Capitalizing on Coronavirus Panic, Threat Actors Target Victims Worldwide

Click here to download the complete analysis as a PDF.
Recorded Future investigated how threat actors are using the global disruptions caused by COVID-19 to further their cyber threat activities. This research is targeted toward those who hope to understand the technical cybersecurity threats that have emerged from the spread of COVID-19.
Executive Summary
The emergence of coronavirus disease 2019 (COVID-19), the novel coronavirus that originated in late December 2019, has brought with it chaos in many different economic sectors — finance, manufacturing, and healthcare, to name a few. However, it has also originated a new cybersecurity threat, igniting a bevy of COVID-19-themed phishing lures and newly registered COVID-19-related domains. The technical threat surrounding COVID-19 primarily appears to be around phishing, with actors promising that attachments contain information about COVID-19.
Recorded Future observed an extensive list of actors and malware employing these techniques, including Trickbot, Lokibot, and Agent Tesla, targeting a broad set of victims, including those in the United States, Italy, Ukraine, and Iran in particular. Threat actors have also endeavored to gain the trust of victims using branding associated with the U.S. Centers for Disease Control and Prevention (CDC) and the World Health Organization (WHO), as well as country-specific health agencies such as the Public Health Center of the Ministry of Health of Ukraine and China’s Ministry of Health, and companies such as FedEx.
Key Findings
- As of March 11, 2020, we believe that COVID-19 has been primarily used by cybercriminals as a theme for phishing lures. However, we have observed at least three cases where reference to COVID-19 has been leveraged by possible nation-state actors. We assess that as the number of COVID-19 cases, as well as publicity around the virus, rises globally, both cybercriminals and nation-state actors will increasingly exploit the crisis as a cyberattack vector.
- Cybercriminals will often use the branding of “trusted” organizations in these phishing attacks, especially the World Health Organization and U.S. Centers for Disease Control and Prevention, in order to build credibility and get users to open attachments or click on the link.
- The number of references to COVID-19 in relation to cyberattacks has increased over the last two months, including country-specific phishing lures as the virus becomes more prevalent in that country. Recorded Future assesses that, for the duration of the outbreak, COVID-19 will continue to be used as a lure, and that new versions of these lures targeting new countries will emerge.
- The number of newly registered domains related to coronavirus has increased since the outbreak has become more widespread, with threat actors creating infrastructure to support malicious campaigns referring to COVID-19. The initial spike in domain registrations coincided with a large spike in reported COVID-19 cases in mid-February — a possible indicator that attackers may have begun to realize the utility of COVID-19 as a cyberattack vector.
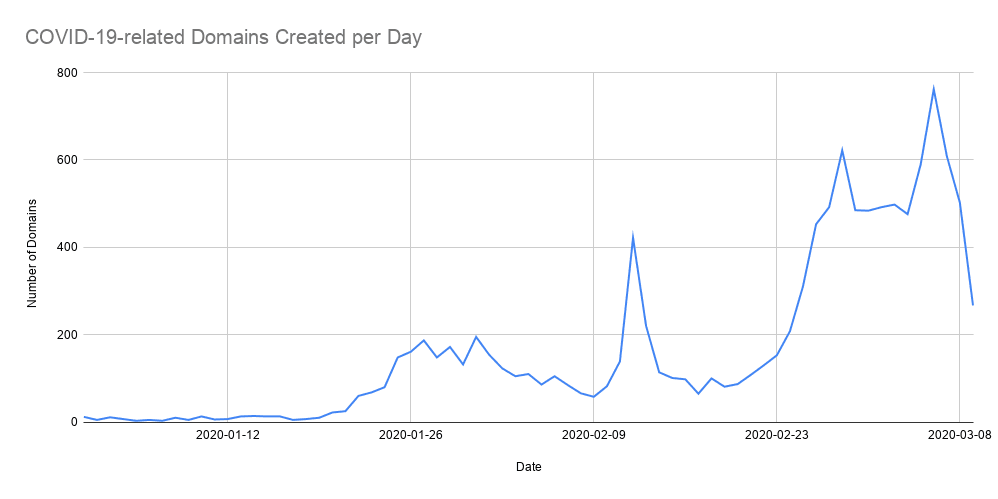
Graph showing the registrations of COVID-19-related domains per day in 2020. Recorded Future analysts created a query to find domain registrations of URLs containing “corona,” “covid19,” or “covid2019.” Download the appendix for a list of these domains.
