Partner Spotlight: Get Verified Phishing Analysis With PhishMe Intelligence
Revealing Dyre Past and TrickBot with PhishMe Intelligence and Recorded Future.
Editor's Note
This is part of a series of blog posts on useful “all-source analysis” research and collaborative approaches using Recorded Future and our OMNI Intelligence Partners.
Summary
Phishing is often the primary vector of compromise for attacks involving ransomware, business email compromise (BEC), malware infections, and credential-based theft.
To counter these threats, analysts can combine Recorded Future’s automated open, deep, and dark web collection and analysis with human-verified PhishMe Intelligence® to proactively research and defend against phishing.
Challenge
Information without context is just data. Intelligence (information with context) is what security teams require to have confidence in their decisions.
Attackers expect multiple layers of defense and prepare their tactics to circumvent whatever obstacles are placed in their way. This is where actionable intelligence is needed. Security analysts struggle to determine which indicators matter most for protecting the business while ensuring the actions taken will not negatively impact business operations.
Solution
When intelligence is human-verified, it can be trusted and operationalized.
PhishMe Intelligence is 100% human-verified machine-readable threat intelligence (MRTI) and subscribers receive a fully vetted source of intelligence. PhishMe also provides security teams with context around the criminal infrastructure to extend beyond expected indicators of compromise (IOCs), and enables teams to see their adversary’s full operation as opposed to one-offs that change rapidly.
Recorded Future empowers analysts to capture and exploit relevant threat intelligence from the entire web, in real time. For many, phishing is where it matters most. Combining Recorded Future and PhishMe Intelligence rapidly uncovers the greatest phishing threats. Also, PhishMe Intelligence doesn’t just tell an analyst what is bad; more importantly, it also clearly highlights why, along with all associated artifacts in the Active Threat Reports.
What is included in Active Threat Reports? PhishMe Intelligence provides human-readable reports describing the malware along with verbose explanations describing the threat actor’s tactics. This is the intelligence report that backs up and supports the MRTI ingestion full of C2, hash, IP, and domain indicators, just to name a few. What this means is that analysts receive and can substantiate the indicators since it has been human-verified.
An analyst in Recorded Future can quickly search for and pull back a plethora of information and easily pivot with one-click access into PhishMe to further investigate phishing campaigns.
| Intelligence Card™ | Extension |
|---|---|
| IP Address | Available |
| Domain | Available |
| Hash | Available |
Take for example, TrickBot, a Dyre-mimicking malware delivered by what else? Phishing!
PhishMe researchers discovered Dyre in 2014 and its prolific banking Trojan characteristics and SSL bypass tactics. At the time of discovery, attackers were leveraging legitimate links in Dropbox delivered by a phishing email with an embedded screensaver within a zip file.
Similar to Dyre, TrickBot does not deliver treats! PhishMe has witnessed the botnet Trojan flaunting Dyre-like characteristics through phishing. “Known as the TrickBot malware due to its distinctive user agent string, this malware provides many of the botnet and financial crimes functionality that made the Dyre malware such a success,” says Brendan Griffin, Threat Intelligence Manager at PhishMe. Below are a couple of notable image examples from TrickBot (extracted from PhishMe).

 Examples from TrickBot extracted via PhishMe.
Examples from TrickBot extracted via PhishMe.
Security analysts reading about TrickBot and its similarities will naturally want to know more. Once logged into Recorded Future and armed with no information other than the malware name (TrickBot), what insight can security teams gather in tandem with PhishMe Intelligence?
Simply enter the search term, TrickBot, and away you go!
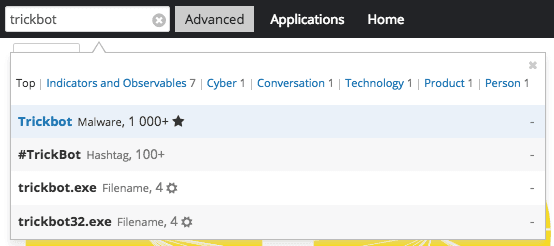 Recorded Future makes it easy to search for malware and other IOCs.
Recorded Future makes it easy to search for malware and other IOCs.
The header from Recorded Future’s Malware Card for TrickBot correlates with PhishMe’s assessment — it's a Dyre-like banking Trojan malware dating back to mid-2014.
