Russia-Nexus UAC-0113 Emulating Telecommunication Providers in Ukraine

Editor’s Note: The following post is an excerpt of a full report. To read the entire analysis, click here to download the report as a PDF.
This report profiles the unique infrastructure used by the threat activity group UAC-0113, which is linked with moderate confidence by CERT-UA to Sandworm. The activity was identified through a combination of large-scale automated network traffic analytics and analysis derived from open source reporting. The report will be of most interest to individuals engaged in strategic and operational intelligence relating to the activities of the Russian government in cyberspace and network defenders.
Executive Summary
Recorded Future continues to monitor cyber espionage operations targeting government and private sector organizations across multiple geographic regions including Ukraine. From August 2022, Recorded Future observed a steady rise in command and control (C2) infrastructure used by the threat activity group tracked by Computer Emergency Response Team of Ukraine (CERT-UA) as UAC-0113.
UAC-0113 has been linked by CERT-UA to the Russian advanced persistent threat (APT) group Sandworm. This report highlights trends observed by Insikt Group while monitoring UAC-0113 infrastructure, including the recurring use of dynamic DNS domains masquerading as telecommunication providers operating in Ukraine, which shows that the group's efforts to target entities in Ukraine remains ongoing. Domain masquerades can enable spearphishing campaigns or redirects that pose a threat to victim networks.
Using a combination of proactive adversary infrastructure detections and domain analysis techniques, Insikt Group determined that UAC-0113’s use of this newly discovered infrastructure overlaps with other infrastructure tactics, techniques, and procedures (TTPs) previously attributed to the group by CERT-UA. The information and TTPs provided in this report enables defenders to better search for and protect against activity by UAC-0113.
Key Judgments
- Insikt Group has identified new infrastructure used by UAC-0113, a group linked with medium confidence to Sandworm by CERT-UA. Sandworm is a Russian advanced persistent threat (APT) group affiliated with the Main Intelligence Directorate/Main Directorate (GRU/GU) of the General Staff of the Armed Forces of the Russian Federation.
- Identified staging infrastructure continues the trend of masquerading as telecommunication providers operating within Ukraine and delivers malicious payloads via an HTML smuggling technique that deploys Colibri Loader and Warzone RAT malware.
- Though the intent of the observed decoy document found in connection with this activity is not fully known, it's likely to be deployed against Ukraine-based targets in support of military action in the region similar to previous UAC-0113 lures.
- A transition from DarkCrystal RAT to Colibri Loader and Warzone RAT demonstrates UAC-0113’s broadening but continuing use of publicly available commodity malware.
Background
On June 24, 2022, a report by CERT-UA detailed the use of the DarkCrystal remote access trojan (RAT) by UAC-0113, a group CERT-UA has indicated as being linked to Sandworm, a Russian Main Intelligence Directorate/Main Directorate (GRU/GU) related threat group. The CERT-UA report indicated that UAC-0113 was employing a malicious lure document which deployed DarkCrystal RAT. This activity likely targeted entities in Ukraine, specifically individuals or entities seeking information about Ukrainian military service personnel in relation to matters of legal assistance. Although the theme of this lure document was focused on military personnel legal matters, CERT-UA noted that the attack was also likely targeted at telecommunications providers of Ukraine.
DarkCrystal RAT is a commodity malware dating back to at least 2018; a sample of the malware was posted to Hybrid Analysis in November of that same year. Since its initial discovery, reporting indicates that it has been offered for sale in underground forums, likely making it a tool of interest to a wide range of threat actor groups, including those entities seeking an infostealer that can hinder attribution efforts by government or security professionals. Analysis of infrastructure linked to UAC-0113 uncovered a newly identified malicious ISO file (SHA256: 1c6643b479614340097a8071c9f880688af5a82db7b6e755beafe7301eea1abf) as part of an HTML smuggling technique. The ISO file contained a lure document, written in Ukrainian, that masquerades as a request for discounts on fuel for citizens of the Oleksandrivka Raion (district), an area in Donetsk. Additionally, the ISO file delivers an executable that deploys both Colibri Loader and Warzone RAT to the target machine.