Background
According to the World Health Organization, the current coronavirus, known as Coronavirus Disease 2019 (COVID-19), was first reported from Wuhan, China on December 31, 2019. COVID-19 is a viral, respiratory disease that has spread throughout the world, causing fear and panic as the outbreak progresses.
To date, over 100,000 people have been infected across the world, and over 4,000 have died. Cybercriminals and threat actors have begun to take advantage of the notoriety of the virus and the uncertainty and fear associated with it, deploying phishing campaigns that use COVID-19 as a lure to get victims to download malware or give away personal information.
Analysis
To understand the use of COVID-19 by cybercriminals and threat actors, Recorded Future correlated the number of domains created associated with “coronavirus” in 2020 with the number of references to cyberattacks or exploits involving “coronavirus” or “COVID-19.”
Cyberattacks Using COVID-19
Over the last two months, Recorded Future has observed an increase in the number of instances involving COVID-19 used as an attack vector in any cyber incident, as shown in the timeline below:
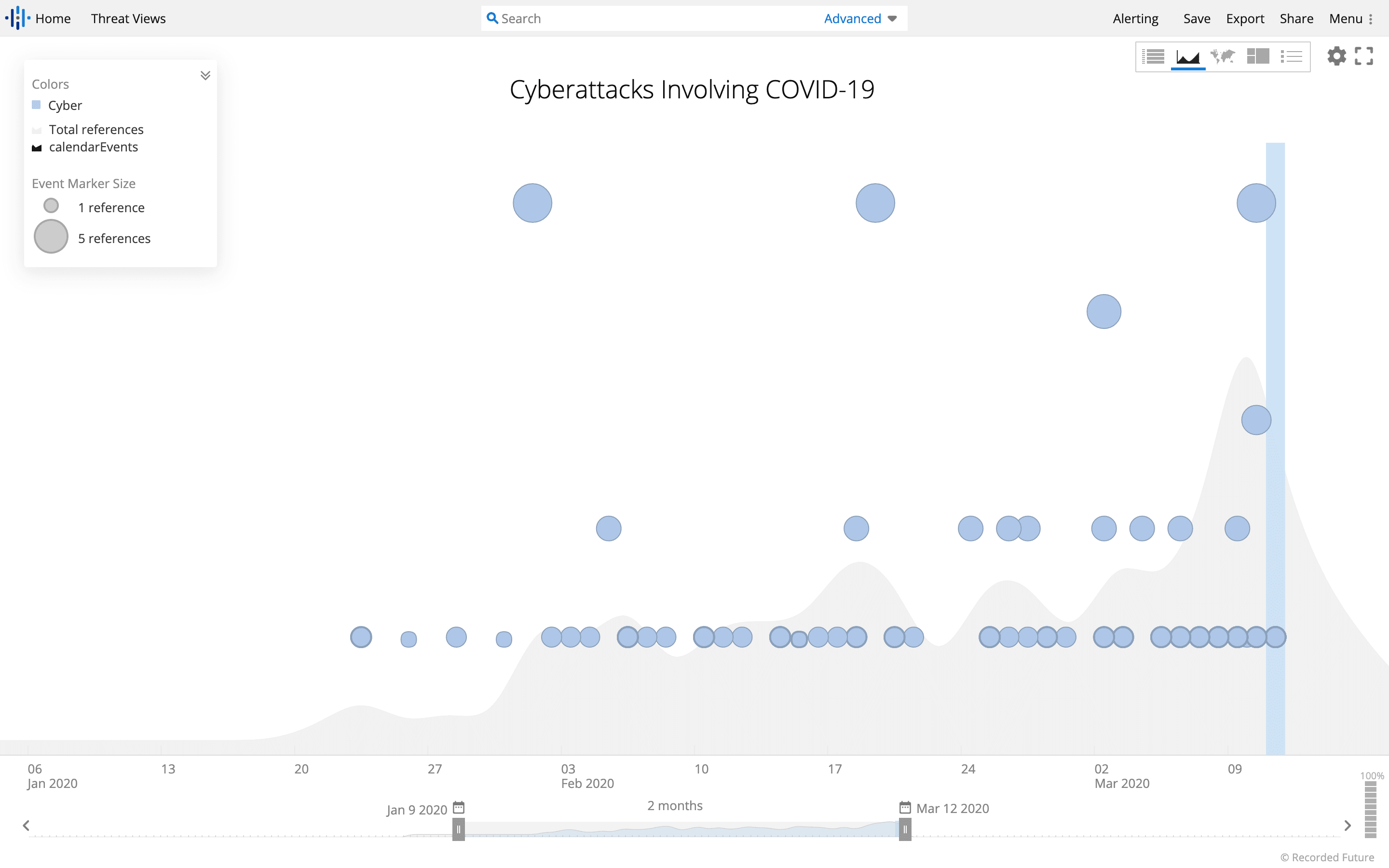
Number of references to coronavirus or COVID-19 used in association with a cyber exploit or cyberattack over the past two months.
