Chinese State-Sponsored Group ‘RedDelta’ Targets the Vatican and Catholic Organizations

Editor’s Note: The following post is an excerpt of a full report. To read the entire analysis, click here to download the report as a PDF.
Insikt Group® researchers used proprietary Recorded Future Network Traffic Analysis and RAT controller detections, along with common analytical techniques, to identify and profile a cyberespionage campaign attributed to a suspected Chinese state-sponsored threat activity group, which we are tracking as RedDelta.
Data sources include the Recorded Future® Platform, Farsight Security’s DNSDB, SecurityTrails, VirusTotal, Shodan, BinaryEdge, and common OSINT techniques.
This report will be of greatest interest to network defenders of private sector, public sector, and non-governmental organizations with a presence in Asia, as well as those interested in Chinese geopolitics.
Executive Summary
From early May 2020, The Vatican and the Catholic Diocese of Hong Kong were among several Catholic Church-related organizations that were targeted by RedDelta, a Chinese-state sponsored threat activity group tracked by Insikt Group. This series of suspected network intrusions also targeted the Hong Kong Study Mission to China and the Pontifical Institute for Foreign Missions (PIME), Italy. These organizations have not been publicly reported as targets of Chinese threat activity groups prior to this campaign.
These network intrusions occured ahead of the anticipated September 2020 renewal of the landmark 2018 China-Vatican provisional agreement, a deal which reportedly resulted in the Chinese Communist Party (CCP) gaining more control and oversight over the country’s historically persecuted “underground” Catholic community. In addition to the Holy See itself, another likely target of the campaign includes the current head of the Hong Kong Study Mission to China, whose predecessor was considered to have played a vital role in the 2018 agreement.
The suspected intrusion into the Vatican would offer RedDelta insight into the negotiating position of the Holy See ahead of the deal’s September 2020 renewal. The targeting of the Hong Kong Study Mission and its Catholic Diocese could also provide a valuable intelligence source for both monitoring the diocese’s relations with the Vatican and its position on Hong Kong’s pro-democracy movement amidst widespread protests and the recent sweeping Hong Kong national security law.
While there is considerable overlap between the observed TTPs of RedDelta and the threat activity group publicly referred to as Mustang Panda (also known as BRONZE PRESIDENT and HoneyMyte), there are a few notable distinctions which lead us to designate this activity as RedDelta:
- The version of PlugX used by RedDelta in this campaign uses a different C2 traffic encryption method and has a different configuration encryption mechanism than traditional PlugX.
- The malware infection chain employed in this campaign has not been publicly reported as used by Mustang Panda.