Colibri Loader, first reported by Insikt Group in August 2021, is a commodity malware leased on XSS Forum by the user “c0d3r_0f_shr0d13ng3r”. It is written in assembly and C to target Windows operating systems without any dependencies. On March 11, 2022, Cloudsek researchers described Colibri Loader as “a type of malware that is used to load more types of malware into the infected system” which has “multiple techniques that help avoid detection”. On April 5, 2022, Malwarebytes researchers also reported on the operations of the Colibri Loader and further detailed its functionality, including its ability to “deliver and manage payloads onto infected computers”.
Warzone RAT (also known as Ave Maria Stealer) is a popular commodity remote access tool (RAT) that has been in active development since 2018. It is sold on underground forums and on the developer’s website, warzone[.]ws. The malware is advertised as a full-featured RAT developed in C/C++ that claims to be “easy to use and highly reliable.”
Threat and Technical Analysis
Insikt Group used intelligence provided by CERT-UA to discover further infrastructure linked to UAC-0113. The information uncovered suggests that it is highly likely that this threat group is continuing to masquerade as telecommunication providers operating within Ukraine. While monitoring the infrastructure, Insikt Group observed a malicious ISO file embedded in the HTML code, suggesting that domains and related IP addresses have likely already been, or are soon to become, operationalized.
Infrastructure
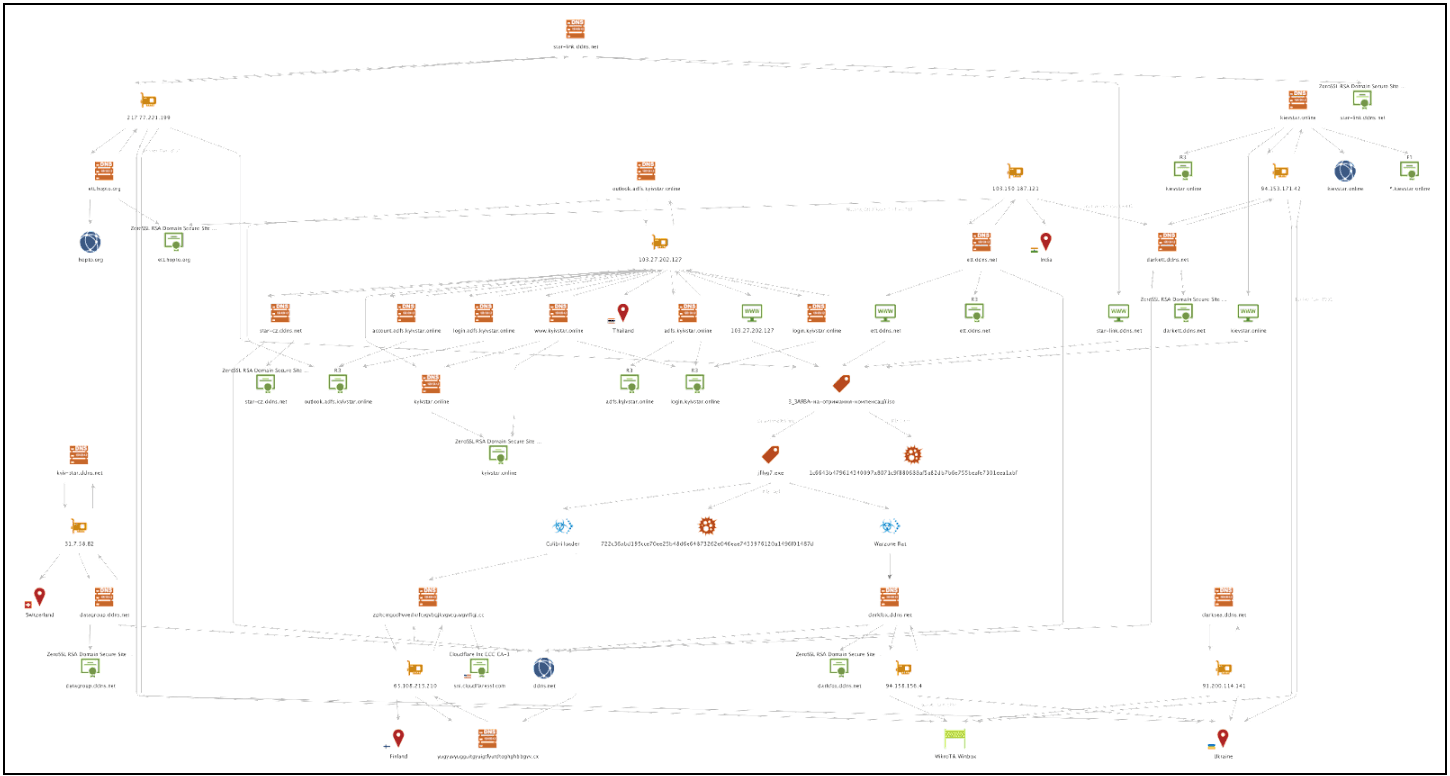 Figure 1: Maltego chart illustrating the links between previously reported infrastructure and the newly described infrastructure and activity in this reporting. See Appendix B (Source: Recorded Future).
