Top 7 Attack Surface Metrics You Should Keep Track Of

Organizations are constantly sprinting to manage and control their scattered workforces and growing attack surfaces. Unfortunately, this is a situation that cybercriminals have been quick to take advantage of; the trend toward complexity and increased interconnectedness of digital systems has brought an increase in potential entry points for malicious actors seeking unauthorized access to networks and systems.
This is why organizations have turned to tangible changes and processes to combat the increased risk of expanding attack surfaces, mainly implementing attack surface management to drive increased security in the face of the increased complexity of their IT infrastructures.
Creating and maintaining an effective attack surface management strategy helps organizations understand the scope of their attack surface, identify risks, attack vectors, and existing attack paths. With these key insights, organizations can prioritize their efforts to protect their most critical assets.
If you’re looking into implementing a proactive attack surface management strategy as well as a solution, it’s important to identify and understand the main drivers needed to ensure that your approach is effective, comprehensive, and empowering enough to truly improve your security posture.
Popular attack surface metrics to track
Tracking attack surface metrics can allow you and your security team to productively monitor your attack surface over time, measure the effectiveness of your attack surface management efforts, and better steer future decision-making regarding cyber risk.
We’ve highlighted the top 7 attack surface metrics you and your security team should be aware of:
1. Total number of assets
Accelerated digital transformation is the new normal, meaning a continuous stream of ever-changing IT assets. These include cloud applications, IoT, third-party code libraries, development and staging domains, VPN endpoints, and more. Any of these assets can introduce security risks to your infrastructure.
Besides providing powerful insight into the actual size of your internet-facing infrastructure, continuously tracking the total number of assets is also the key to understanding usage patterns and spotting irregularities. Additionally, knowing the total number of assets can help CISOs track the size of their infrastructure over time and inform future decision-making regarding digital transformation.
2. Newly discovered assets
In addition to the current and total number of assets, the number of newly discovered IT assets is an equally important attack surface metric to track.
Just as organizations utilize various applications, domains, and databases, malicious actors continuously scan these assets' IPs and open ports. And with new assets being constantly added to your infrastructure, one simple oversight on your part—on an asset that holds a vulnerable exposure—can present an entry point for attackers interested in your sensitive data. Based on your organization’s monitoring capabilities, knowing the number of newly discovered assets in a day allows your security team to find any potentially vulnerable exposures before attackers do. Newly discovered assets can be categorized and tagged to understand their location, ownership, and running services, which indicate whether an asset could be holding risks.
Tracking newly discovered assets is also important in the event of a security incident. When an incident occurs in a large, complex IT environment, it can be challenging for security teams to pinpoint where the intrusion occurred and begin remediation. Knowing how many new assets were added, and on which day, can simplify the analysis process and reduce the pool of data that needs to be examined.
3. Number of exposed assets
While maintaining an accurate inventory of all assets is an important attack surface metric, it would be misleading to assume that all assets contribute equally to the attack surface. Furthermore, in an increasingly digitized world, securing every asset equally is simply not an option. Thus, knowing how many assets are exposed to critical risks is crucial for effectively implementing security controls.
Tracking the number of exposed assets is also crucial to attack surface reduction. Smaller targets are harder to hit, and you want to make each entry point of your attack surface more difficult to compromise. This metric also allows for tracking the growth of the attack surface and can steer decision-making regarding security risks and future ASM efforts.
4. Mean time to detect (MTTD)
Mean Time to Detect (MTTD) is a metric used in incident management to measure the average time to detect an issue or incident. It is the average time between the occurrence of an incident and the point at which it is detected. MTTD is often used with metrics such as Mean Time to Respond (MTTR) and Mean Time to Resolve (MTTR) to provide a comprehensive picture of an organization's incident management performance.
MTTD is an important metric because the faster an incident is detected, the quicker it can be addressed and resolved—this helps minimize the incident's impact on the organization and its customers. Additionally, a low MTTD can help identify areas of weakness in an organization's incident detection process, allowing for improvements to reduce the time taken to detect future incidents. Calculating an organization's MTTD entails taking the time between an incident and its detection divided by the number of incidents during a specific period.
5. Mean time to remediate (MTTR)
While acting proactively and securing your infrastructure from attacks is the goal, having proper incident response and security measures if an attack occurs is equally important. Limiting the time attackers have to cause damage to your network can reduce risk. The mean time to remediate (MTTR) tracks the time from a security event’s first appearance to the moment a security control has been put in place for it. Resolving incidents and exposure quickly and efficiently is an important metric, and the size and complexity of an attack surface directly impact it.
Organizations can improve their MTTR by maintaining complete visibility over their infrastructure. This is tremendously important for being immediately alerted towards any exposures and for having actionable information ready to triage and remediate the issue as quickly as possible.
6. Criticality of risks
Another key component in understanding your digital risk profile is measuring the criticality of risks on your exposed assets. Knowing that vulnerabilities and exposures exist in your infrastructure is not enough. Just like assets, not all risks should be treated equally, as they have different potentials for damage in the event of an attack. You need to be able to see risks and vulnerabilities in the context of threats to your attack surface to empower more accurate and timely decisions.
Risk assessment is an integral part of any attack surface management strategy. By applying threat-level context to risks, you can prioritize where you allocate your mitigation resources and focus on the most critical risks first. Furthermore, keeping track of the criticality of risks will give you better insight into your digital risk profile, how it changes over time, and how your attack surface management efforts are progressing.
