True Identity of Notorious Hacker tessa88 Revealed

_Scope Note: To create the following actor profile, Insikt Group used OSINT, Recorded Future data, and dark web analysis to identify the contact information, alternative aliases, and TTPs used by the actor tessa88.
This profile will be of most interest to email service providers, social media, and technological companies located primarily in the United States and Russia._
Executive Summary
In early 2016, a previously unknown hacker operating under the alias of tessa88 publicly emerged after offering an extensive list of compromised, high-profile databases for sale. The hacker offered for sale the databases of companies such as VKontakte, Mobango, Myspace, Badoo, QIP, Dropbox, Rambler, LinkedIn, and Twitter, among others. Within several months of incredibly active public engagement, the hacker's personas were banned from almost every dark web community for various reasons, and by May of 2016, tessa88 entirely ceased all communications with the media and public alike. In the following months, numerous attempts were made to uncover the true identity of the hacker. However, no concrete evidence was ever produced that linked tessa88 with any real individual.
New findings strongly suggest that the individual behind tessa88 may be Maksim Donakov of Penza, Russia, who operated under multiple different monikers on the dark web. It is possible that a second unknown individual was assisting Donakov in maintaining the tessa88 account, adhering to impeccable OPSEC procedures and until this day remaining anonymous. In either scenario, we firmly believe that Donakov Maksim has directly benefited from the sales of compromised databases and should be viewed as the main actor.
Key Judgments
- tessa88’s criminal career likely began as early as 2012, before the breaches of LinkedIn, Dropbox, Yahoo, and others that were accredited to them. They likely created the alias tessa88 specifically to sell high-profile databases.
- Our analysis, based on discovered images of the real individual hiding behind the moniker tessa88 and underground forum discussions, allows us to assess with a high degree of confidence that tessa88 is a man and not a woman.
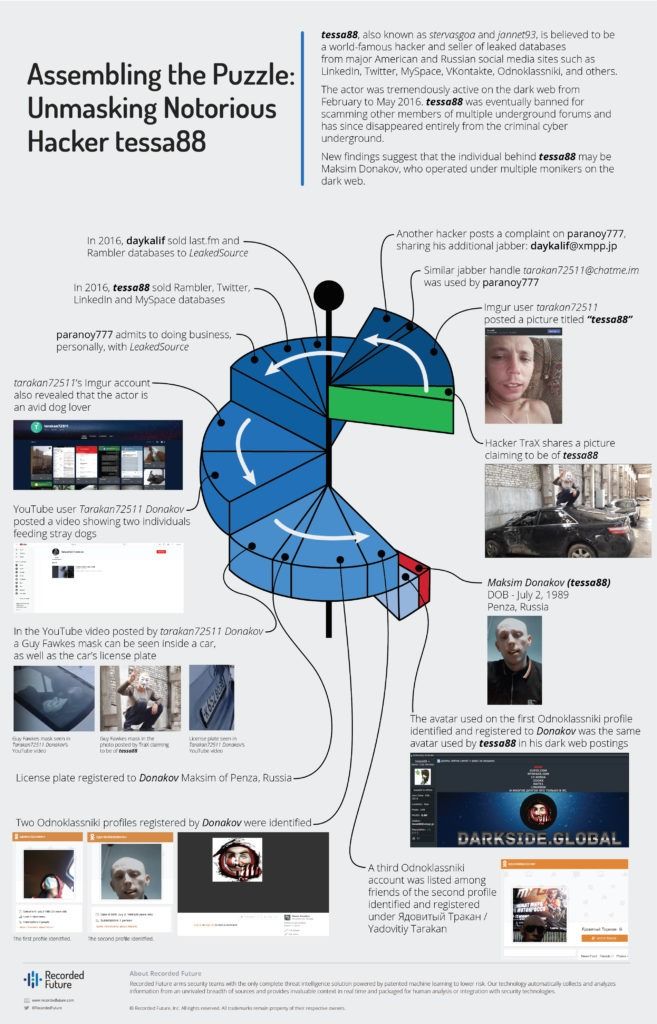
- Our analysis reveals that the moniker tessa88 is tied to aliases Paranoy777, Daykalif, and tarakan72511. All share similar social media photos that are nearly identical to a passport photo of Maksim Donakov, who is the individual behind Paranoy777.