Figure 1: Maltego chart illustrating the links between previously reported infrastructure and the newly described infrastructure and activity in this reporting. See Appendix B (Source: Recorded Future).
A domain noted in CERT-UA's June report on UAC-0113, datagroup[.]ddns[.]net, was likely masquerading as the Ukrainian telecommunications company Datagroup. This domain resolved to the IP address 31[.]7[.]58[.]82, which also hosted a further domain, kyiv-star[.]ddns[.]net, likely masquerading as the Ukrainian telecommunications company Kyivstar.
Analysis of these domains and their related shared IP address revealed a ZeroSSL TLS certificate hosted on port 443 with the Subject Common Name datagroup[.]ddns[.]net. No certificate for kyiv-star[.]ddns[.]net was found. The server banner for IP address 31[.]7[.]58[.]82 is detailed below in Figure 2.
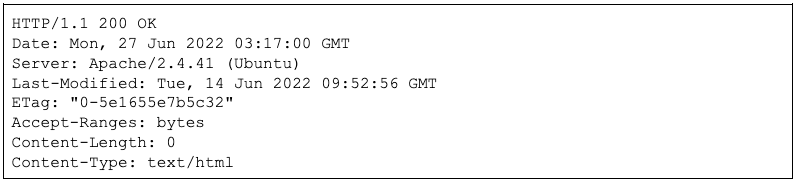 Figure 2: Server Banner of the IP Address 31[.]7[.]58[.]82 (Source: Shodan.io)
Figure 2: Server Banner of the IP Address 31[.]7[.]58[.]82 (Source: Shodan.io)
ett[.]ddns[.]net
Insikt Group identified further domain likely linked to UAC-0113, ett[.]ddns[.]net, hosted between July 7 and 15, 2022, on IP address 103[.]150[.]187[.]121. The domain ett[.]ddns[.]net is likely a spoof of the legitimate domain for EuroTransTelecom LLC, ett[.]ua, a Ukrainian telecommunications operator. This new infrastructure has several overlaps with the infrastructure noted in the CERT-UA reports, such as the use of the Dynamic DNS provider NO-IP with a domain masquerading as a telecommunications provider operating in Ukraine, the use of a TLS certificate from a free TLS certificate provider, and a server banner that shares similarities with the banner seen on IP address 31[.]7[.]58[.]82 shown above in Figure 2.
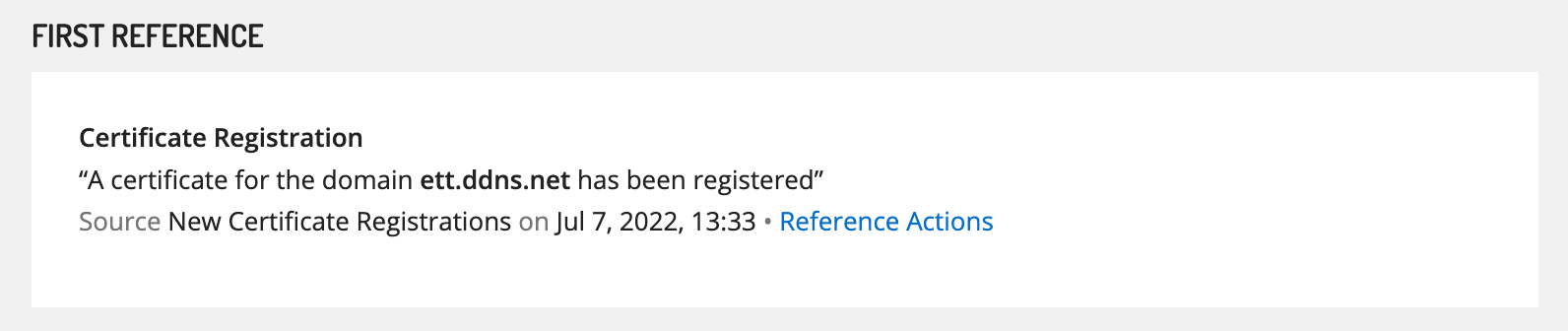 Figure 3: ett[.]ddns[.]net certificate registration event (Source: Recorded Future)
Figure 3: ett[.]ddns[.]net certificate registration event (Source: Recorded Future)
darkett[.]ddns[.]net
In addition to the ett[.]ddns[.]net domain, SecurityTrails banner data identifies a similarly named domain, darkett[.]ddns[.]net, hosted on the same IP address, 103[.]150[.]187[.]121, as ett[.]ddns[.]net. The domain darkett.ddns[.]net also uses a TLS certificate provided by ZeroSSL, similar to the previously observed domain datagroup[.]ddns[.]net.
