Threat Actor Cards
Threat Actor Intelligence Cards (aka Threat Actor Cards) provide an on-demand
summary of essential information related to a specific threat actor group. Threat
Actor Cards are updated in real time as Recorded Future collects new information.
You can use Threat Actor Cards as a starting point when identifying a threat
actor and making a risk assessment for your organization, or when updating
a risk assessment. Threat Actor Cards are also pivot points during investigations
that start with an indicator, malware tool, or vulnerability.
Descriptions of several common components of the Threat Actor Card are found
in the Overview of Intelligence Cards;
the details below are specific to the Threat Actor Card:
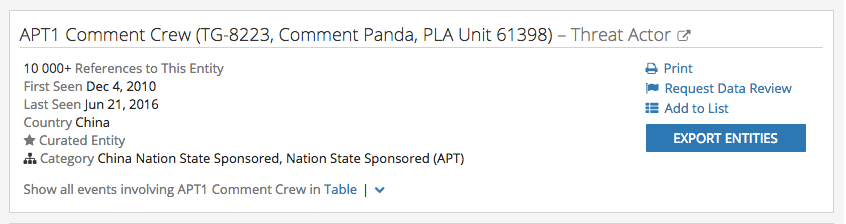
Heading
The heading section identifies the Threat Actor Group. Many cards list multiple names for the same group, as used by different communities of practitioners, researchers, and vendors.
Many Intelligence Cards link threat actors to one or more Threat Actor Categories. These categories organize threat actors into risk areas like financially motivated, nation-state sponsored, and hacking communities. Categories also capture the Country from which the threat actor group is reported to operate. The Nation State Sponsored categories represent APT threat actors who use advanced methods to remain persistent in target networks, often with the objective of exfiltrating high-value data.
Identification, attribution, and characterization of threat actor groups
is notoriously difficult. The assignment of threat actor groups to countries
and categories in Recorded Future is not intended as a definitive statement of
fact. Instead, it captures the consensus or leading hypothesis in the security
community, as observed by our team - or can link a threat actor group to multiple
categories when there are strong competing hypotheses in the security community.
We welcome feedback, suggestions, and critiques on threat actor metadata.
Please use the Request Data Review action to contact us.
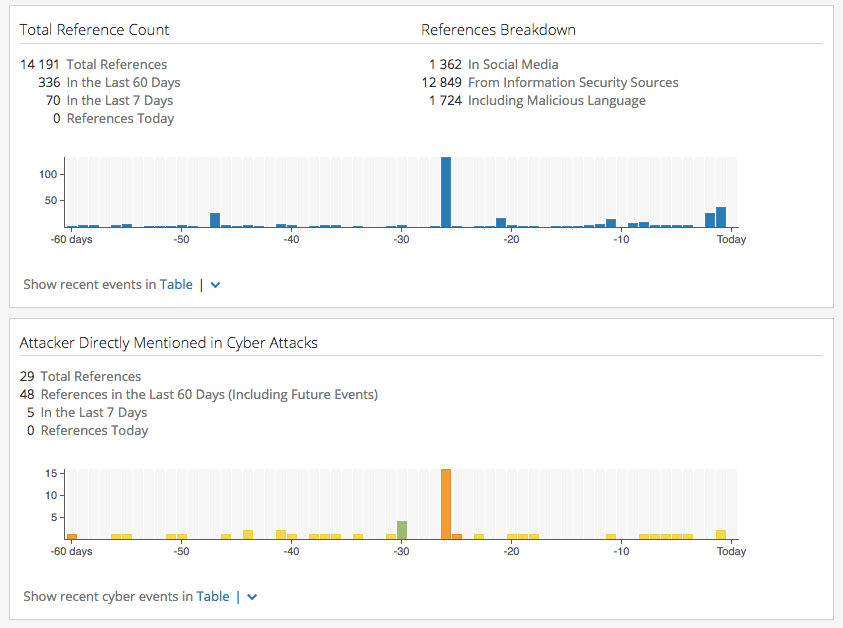
Recent Event Timelines
Most Threat Actor Cards present two timelines. The first timeline section, colored in blue, gives summary metrics for all reporting involving the Threat Actor, and shows a timeline of reporting in the last 60 days.
