Why Security Teams Should Pay Attention to the European Cyber Army

The European Cyber Army (ECA) kicked off 2014 by posting successful cyber attacks on governments, companies, and organizations around the world. One of the earliest mentions of the group occurred on Twitter on January 12 when the ECA, in conjunction with 1775Sec, claimed to have leaked an Apple database, posting the data on Pastebin. This occurred the same day the ECA posted its first tweet under the handle @ECA_Legion.

The success of this attack, like many of their subsequent attacks is overstated. According to Appleinsider.com, the Apple leak was not confirmed by Apple, and much of the leaked data was dated and possibly not from Apple. The ECA also claimed to have “nuked,” a term used often by the ECA, Yahoo on February 4th, but this is appears to be a false claim. They also claimed to have hacked WebEx on February 13, but they most likely capitalized on an outage or network problem.
According to the ECA’s Twitter handle, @ECA_Legion, the group claimed to take down the North American Antivirus company ESET as well as Bank of America, JP Morgan Chase, and Fidelity Bank’s websites via DDoS attack. On January 27 the ECA took credit for DDoSing the the United States Judiciary’s court system, pacer.gov and uscourts.gov for a period of several hours. The attack on the United States judicial system attracted the attention of the FBI, United States Judiciary, and several news outlets. It remains another unconfirmed hacking success for the ECA.
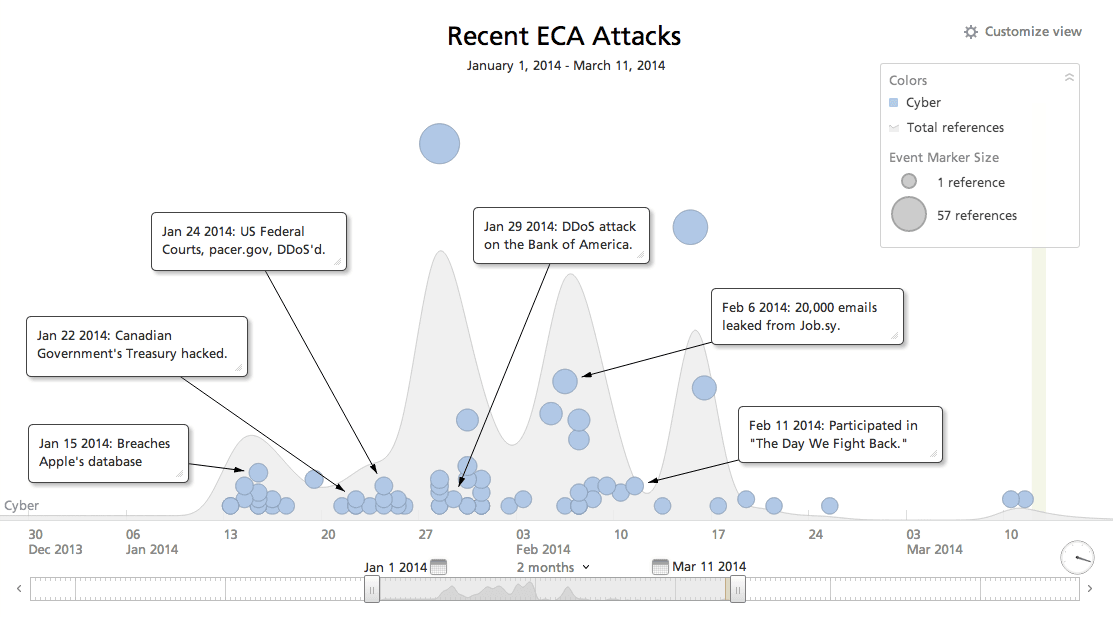
The ECA has been participating in several Anonymous operations such as AntiSec, an Anti-Israeli operation to expose Israeli supporters by revealing their email addresses, phone numbers, and social security numbers, and OpSochi particularly against animal abuse. The ECA also took a stand on February 11 with other hacktivists in “The Day We Fight Back” campaign opposing massive government surveillance programs. The ECA took aim at the NSA, FBI, and the UK’s GCHQ although their success against those targets is unconfirmed.