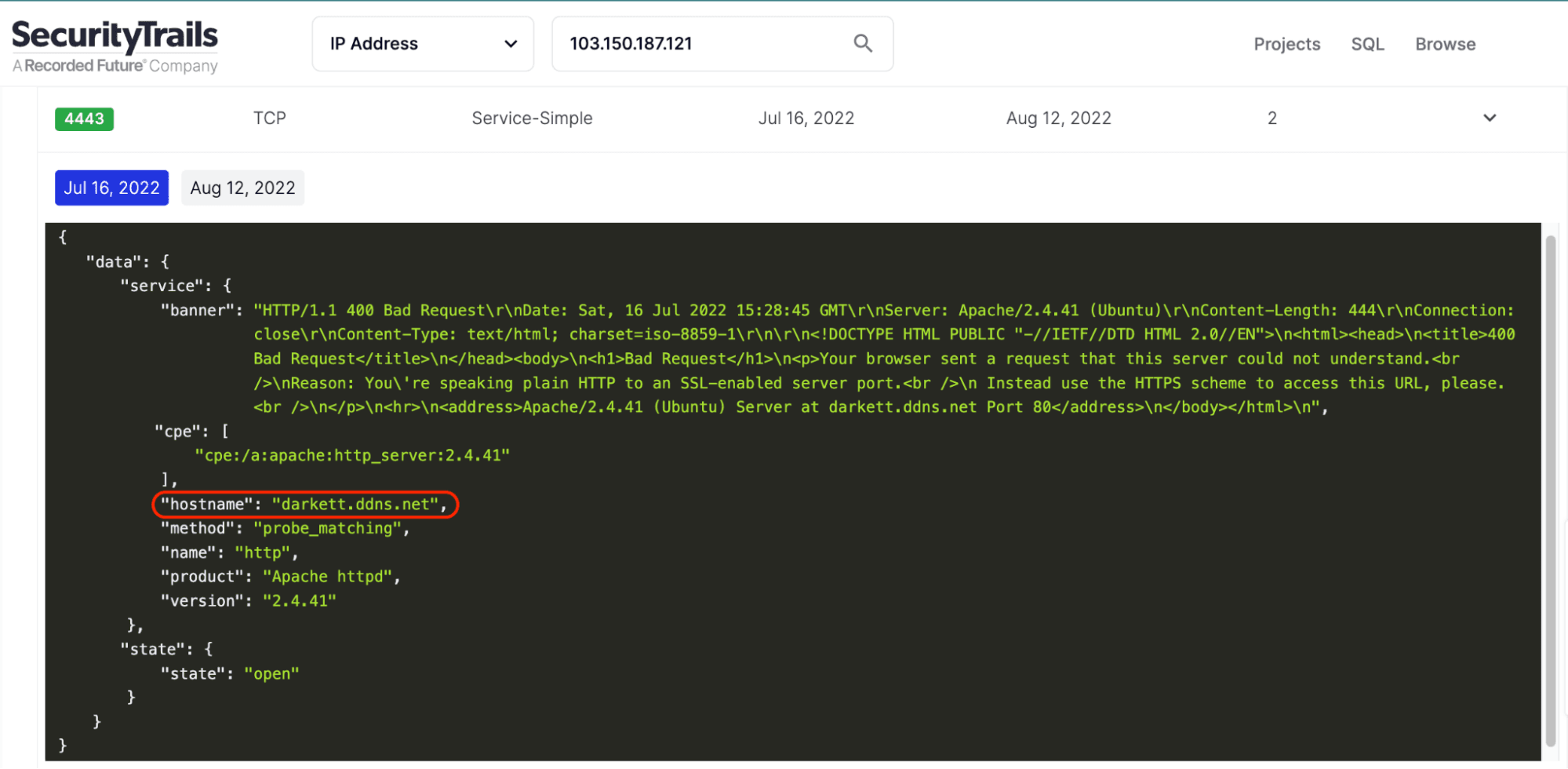 Figure 4: July 16, 2022, server banner and HTML from scan of the IP address 103[.]150[.]187[.]121 on port 4443 (Source: SecurityTrails)
Figure 4: July 16, 2022, server banner and HTML from scan of the IP address 103[.]150[.]187[.]121 on port 4443 (Source: SecurityTrails)
Further analysis of the domain darkett.ddns[.]net revealed that between July 15 and 16, 2022, the domain was also hosted on IP address 94[.]153[.]171[.]42. Historical DNS for IP address 94[.]153[.]171[.]42 also lists a resolution for the domain kievstar[.]online on July 12, 2022.
