Detections in the Sky: Sigma Rules to Enhance Cloud Security for the Big Three


Editor’s Note: The following post is an excerpt of a full report. To read the entire analysis, click here to download the report as a PDF.
This report provides an overview of tools used to attack the 3 major cloud providers, Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). It contains details on the capabilities of these attack tools and provides detections for suspicious and malicious behavior against these cloud providers. This report is intended for security operations audiences who focus on detection engineering. Sources include the Recorded Future® Platform and open-source research.
Executive Summary
Many organizations are migrating their data, resources, and/or services to the cloud. The cloud offers organizations the ability to scale services and provide capabilities that would not otherwise be feasible with the organization's on-premises resources. With the increased use of cloud services, the need for organizations to properly secure and monitor their cloud environments becomes more critical. Attacks against cloud infrastructure look different and require a unique approach to detection when compared to on-premises infrastructure. As a result, cloud infrastructure security best practices are distinct from other best practices that can be applied to conventional infrastructure.
While the Big Three platforms, Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) all have built-in security controls and provide logging capabilities, there is still ambiguity on threat detection and response for cloud environments. Our research provides details on the different types of attacks that can be performed against the Big Three platforms, such as artifact deletion, command execution, and cloud environment enumeration, among others, as well as Sigma rules to detect a subset of the attacks that we emulated as part of our research.
Key Judgments
- The Big Three platforms provide logging capabilities to detect most malicious activity if combined with the infrastructure to collect, aggregate, and correlate the logs.
- The tools developed for attacking AWS and Azure are more sophisticated compared to those targeting GCP.
- Detection engineering for attacks against cloud infrastructure are complicated due to the distributed and ephemeral nature of the cloud, the many different workloads that can be run from a cloud infrastructure, and differences between the cloud providers.
- Opportunities for detecting attacks targeting cloud service providers exist on both the cloud provider as well as the hosted virtual machines for both Azure and GCP.
Background
Cloud Workloads
There are many different ways an organization can use cloud resources, referred to as cloud workloads. Dell defines a cloud workload as a “specific application, service, capability or a specific amount of work that can be run on a cloud resource”. These workloads are potential targets for, or are at risk of, exposure from cloud-related intrusions.
Gartner has stated that the top 7 workloads that should be migrated to the cloud are:
- Mobile device and application support
- Collaboration and content management
- Videoconference
- Virtual desktops and remote workstation management
- Scale-out application
- Disaster recovery
- Business continuity solutions
The Big Three
We chose the top 3 providers for cloud infrastructure-as-a-service (IaaS) as the focal points of this research: Amazon Web Services (AWS), Azure, and Google Cloud Platform (GCP). Together, these platforms represent over 62% of the global cloud IaaS market for Q1 2022, with AWS at 33% of market share, Azure at 21%, and GCP at 8%.
All three platforms have similar service offerings; however, in a recent blog by BMC, AWS and Azure both offer approximately 200+ services, while GCP offers 100+. BMC also outlines the common services that each platform offers; the following is a summary of their research:
- Compute services (VMs, platform-as-a-service, containers and serverless functionality)
- Database and storage services (relational database management, NoSQL, object storage, file storage, archive storage, data warehouse/data lake)
- Networking (virtual network, load-balancing, firewall, DNS, content delivery)
BMC also states that for some of the more specialized services like robotics, end-user computing, game development, virtual reality, and IoT, both Azure and AWS offer more services when compared to GCP.
In the end, the choice of which Big Three platform to use is more dependent on the particular use case the organization is looking to solve.
The Big Three Threat Analysis
Securing cloud infrastructure inherently follows a security model that was first introduced by Sounil Yu at the 3rd Annual National Cybersecurity Summit (2020), and is known as the DIE triad. The DIE triad is an adapted version of the well-known CIA triad (confidentiality, integrity, and availability) but focuses more on the infrastructure on which an organization's resources or data reside. Copado also provides the following definitions for the DIE triad:
- Distributed: Are systems distributed to allow for scalability while preventing dependence on a single zone?
- Immutable: Can the infrastructure be disposed of and replaced in the event of an issue, aka infrastructure-as-code?
- Ephemeral: What’s the period for system reprovisioning, and are assets disposable in the event of a breach?
