New “Crypto Drainer” Phishing Pages Siphon Cryptocurrency in Seconds

Editor’s Note: This is an excerpt of a full report. To read the entire analysis with endnotes, click here to download the report as a PDF.
Executive Summary
A Nigerian prince needs your help. Or a coworker texts you, urgently demanding that you send gift cards. Words like “fraud” and “phishing” often evoke simple scams that only fool the foolish. In reality, threat actors develop refined tactics, techniques, and procedures (TTPs) to target users who believe themselves too clever to be fooled.
“Crypto drainers” are malicious scripts that function like e-skimmers and are deployed with phishing techniques to steal victims’ crypto assets. The phishing pages that are deployed with crypto drainers often imitate popular crypto services and use common third-party applications and extensions (such as MetaMask) that are not unusual for the legitimate services that these phishing pages imitate.
We discovered a ready-to-go crypto drainer phishing page advertised by a threat actor on a top-tier dark web forum. This phishing page purports to mint non-fungible tokens (NFTs) and uses third-party services that are commonly used in the crypto sphere. After analyzing this crypto drainer, we concluded that it can be effectively used to steal crypto assets from compromised crypto wallets. Once crypto wallets are compromised, no safeguards exist to prevent the theft of crypto assets. Since their first appearance in 2022, crypto drainer phishing pages have surged in popularity, and crypto drainer phishing pages will likely remain relevant, effective, and widely used in 2023.
Key Judgments
- Crypto drainers are used on phishing pages that imitate popular crypto services to steal crypto assets from unsuspecting victims. They exploit legitimate extensions and applications that are frequently used with the crypto services that the phishing pages imitate.
- We analyzed a ready-to-go crypto drainer phishing page advertised by a threat actor on a top-tier dark web forum. This phishing page entices victims into connecting their wallets with an offer to mint NFTs. As soon as victims attempt to mint NFTs, the crypto drainer siphons available cryptocurrency and desired NFTs to the attacker’s wallet.
- Crypto drainer projects are surging in popularity, and a growing number of ready-to-go crypto drainer phishing packages could allow threat actors to execute them quickly and at scale.
Background
Though blockchain technology is designed from the ground up with security in mind, openings nevertheless exist for threat actors to defraud victims of their crypto assets. “Crypto drainers” are malicious files that function similarly to e-skimmers by automatically executing transfers of crypto assets.
Crypto drainers are commonly deployed on phishing pages that imitate popular crypto services. Examples of the crypto services that a crypto drainer phishing page might imitate include cryptocurrency exchanges or non-fungible token (NFT) platforms. Importantly, crypto drainer phishing pages often use third-party services or extensions (such as MetaMask) that are commonly used with the crypto services they imitate. The use of legitimate services on crypto drainer phishing pages may increase the likelihood that the phishing page will pass an otherwise savvy user’s “scam litmus test”.
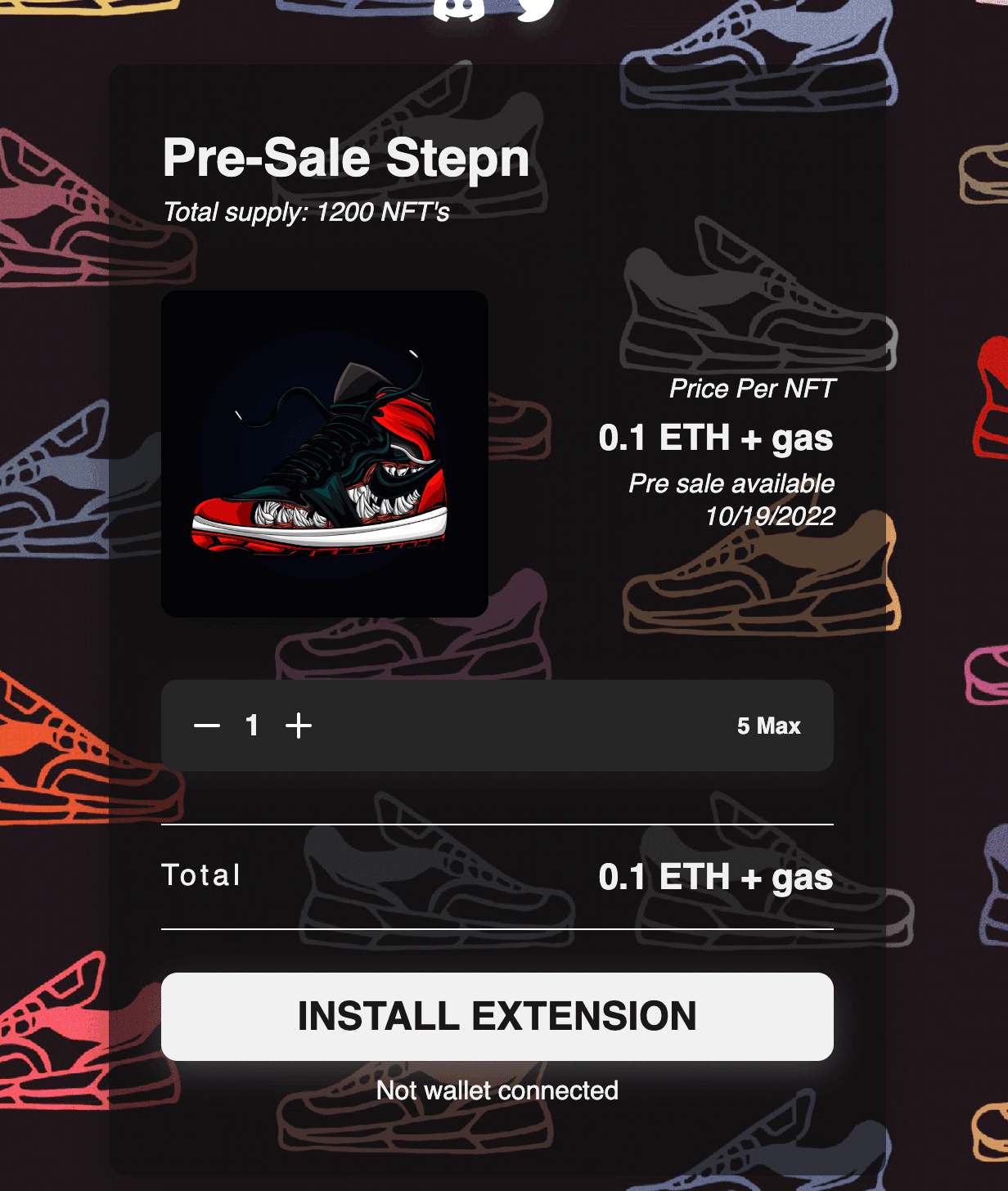 Figure 1: Recorded Future analyzed a crypto drainer phishing page that entices victims to connect their wallets with the promise of minting NFTs (Source: Recorded Future)
Figure 1: Recorded Future analyzed a crypto drainer phishing page that entices victims to connect their wallets with the promise of minting NFTs (Source: Recorded Future)
Related
