Steering Through Threat Intelligence Hype
Threat intelligence is a relatively new area of information security, and those with services and technology to offer are keen to ensure organizations understand the benefits they’ll see from this type of capability. But as with any emerging technology, the hype occasionally overtakes reality.
Actual Benefits of Threat Intelligence
Recent research from an SC Media survey of information security professionals provides some insight here, with 43 percent of respondents expecting threat intelligence to offer an “early warning of new threats and tactics” immediately and with minimal effort.
While a mature and effective threat intelligence capability should aim to eventually deliver this, there are many other benefits of threat intelligence that can be more realistically achieved in the short, medium, and long term.
Other benefits featured in the survey responses included:
- 23.2%: Uncovering new exploits or vulnerabilities affecting relevant technologies.
- 10.8%: Monitoring for brands mentioned in connection with attacks and breaches.
- 9.1%: Aiding with incident response investigations.
- 9.1%: Correlating internal security alerts with context from external intelligence.
You can see all the results from this recent survey, which gathered insight from more than 200 security professionals across an array of industries, revenues, and company sizes.
Threat Intelligence Isn’t Just Flipping a Switch
Some of the hype surrounding threat intelligence might make it seem like companies can simply “flip a switch” and “do threat intelligence.” In reality, businesses need to be pragmatic when it comes to defining how threat intelligence can be applied as part of their whole information security strategy, and consider which phases will align to their most pressing risks, as well as available resources and existing technology.
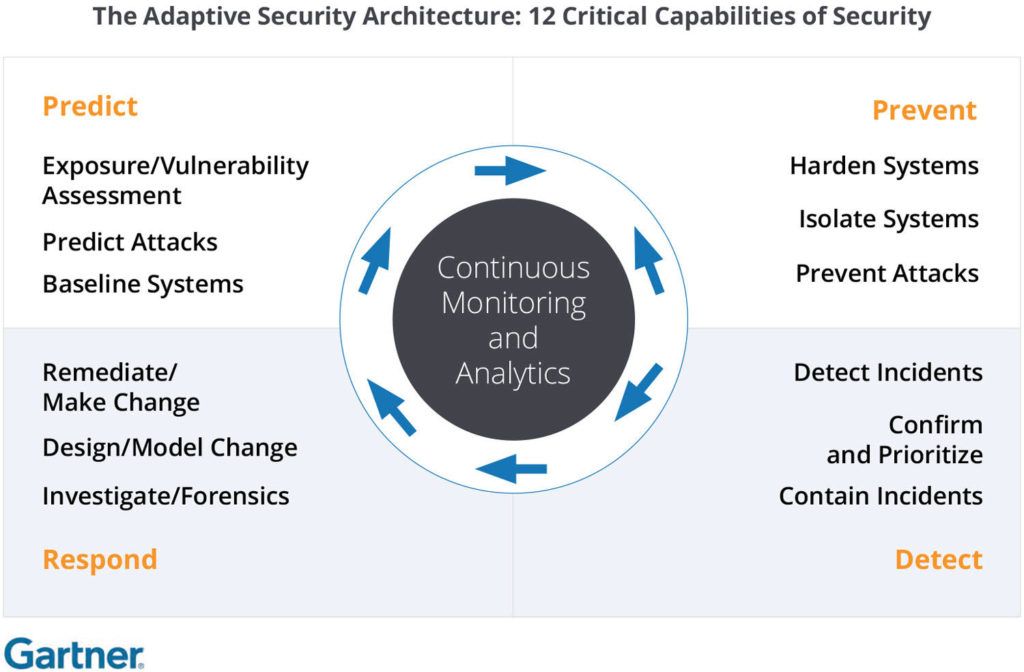
We can see this ethos reflected in Gartner’s proposed Adaptive Security Architecture. The diagram above details the operational functions of information security, and their roles in reducing the risk from incoming attacks.
But, of course, these are only effective when augmented with the outputs from continuous monitoring and analytics.
Historically, you might consider this monitoring and analysis to be from internal log data, but modern threat intelligence has an important role to play in bringing context to the entire information security lifecycle. There are many applications, across numerous teams with varying responsibilities that can work together to prevent, detect, respond to, and predict the latest known and unknown threats and attacks.
Is your security team complaining that they don’t have enough raw data about emerging threats and newly discovered attacks to do their job? Perhaps not.
Are they drowning in data, some from internal sources, and some from the outside world? Maybe.
Is it hard to know how to correlate data with business-centric action? In many teams, absolutely.
Perhaps the idea of applying threat intelligence seems complicated, as well as time and resource intensive, but as with implementing any new initiative, even the small improvements you make have the potential to dramatically improve both efficiency and security.
Do you need help getting started? Read our white paper to get best practices for applying threat intelligence.
Related