Threat-modeling attacks against cloud infrastructure are increasingly complicated due to the distributed and ephemeral nature of the cloud and the variety of workloads that can be run from a cloud infrastructure. As a result, cloud infrastructure varies from organization to organization, and threats that may directly affect one organization’s cloud infrastructure may not directly affect another organization’s cloud infrastructure. These differences help illustrate the diverse nature of cloud environments and aid in explaining challenges associated with creating a uniform security model for cloud environments.
Using the Recorded Future Platform and OSINT research to identify cyber threats affecting each of these platforms, we found that misconfigurations present the greatest risk to Amazon AWS instances, followed by credential theft, for allowing threat actors to gain initial access. The most common misconfigurations that lead to compromise stem from cloud service configurations that allow the environment to be publicly accessible. Microsoft Azure, however, was affected by a diverse set of cybersecurity threats, of which misconfigurations were not a big portion. Finally, Google Cloud products were targeted in only 1 cyber incident, and were mentioned very few times in relation to misconfiguration issues.
There are many resources available to organizations to guide them in the implementation of cloud infrastructure security best practices. Such resources should be examined for applicability to an individual organization’s situation, but common ones include those of the Cloud Security Alliance, the United States National Institute of Standards and Technology, and the US Cybersecurity & Infrastructure Security Agency.
For this research, our approach was to identify common tools and frameworks used to attack the Big Three platforms and then use those tools against our test environments. Figure 1 below illustrates our cloud detection methodology. At a high level, our methodology consisted of running these malicious tools against the cloud provider test environments we created; we analyzed the cloud provider logs to look for artifacts indicating the use of these tools and created Sigma rules based on them where possible.
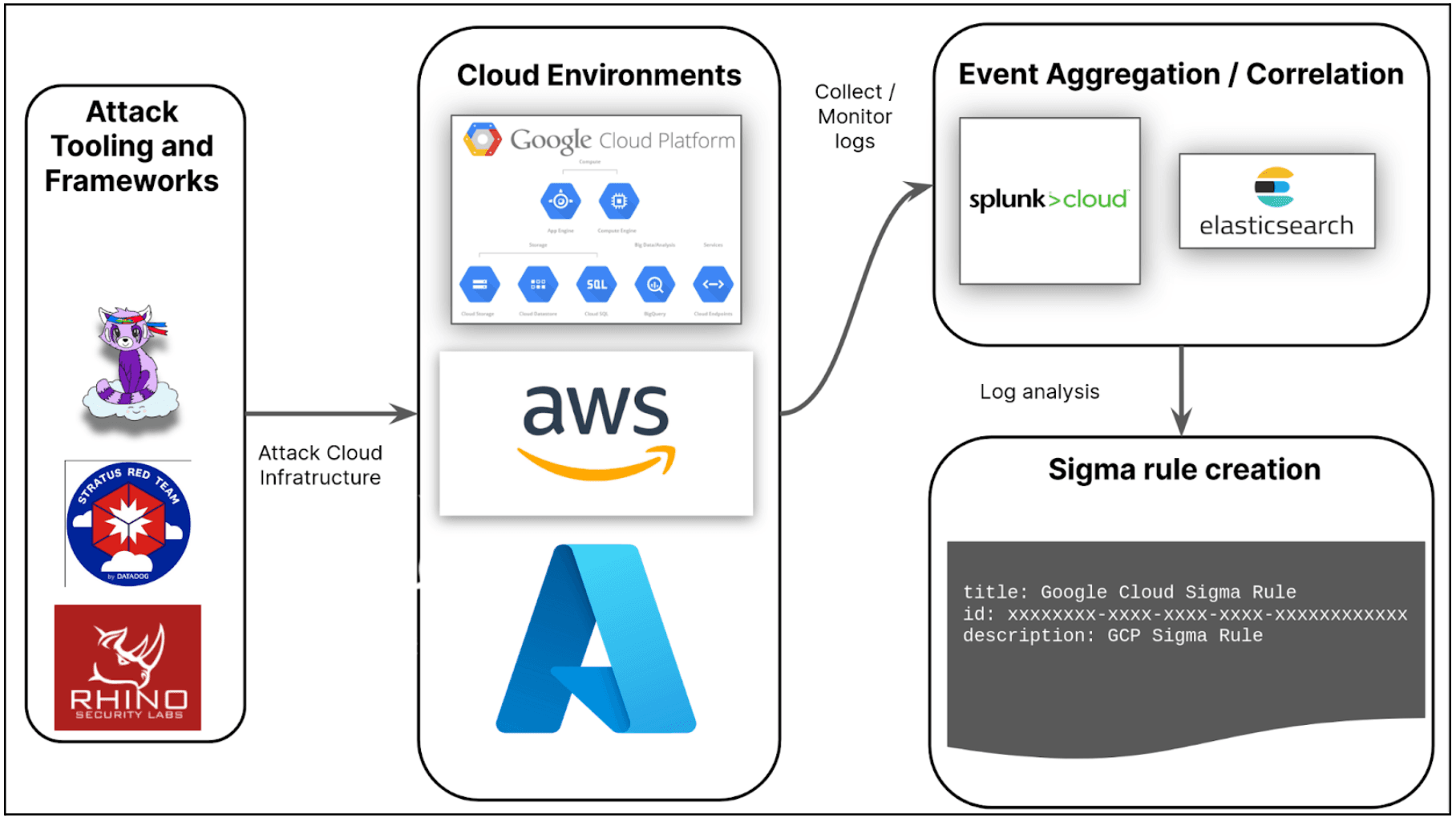 Figure 1: Insikt Group cloud detection engineering methodology (Source: Recorded Future)
Figure 1: Insikt Group cloud detection engineering methodology (Source: Recorded Future)
AWS Threat Analysis
Attack Surface
AWS environments are commonly targeted by threat actors of all varieties with highly disparate motivations and attack techniques. There are myriad tools that could be used to emulate common attacks that affect AWS environments and to demonstrate attack strategies that may be implemented by a threat actor. We have identified a selection of these tools, focusing on recency and breadth of potential attack types, and used them to generate log data for the AWS logging service CloudTrail. Using this data, we created Sigma detections for the displayed behavior, allowing defenders and threat researchers to better identify potentially malicious activity in AWS environments and the use of these tools.
The tools that we used to generate CloudTrail log data are described below.
