Charting China’s Climb as a Leading Global Cyber Power

Over the past five years, Chinese state-sponsored cyber operations have evolved into a more mature and coordinated threat, focusing on exploiting both known and zero-day vulnerabilities in public-facing security and network appliances. They have also placed a strong emphasis on operational security and anonymity, making it harder to detect their activities. These changes have been influenced by both internal factors like military restructuring and changes in domestic regulations, as well as external factors including reporting by Western governments and the cybersecurity community. This evolution has made it more challenging for organizations, governments, and the cybersecurity community to defend against these threats.
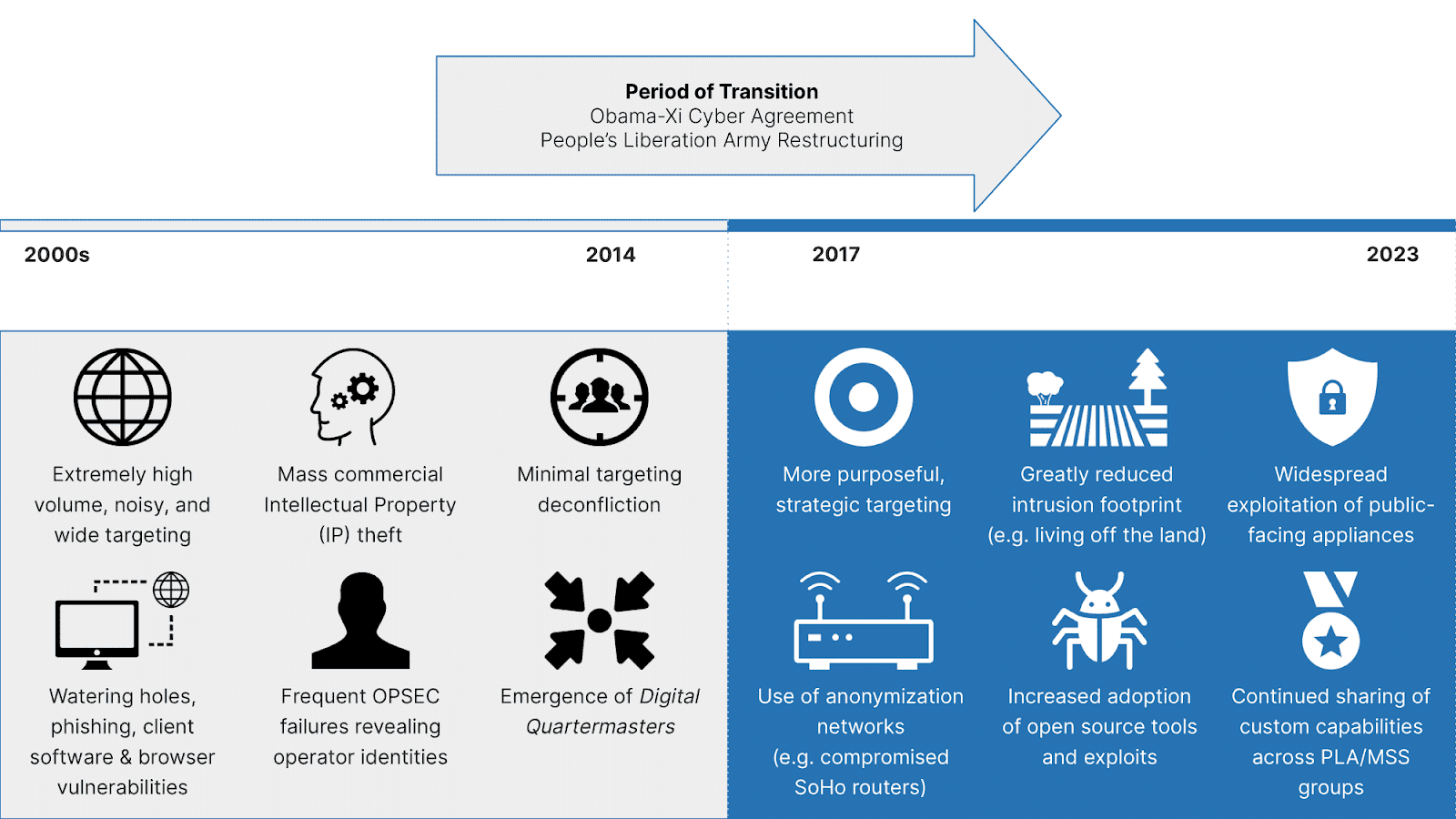 Evolution of Chinese cyber-espionage activity (Source: Recorded Future)
Evolution of Chinese cyber-espionage activity (Source: Recorded Future)
Chinese cyber-enabled economic espionage has shifted from broad intellectual property theft to a more targeted approach supporting specific strategic, economic, and geopolitical goals, such as those related to the Belt and Road Initiative and critical technologies. This poses risks for governments and corporations, impacting negotiations and competitiveness. Due to the focus on exploiting novel vulnerabilities in public-facing devices, a vulnerability-centric defense approach is inadequate, emphasizing the need for better defensive in-depth measures to detect post-exploitation activities.
As China continues to develop its cyber capabilities, there has been a growing focus on exploiting zero-day vulnerabilities in public-facing appliances, which has proven an effective tactic for gaining access to various global targets. With organizations moving to cloud services it is likely they will see a similar emphasis. China's efforts to project power in the South China Sea and Taiwan, along with the U.S. strengthening alliances in the region, will likely lead to increased intelligence gathering and strategic reconnaissance activities. Targeting critical infrastructure is not necessarily a sign of imminent conflict but is done in preparation for potential future actions.
Given China's significant commitment of resources to offensive cyber operations and the evident enhancement of their capabilities, they are poised to become a dominant global force in cyber espionage and information warfare.
To read the entire analysis, click here to download the report as a PDF.
Related