Beginning in late January 2020, the volume of data increases, with larger spikes occurring as the number of COVID-19 infections increased through the month of February. While Recorded Future has observed COVID-19 being used as part of different types of cyber incidents, it has been primarily used as a phishing lure. Using a Recorded Future query, Recorded Future identified incidents of the malicious use of COVID-19 over the last month. Where possible, we provide IOCs for these campaigns in the appendix. The following incidents were identified:
- The AZORuIt malware was observed being delivered by phishing documents that used COVID-19 as a lure in early February 2020. Researchers at Proofpoint observed a COVID-19-themed phishing campaign targeting the manufacturing, industrial, finance, transportation, pharmaceutical, and cosmetic industries. These attacks involved emails that contained Microsoft Office document attachments designed to lure victims and exploit a Microsoft Office vulnerability, tracked as CVE-2017-11882, which allows attackers to run arbitrary code in the context of the current user. The malicious documents contained what is purported to be an advisory on the impact of the virus on the shipping industry. Once the malicious document is opened, it installs the information-stealing malware “AZORult.” The AZORult strain observed in the campaign did not download ransomware, as it has done in previous attacks. According to researchers at Proofpoint, the malicious emails are originating from groups in Russia and Eastern Europe.
- In late January 2020, researchers at IBM X-Force observed cybercriminals using coronavirus as a phishing lure to distribute Emotet in a campaign primarily targeting Japan. The phishing emails claimed that the attached Microsoft Word documents contained health information and updates, but in reality contained a malicious VBA macro that installs a PowerShell script, which then downloads the Emotet trojan.
- Kaspersky published an article about phishing emails that emulated the CDC, in particular from emails containing the domains cdc-gov[.]org and cdcgov[.]org. In one instance, the URL contained within a phishing email led to a fake Microsoft Outlook login page, designed to convince victims to input their credentials. In another instance, victims were asked to donate Bitcoin to the CDC to aid in the pursuit of a vaccine.
- The security firm Cofense identified a similar, though more sophisticated, phishing campaign using the subject line “COVID-19 — Now Airborne, Increased Community Transmission” that appears to originate from the address CDC-Covid19[@]cdc[.]gov. When victims click on the embedded link, they are redirected to a Microsoft Outlook login page, and upon entering their legitimate credentials, are further redirected to a legitimate website of the CDC. While these phishing emails appear to come from a legitimate address on the CDC domain, this is due to the threat actor purposefully disguising the true origin of the email. The deception was made possible by inserting an SMTP HELO command that tells the receiving email server to treat the email as if it originated from “cdc[.]gov,” despite the fact that the sender has a different domain and IP.
- Cofense also identified a phishing campaign using the subject line “Attention: List Of Companies Affected With Coronavirus March 02, 2020.” that contained a malicious attachment that dropped Agent Tesla Keylogger. This attachment used the icon of a Microsoft Excel file to masquerade as a legitimate Office document and was reported to be titled “SAFETY PRECAUTIONS,” with an .exe file extension.
- Phishing emails primarily targeting Italian email addresses contained malicious Microsoft Office documents with embedded VBA macros that were used to drop Trickbot. The Trickbot banking trojan can be used to steal victims’ confidential information, as well as to drop additional malware. The email subject line used in this campaign was “Coronavirus: informazioni importanti su precauzioni,” and to bolster the credibility of the attached lure, the supposed author was “Dr. Penelope Marchetti,” an employee of the WHO in Italy.
- The security research team @issuemakerslab observed a malicious Microsoft Word document dropping the North Korean BabyShark malware that claimed to contain information on South Korea’s response to the COVID-19 virus.
- The security research team @reddrip7 identified a malicious Word document attachment called “Коронавірусна інфекція COVID-19.doc” that contained a C# backdoor. Researchers suspect this malware is related to the Hades APT. Due to the presence of the string “TrickyMouse” in the malware, the campaign has been dubbed “TrickyMouse” by the researchers. The document uses the branding and trademark of WHO and the Public Health Center of the Ministry of Health of Ukraine as a decoy and was used to target Ukraine.
