OilAlpha: A Likely Pro-Houthi Group Targeting Entities Across the Arabian Peninsula
Since May 2022, Insikt Group has tracked an ongoing campaign by the threat group, OilAlpha,; which we are linking to threat actors that likely support a pro-Houthi movement agenda.
The group is highly likely to have targeted entities associated with the non-governmental, media, international humanitarian, and development sectors. It is almost certain that the entities targeted shared an interest in Yemen, security, humanitarian aid, and reconstruction matters. The group’s operations have reportedly included targeting persons attending Saudi Arabian government-led negotiations; coupled with the use of spoofed Android applications mimicking entities tied to the Saudi Arabian government, and a UAE humanitarian organization (among others). As of this writing, we suspect that the attackers targeted individuals the Houthis wanted direct access to.
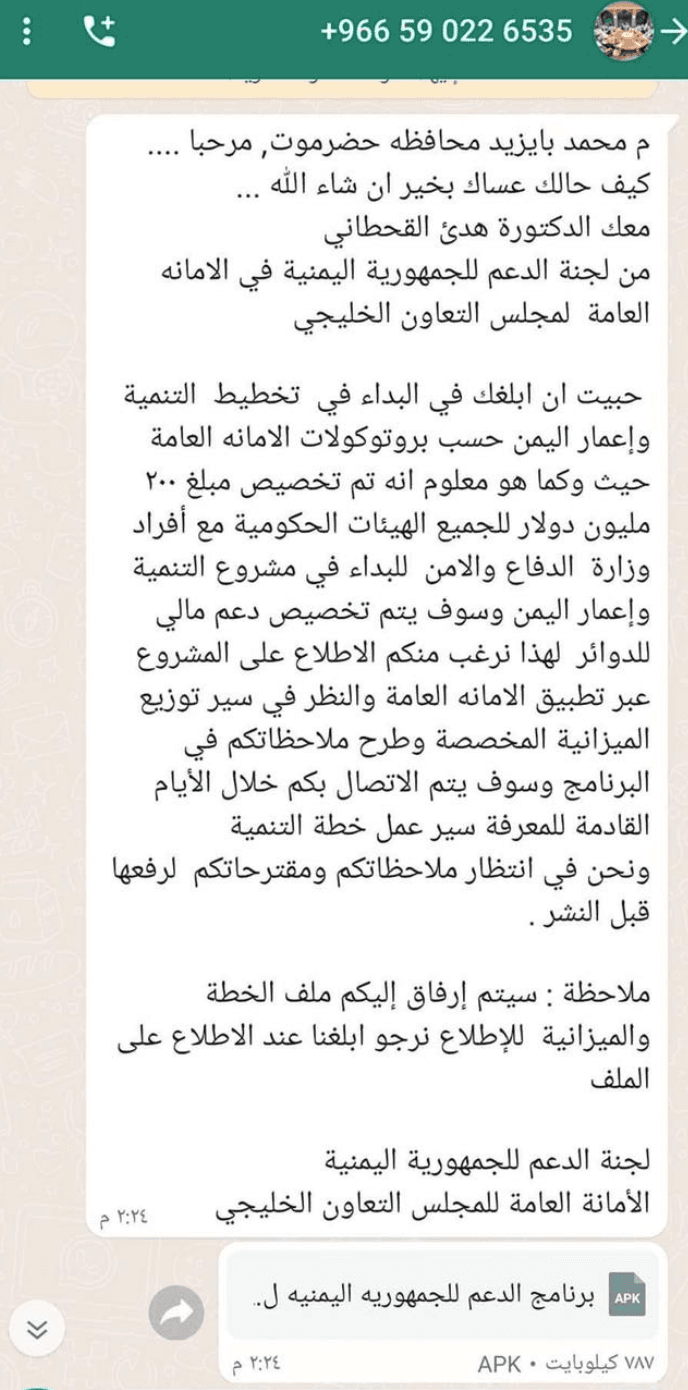
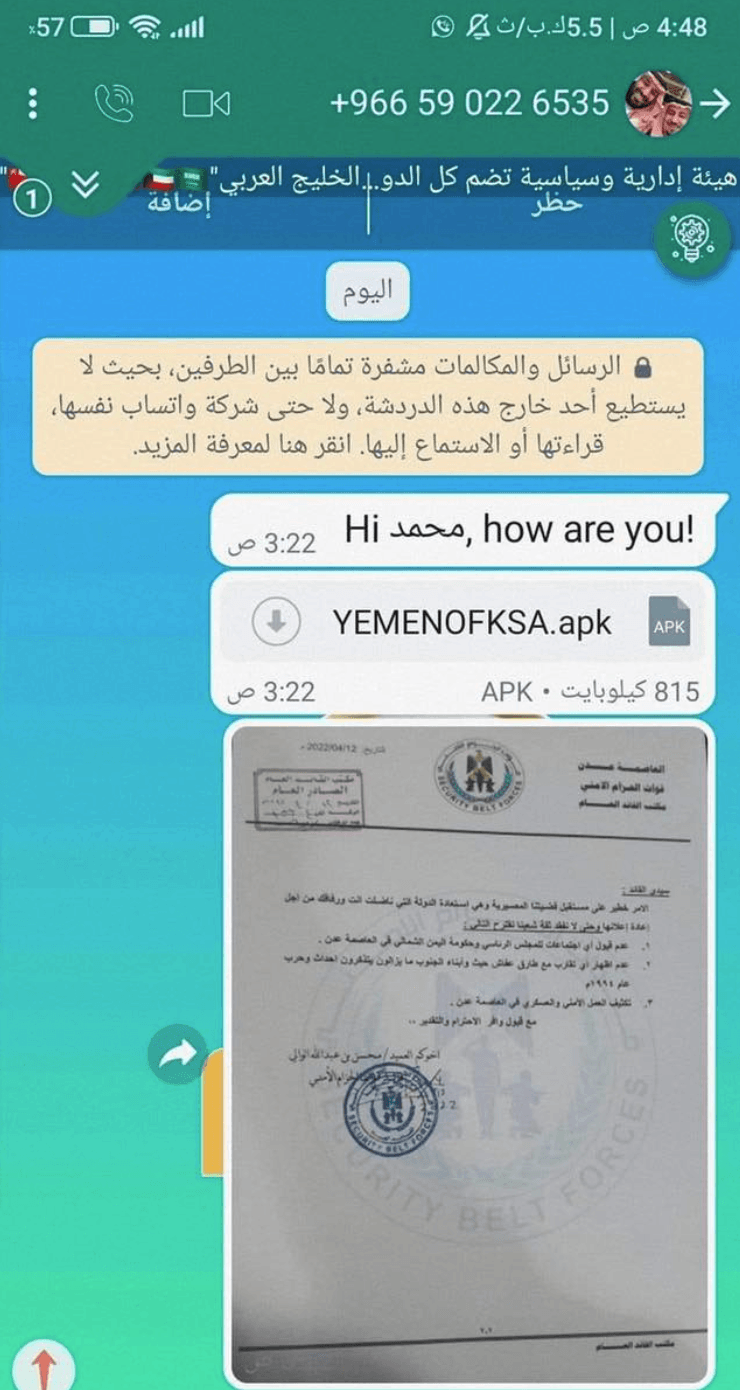
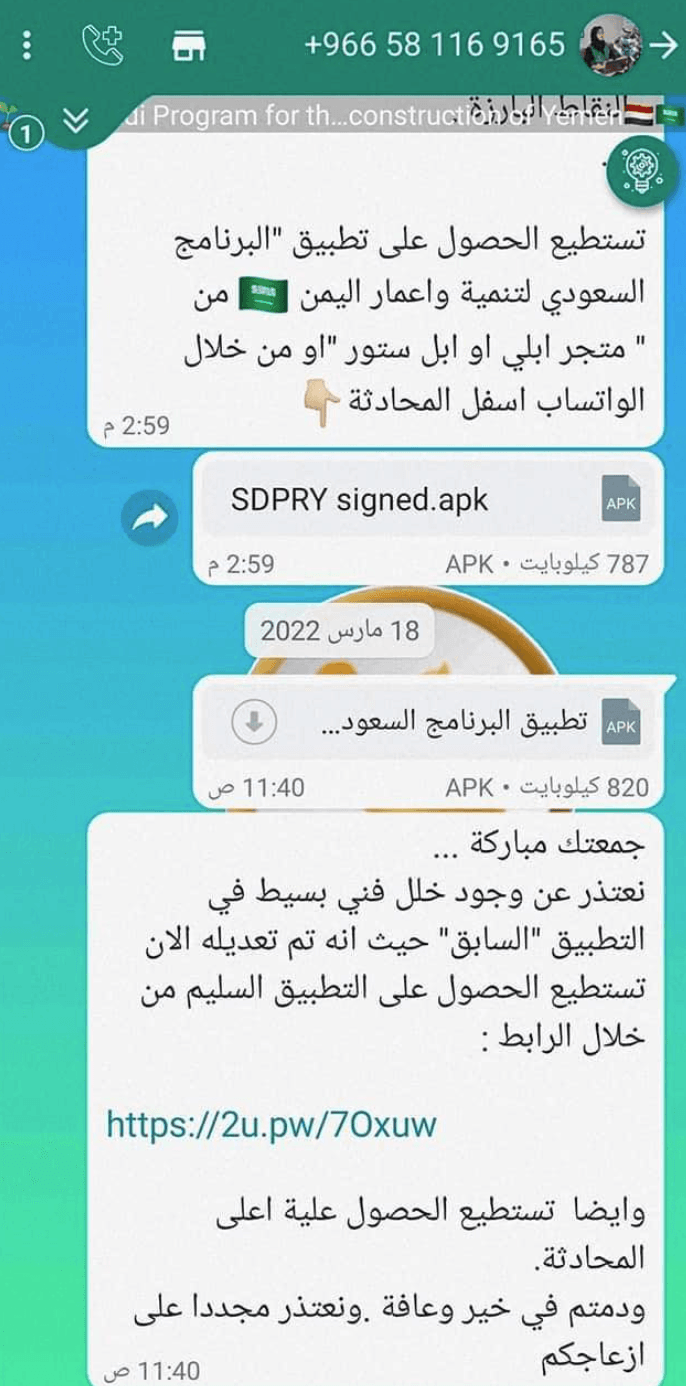 Messages reportedly sent to targets from Saudi Arabian telephone numbers (Source: Meta 1, 2, 3)
Messages reportedly sent to targets from Saudi Arabian telephone numbers (Source: Meta 1, 2, 3)
OilAlpha has almost exclusively relied on infrastructure associated with the Public Telecommunication Corporation (PTC), a Yemeni government-owned enterprise reported to be under the direct control of the Houthi authorities. OilAlpha used encrypted chat messengers like WhatsApp to launch social engineering attacks against its targets. It has also used URL link shorteners. Per victimology assessment, it appears a majority of the targeted entities were Arabic-language speakers and operated Android devices.
OilAlpha threat actors are highly likely to be involved in espionage activity, as handheld devices were targeted with remote access tools (RATs) like SpyNote and SpyMax. We have also observed njRAT samples communicating with C2s associated with this group, making it likely that OilAlpha has used other malware for testing or attack operations.
Barring the discovery of new information or broader geostrategic shifts, OilAlpha is likely to continue to use malicious Android-based applications to target entities that share an interest in Yemen’s political and security developments and the humanitarian and NGO sectors that operate in Yemen.
To read the entire analysis with endnotes, click here to download the report as a PDF.
Related