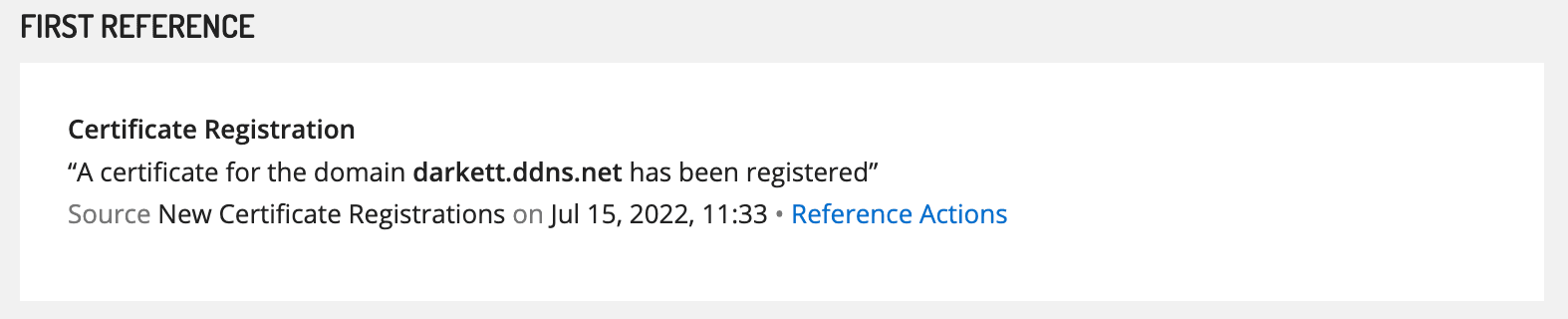 Figure 5: darkett[.]ddns[.]net certificate registration event (Source: Recorded Future)
Figure 5: darkett[.]ddns[.]net certificate registration event (Source: Recorded Future)
kievstar[.]online
On July 12, 2022, the domain kievstar[.]online moved from IP address 94[.]153[.]171[.]42 to multiple content delivery network (CDN) IP addresses hosted by Cloudflare. Further analysis of the domain kievstar[.]online details a Let’s Encrypt TLS certificate that was created on July 12, 2022.
103[.]150[.]187[.]121, ett[.]hopto[.]org and star-link[.]ddns[.]net
On August 1, 2022, SecurityTrails identified further updates to the IP address 103[.]150[.]187[.]121, listing a new TLS certificate for the domain ett[.]hopto[.]org. This TLS certificate is also provided by ZeroSSL and was created on July 13, 2022. On July 13, 2022, the domain ett[.]hopto[.]org resolved to the IP address 217[.]77[.]221[.]199. Further analysis of this IP address also details the resolution of the domain, star-link[.]ddns[.]net, on August 15, 2022, again likely spoofing a telecommunications company, Starlink (operated by American manufacturer SpaceX), which is reportedly assisting Ukraine in the conflict with Russia.