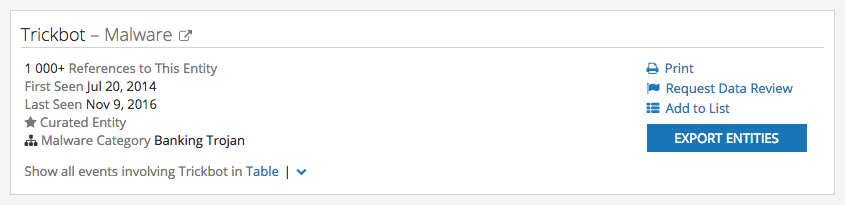 A section of the Recorded Future Intelligence Card™ for TrickBot malware.
A section of the Recorded Future Intelligence Card™ for TrickBot malware.
Scrolling through the rest of Recorded Future’s Intelligence Card™ on TrickBot, analysts can easily see all of the rich context amassed to gain additional insight quickly, or they can cut-to-the-chase to investigate IOCs, such as IP addresses, immediately.
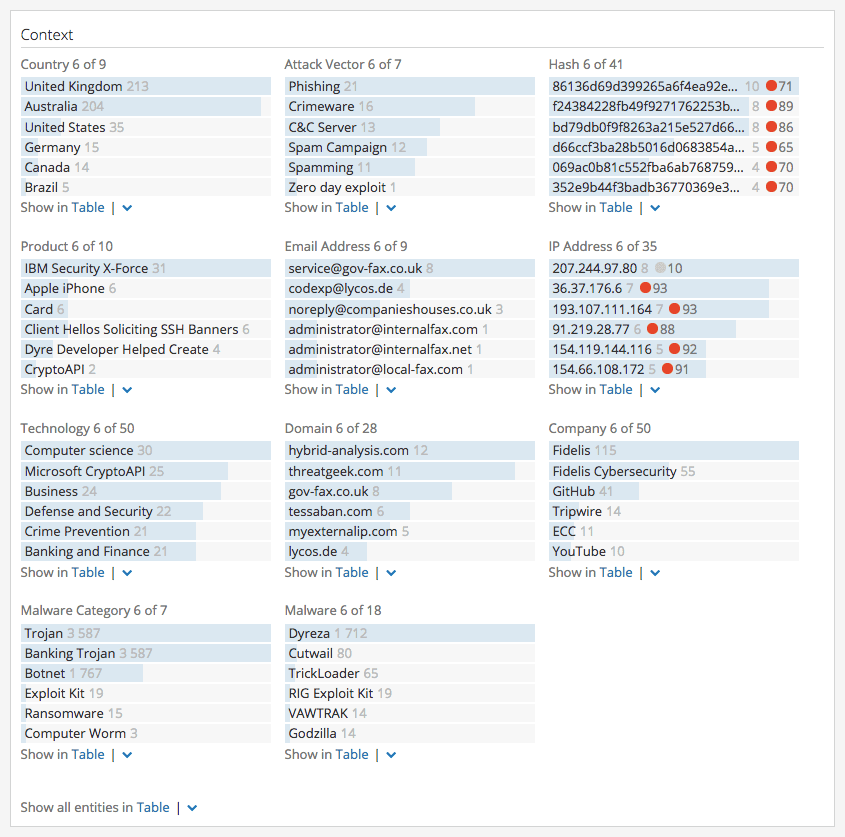 Investigate IOCs quickly with the Context section of the Intelligence Card™.
Investigate IOCs quickly with the Context section of the Intelligence Card™.
Recorded Future makes it easy to prioritize IOCs with the risk score stop light designations. For example, let’s drill down on IP 91[.]219[.]28[.]77, which has the highest risk score listed:
 Intelligence Card™ for IP address 91[.]219[.]28[.]77.
Intelligence Card™ for IP address 91[.]219[.]28[.]77.
Mutual Recorded Future and PhishMe customers who've enabled the PhishMe extension through the OMNI Intelligence Partners Program can use a one-click lookup to pivot to human-verified intelligence from PhishMe (as shown below).