- Our research suggests that Donakov, Maksim Vladimirovich (Донаков, Максим Владимирович), is a resident of the Russian Federation.
Uncovering tessa88’s true identity.
Background
The threat actor tessa88, also known as stervasgoa and jannet93, is a famous hacker who was involved in the sale of multiple high-profile databases, including LinkedIn, VKontakte, Facebook, MySpace, and Twitter, from February to May of 2016. It is believed by some in the media that the actor is a Russian-speaking female. tessa88 was active for only a short time, during which they sold databases from websites including LinkedIn, VKontakte, Yahoo, Yandex, Rambler, MySpace, Badoo, QIP, and Mobango. tessa88 was eventually banned on multiple forums due to accusations of fraudulent activities from other members.
Recorded Future data shows that the actor Peace_of_Mind, also known as Peace, was selling a LinkedIn database as early as May 16, 2016 on the currently defunct TheRealDeal Market. The LinkedIn breach resulted in the arrest of Russian national Yevgeniy Nikulin (Евгений Никулин) by the FBI in October 2016. Nikulin was in the Czech Republic at the time and was later extradited to the United States. The Russian government claimed that the actions of the U.S. were politically motivated, and in an effort to fight Nikulin’s extradition, issued a warrant for his arrest in November 2016, alleging the individual had stolen $3,450 in WebMoney. At the time of this report, the investigation is still pending, and no clear evidence has been produced linking Nikulin to Peace_of_Mind.
Motherboard published their findings from an interview they had with tessa88, who claimed to be a veteran member of the criminal underground and accused Peace_of_Mind of stealing the databases that tessa88 was selling. Peace_of_Mind, in return, claimed that tessa88 stole the databases from a friend to sell online.
A report from the cybersecurity firm InfoArmor claims that tessa88 acted as a proxy who sold accounts and personally identifiable information (PII) stolen by a group of hackers identified as “Group E.” InfoArmor claims that tessa88 was the first to sell accounts from many of these high-profile databases beginning as far back as February 2016, which Recorded Future data confirmed.1 Around May 2016, InfoArmor claimed that tessa88 and Peace_of_Mind made an agreement to share at least some of their respective databases between one another in a likely attempt to expedite monetizing the massive amount of data between the two actors. The relationship between tessa88 and Peace_of_Mind deteriorated as other members of the underground communities claimed the data was of poor quality. If this report is accurate, this corroborates Motherboard’s findings and explains the outspoken hostility between the two actors.
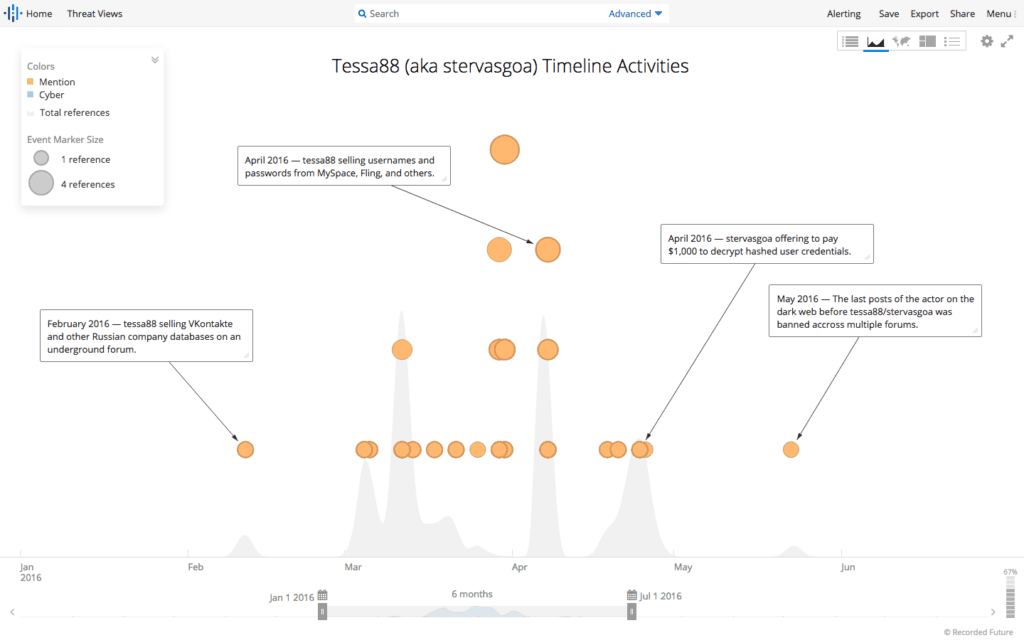
Activity of tessa88 (also known as stervasgoa) on the dark web between February and May 2016.