7. Number of hosting providers
During asset discovery, security teams often encounter questions about the number of hosting providers, locations, and alignment with any existing security policies. This exact knowledge is crucial when evaluating the attack surface because it directly impacts the security posture of the entire organization.
It's important to note that web hosting providers have varying security controls, policies, and certifications for the data they host, infrastructure, and network. Some providers have a history of extensive security breaches, are more susceptible to large DDOS attacks, or don't offer adequate privacy controls due to being hosted in countries with lenient data protection laws. Therefore, understanding the number and location of different hosting providers is crucial for analyzing the attack surface, providing valuable insights into potential vulnerabilities, and informing risk mitigation strategies.
How can you keep track of your attack surface metrics? Enter Attack Surface Intelligence
Attack Surface Intelligence is the Swiss Army knife of external attack surface management. Monitoring and measuring exposure levels via the attack surface allows organizations to align with an established security posture. And by actively tracking potential threats that could lead to a successful attack against the organization’s assets or data, Attack Surface Intelligence services are valuable to organizations looking to expand their security program.
With Attack Surface Intelligence, you’ll be able to get important attack surface metrics in an instant, allowing you to:
- Gain complete oversight over all assets in your attack surface
- Track newly discovered assets by day, and keeping your inventory updated
- Highlight all exposed assets and score the criticality of their exposure
- Maintain a complete digital risk profile with risk severity to allow prioritization
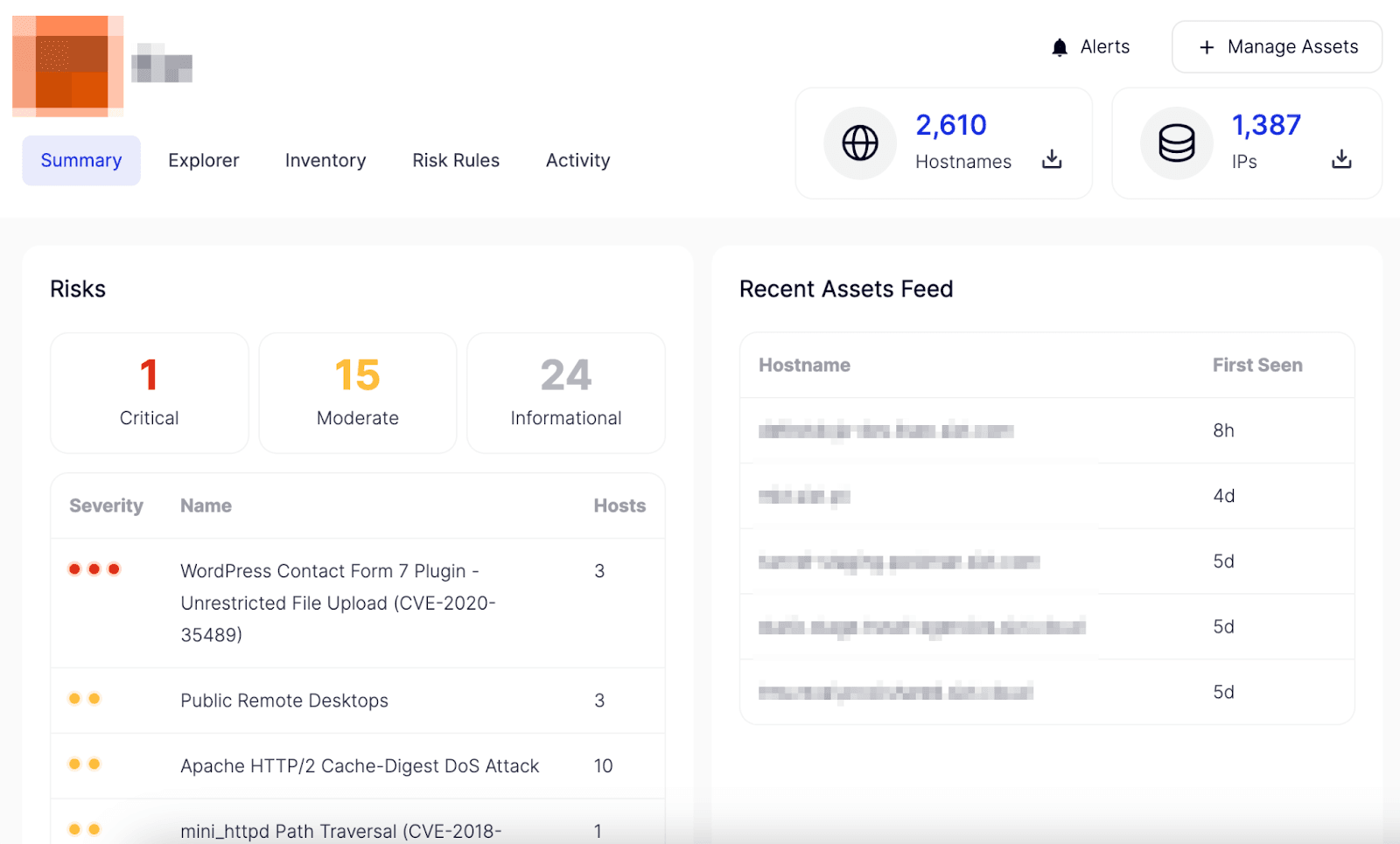
Take back control of your attack surface and ensure comprehensive risk management with Attack Surface Intelligence. If you’re interested in how Attack Surface Intelligence can empower your attack surface management efforts, see it in action — book a demo now!
Related