The second timeline section summarizes reported Cyber Attack and Cyber Exploit events where the Threat Actor was directly reported as the attacker. Each day in the cyber event timeline is color-coded by the criticality of the Cyber Threat signal for this Threat Actor on that date.
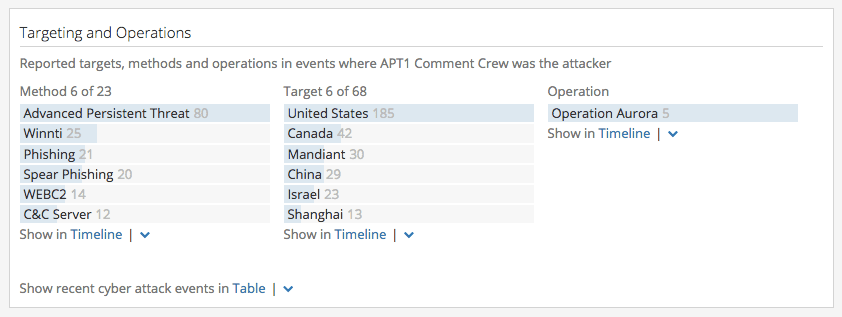
Targeting and Operations
This section summaries Methods, Targets, and Operations or Campaigns from Cyber Attack events where this Threat Actor was directly reported as the attacker. Methods include generic attack vectors, malware tools and malware categories, and vulnerabilities. You can click on any of these top entities to view the events reporting this link. Use the Show in Timeline action to drill down as see more related entities, in the Timeline, Table, Tree Map, etc.
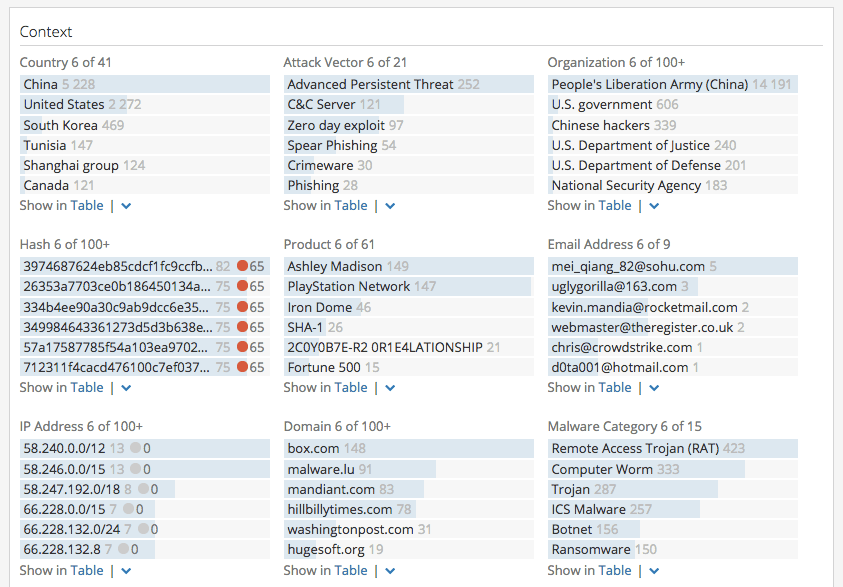
Context
This section summarizes other infrastructure and entities reported with the Threat Actor, organized by entity type. You can view the specific events for each link by clicking on the related entity in the list. Current risk scores are shown where available. You can view more related entities, beyond the top list shown in the Intelligence Card, by clicking the Show in Table action.
Recent References and First Reference
Each Threat Actor Card concludes with a set of individual references, highlighted based on time of reporting (most recent report and first report) or highlighted as the most recent report from an event type or group of sources. These highlighted recent events include Cyber Events, Paste Sites, Social Media, Information Security sources, Underground Forums, and Dark Web sources.