Threat Analysis
An analysis of dark web activity connected tessa88 to multiple chat and email accounts, including the Jabber accounts tessa88@exploit[.]im, tessa88@xmpp[.]jp, mrfreeman777@xmpp[.]jp, darksideglobal@exploit[.]im, the ICQ account 740455, and the email address firetessa@yahoo[.]com.

tessa88 selling databases from websites including LinkedIn and MySpace on an underground forum that is currently defunct.
The tessa88@exploit[.]im Jabber account used by tessa88 in sales threads on underground forums led to the Twitter account @firetessa, which on July 5, 2016, tweeted out that the Jabber account tessa88@exploit[.]im was theirs.
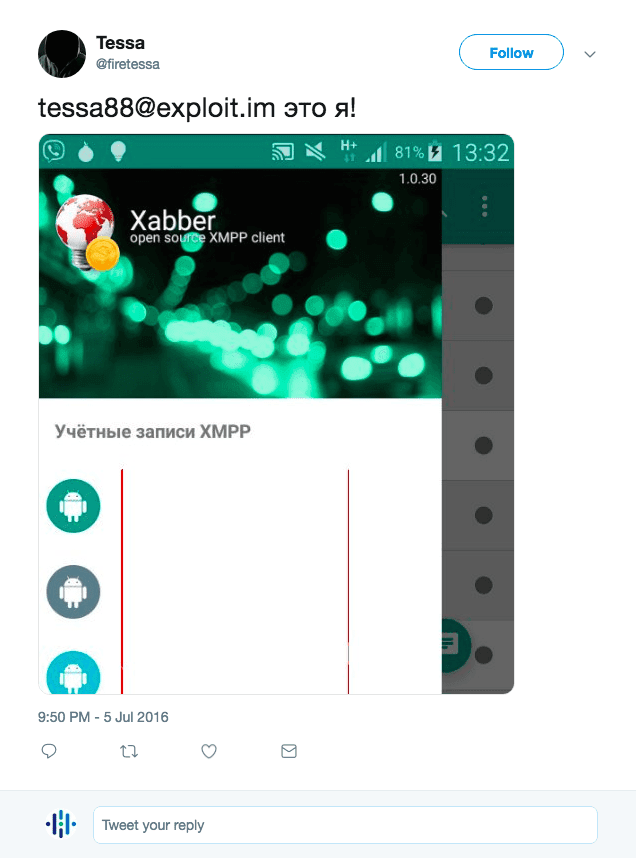
The tweet from the Twitter account @firetessa claiming tessa88@exploit[.]im to be theirs.
The actor TraX, a member of the underground community, stated that tessa88 is a man and posted an alleged photo of the actor on an underground forum. TraX also stated that tessa88 was behind recent mega breaches like LinkedIn, MySpace, and Yahoo, and even expressed a willingness to share this information with reporters.

An alleged photo of tessa88 posted by TraX on an underground forum.
OSINT then identified the Imgur account tarakan72511, who posted screenshots of discussions regarding the Yahoo and Equifax breaches with the actors HelloWorld and Ibm33a14. Note that Ibm33a14 is a Russian-speaking actor who claimed to have the original Yahoo and Equifax database dumps in 2017 on several cybercriminal forums.