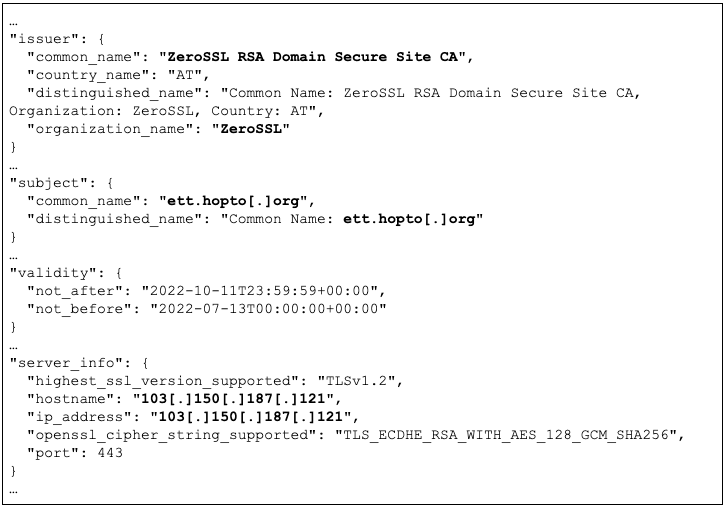 Figure 6: JSON excerpts from August 1, 2022, scan of the IP address 103[.]150[.]187[.]121 on port 443 (Source: SecurityTrails)
Figure 6: JSON excerpts from August 1, 2022, scan of the IP address 103[.]150[.]187[.]121 on port 443 (Source: SecurityTrails)
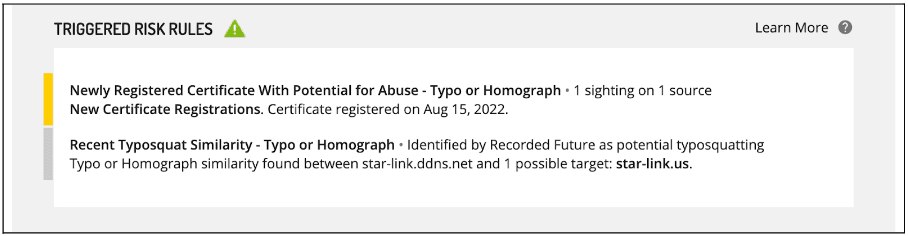 Figure 7: star-link[.]ddns[.]net’s Intelligence Card (Source: Recorded Future)
Figure 7: star-link[.]ddns[.]net’s Intelligence Card (Source: Recorded Future)
star-cz[.]ddns[.]net
Analysis of the domain star-cz.ddns[.]net, reported by CERT-UA on June 10, 2022, shows a resolution to the IP address 103[.]27[.]202[.]127. A further domain, kyivstar[.]online, was also found to resolve to this same IP address and the use of this domain continues with the theme of emulating telecommunication providers in Ukraine. The aforementioned use of the similar domain kievstar[.]online is of note as the spelling is not typically employed in Ukraine but has been employed previously by the international community, as well as historically during Soviet times, and has now been carried into Russian domestic colloquial use.
