Vulnerability prioritization and mitigation based on risk
Utilize comprehensive data for risk-based vulnerability prioritization. Accelerate patching and enhance security.

60% of breaches are tied to unpatched vulnerabilities and 50% of existing 0-day exploits from 2022 are variants of previously remediated vulnerabilities. Recorded Future's Vulnerability Intelligence provides your security and IT teams access to the most comprehensive database of vulnerabilities and exploits, enabling your organization to accelerate patch management and remediate gaps quickly.

Search the most comprehensive database of vulnerabilities
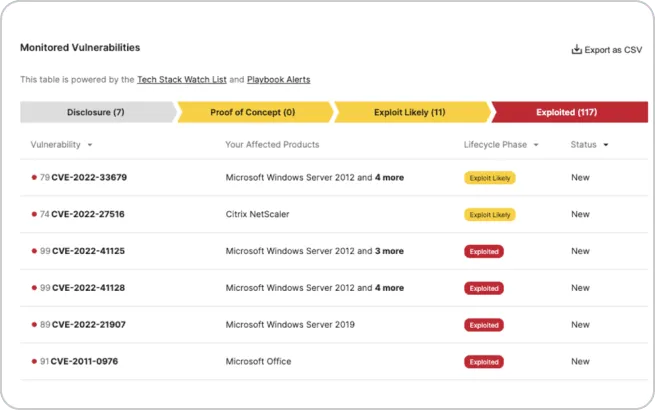
Utilize the most comprehensive and timely database of known and emerging vulnerabilities to your tech stack. Our certified relevant vulnerability sources allow your team to research and identify patches to apply to your environment for remediation with ease.
Get alerted on CVEs pre-NVD
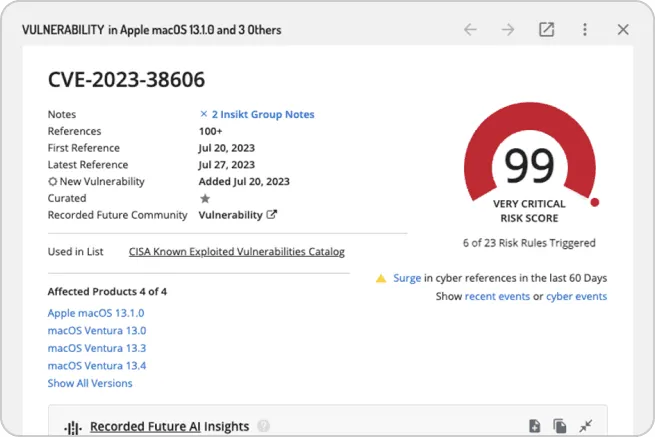
Empower your security and IT teams to get alerts and insights of vulnerabilities not fully known to the public with enriched content. Quick identification and notification paired with enriched context enables your teams to work towards proactive remediation.
Prioritize vulnerabilities based on exploitation
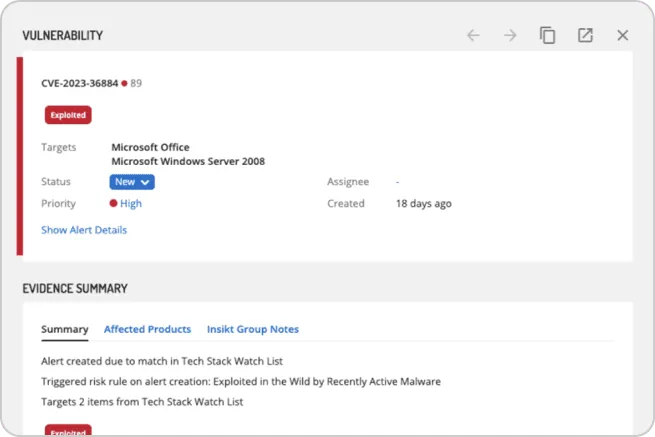
Provide a threat risk score for each vulnerability and identify which vulnerabilities should be prioritized relevant to your company. The Recorded Future risk scoring allows your team to quickly prioritize and take remediation actions on the vulnerability.
Enhance Your Organization's Security Posture and Proactively Defend Against Cyber Threats
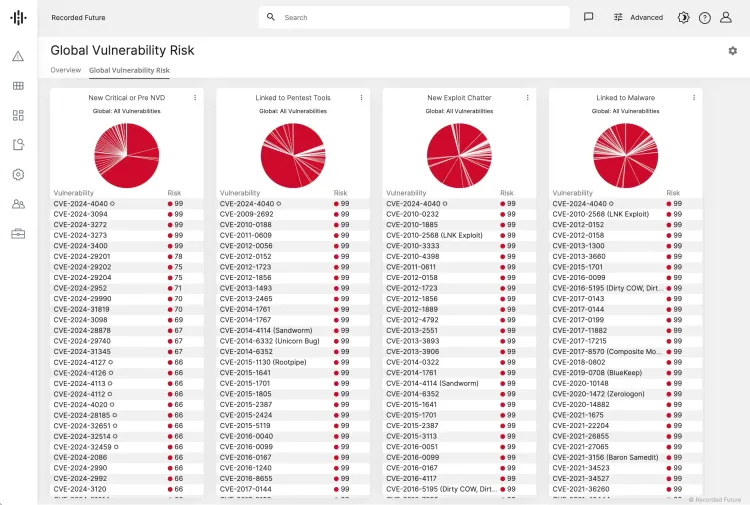
Additionally, leverage Recorded Future's vulnerability prioritization to enhance your organization's security posture and proactively defend against cyber threats. Incorporate vulnerability prioritization into your risk-based vulnerability prioritization strategies to identify and mitigate vulnerabilities effectively, ensuring comprehensive protection of your digital assets and infrastructure.

Key capabilities
- Risk-based patch prioritization
- Evidence-based risk scoring
- Vulnerability lifestyle stage reporting
- Early vulnerability notification (before they hit the public)
- Ransomware dashboard
- Real-time alerting and notification
- Integrations and API endpoints