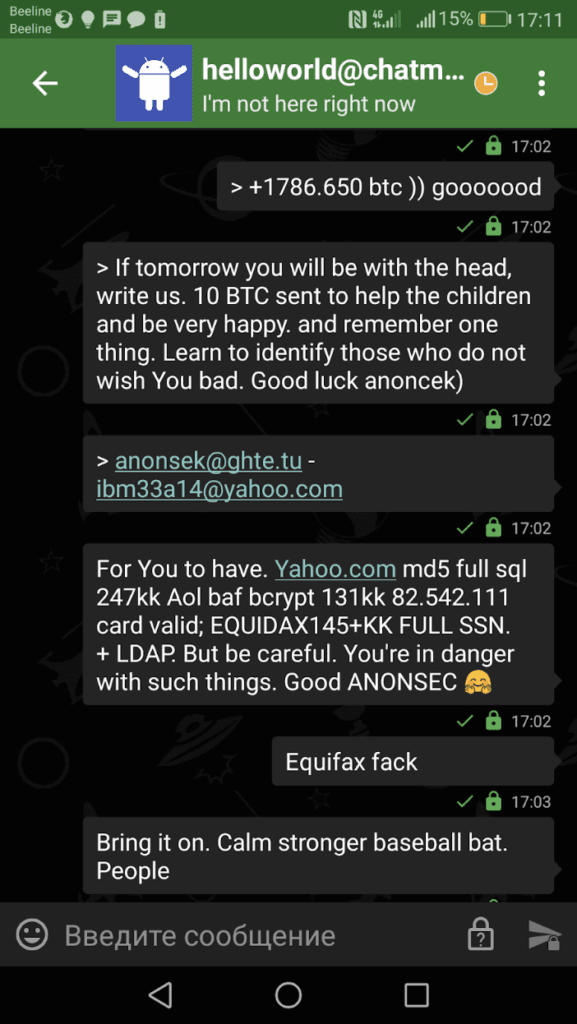
A screenshot of a discussion regarding the Yahoo and Equifax posted by tarakan72511.
That same Imgur account also posted a picture titled “tessa88” in 2017, showing a man whose body type and hairstyle are similar to the individual depicted in the aforementioned picture posted by TraX.

A potential picture of tessa88 posted by tarakan72511 on Imgur.
The moniker tarakan72511 is an alias used by the actor Paranoy777, who uses the Jabber account tarakan72511@chatme[.]im. Paranoy777, like tessa88, both were sellers of stolen databases from large social media and technology companies from February to May 2016.
Recorded Future identified a complaint filed against tarakan72511 in which another member claimed that Daykalif is a Russian-speaking scammer who was trading large databases and used the Jabber accounts daykalif@xmpp[.]jp and tarakan72511@chatme[.]im — the same Jabber account used by the actor Paranoy777, who, in turn, is connected to tarakan72511. If this claim is true, then it is likely that the users Paranoy777 and Daykalif are the same person.
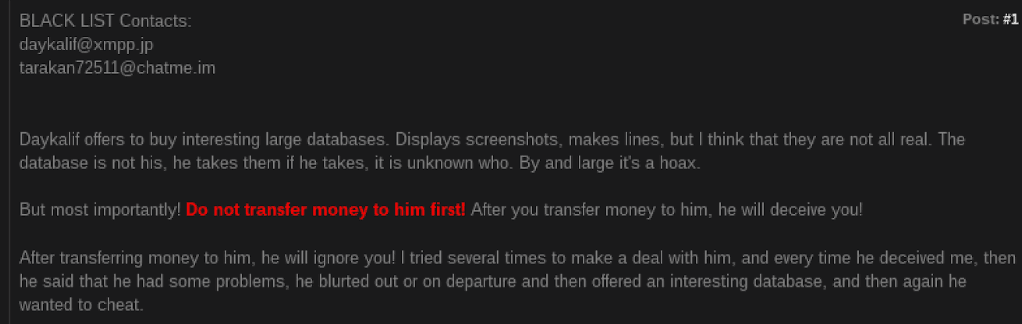
A complaint found on a criminal forum claiming that Daykalif used the Jabber accounts daykalif@xmpp[.]jp and tarakan72511@chatme[.]im.