Domain to IP Address Resolutions Timeline
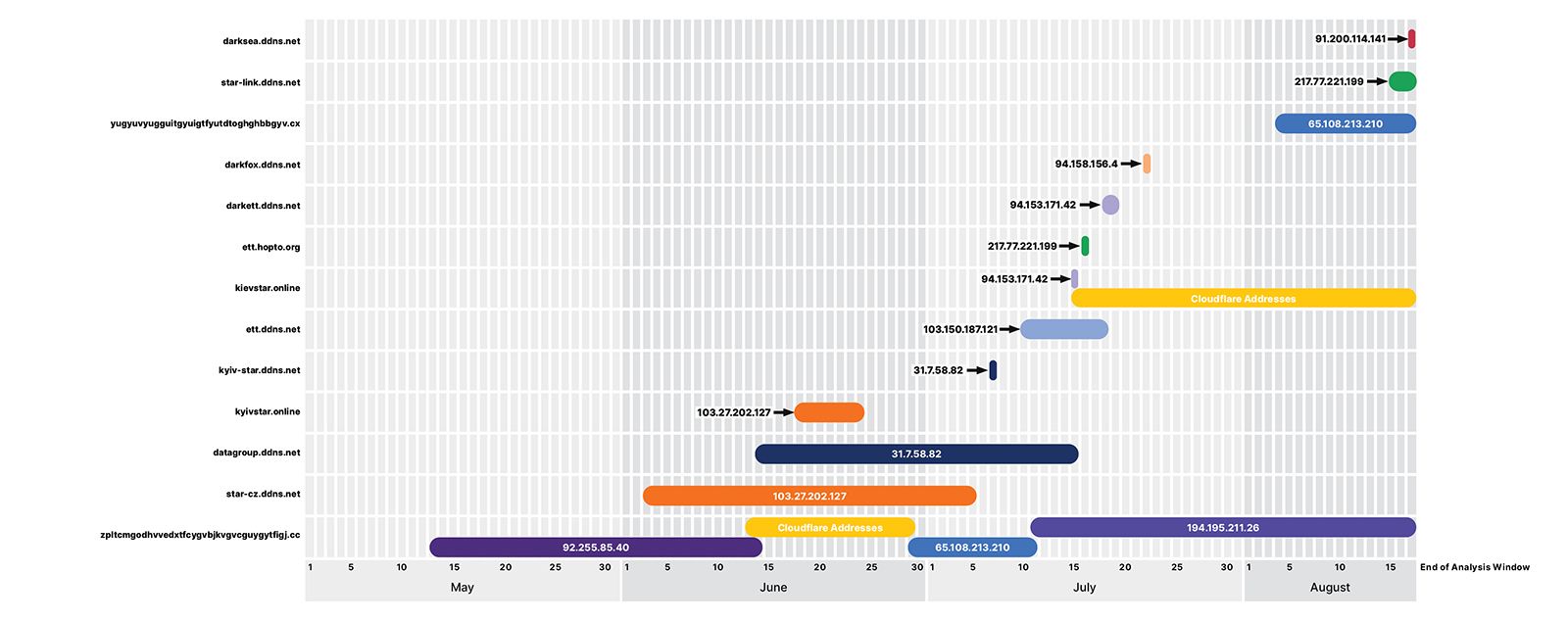 Figure 8: A timeline of UAC-0113 domain activity between May and August, 2022 (Source: Recorded Future)
Figure 8: A timeline of UAC-0113 domain activity between May and August, 2022 (Source: Recorded Future)
HTML Analysis
The domains ett[.]ddns[.]net, star-link[.]ddns[.]net, kievstar[.]online, and IP addresses 103[.]150[.]187[.]121 and 217[.]77[.]221[.]199 have all hosted, at various times, the same web page. The web page features the Ukrainian-language text “ОДЕСЬКА ОБЛАСНА ВІЙСЬКОВА АДМІНІСТРАЦІЯ” which translates as “Odesa Regional Military Administration”, along with “File is downloaded automatically” in English as shown in Figure 9 below.
 Figure 9: Screenshot of 103[.]150[.]187[.]121 (Source: URLScan)
Figure 9: Screenshot of 103[.]150[.]187[.]121 (Source: URLScan)
Contained within the HTML of the webpage is a Base64-encoded ISO file that is deployed via the HTML smuggling technique. This ISO file is set to auto-download when the website is visited. Figure 10 below shows the HTML content of the file.
