Multi-year Chinese APT Campaign Targets South Korean Academic, Government, and Political Entities

Recorded Future's Insikt Group has conducted an analysis of a prolonged cyber-espionage campaign known as TAG-74, which is attributed to Chinese state-sponsored actors. TAG-74 primarily focuses on infiltrating South Korean academic, political, and government organizations. This group has been linked to Chinese military intelligence and poses a significant threat to academic, aerospace and defense, government, military, and political entities in South Korea, Japan, and Russia. TAG-74’s targeting of South Korean academic institutions aligns with China's broader espionage efforts aimed at intellectual property theft and expanding its influence within higher education worldwide.
The motivation behind Chinese state-sponsored actors collecting intelligence in South Korea is likely driven by regional proximity and South Korea's strategic role in China's competition with the United States and its regional allies in the Indo-Pacific. Recent tensions have emerged as China expressed concerns about South Korea's closer relations with the US and its perceived involvement in Taiwan and alignment with the US and Japan's containment of China. TAG-74's intelligence collection efforts, which include spoofed domains and decoy documents related to inter-Korean cooperation, are expected to intensify as China seeks information to shape its diplomatic and business engagements with South Korean entities.
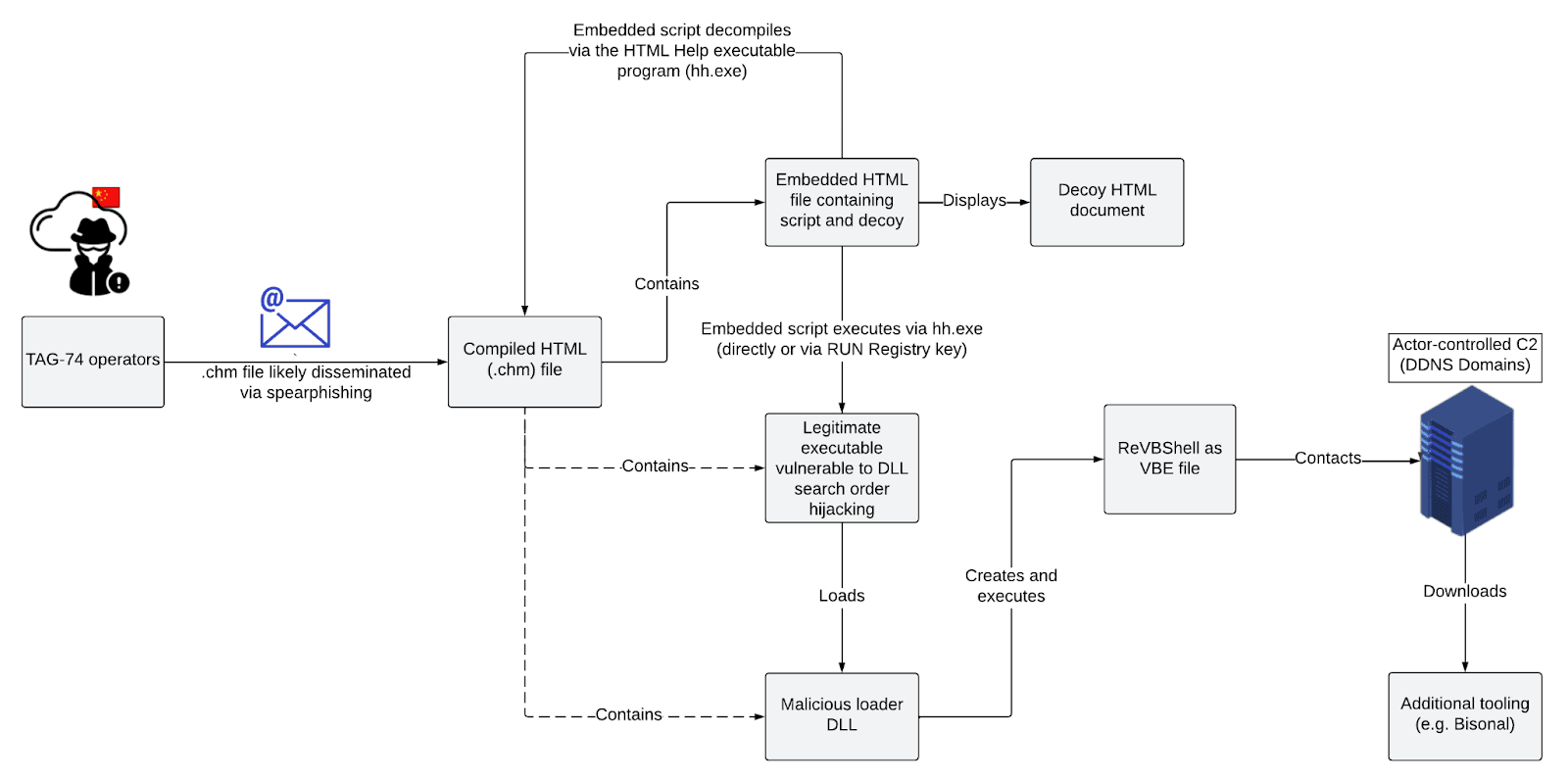 Typical infection chain observed in TAG-74 campaign targeting South Korea (Source: Recorded Future)
Typical infection chain observed in TAG-74 campaign targeting South Korea (Source: Recorded Future)
TAG-74 is a well-established Chinese state-sponsored threat activity group specializing in intelligence collection against South Korean, Japanese, and Russian organizations. Their tactics, techniques, and procedures (TTPs) include the use of .chm files that trigger a DLL search order hijacking execution chain to load a customized version of the VBScript backdoor ReVBShell. Additionally, a custom backdoor known as Bisonal is used to enhance capabilities once initial access through ReVBShell is established. This customized ReVBShell variant is likely shared between TAG-74 and another closely related threat activity group, Tick Group, indicating collaboration between these groups.