More information provided by Imgur account tarakan72511 revealed that the user is apparently an avid dog lover. OSINT identified a YouTube account with a similar username — Tarakan72511 Donakov — who posted a video showing someone feeding stray dogs. During the video, a voice was heard stating that they are in Penza, Russia. The vehicle in the video is Mitsubishi Lancer with the registration number K652BO 58.
Tarakan72511 Donakov’s YouTube profile.
Moreover, at 56 seconds in the video, a Guy Fawkes mask is seen. A similar mask was used as the avatar on Tarakan72511 Donakov’s YouTube profile and is also worn by the person on the image shared by TraX.

The Guy Fawkes mask seen in the YouTube video, YouTube avatar, and in TraX’s image.
OSINT gathered on Donakov (Донаков) from Penza (Пенза) revealed that someone named Донаков М.В./Donakov M.V. committed several crimes in the Russian cities of Yaroslavl and Penza, including a motor vehicle accident that happened while driving a Mitsubishi Lancer in 2017. An individual named Donakov, Maksim Vladimirovich (Донаков, Максим Владимирович), originally from Yaroslavl and later having moved to Penza, was also mentioned in multiple articles from SudAct, stating that the individual had spent several years in prison prior to the accident.2
Pivoting from these records, the research identified three Odnoklassniki profiles, all with the name Maxim Donakov — two of which listed their current location as Yaroslavl, and one as Penza. The first Odnoklassniki profile belongs to a man who was residing in Yaroslavl and was born on July 2, 1989. The user last visited the site on September 9, 2013. The second Odnoklassniki profile has the same name and date of birth as the previous profile. Both the profile picture and other images depict the same individual seen in the Imgur image from tarakan72511. Note the Mitsubishi Lancer with the license plate А 134МК 76.
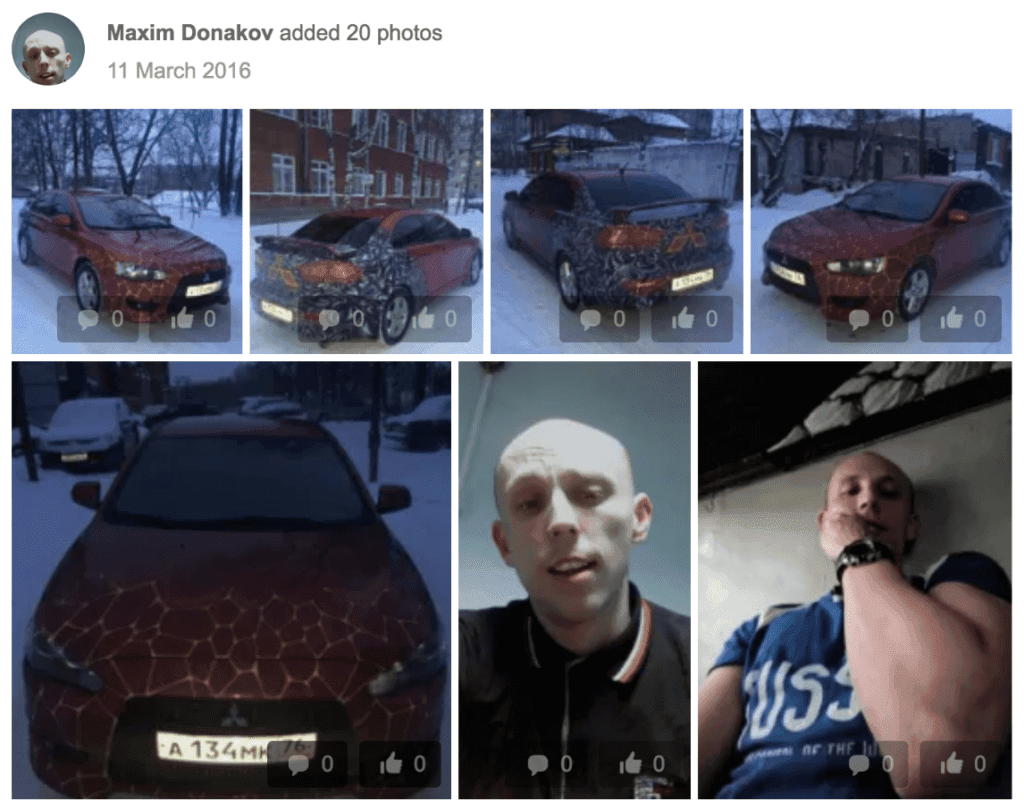
Images from the Odnoklassniki profile of Maxim Donakov.