In addition to the targeting of entities related to the Catholic Church, Insikt Group also identified RedDelta targeting law enforcement and government entities in India and a government organization in Indonesia.
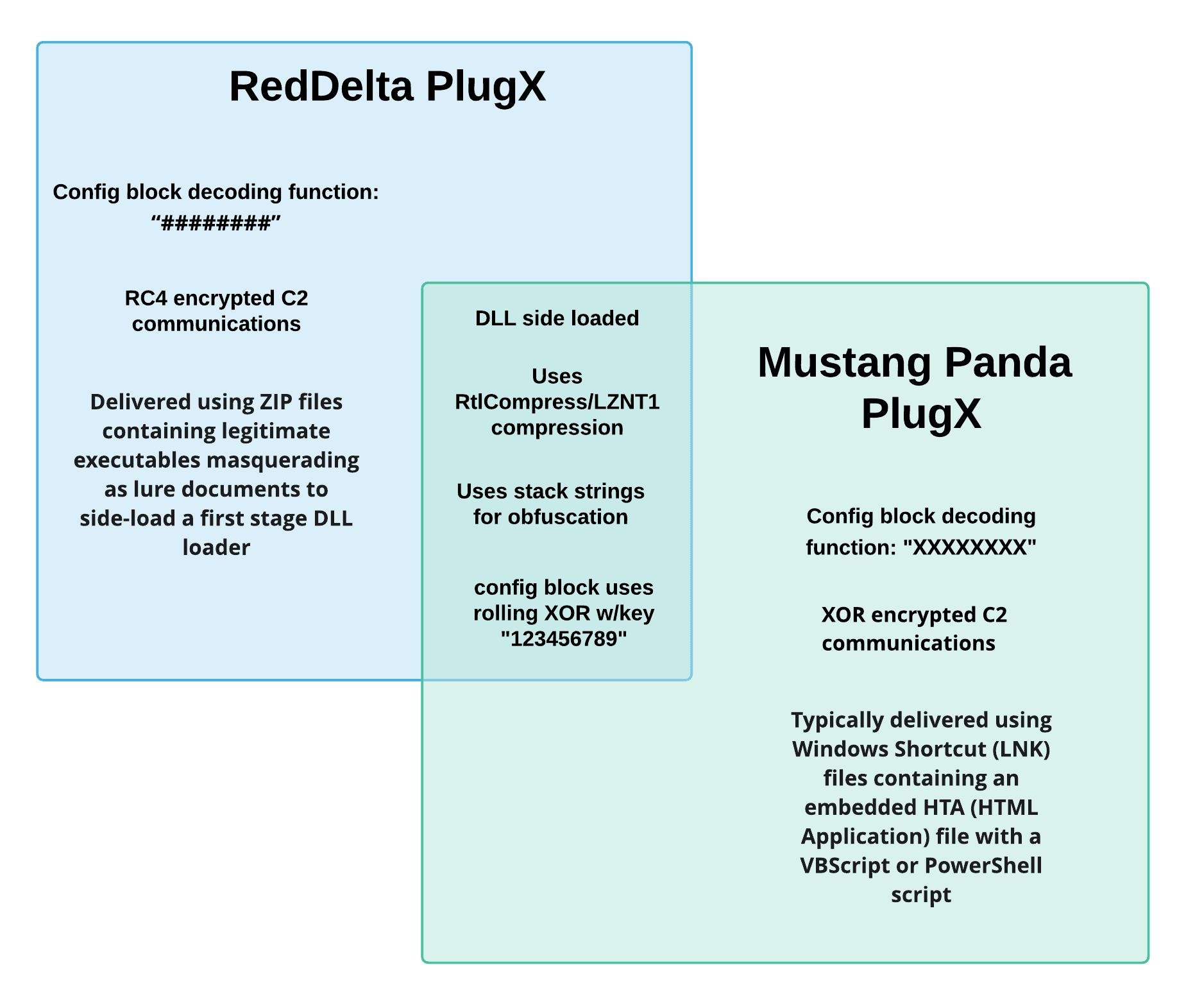
Figure 1: Selection of main differences between PlugX variants and the infection chain used by RedDelta and Mustang Panda.
Key Judgments
- The targeting of entities related to the Catholic church is likely indicative of CCP objectives in consolidating control over the “underground” Catholic church, “sinicizing religions” in China, and diminishing the perceived influence of the Vatican within China’s Catholic community.
- Due to RedDelta’s targeting of organizations that heavily align to Chinese strategic interests, use of shared tooling traditionally used by China-based groups, and overlaps with a suspected Chinese state-sponsored threat activity group, Insikt Group believes that the group likely operates on behalf of the People’s Republic of China (PRC) government.
- The identified RedDelta intrusions feature infrastructure, tooling, and victimology overlap with the threat activity group publicly reported as Mustang Panda (also known as BRONZE PRESIDENT and HoneyMyte). This includes the use of overlapping network infrastructure and similar victimology previously attributed to this group in public reporting, as well as using malware typically used by Mustang Panda, such as PlugX, Poison Ivy, and Cobalt Strike.
Background
China and the Catholic Church
For many years, Chinese state-sponsored groups have targeted religious minorities within the the PRC, particularly those within the so-called “Five Poisons,” such as Tibetan, Falun Gong, and Uighur muslim communities. Insikt Group has publicly reported on aspects of this activity, such as our findings on RedAlpha, the ext4 backdoor, and Scanbox watering hole campaigns targeting the Central Tibetan Administration, other Tibetan entities, and the Turkistan Islamic Party. Most recently, a July 2020 U.S. indictment identified the targeting of emails belonging to Chinese Christian religious figures — a Xi’an-based pastor, as well as an underground church pastor in Chengdu, the latter of whom was later arrested by the PRC government, by two contractors allegedly operating on behalf of the Chinese Ministry of State Security (MSS). Regional branches of China’s Ministry of Public Security (MPS) have also been heavily involved in digital surveillance of ethnic and religious minorities within the PRC, most notably by the Xinjiang Public Security Bureau (XPSB) in the case of Uighur muslims.
Historically, the PRC has had a highly turbulent relationship with the Vatican and its governing body, the Holy See. In particular, the Holy See’s recognition of bishops within China’s historically persecuted “underground” Catholic church traditionally loyal to the Vatican and its relationship with Taiwan has maintained an absence of official relations since the 1950s. The CCP perceived this behavior as the Holy See interfering in religious matters within China. In September 2018, the PRC and the Holy See reached a landmark two-year provisional agreement, marking a significant step towards renewed diplomatic relations.