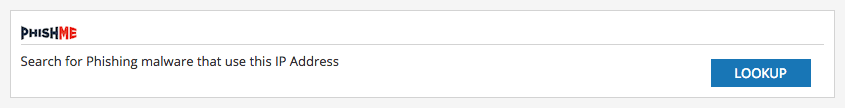
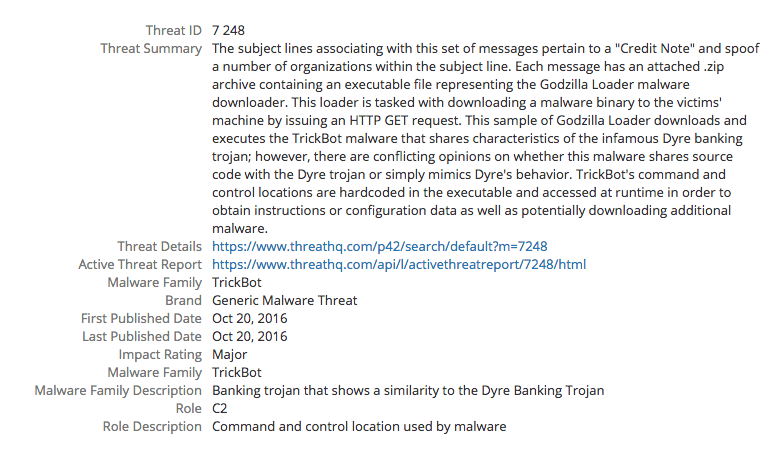 Human-verified intelligence on TrickBot from PhishMe Intelligence inside the Recorded Future product.
Human-verified intelligence on TrickBot from PhishMe Intelligence inside the Recorded Future product.
Looking up the malicious IP address, PhishMe upholds the research. Right away analysts are presented with the substantiated intelligence shown above.
In addition to providing IOCs for ingestion by SIEMs and threat intelligence platforms (TIPs), PhishMe delivers human-readable reports for analysts to continue their research.
Subjects Associated With TrickBot
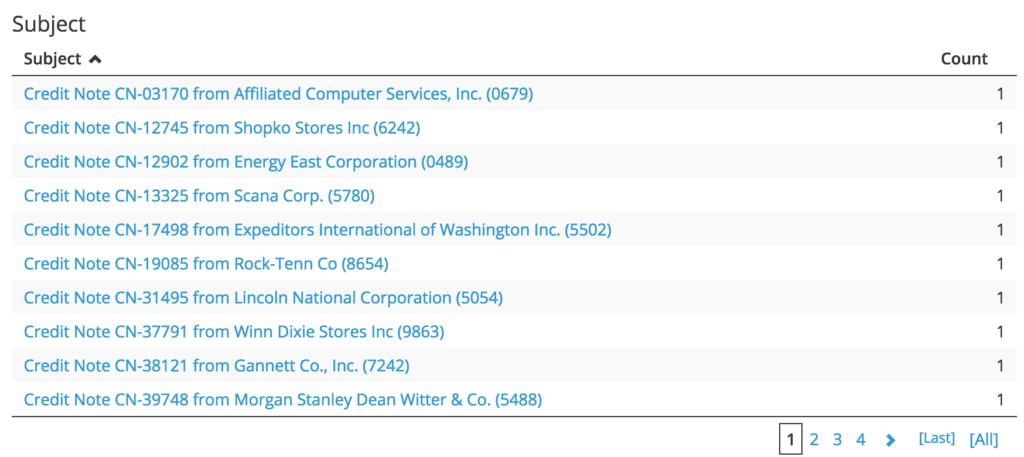
Sender Domains

Sender IP(s)