The analysis of the second Odnoklassniki profile revealed that the actor is linked to another user, “Ядовитый Таракан” (Yadovitiy Tarakan), allegedly residing in Pervomaysk, Ukraine. Yadovitiy Tarakan’s name is synonymous with the Imgur account tarakan72511, and the profile photo of the person strongly resembles Donakov Maxim. It is worth mentioning that Pervomaysk is Maxim Donakov’s real place of birth. Considering the facts mentioned above, we assess with a high degree of confidence that Yadovitiy Tarakan’s profile also belongs to Donakov Maxim.
Another Odnoklassniki profile with the username “Ядовитый Таракан” created by Maxim Donakov.
Furthermore, confidential sources confirmed that Maxim (Maksim) Donakov is a real person born on July 2, 1989. According to SudAct, Donakov was released under police supervision but was then imprisoned after committing another crime in 2014. This may explain the existence of multiple Odnoklassniki profiles, as Donakov may have been forced to create a new profile after his release from prison if he forgot the login credentials for his previous account(s).
OSINT identified other accounts and contact information likely related to Donakov (tessa88), such as a VKontakte profile for Maxim Ivanov with the phone number +79022222229, profiles on Vkrugudruzei and Valet.ru, and the YouTube account Maxim Donakov with the phone number +17789981919. An open web search for “Максим Донаков” revealed the profile Gulik01 on Freelance.ru, which possibly belongs to tessa88 (Donakov). The account information for Gulik01 states that he is a Russian-speaking information technology freelancer.
Moreover, additional searches in leaked databases identified Maksim Donakov, a resident of Penza born on July 2, 1989, matching the user profile information from the aforementioned Odnoklassniki profiles and the image titled “tessa88” posted by the Imgur user tarakan72511, which depicts the same person. Again, all of this indicates that tessa88 is indeed Maksim Donakov.
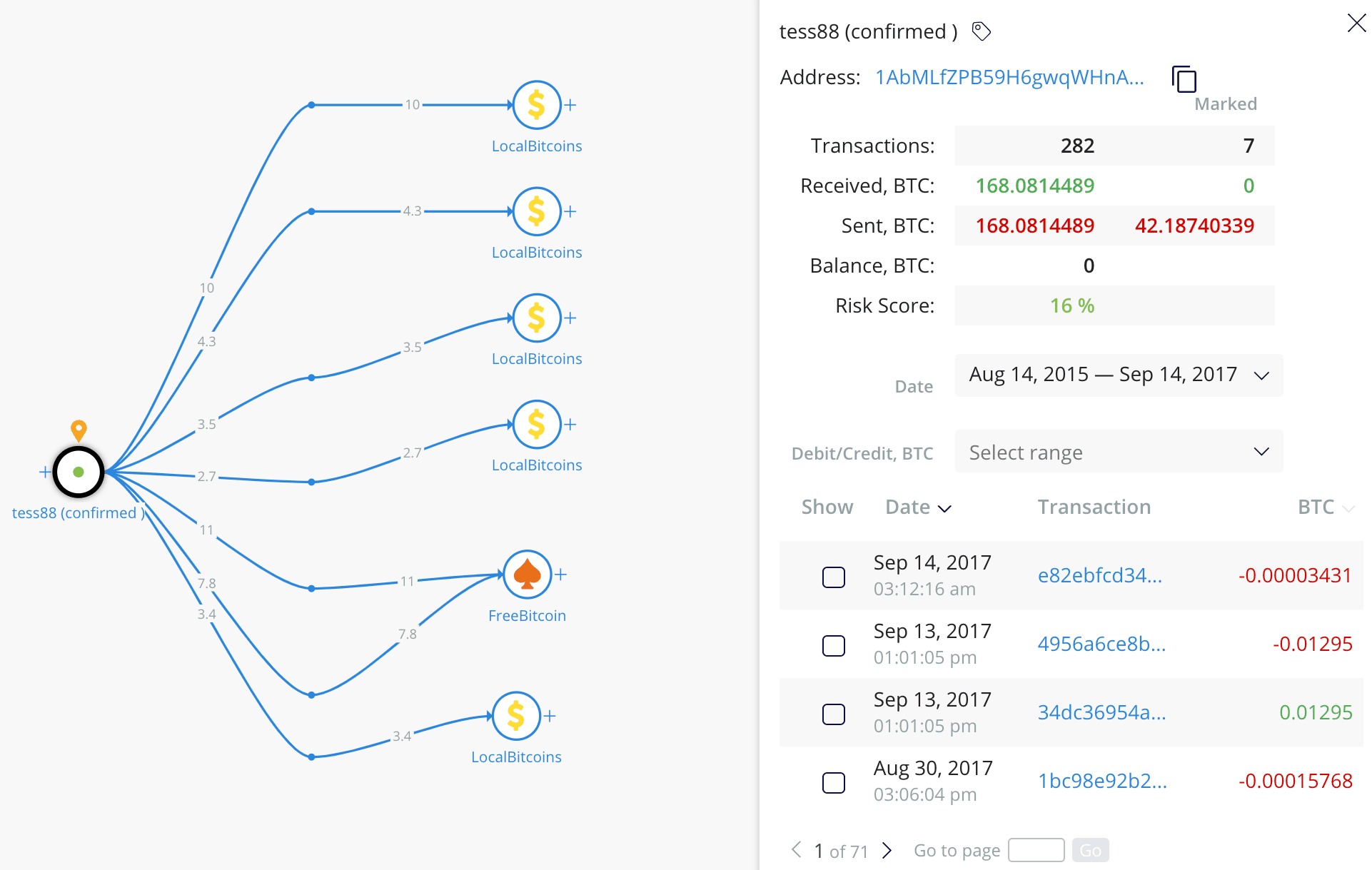
