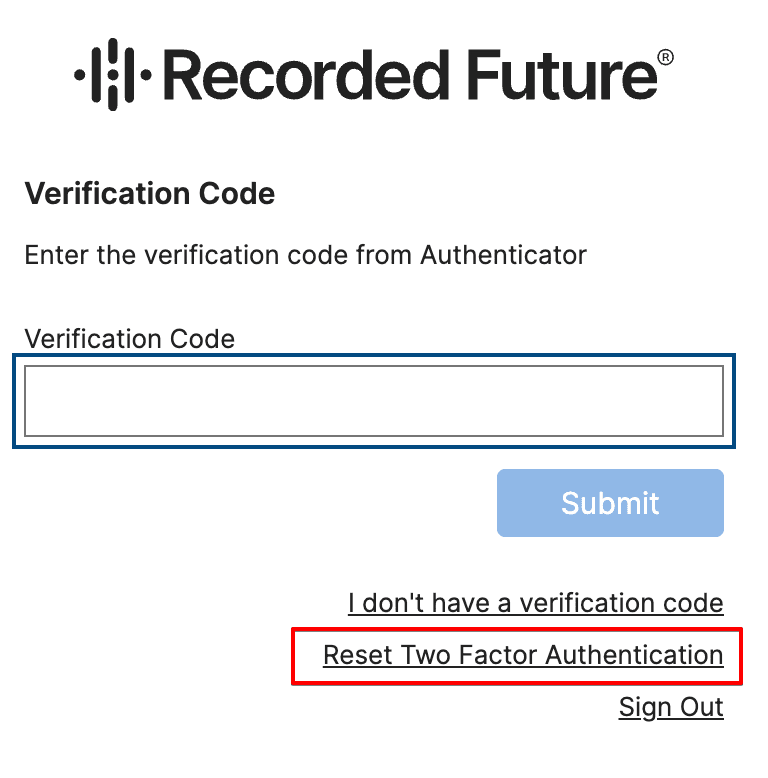
Please note that if you are an existing enterprise admin requesting reset, any other admins on the account will receive the prompt to assist and can help reset, or you can contact support as a last resort.
Experiencing Issues?
Occasionally, users devices may become out of sync with the authentication app. When this happens, the TOTP code generated may no longer be valid with our service. Resetting your phone's time settings may help. Below are suggested instructions for both iOS and Android for resetting your devices time settings
Screen_Shot_2020-08-19_at_1.04.49_PM.png
Resetting your phone's time settings may help:
Android: From within Authenticator
- Go to the Main Menu
- Select Settings
- Select Time correction for codes
- Select Sync now
iPhone/iOS: From within the Settings app
- Select General
- Select Date & Time
- Enable Set Automatically
- If it's already enabled, disable it, wait a few seconds and re-enable
I am Unable to Implement Two-Factor Authentication
If you have security concerns about the ability of your organization to use 2fa, please fill out this form and your account team will reach out to you.
Additional Support Links
Google's 2FA troubleshooting guide Common issues with 2-Step Verification.
Additional TOTP resources for Windows, Android, and iOS can be found on GitHub’s TOTP site.
Multi factor authentication self service reset
Recorded Future offers enterprises the option to manage their own Multi-Factor Authentication (MFA) reset through our enterprise settings tool.
Enterprise admins can reset MFA for other users within their enterprise.If your enterprise does not have a designated Enterprise admin, contact Support to get that set up.
If you are an Enterprise admin you will have access to enterprise settings (marked with red) that can be found under the user icon (marked with blue).
You can reset MFA in two ways:
- User requests MFA reset
- Enterprise admin resets MFA
This article walks you through both options.
User requests MFA reset
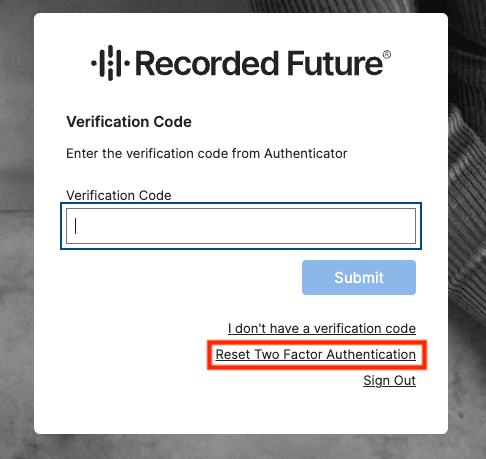
When users are prompted to add verifications codes from MFA, there is an option to request an MFA reset.
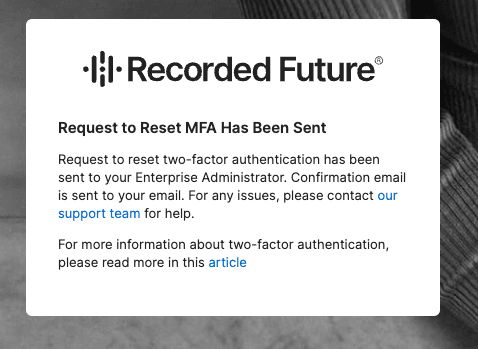
When an end user clicks this button, Enterprise admins within the organization are notified of the reset request via email, which they will also see within their enterprise settings.