The persistence of TAG-74 in targeting South Korean organizations and its likely operational alignment with the Northern Theater Command suggests that the group will continue its active and long-term intelligence-gathering efforts in South Korea, Japan, and Russia. Notably, the use of .chm files by Chinese state-sponsored actors is not particularly common outside of South Korea. However, the use of this attack vector in activity targeting South Korea has been seen both in TAG-74 campaigns and, more widely, in activity attributed to North Korean state-sponsored threat activity groups such as Kimsuky and APT37. Organizations should monitor for the presence and use of .chm files, particularly if they are not commonly used within their environment, as this tactic has gained prevalence among threat actors in recent years.
To read the entire analysis, click here.
Appendix A — Indicators of Compromise
|
Domains alleyk.onthewifi[.]com anrnet.servegame[.]com asheepa.sytes[.]net attachdaum.servecounterstrike[.]com attachmaildaum.servecounterstrike[.]com attachmaildaum.serveblog[.]net bizmeka.viewdns[.]net bucketnec.bounceme[.]net chsoun.serveftp[.]com ckstar.zapto[.]org daecheol.myvnc[.]com eburim.viewdns[.]net eduin21.zapto[.]org elecinfonec.servehalflife[.]com foodlab.hopto[.]org formsgle.freedynamicdns[.]net formsgle.freedynamicdns[.]org fresh.servepics[.]com global.freedynamicdns[.]net global.freedynamicdns[.]org hairouni.serveblog[.]net hamonsoft.serveblog[.]net hanseo1.hopto[.]org harvest.my-homeip[.]net hometax.onthewifi[.]com hwarang.myddns[.]me jaminss.viewdns[.]net janara.freedynamicdns[.]org jeoash.servemp3[.]com jstreco.myftp[.]biz kanager.bounceme[.]net kcgselect.servehalflife[.]com kjmacgk.ddnsking[.]com kookmina.servecounterstrike[.]com ksd22.myddns[.]me kumohhic.viewdns[.]net kybook.viewdns[.]net leader.gotdns[.]ch likms.hopto[.]org logindaums.ddnsking[.]com loginsdaum.viewdns[.]net mafolog.serveminecraft[.]net mailplug.ddnsking[.]com minjoo2.servehttp[.]com mintaek.bounceme[.]net munjanara.servehttp[.]com necgo.serveblog[.]net pattern.webhop[.]me pixoneer.myvnc[.]com plomacy.ddnsking[.]com proeso.servehttp[.]com prparty.webhop[.]me puacgo1.servemp3[.]com saevit.servebeer[.]com safety.viewdns[.]net samgiblue.servegame[.]com sarang.serveminecraft[.]net satreci.bounceme[.]net sejonglog.hopto[.]org signga.redirectme[.]net skparty.myonlineportal[.]org steering.viewdns[.]net stjpmsko.serveblog[.]net surveymonkey.myddns[.]me themiujoo.viewdns[.]net tsuago.servehalflife[.]com tsuagos.servehalflife[.]com unipedu.servebeer[.]com visdpaka.servemp3[.]com visual.webhop[.]me wwl1764.ddnsking[.]com IP Addresses 45.133.194[.]135 92.38.135[.]92 107.148.149[.]108 141.164.60[.]28 148.163.6[.]214 158.247.223[.]50 158.247.234[.]163 Bisonal 01e5ebc2c096d465800660a0ad6d62208a5b2b675e3700f3734fac225b1d38bd 11cd4b64dcac3195c01ffc937ae1eb77aa2f98d560a75347036d54a1cf69a5fd a88ca28b0948e810d4eb519db7b72a40cfe7907ce4c6a881a192880278f3c8b5 89f250599e09f8631040e73cd9ea5e515d87e3d1d989f484686893becec1a9bc 0ea0b19c562d20c6ac89a1f2db06eedcb147cde2281e79bb0497cef62094b514 ReVBShell (Decoded) aa4ad5341a9258330abd732cbab3721d76764f1ff21a8f960622661d701a1a71 