The analysis of tessa88’s confirmed Bitcoin wallet, with the majority of funds being laundered through LocalBitcoins.
Insikt Group’s analysis of transactions associated with the confirmed tessa88 Bitcoin wallet using Crystal Blockchain revealed that the hacker received at least 168 Bitcoins, or approximately $90,000, and most of the funds were eventually laundered through LocalBitcoins, a popular peer-to-peer exchange service. Despite the actor's disappearance in May of 2016, he continued using his Bitcoin wallet until August 2017.
Outlook
Insikt Group assesses with a high degree of confidence that tessa88 is one of many monikers created by Maksim Donakov to sell high-profile databases on underground criminal forums. Furthermore, it is likely that Donakov was active on the dark web since at least 2012 and also used the monikers Paranoy777, Daykalif, and tarakan72511.

Maxim Donakov, also known as tessa88, Paranoy777, and Daykalif.
Maksim Donakov, whose full name is Maksim Vladimirovich Donakov (Максим Владимирович Донаков), was born on July 2, 1989. Donakov is a resident of the Russian Federation who previously lived in Yaroslavl and later moved to Penza. Analysis of social media accounts and other sources from Recorded Future further confirm our findings.
According to the conducted analysis, the monikers tessa88, Paranoy777, and Daykalif were created intentionally to sell compromised data on the dark web. Considering the contradictory information regarding the breaches of the aforementioned companies, it is difficult to identify real tactics, techniques, and procedures (TTPs) applied by the hackers. However, the pending investigation of Yevgeniy Nikulin’s case, tied with the LinkedIn data leak, may shed light on this story and fill the remaining gaps.
1Recorded Future observed tessa88 selling PII from high-profile databases on a Russian hacking forum as early as February 2, 2016.
2SudAct (sudact.ru) is the largest non-governmental Russian website of judicial records.
Related
