LockerGoga Ransomware Disrupts Operations at Norwegian Aluminum Company
Norwegian aluminum company Norsk Hydro was hit by a ransomware attack on Tuesday, March 19, 2019. According to the Norwegian National Security Authority (NSM), the attackers used LockerGoga, a relatively new strain of ransomware first discovered in January.
According to Reuters, the attack was severe enough to disrupt parts of production at Norsk Hydro. On Tuesday morning, employees were prevented from logging into the network for fear of spreading the ransomware, while the IT staff was attempting cleanup.
Findings from Recorded Future’s Insikt Group indicate that the first known outbreak of LockerGoga was in late January of this year, when it was used against Altran, a French engineering consultancy. During this first campaign, the LockerGoga malicious binary was digitally signed by a previously unknown code signing authority, MIKL LIMITED. The trust for this certificate was revoked following the Altran attack. The new samples relating to the Norsk Hydro attack appear to be signed by ALISA LTD — again, a relatively unknown entity. Trust for this certificate has also now been revoked. There are LockerGoga binaries also signed by KITTY’S LTD, which were uploaded in February of this year by VirusTotal users from the United States, Turkey, and Germany, and only appear to have been used during that campaign. There are also some binaries that aren’t digitally signed.
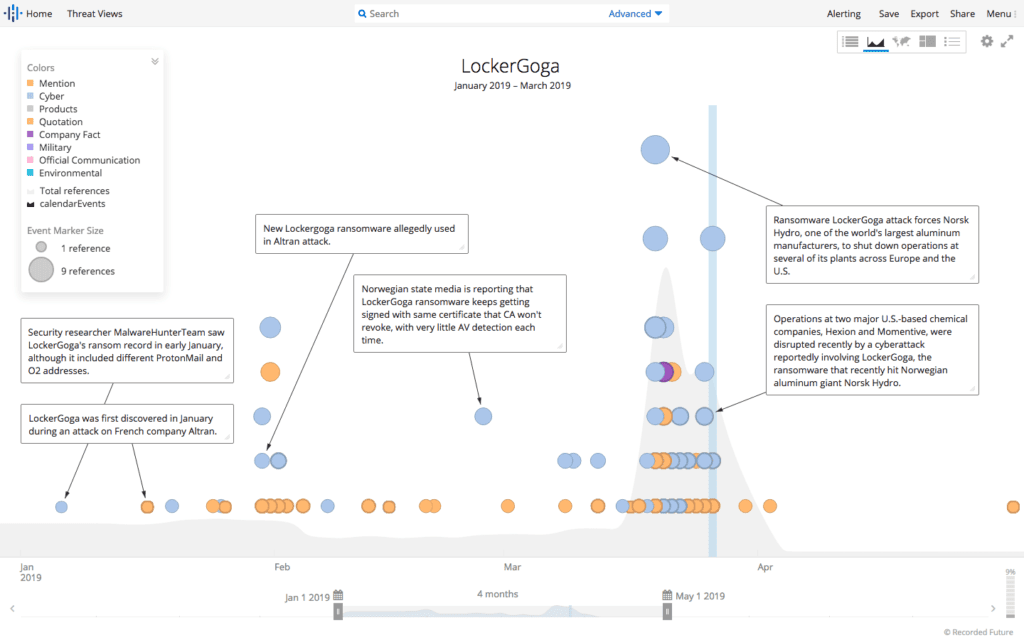
LockerGoga activity between January 2019 to March 2019.
The LockerGoga ransomware itself is not very sophisticated, according to analysis published by Bleeping Computer. Deployment of the ransomware is manual, with the attackers behind LockerGoga most likely using Active Directory to spread the ransomware. Initial infection into Norsk Hydro is suspected to be via a phishing campaign, but that has not been confirmed as of this writing. At this time there is no decryption tool for LockerGoga. The cure for LockerGoga at this point appears to be good protection against phishing attacks, and keeping antivirus and other endpoint protections up to date.
One researcher has posted a list of the most up-to-date IOCs from the various LockerGoga samples to a GitHub repository (applause to Recorded Future customer E.C. for the tips).
Once inside a target network, the team behind LockerGoga is using techniques similar to the attackers behind Ryuk, CrySIS, SamSam, and other recent successful ransomware campaigns: deploying the ransomware in multiple places on the target network to disrupt operations, cause the most damage, and force the targeted organization to pay the ransom — although the skillset of the LockerGoga team seems to be more shallow than similar teams.
However, the team at Norsk Hydro has stated they will not pay the ransom; instead, they are restoring systems from backup.
These types of disruptive attacks are becoming more common, with the most famous one being the SamSam attack on Atlanta last year. Recent attacks on the Boston Public Defender’s Office, Orange County in North Carolina, and shipping company COSCO have all had a disruptive effect on services.
There are a million reasons not to pay the ransom in these types of attacks. Paying the ransom only helps the criminals to produce better malware, and like a bad romance, it may encourage them (or other attackers) to strike a target again, knowing that they are likely to pay the ransom. This happened with the Colorado Department of Transportation in 2018.
The costs to restore dozens or hundreds of systems are enormous, however, and that doesn’t take into account all of the associated incident response costs. From a cost perspective, it may make more sense to pay the ransom. One word of caution with regard to LockerGoga: this particular ransomware also encrypts DLL files. There have been cases with other ransomware families where trying to decrypt systems that contain encrypted DLL files fails. This means organizations have paid the ransom and still didn’t have access to their files.
Update: Since this post was published, two additional LockerGoga victims have been reported by Vice: Hexion and Momentive, which are both American chemical companies. There has still been no confirmation of the initial infection point, and Hexion and Momentive have managed to avoid the paparazzi and keep a low profile. There have been reports of additional victims, but no confirmation at this point.
Both Unit 42 and DoublePulsar have excellent writeups on LockerGoga, and both were able to confirm that there is no mechanism for spreading through the network built directly into LockerGoga. Instead, the malware appears to rely on Active Directory to spread, which likely means it requires a great deal of manual intervention to deploy.
The Unit 42 writeup also focuses on the evolution of the ransomware from the initial Altran attack to the latest versions.
We will continue to update as the situation warrants.
Click here to download the associated indicators of compromise.
Related