8f50f49e77ddcc7ef639a76217b2eb25c48f9ce21ae8341050d0da49b89b7b34 ae0f641dc9d33ee50990971104ef1c598e216693700be6b74bb1e9ef373af97c 465c7c6a0f23ba5f928fc0d0cdc4d9f6ec89e03dcedafc3d72b3b3c01a54a00c 6a59421fd225d90439b6a933458718cf43dbe518c63979e8980bc070c070558a df7d584d56af6fcf3cca31ed0d3a4d34abd2c1019b8d223a230f8a78075a7d9a 078a8026f32b8d05258285dc527408388c651f6c3eaebc45f8bb3f4b42248631 Loader DLLs c643598b4ee0e9b3b70dae19437bbec01e881a1ad3b2ec1f6f5c335e552e5d6e 9425666e58b200306935c36301d66a4bf2c831ad41ea0ee8984f056257b86eb6 a16997954b64499479b4721c9f742b5d2875496f2035e1c654b06694981041b2 0d0acd7e7257a715c10dded76acb233adc8fdfe32857eda060bd1448e8b54585 0ea02fddf2ec96d4aee8adaffda2dd5fab0ea989b0c3f8c1577a1be22ee9153a e3cdaa9bfba6bfac616b7f275c1e888b8910efcb8a3df071f68ad1e83710bd61 9fdb528949a2b80ac40cb7d3333bdff5d504294cc3d90cf353db72b8beffd2b2 607f324c3427916d67369e40af72aa441f3ca7be1e0ec6c53c3558fc7a1c4186 8efc5db8c678bdf27dacbf033842c2ef676c979afdc4561cb8d315d2d488491f CHM Files beb09817608daba003589292a6cca2f724c52f756df2ef0e230380345d702716 ba07ee6409908384172511563e6b9059cf84121fcb42c54d45c76ec67cb36d7c bf1d1f5157756529d650719cc531ec2de94edb66ae1dabd00ed6f4b90a336d9c 2dd7c9ea32f5b2a4d431fc54aa68cd76837f80bb324ef2e4e1e5134e467e35af 56c9235e55b1a6371762159619e949686d8de2b45a348aeb4fd5bed6a126f66a dda47ba7a41c9a2f041cc10f9b058a78e0019315c51cc98d0f356e2054209ae5 cf5bbbcb3f4d5123c08635c8fd398e55e516893b902a33cd6f478e8797eea962 HTML Files b3a8ea3b501b9b721f6e371dd57025dc14d117c29ce8ee955b240d4a17bc2127 9d10de1c3c435927d07a1280390faf82c5d7d5465d772f6e1206751400072261 0eea610ec0949dc602a7178f25f316c4db654301e7389ee414c9826783fd64c0 8073593a7311bc23f971352c85ce2034c01d3d3fbbe4f99a8f3825292e8f9f77 e1748e7e668d6fc7772e95c08d32f41ad340f4a9acf0e2f933f3cbeba7323afa 0d6893c7a3a7afc60b81c136b1dcdfb24b35efab01aac165fe0083b9b981da7c 77fbb82690c9256f18544e26bb6e306a3f878d3e9ab5966457ac39631dfd2cb0 Filenames KOREA MARITIME & OCEAN UNIVERSITY.chm SPM_(협력사)_사용자매뉴얼_v2.1.chm 세종대학교 DID 연락처 Ver1.0(202103 현재).chm 서울기독대 전자출결-웹페이지 교수자-메뉴얼 Ver1.0.chm 2022년도_기초과학연구역량강화사업_착수보고회_개최_계획 Ver1.1.chm 국토위 위원명단(사진)_Ver_1.2.chm 비젠테크_Seculetter_제품소개서_2021 v1.4.chm 통일부 남북경협관련 법인 연락처_Ver2.1.chm |
Appendix B — MITRE ATT&CK Techniques
| Tactic: Technique | ATT&CK Code |
| Initial Access - Spearphishing Attachment | T1566.001 |
| Execution - Command and Scripting Interpreter: Visual Basic | T1059.005 |
| Execution - User Execution: Malicious File | T1204.002 |
| Persistence - Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | T1547.001 |
| Defense Evasion - Hijack Execution Flow: DLL Search Order Hijacking | T1574.001 |
| Defense Evasion - System Binary Proxy Execution: Compiled HTML File | T1218.001 |
| Defense Evasion - - Execution Guardrails | T1480 |
| Discovery - Software Discovery: Security Software Discovery | T1518.001 |
| Command and Control - Data Encoding: Standard Encoding | T1132.001 |
| Command and Control - Application Layer Protocol: Web Protocols | T1071.001 |
| Command and Control - Encrypted Channel: Symmetric Cryptography | T1573.001 |
| Exfiltration - Exfiltration Over C2 Channel | T1041 |
Related