- @reddrip7 also identified a COVID-19-themed phishing campaign that used a decoy document containing Nanocore RAT targeting the South Korean chemicals manufacturing company Dongwoo Fine-Chem Corporation.
- Another campaign used the FedEx trademark in a phishing attack, claiming to provide victims with information on global FedEx operations while the COVID-19 outbreak continues. It contained an attachment titled “Customer Advisory.PDF.exe” that, when opened, infected the victim with the Lokibot malware.
- Lokibot was additionally distributed in a phishing campaign that used COVID-19 as a lure, claiming to be sent by the Ministry of Health in the People's Republic of China. The emails claimed to contain information about emergency regulations surrounding the virus with the subject line “Emergency Regulation Ordiance” (sic), and had a Windows RAR file attachment with the extension .arj. Once opened, the malicious attachment infects the victim with Lokibot, immediately contacting a malicious IP address and exfiltrating user credentials.
- The Grandoreiro banking trojan was observed being distributed via malicious sites that use the ongoing coronavirus epidemic as a lure. Twitter user @JAMESWT_MHT shared an instance of the trojan used as part of this campaign. The websites show information about the coronavirus with an embedded video player, and once the user clicks the player, the Grandoreiro executable is downloaded. According to Twitter user @ESETresearch, the malware is currently targeting users in Brazil, Mexico, and Spain.
- COVID-19 was also used as a lure in what researchers suspect is a MUSTANG PANDA campaign. MUSTANG PANDA is a suspected Chinese government-linked threat actor group. The lure used in this campaign was a .rar file purportedly containing statements from Vietnamese Prime Minister Nguyen Xuan Phuc regarding COVID-19. The .rar file contains a .lnk file that when opened by the victim, executes mshta.exe via cmd.exe to run the malicious script contained in the .lnk file. While the malicious script executes, a Word document titled “Chi Thi cua thu tuong nguyen xuan phuc.doc” is displayed to the victim. Ultimately, a DLL side-loading technique is used to download and execute a malicious executable and communicate with a command-and-control server.
Coronavirus has also been weaponized as a way to spread spyware by the Iranian government. Iran’s Health Ministry sent a message to victims advising them to download a specific application to monitor for potential symptoms of COVID-19. This application was, in reality, spyware. The malicious Android application, called ac19.apk, is capable of gathering victim location services and monitoring a user’s physical activity (such as walking or sitting) — ostensibly to determine where the user is going and when. The application is distributed on a website created by the Iranian government, https://ac19[.]ir/.
Domain Registrations