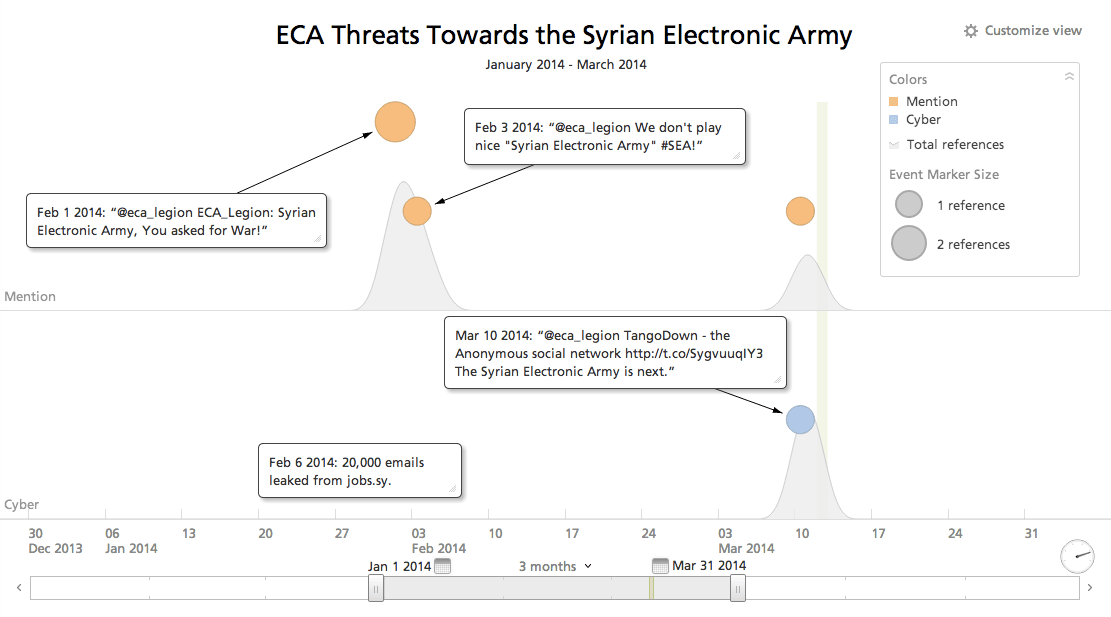
While the ECA works with members of Anonymous, the ECA is not a fan of the Syrian Electronic Army (SEA) hacker group. In fact, some of their efforts have been hacks directed against the SEA, to include Syrian targets, such as a hack and subsequent leak on Pastebin of 20,000 emails on Jobs.sy on February 6th and threats to Syria’s telecommunications network and internet.
Who is the European Cyber Army?
Although the size and organization of the ECA remain a mystery, Recorded Future analysis was able to identify some details about the ECA hackers based on their social media presence. Joining the ECA may even be as easy as emailing esercitoeuropeocyber [at] gmail [dot] com with your online persona data and hacking credentials, according to their introduction post on Pastebin (http://pastebin.com/0S2wwWda).
On February 14 dollarboot.com posted on Pastebin that Chris Ducinski of Massachusetts was the leader of the ECA, providing his email, image, and facebook page. It is unclear whether there is any truth to this claim. Andre Verzaal, @Andre_Verzaal, and @niggernos, self-proclaimed their affiliation with the ECA. Another prevalent Twitter user, Anonymous Priest, @YourAnonPriest, who was one of the first to engage with the ECA on Twitter, also appears to be hacking on behalf of the ECA although the identity of this user remains unknown.
One interesting question about this new group is why are they called the European Cyber Army? The group has not been vocal about the origins of their name or their motivations and intentions. The diversity of their targets does not help to pinpoint any geopolitical based motivations, but their motives do appear to be in line with those of Anonymous.
According to an ECA page on Pastebin, the ECA hacks by Dox (releasing a dossier and/or personal information about someone), DDoS, Deface, Leak, SQLi, and Lulz. They also consider their work to to be Black, White, and Grey Hat activities. The ECA, according to a Pastebin post, merged with LEAKSEC on January 17.
Future Plans
On February 8 @YourAnonPriest tweeted the ECA planned to “storm the White House” on November 5, 2014 in what appears to be an Anonymous affiliated operation. But November is a long way down the road, and the world will have to wait and see what the ECA has planned in the meantime. Recorded Future analysis shows while Anonymous has been talking about several upcoming events the ECA remains quiet, it is unclear as of now whether or not the ECA will join in those Anonymous operations.
Related