Bashed and Shellshocked: Early Reports of Exploitation in the Wild

Lots of IT security teams are at work right now to patch the Shellshock vulnerability (CVE-2014-6271) ASAP – while keeping an eye on their threat intelligence sources for exploitation in the wild. And the reports are coming in…
One of the first reports via GitHub identified the IP 162.253.66.76 as the source of suspicious activity. We took a quick look in our OSINT archive, using Maltego, to make an initial assessment. Pentester scanning? Malicious? Looks like the latter.
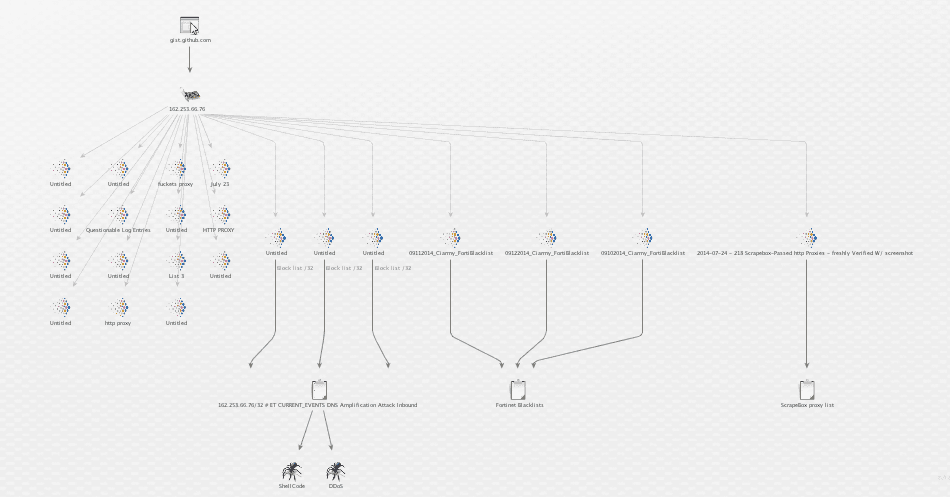
Looked at on a Recorded Future timeline, the reporting involving suspicious activity and blocking of this IP address date back to early September.
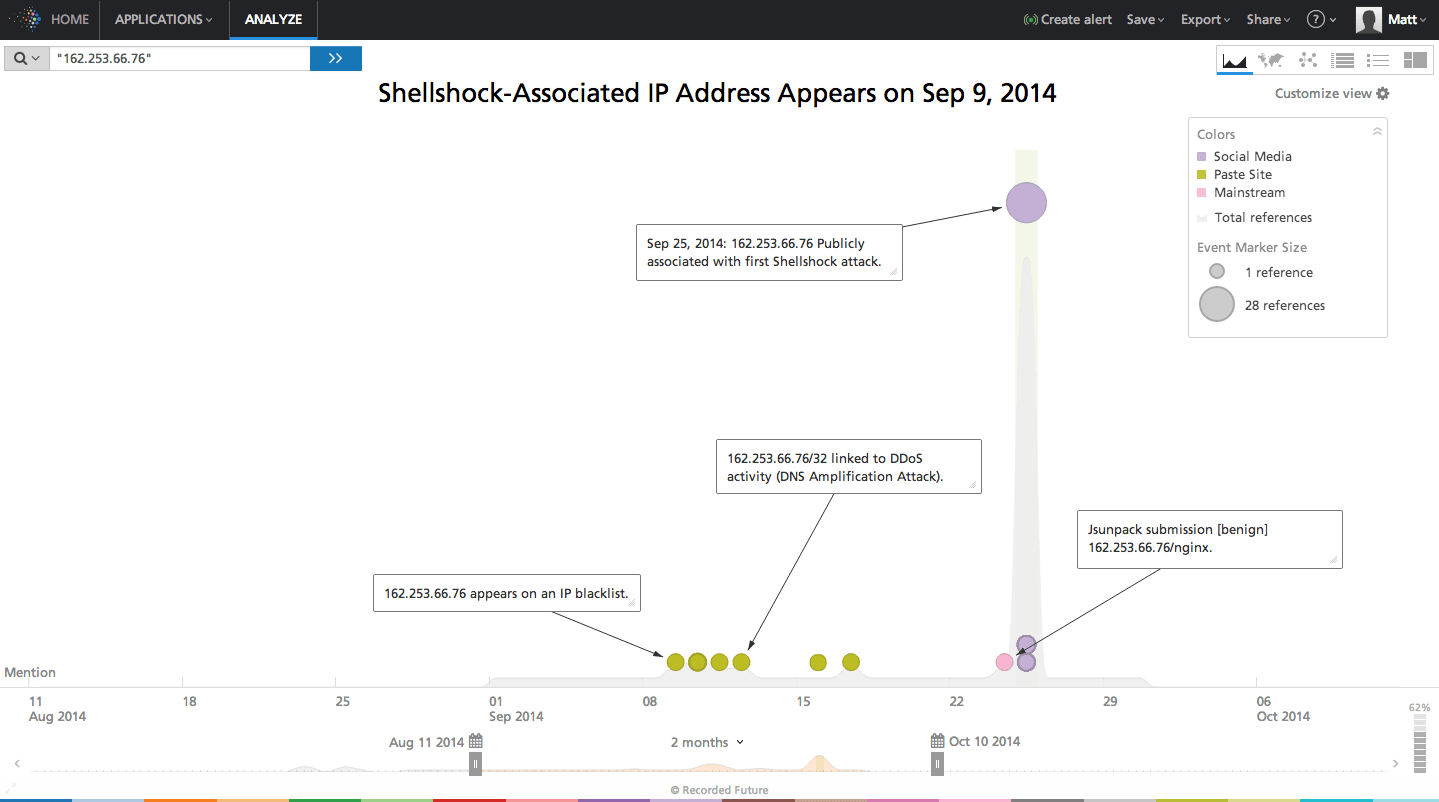
Here’s the view a few hours later, when many other authors on the web were linking this IP address to Shellshock.
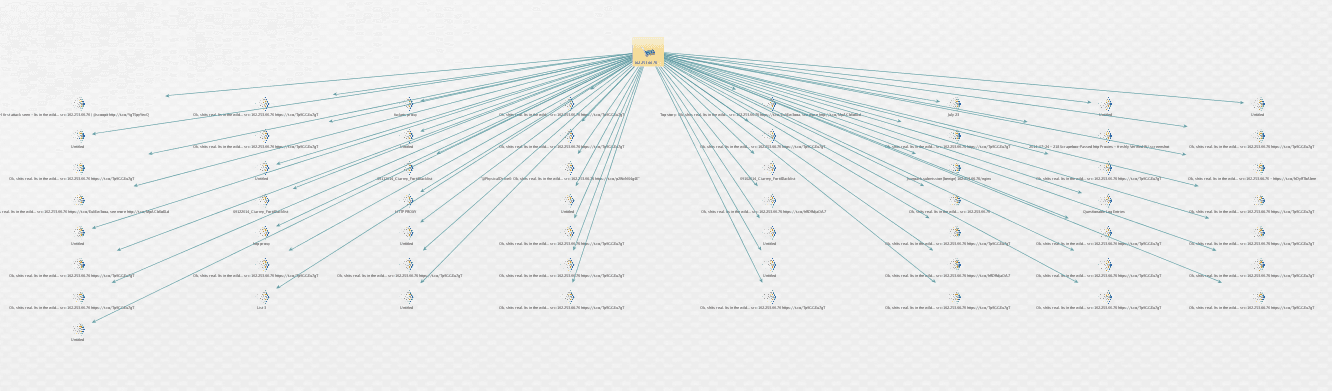
Time to patch!
Related