Under the provisional agreement, China would regain more control over underground churches, and the Vatican in turn would gain increased influence over the appointment of bishops within the state-backed “official” Catholic church. The deal was met with a mixed reaction, with critics arguing that the deal was a betrayal of the underground church and would lead to increased persecution of its members. Many of the harshest criticisms came from clergy within Hong Kong. A year after the agreement, numerous reports noted the Vatican’s silence in response to the Hong Kong protests beginning in late 2019, in what critics called an effort to avoid offending Beijing and jeopardizing the 2018 agreement.
Threat Analysis
Overview of Catholic Church Intrusions
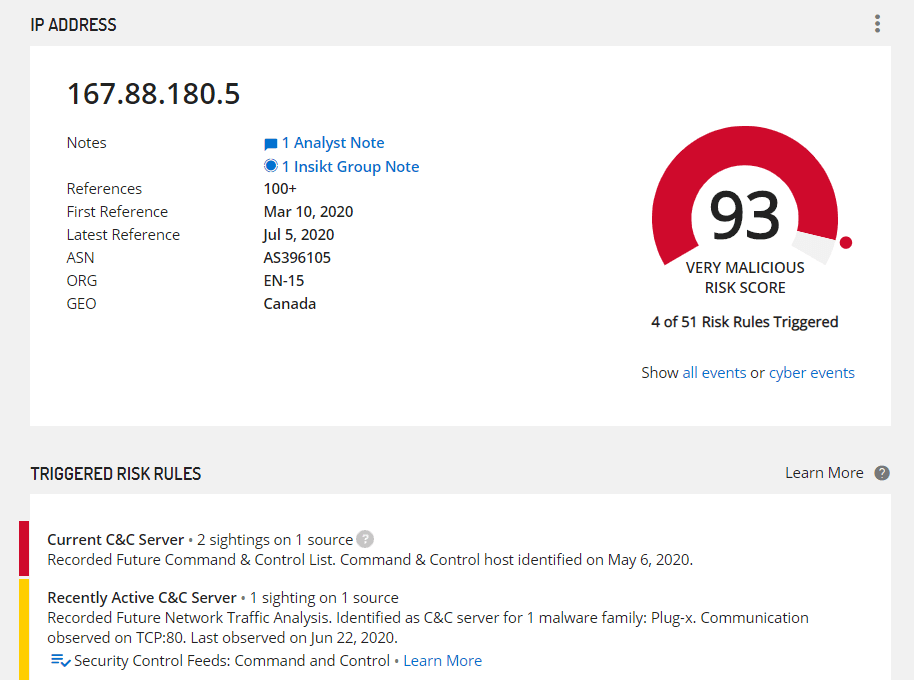
Figure 2: Intelligence Card for RedDelta PlugX C2 Server 167.88.180[.]5.
Using Recorded Future RAT controller detections and network traffic analysis techniques, Insikt Group identified multiple PlugX C2 servers communicating with Vatican hosts from mid-May until at least July 21, 2020. Concurrently, we identified Poison Ivy and Cobalt Strike Beacon C2 infrastructure also communicating with Vatican hosts, a Vatican-themed phishing lure delivering PlugX, and the targeting of other entities associated with the Catholic Church.

Figure 3: Vatican lure document targeting the head of Hong Kong study mission to China.
The lure document in Figure 3, which has been previously reported on in relation to links to Hong Kong Catholic Church targeting, was used to deliver a customized PlugX payload that communicated with the C2 domain systeminfor[.]com. The document purported to be an official Vatican letter addressed to the current head of the Hong Kong Study Mission to China. It is currently unclear whether the actors created the document themselves, or whether it is a legitimate document they were able to obtain and weaponize. Given that the letter was directly addressed to this individual, it is likely that he was the target of a spearphishing attempt. Additionally, as this sample was compiled after signs of an intrusion within the Vatican network, it is also possible that the phishing lure was sent through a compromised Vatican account. This hypothesis is supported by the identification of communications between PlugX C2s and a Vatican mail server in the days surrounding the sample’s compilation date and its first submission to public malware repositories.
The head of the Hong Kong Study Mission is considered the Pope’s de facto representative to China and a key link between Beijing and the Vatican. The predecessor to this role played a key part in the finalization of the 2018 provisional China-Vatican agreement, making his successor a valuable target for intelligence gathering ahead of the deal’s expiry and likely renewal in September 2020.
Further entities associated with the Catholic Church were also targeted by RedDelta in June and July 2020 using PlugX, including the mail servers of an international missionary center based in Italy and the Catholic Diocese of Hong Kong.

Figure 4: Union of Catholic Asian News article lure document (left), and Qum, the Vatican of Islam lure document (right).