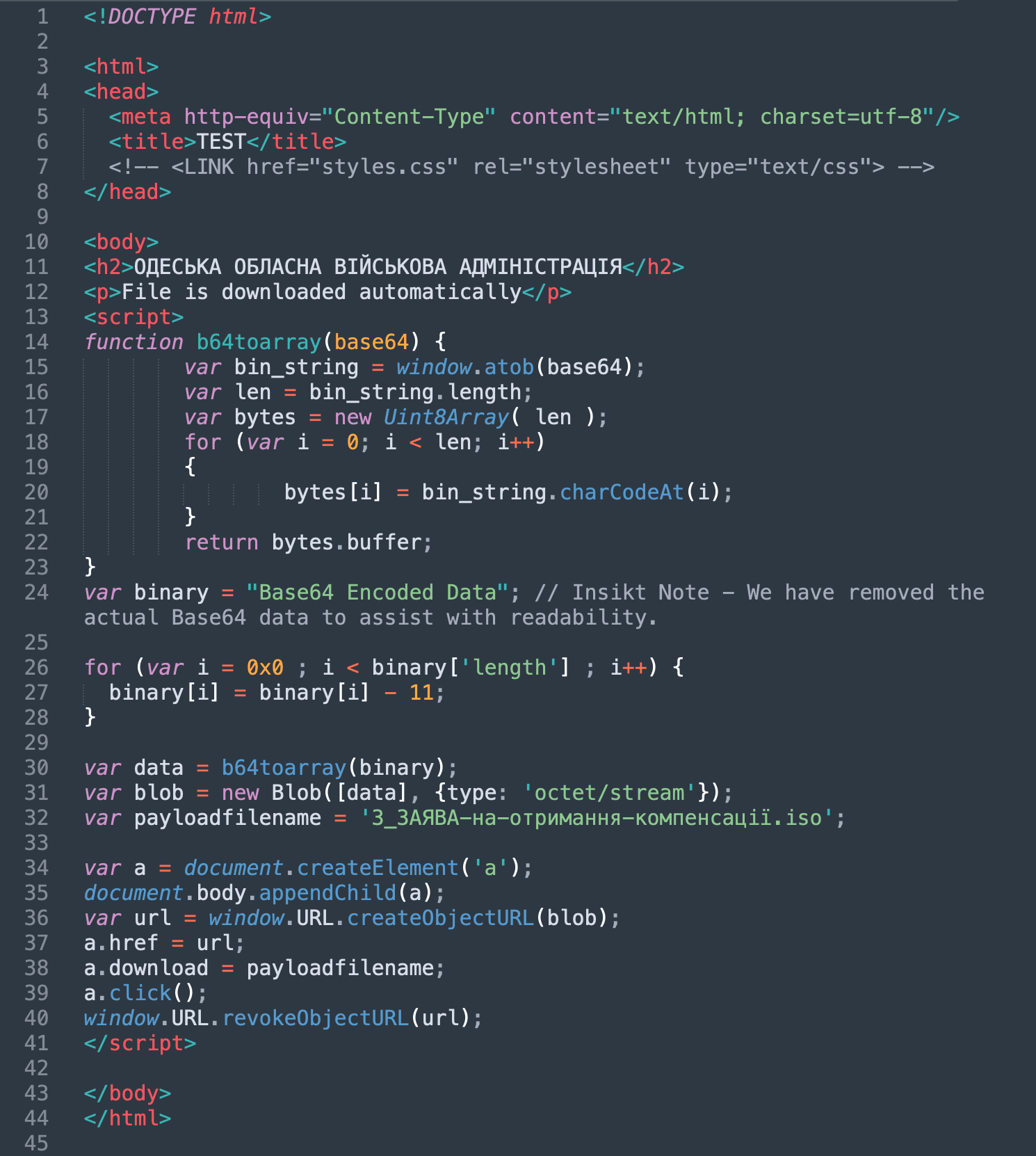 Figure 10: The HTML content for the IP address 103[.]150[.]187[.]121 (with Base64-encoded data removed), August 8, 2022 (Source: URLScan)
Figure 10: The HTML content for the IP address 103[.]150[.]187[.]121 (with Base64-encoded data removed), August 8, 2022 (Source: URLScan)
Insikt Group inspected the web page’s HTML, and identified embedded JavaScript, which assists in the malicious ISO delivery behavior of the page. Testing the functionality of the for loop on lines 26 to 28 does not change the Base64-encoded data held in the variable “binary”. The for loop attempts to take away the integer value 11 from the characters that make up the Base64 string. JavaScript will produce an error when attempting to subtract an integer from a char, resulting in its value not being updated. The Base64 contents of the variable “binary” will be exactly the same after going through the for loop, making it redundant, and the Base64 data will still correctly decode to an ISO file.
The purpose of the inclusion of this routine by UAC-0113 could be due to operator error, as its functionality serves no purpose because strings are immutable objects in JavaScript.
Of note, a report by Palo Alto’s Unit42 details a similar HTML Smuggling routine used by APT29 in a separate campaign to download an ISO file, shown below in Figure 11. APT29’s original use of this routine was for a binary array, which helps to potentially illuminate UAC-0113’s redundant for loop's original purpose. APT29’s HTML and JavaScript code has similar overlaps with the UAC-0113 linked sample shown in Figure 10 above.
Editor’s Note: This post is an excerpt of a full report. To read the entire analysis, click here to download the report as a PDF.
Related