Stratus Red-Team
Stratus Red-Team is a penetration testing tool created by DataDog, the creator of a cloud-based logging, monitoring, and security platform. Stratus is based on Red Canary’s Atomic Red Team pentesting suite; however, Stratus focuses on cloud environments whereas Atomic Red Team is used to target Windows, Linux, and MacOS operating systems and networks.
Stratus contains more than 30 pre-written attack techniques, as shown in Figure 2. All but 7 of these techniques are used to perform various attacks against AWS environments. These attacks are varied and span the credential access, defense evasion, discovery, execution, privilege escalation, exfiltration, initial access, and persistence ATT&CK tactics.
Pacu
Pacu is an open-source exploitation framework that focuses on performing attack techniques against AWS cloud platforms using pre-written modules. The tool is intended to be used for red-teaming to identify vulnerabilities and misconfigurations within AWS environments. It currently has 42 modules that perform reconnaissance, discovery (enumeration), privilege escalation, lateral movement, persistence, exfiltration, and defense evasion, among other tactics. Pacu also includes a list of exploitation-specific modules that allow the user to perform actions including:
- The automatic creation of identity and access management (IAM) keys in a target environment
- Lightsail SSH key discovery, SSH key generation, and temporary access-granting
- Remote code execution on EC2 instances as SYSTEM/root
Sigma Rule Detections
AWS Sigma Rule: Stratus Activity Detection
This rule detects the string stratus-red-team, which is included in the user-agent any time Stratus executes a module. While Stratus is mainly used to demonstrate malicious activity for red-teaming purposes, it is possible that a threat actor could modify Stratus modules to weaponize the tool. Stratus’s reliance on the Terraform infrastructure-as-code (IaC) tool to perform attacks and initialize the target environment means it is possible that the threat actor will leave the user-agent unmodified and the user-agent will continue to include stratus-red-team.
AWS Sigma Rule: Port 22 Ingress
The Stratus module aws.exfiltration.ec2-security-group-open-port-22-ingress allows the user to create a security group allowing inbound access to the environment over port 22. By creating this security group a threat actor would have a route to drop tools or provide C2 commands within a victim environment. The general activity of allowing port 22 ingress can be detected by identifying events with the event name AuthorizeSecurityGroupIngress and by identifying events where the request parameters toPort contain the string 22.
AWS Sigma Rule: CloudTrail Trail Deletion
The Stratus module aws.defense-evasion.cloudtrail-delete allows users to create a CloudTrail trail to remove logging data from the AWS environment. This technique can be detected simply by identifying events with the event name DeleteTrail but these events should be scrutinized to ensure that the deletion was not performed legitimately.
Editor’s Note: This post is an excerpt of a full report. To read the entire analysis, click here to download the report as a PDF.
Related