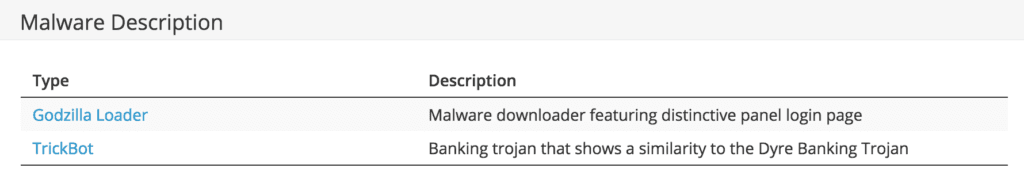
Malware Description
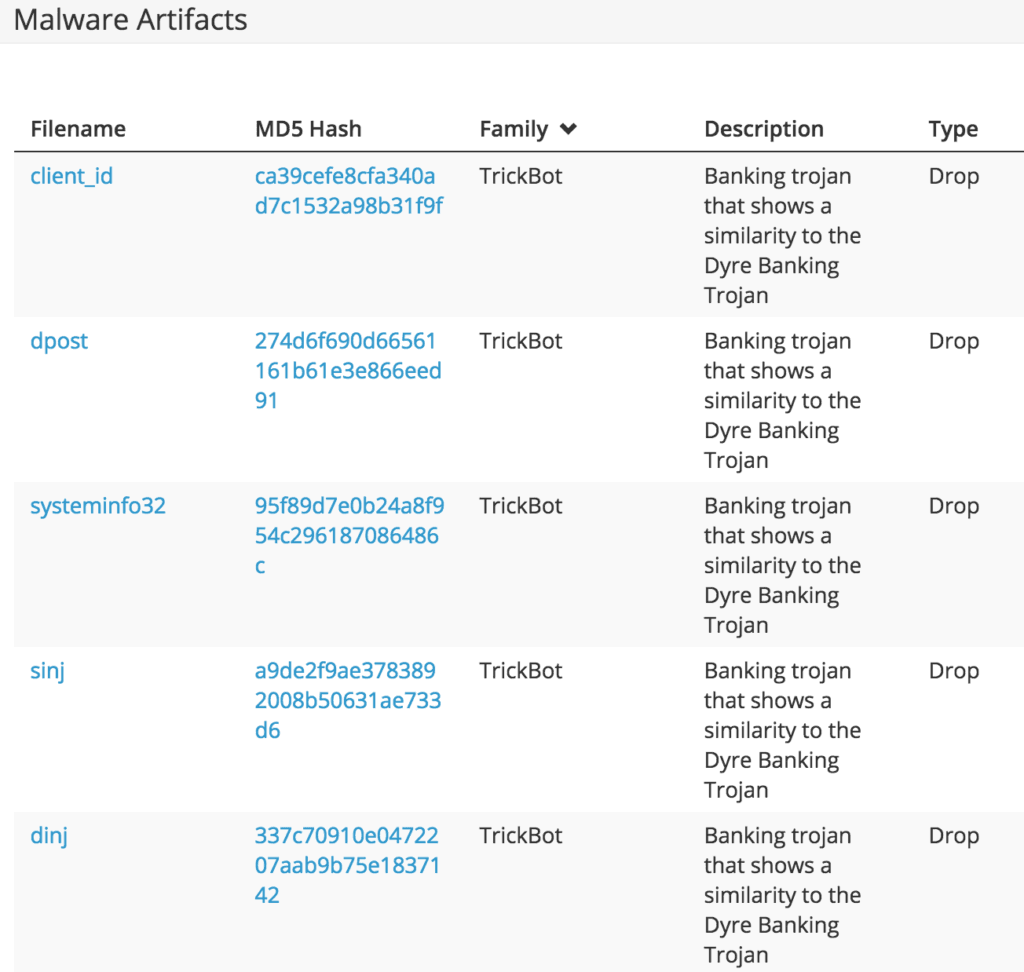
Malware Artifacts (Filename, Hash, Malware Family)
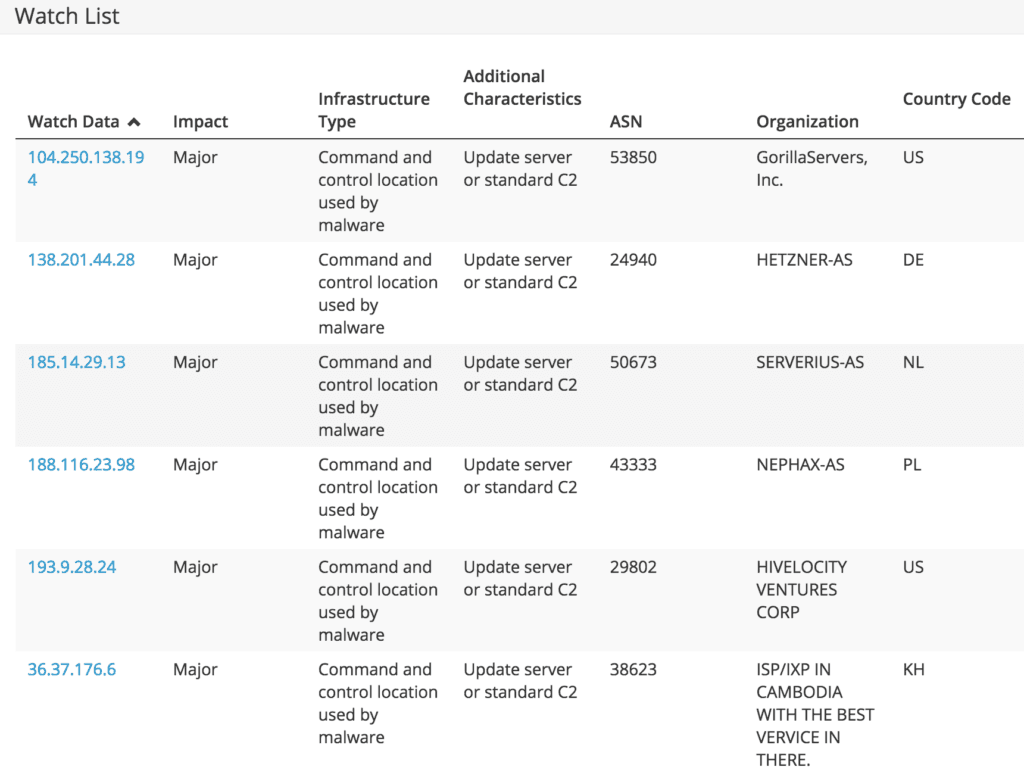
Watch List (Including Crucial Impact Ratings)
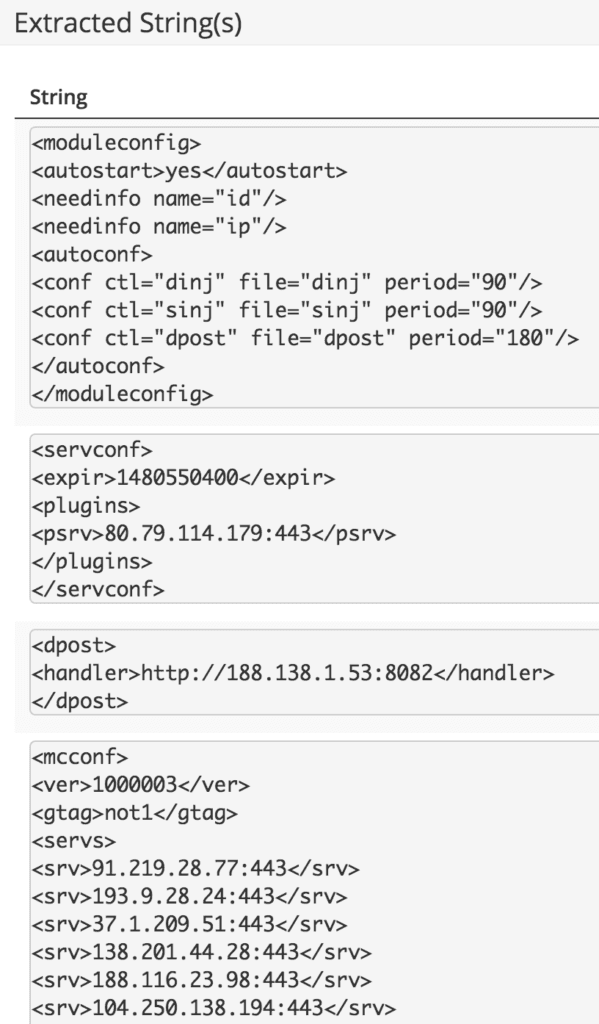
Extracted Malware Strings
Closing
The above intelligence can be operationalized and prioritized easily as analysts pivot between trusted sources. Analysts thus gain fast, flexible investigation capability from the combination of technology partnerships and APIs, machine-readable data, and rich contextual reports that provide organizations the intelligence needed to defend the business and understand their threats.
The integration between PhishMe Intelligence and Recorded Future is a great example of how businesses can maximize the value from their existing investments and pivot from one source of intelligence into another and back again.
Demo
Want to learn more about using PhishMe with Recorded Future? Request a free demo. You can also contact the PhishMe sales team directly by clicking here.
PhishMe
PhishMe is the leading provider of threat management for organizations concerned about human susceptibility to advanced targeted attacks. PhishMe’s intelligence-driven platform turns employees into an active line of defense by enabling them to identify, report, and mitigate spear phishing, malware, and drive-by threats.
Related
