Russian-Speaking Hacker Selling Access to the US Election Assistance Commission

Key Findings
- On December 1, 2016, Recorded Future identified chatter related to a suspected breach of the U.S. Election Assistance Commission (EAC).
- Recorded Future engaged the Russian-speaking actor (referred to as "Rasputin" in this research) to assess the full scope of the unauthorized access, and provided all relevant information to federal law enforcement.
- Further analysis identified more than 100 potentially compromised access credentials, including some with administrative privileges.
- Rasputin offered to sell an unpatched system vulnerability to a Middle Eastern government broker.
- Recorded Future successfully attributed the EAC breach to Rasputin.
Summary
On December 1, 2016, Recorded Future threat intelligence technology identified chatter related to a suspected breach of the U.S. Election Assistance Commission (EAC).
Further research identified a Russian hacker (Recorded Future refers to this actor as Rasputin) soliciting a buyer for EAC database access credentials.
The EAC was established by the Help America Vote Act of 2002 (HAVA), and among many other responsibilities, the Commission is mandated to test and certify voting equipment, maintain the National Voter Registration form, and administer a national clearinghouse on elections. This includes developing shared practices, distributing information for voters, and providing other resources to improve elections. EAC also accredits testing laboratories and voting systems, as well as conducts a financial audit of HAVA programs.
Assessment
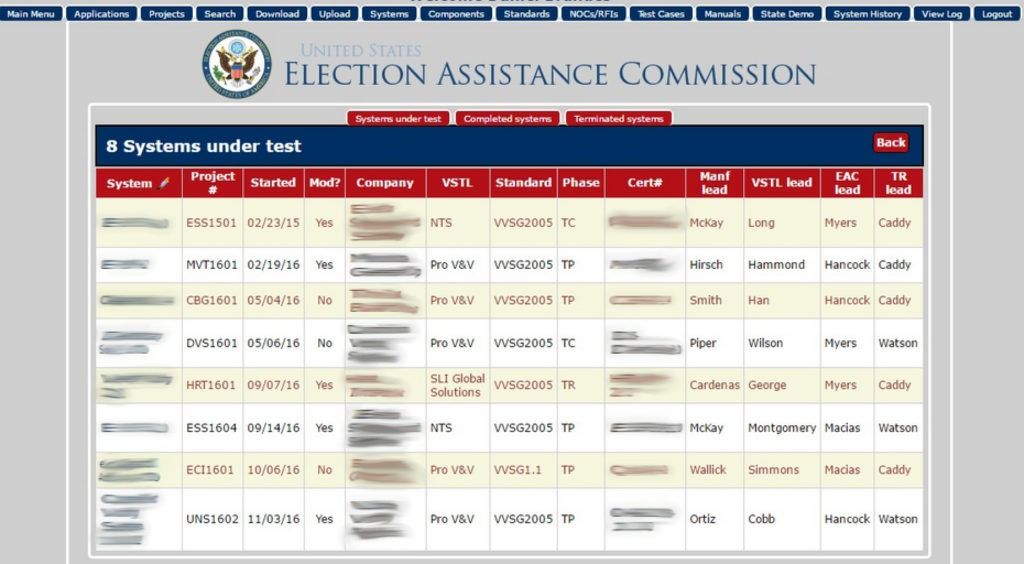
Systems status report page (image provided by Rasputin).
Recognizing the significant implications of such a compromise, Recorded Future provided law enforcement with the necessary data to further assess the potential damage. The breach appeared to include more than one hundred access credentials, including some with the highest administrative privileges. These administrative accounts could potentially be used to access sensitive information as well as surreptitiously modify or plant malware on the EAC site, effectively staging a watering hole attack utilizing an official government resource.
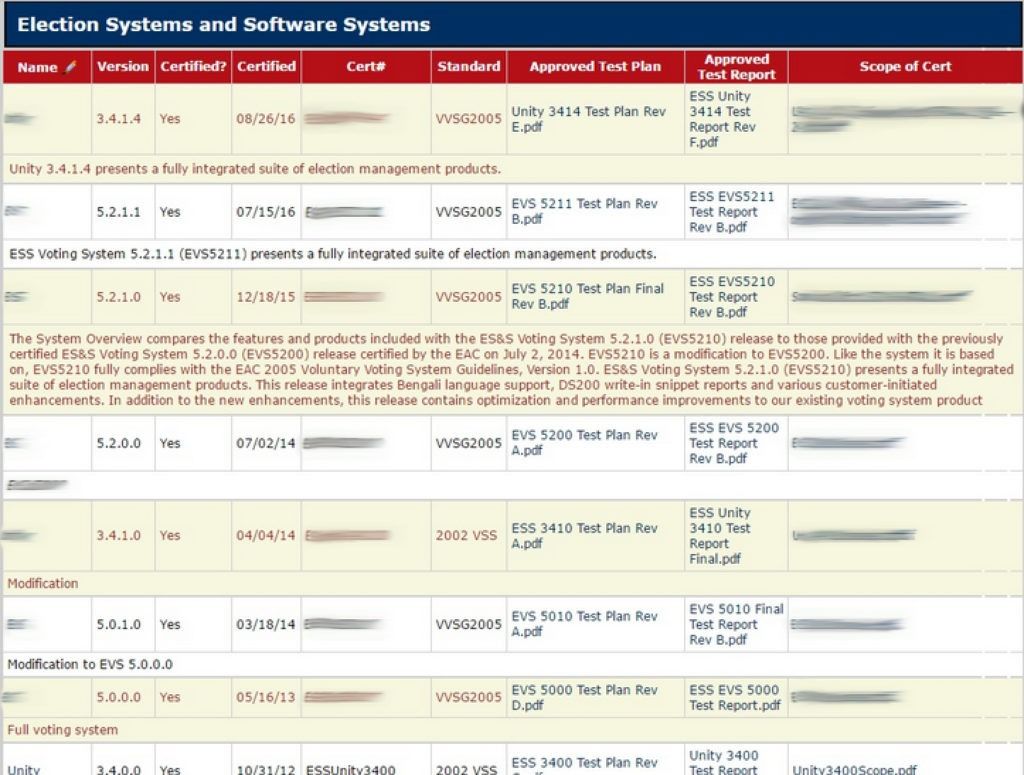
Election and software systems test reports (image provided by Rasputin).
