Recorded Future Maltego Integration — Now With Moar

Webinar: Learn how to use Maltego for better insight into cyber threats. Watch now.
At Black Hat 2015 this year, we were busy previewing the new version of our Maltego integration! If you didn’t see us out in the desert this year, here are highlights of upcoming improvements from Recorded Future and our partner Malformity Labs.
More Intel
First off, we are packing a lot more intel information into the Entities returned by our Maltego transforms. An intelligence summary is returned for IP addresses, domains, and hashes and appears in the Detail View. The summary lists related infrastructure, malware, or CVE vulnerabilities. For example, here’s the summary for an IP address recently linked to the IpTabLex botnet:
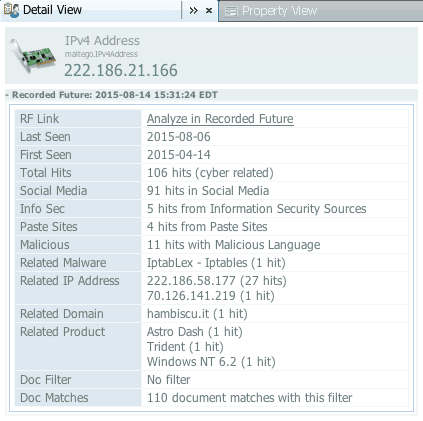
We’re packing more intel into document entities too. For example, here’s the summary for a recent blog post about CVE-2015-3113:
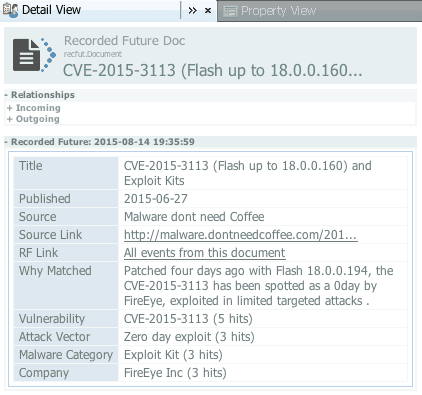
Of course, you’ll want to read the original yourself, using the source link. This improved summary gives you a clear “information scent” for what’s available in that document.
More Efficiency
Building on these same intel summaries, we’ve added new transforms for IP addresses, domains, and hashes that retrieve those top related entities directly – without drilling down into detailed document-level intel. This make it faster to pull related entities into your investigation, vet them for hits in your other technical intel sources, and focus your investigation in on those interesting multi-source hits.
Below is a graph snippet with the top 12 hits for a specific domain – one that is not malicious per se, but is reportedly exploited as secondary infrastructure. After checking off these IPs against other internal logs and other intel sources, you can zero in on the interesting ones.
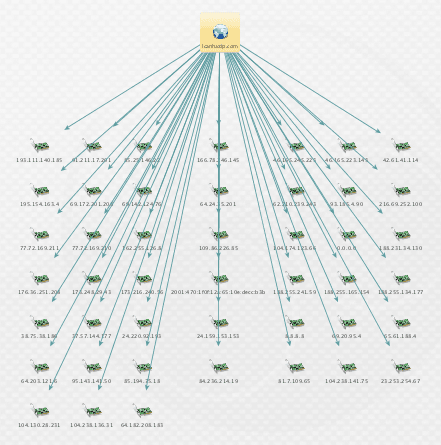
More Drilldown
For some entities, these summaries cover a lot of information – more than can readily be pushed back into Maltego. The full summary is available through a drilldown link back to Recorded Future. Here’s the beginning of the summary for that same domain:
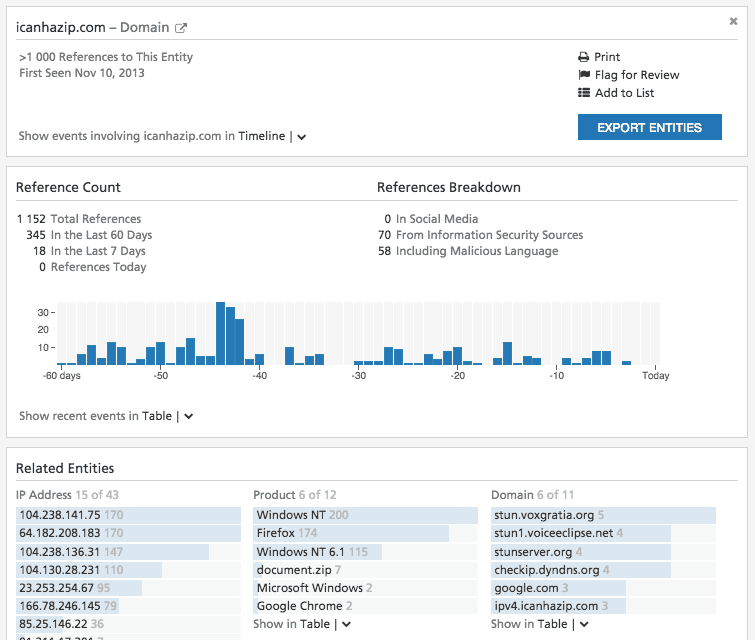
We’ve also added deep links into Recorded Future for documents – so you can slice and dice all of the events reported in the document, and access any cached content.
Early Access is Available
Are you already using our integration and want to be an early adopter of these improvements? If you’re not afraid of a few bugs and want to jump to the front of the feedback line, please email us at support [at] recordedfuture [dot] com.
Learn More
If early access is not for you, or if you’re not already using our Maltego integration, you can learn more by watching our recent webinar.
Related