Beginning in on January 12, the number of domain registrations started to increase, with an additional large spike on February 12, as shown in the first image, which aligns with the increase in the number of references seen in the previous image. This spike coincides with the largest single-day spike in the number of COVID-19 cases, as seen in the chart below:
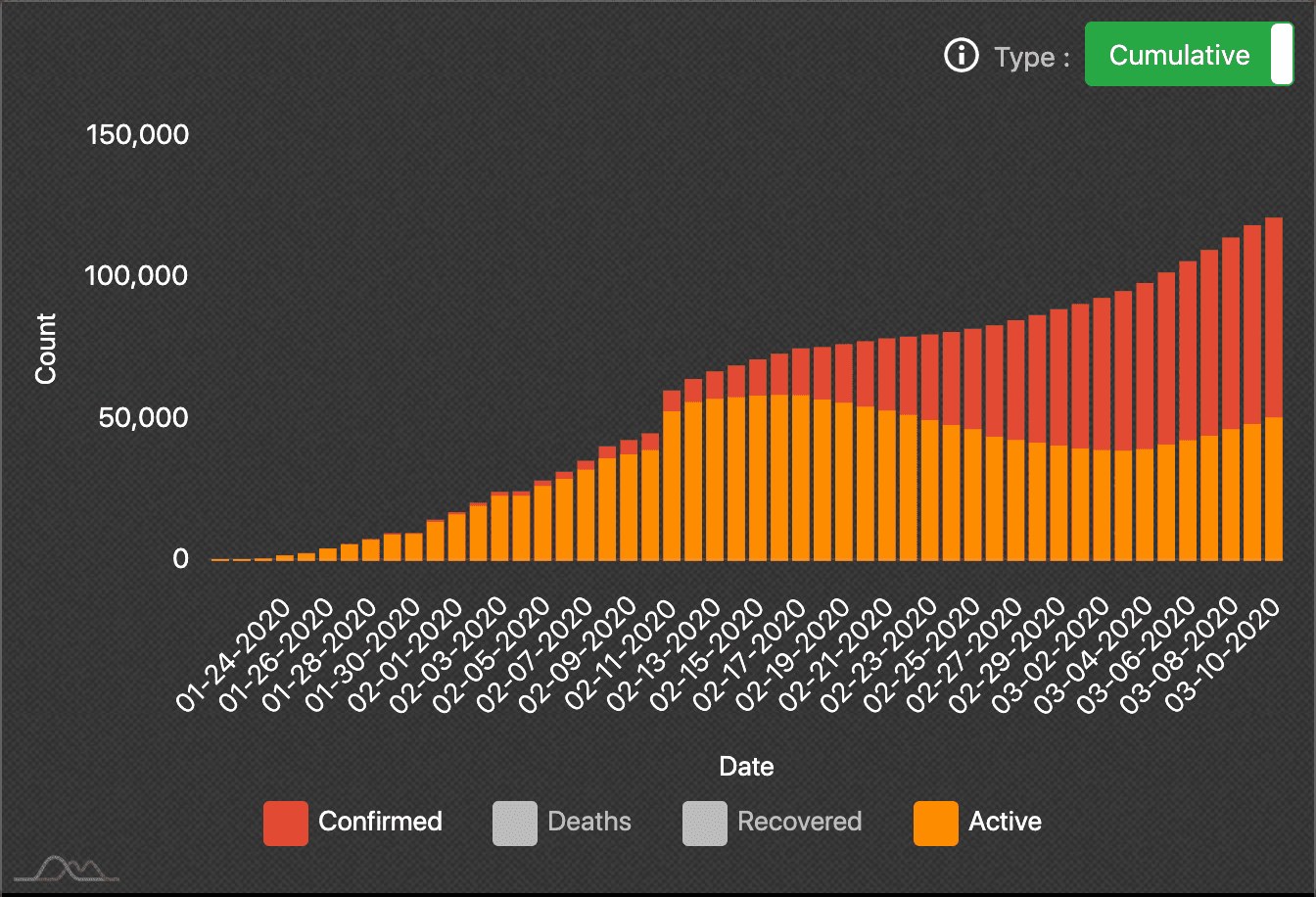
Graph showing number of COVID-19 cases per day over time.
Recorded Future analysts cannot confidently establish the domain registrations in mid-February as the effect of the increase in cases during that time period. However, we assess that this correlative relationship possibly indicates that cybercriminals and other threat actors increasingly observe the relevance of the outbreak as a targeting mechanism.
Outlook
Recorded Future observed cybercriminals and other threat actors employing references to COVID-19 primarily in phishing attacks designed to obtain victims’ personal information or to drop additional malware. Because these attacks prey on the fears of victims and often use a sense of urgency to get the victim to click, organizations should take the following precautions:
- Be especially wary of any email or other communications purporting to come from the CDC or WHO, even if it appears to come from a legitimate address on the official domains (cdc[.]gov and who[.]int). Many of the phishing emails used the branding and trademarks of these two organizations as part of the lure, and this trend will likely continue as the outbreak grows in the United States. Threat actors have also incorporated URLs with legitimate websites as the link text, while the underlying link is malicious. The U.S. Federal Trade Commission has suggested that interested parties visit the known WHO and CDC websites directly for up-to-date information and to be cautious about any email purporting to be from those entities. Unless your organization is in the healthcare field, it is unlikely that these agencies will be sending you emails about COVID-19. Also note that the CDC, WHO, and other organizations do not take cryptocurrency payments, so any request of this type should be considered malicious.
- While many legitimate organizations will send emails regarding precautions that they are taking to minimize the threat of COVID-19, the use of legitimate corporate branding has been used to send malware to victims. The malicious emails often use language creating a sense of urgency (though often with bad grammar or spelling), or attachments or links that are said to contain additional information rather than being informational themselves. Users should avoid opening attachments, but it is advisable to treat all emails regarding the COVID-19 outbreak with caution.
- As with all phishing attacks, it is recommended that users disable macros in Microsoft Office for any users that do not absolutely require it. Many of the malicious attachments observed by Recorded Future analysts in association with COVID-19 used VBA macros as an initial part of the infection of victims. VBA macros remain popular infection mechanisms for malicious documents that are used as phishing lures, and analysts assess with high confidence that this trend will continue.
Related