At that point, the enterprise admin(s) on the account will receive the following email requesting them to assist with resetting the 2FA for the user who submitted:
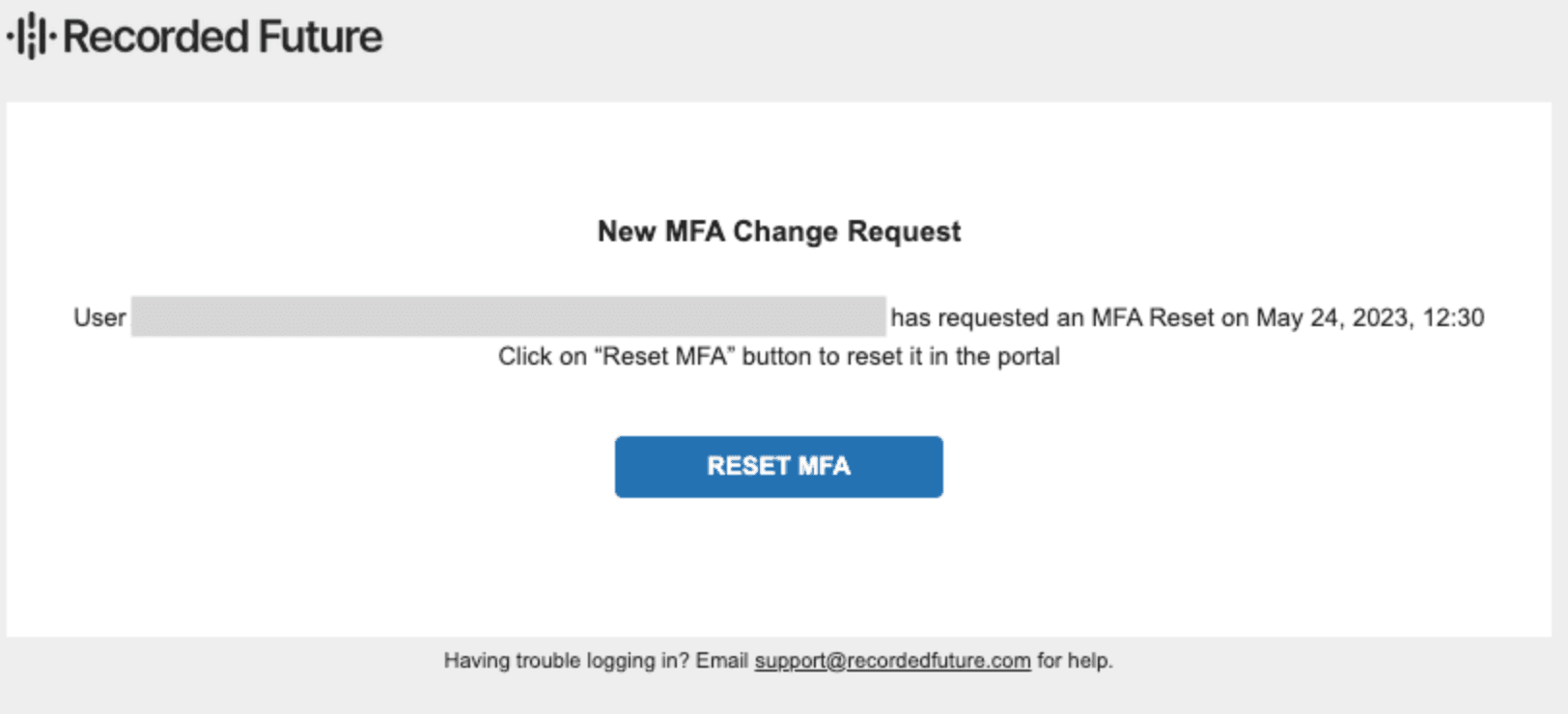
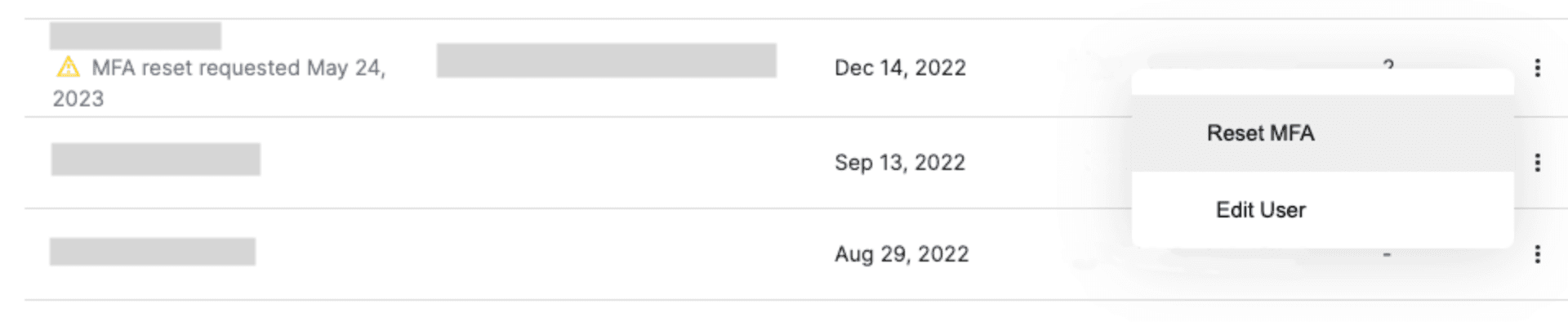
Upon clicking the RESET MFA box, the admin will be presented with a screen to manage user membership. They will then click the three dots on the right side to reset MFA for a user.
The end user will then get an email that their MFA was reset and will be prompted to set up a new MFA when logging in to Recorded Future.
All requests for an MFA reset and the completed resets are logged in the enterprise settings for the enterprise admin, with the last 3 logs appearing under the username. To view additional logs, they can click the number under the logs tab that represents how many logs are connected to the user.
Enterprise admins can also reset a user’s MFA without a request.
Note:
MFA self-management can be turned off for an enterprise if requested, and all MFA resets would need to be completed by Recorded Future Support.