Insikt Group identified two additional phishing lures loading the same customized PlugX variant, which both communicated with the same C2 infrastructure as the Vatican lure. The first sample included a lure document spoofing a news bulletin from the Union of Catholic Asian News regarding the impending introduction of the new Hong Kong national security law. The content of the lure file, titled “About China’s plan for Hong Kong security law.doc,” was taken from a legitimate Union of Catholic Asian News article. The other sample also references the Vatican using a document titled “QUM, IL VATICANO DELL’ISLAM.doc” for the decoy document. This particular decoy document translates as “Qum, the Vatican of Islam,” referring to the Iranian city of Qum (Qom), an important Shi’ite political and religious center. It is taken from the writings of Franco Ometto, a Italian Catholic academic living in Iran. Although the direct target of these two lures are unclear, both relate to the Catholic church.
We believe that this targeting is indicative of both China’s objective in consolidating increased control over the underground Catholic Church within China, and diminishing the perceived influence of the Vatican on Chinese Catholics. Similarly, a focus on Hong Kong Catholics amid pro-democracy protests and the recent sweeping national security law is in line with Chinese strategic interests, particularly given the Anti-Beijing stance of many of its members, including former Hong Kong Bishop Cardinal Joseph Zen Ze-kiun.
Outlook
Our research uncovered a suspected China state-sponsored campaign targeting multiple high-profile entities associated with the Catholic Church ahead of the likely renewal of the provisional China-Vatican deal in September 2020. The CCP’s warming diplomatic relations with the Holy See has been commonly interpreted as a means to facilitate increased oversight and control over its unofficial Catholic church. This also supports the CCP’s wider stated goal of “sinicizing religions” in China. Furthermore, it demonstrates that China’s interest in control and surveillance of religious minorities is not confined to those within the “Five Poisons,” exemplified by the continued persecution and detainment of underground church members and allegations of physical surveillance of official Catholic and Protestant churches.
The U.S. Ambassador-at-Large for International Religious Freedom recently expressed concern regarding the impact of the new national security law within Hong Kong, stating it has the “potential to significantly undermine religious freedom.” The targeting of the Catholic diocese of Hong Kong is likely a valuable intelligence source for both monitoring the diocese’s position on Hong Kong’s pro-democracy movement and its relations with the Vatican. This marks a possible precursor to increased limits on religious freedom within the special administrative region, particularly where it coincides with pro-democracy or anti-Beijing positions.
RedDelta is a highly active threat activity group targeting entities relevant to Chinese strategic interests. Despite the group’s consistent use of well-known tools such as PlugX and Cobalt Strike, infrastructure reuse, and operations security failures, these intrusions indicate RedDelta is still being tasked to satisfy intelligence requirements. In particular, this campaign demonstrates a clear objective to target religious bodies, and therefore we feel this is particularly pertinent for religious and non-governmental organizations (NGOs) to take note and invest in network defenses to counter the threat posed by Chinese state-sponsored threat activity groups like RedDelta. A lack of ability to invest in security and detection measures for many NGOs and religious organizations greatly increases the likelihood of success for well-resourced and persistent groups, even using well-documented tools, TTPs, and infrastructure.
Network Defense Recommendations
Recorded Future recommends that users conduct the following measures to detect and mitigate activity associated with RedDelta activity:
- Configure your intrusion detection systems (IDS), intrusion prevention systems (IPS), or any network defense mechanisms in place to alert on — and upon review, consider blocking illicit connection attempts from — the external IP addresses and domains listed in the appendix.
Additionally, we advise organizations to follow the following general information security best practice guidelines:
- Keep all software and applications up to date; in particular, operating systems, antivirus software, and core system utilities.
- Filter email correspondence and scrutinize attachments for malware.
- Make regular backups of your system and store the backups offline, preferably offsite so that data cannot be accessed via the network.
- Have a well-thought-out incident response and communications plan.
- Adhere to strict compartmentalization of company-sensitive data. In particular, look at which data anyone with access to an employee account or device would have access to (for example, through device or account takeover via phishing).
- Strongly consider instituting role-based access, limiting company-wide data access, and restricting access to sensitive data.
- Employ host-based controls; one of the best defenses and warning signals to thwart attacks is to conduct client-based host logging and intrusion detection capabilities.
- Implement basic incident response and detection deployments and controls like network IDS, netflow collection, host logging, and web proxy, alongside human monitoring of detection sources.
- Be aware of partner or supply chain security standards. Being able to monitor and enforce security standards for ecosystem partners is an important part of any organization’s security posture.
Editor’s Note: This post was an excerpt of a full report. To read the entire analysis, click here to download the report as a PDF.
Related