Moreover, in addition to a significant number of highly sensitive records, Rasputin claimed to be accessing the system via an unpatched SQL injection (SQLi) vulnerability. It's not uncommon for this type of vulnerability to lead to broader system level access, however, in this case the full extent of the EAC compromise remains unknown.
Research suggests that the actor was in ongoing negotiations with a potential buyer, on behalf of a Middle Eastern government. Recorded Future successfully identified the penetration source and provided all information to federal law enforcement agencies.
Portal login page (image provided by Rasputin).
Aside from regulatory and equipment-certification procedures, EAC — through its Office of the Inspector General — is supporting both open and anonymous fraud reporting and abuse complaints.
EAC projects reports page (image provided by Rasputin).
The intentional release of this information by an unauthorized party could significantly undermine the public trust in the established confidential whistleblower process.
Recorded Future continues to assist federal law enforcement in the ongoing investigation, as they determine the full extent of the compromise.
Threat Actor Background
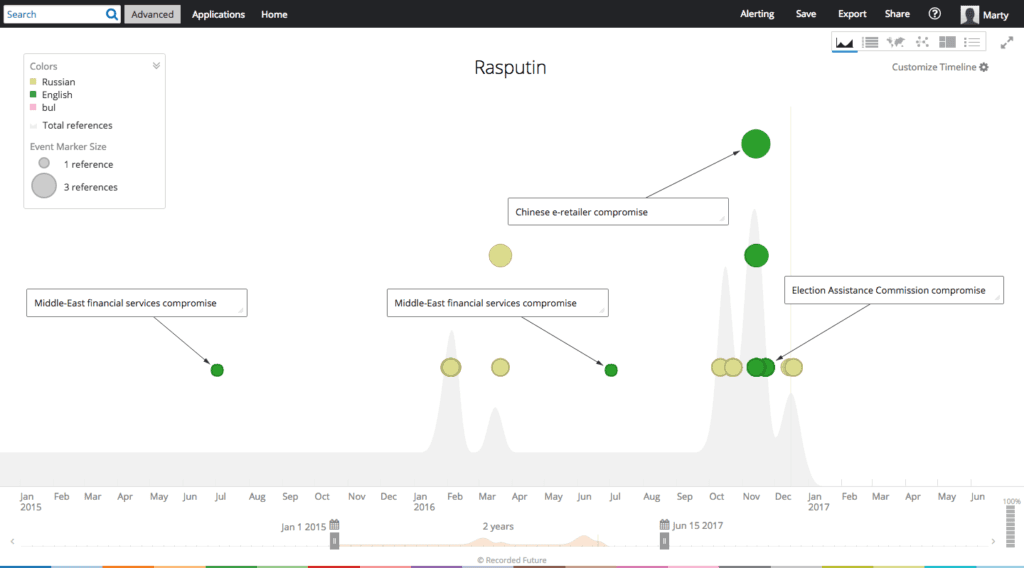
Recorded Future timeline of Rasputin’s activity beginning in 2015.
Related Media Coverage
In December 2015, several security researchers identified the sale of 191 million U.S. voter records by a member of a top-tier Russian underground community.
On October 8, 2016, EAC published a Washington Post op-ed reassuring the public of the full integrity and security of its voting systems.
"To be sure, malicious actors may be looking at the U.S. election system as a possible target. While headlines on this conversation may be new, election officials have been working to secure our voting systems for years. As threats emerge and evolve, those of us who work in elections are responding, adapting, and constantly improving," says Thomas Hicks, Matthew Masterson, and Christy McCormick, of the EAC, in a joint statement.
Conclusion
It's unclear how long the EAC vulnerability has been active; however, it could have been potentially discovered and accessed by several parties independently. Based on Rasputin’s historical criminal forum activity, Recorded Future believes it’s unlikely that Rasputin is sponsored by a foreign government. Recorded Future’s artificial intelligence technology is continuously scanning and analyzing the internet for updated threat indicators and tactics. Prior to this incident, no previous malicious activity related to EAC has been identified.
Disclaimer
Recently, there has been intense reporting about potential Russian efforts to influence the U.S. presidential election. While this blog post may be relevant to informing some of those discussions, we make no claims whatsoever regarding operations run by any Russian intelligence service. Such operations are out of scope for this research and blog post.
This research was initiated by Recorded Future — a threat intelligence company financed by a range of investors that includes In-Q-Tel.
Related