Vendors Rush to Patch Meltdown and Spectre Vulnerabilities
Key Judgements
- Because Meltdown and Spectre impact Intel, AMD, and ARM processors, all types of of systems from desktop, to server, to cloud, to IoT and mobile devices are impacted.
- Windows, Linux, and OS X (prior to High Sierra 10.13.2) are all impacted by these vulnerabilities.
- The vulnerabilities do not appear to allow remote access; instead, they are information disclosure vulnerabilities that could allow an attacker to gain information about the target system.
- Exploiting the vulnerability can be done remotely using client-side JavaScript or other typical web-based attack methods.
- Several security researchers have released POC exploit code for these vulnerabilities.
Executive Summary
Two vulnerabilities, potentially dating back to as far as 1995 and affecting almost all processors, have been disclosed by security researchers. The vulnerabilities, dubbed Meltdown and Spectre, are information disclosure vulnerabilities that allow an attacker to use a malicious program to potentially see any information any other program is storing in memory. There are three CVEs associated with these vulnerabilities: CVE-2017-5753 (Spectre Variant 1), CVE-2017-5715 (Spectre Variant 2), and CVE-2017-5754 (Meltdown). Vendors have started releasing patches for these vulnerabilities and security researchers have released POC exploit code.
Background
Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5715 and CVE-2017-5753) were discovered and reported using responsible disclosure methods in July 2017. Vendors had been working on patches and were scheduled to release them ahead of a January 9 embargo date, but security researchers discovered the changes in early releases of the patched operating systems and began speculating about the vulnerability, forcing the researchers to release information prior to the original embargo date.
Meltdown and Spectre are both hardware vulnerabilities. The researchers behind both vulnerabilities have created a web page that explains both attacks in detail and provides background on the research they did to find the attacks.
Meltdown is specific to Intel processors and takes advantage of speculative execution and indirect branch prediction that Intel has enabled in its chipset. Intel states that other chip manufacturers may be susceptible to this vulnerability as well, but the researchers who uncovered the flaw were not able to replicate it on other chipsets.
- Speculative execution and indirect branch prediction allow programs to run faster on a system by “speculatively” finding available memory to execute the next fork in the program. During this speculative action, processes are not adequately segmented from each other. In other words, anyone who can gain access to the kernel can use specific code to see all of the other processes.
- At this point, researchers don’t think anything can be changed or manipulated, but it is enough to be able to see everything that is stored in memory. Exploiting Meltdown could allow an attacker to see things like usernames and passwords, which might be encrypted on disk, but in plaintext while memory resident and extract that information.
Spectre was successfully tested by researchers on Intel, ARM, and AMD processors. While the result of an attack exploiting the Spectre vulnerability is fundamentally the same as Meltdown, the attack surface is slightly different.
- Rather than pulling information readily available in the kernel space, a Spectre attack involves tricking applications on the victim’s system into speculative execution that would not normally be performed, giving an attacker access to information that would not normally be exposed.
- According to the authors, this attack is more difficult to carry out, but it is also much harder to patch. Rather than issue a single patch, manufacturers may have to release multiple patches as new ways to exploit this line of attack are uncovered.
Threat Analysis
While the prevalence of vulnerable systems is extensive, the threat should not be blown out of proportion. Successfully exploiting this vulnerability would allow an attacker to read small arbitrary chunks of privileged kernel memory, bypassing Kernel Address Space Layout Randomization (KASLR), a key mitigation against kernel exploits in modern operating systems.
While consumers are urged to apply patches as soon as they become available, this vulnerability is unlikely to reach a critical threat level on consumer endpoints unless a public exploit becomes available that allows attackers to leverage arbitrary kernel memory reads in a useful manner becomes available.
Security implications may prove greater for cloud services where the segmentation of these services may be threatened by an ability to read privileged memory. Cloud service providers such as Google have taken a proactive stance to remedy the issue before disclosure. In addition, both Amazon and Microsoft have already delivered emergency patches to their AWS and Azure cloud services, respectively.
While there have been several potentially disturbing proof-of-concept exploit code examples released, to our knowledge, this has not been exploited in the wild. Reliably exploiting these vulnerabilities in the wild may prove challenging for all but the most advanced attackers. The next couple of weeks will help to determine whether the proof-of-concept code is deployed widely.
Mitigation
One major concern with attacks taking advantage of both of these vulnerabilities is that there is currently no way to detect these attacks using traditional security methods. Unlike many attacks, exploits of these vulnerabilities will not leave traces in log files or unusual files on the system for analysts to examine. An attacker could exploit these vulnerabilities without leaving a trace in traditional security tools.
The best way to mitigate against these attacks is to apply vendor patches as quickly as possible. Apple released a patch for High Sierra (10.13.2) in December that fixes these vulnerabilities, and Microsoft has issued an out-of-band security patch for Windows systems as well. The maintainers of the Linux kernel expect to have their patch ready for release Friday, January 5 — from there it should quickly make its way to various Linux distributions.
One note of caution, the new patch for Windows system reportedly can conflict with anti-virus systems and may result in a “Blue Screen of Death.” Microsoft has added a technical note explaining the issue, and security researcher Kevin Beaumont has released a spreadsheet that documents which anti-virus vendors are updated to support the new patch in Windows.
In addition to releasing a patch, Microsoft has released a PowerShell script that users can run to verify that their systems are properly patched and no longer vulnerable to Meltdown and Spectre.
Google has released a separate document providing mitigating steps for Google Chrome. Specifically, they recommend enabling Site Isolation as an added layer of protection. Firefox has published a report stating that they are working on a fix for this issue. Unfortunately, there appears to be exploit code showing that an attacker can use Meltdown to expose saved usernames and passwords in Firefox. Presumably, the same type of attack could be used again in Safari and Microsoft Edge.
Hello #Firefox, this is #Meltdown.
— Daniel Gruss (@lavados) January 4, 2018
And these are your passwords.
Figures from the #Meltdown paper - see https://t.co/RPiT6M8Xv2 and https://t.co/wtyTUEBLJq
/cc @misc0110 @mlqxyz @yuvalyarom @stefanmangard #kpti #kaiser #intelbug pic.twitter.com/XhxVmGlEwV
Exploit code was shared on Twitter showing how an attacker can use Meltdown to expose saved usernames and passwords.
Amazon has already patched their Amazon Web Service and Microsoft has deployed patches to their Azure service. Because cloud providers are particularly susceptible to Meltdown and Spectre, it is recommended that customers reach out to their cloud providers to understand what their mitigation plans and timetables are.
A list of vendors and their patch information has been appended to this report.
Using Recorded Future to Track Meltdown and Spectre
Recorded Future is tracking the latest developments for both Meltdown and Spectre, including monitoring closed sources to look for attackers who may try to weaponize these vulnerabilities, and new vulnerabilities that may arise because of the original research work.
Underground actors posting and discussing on these exploits already.
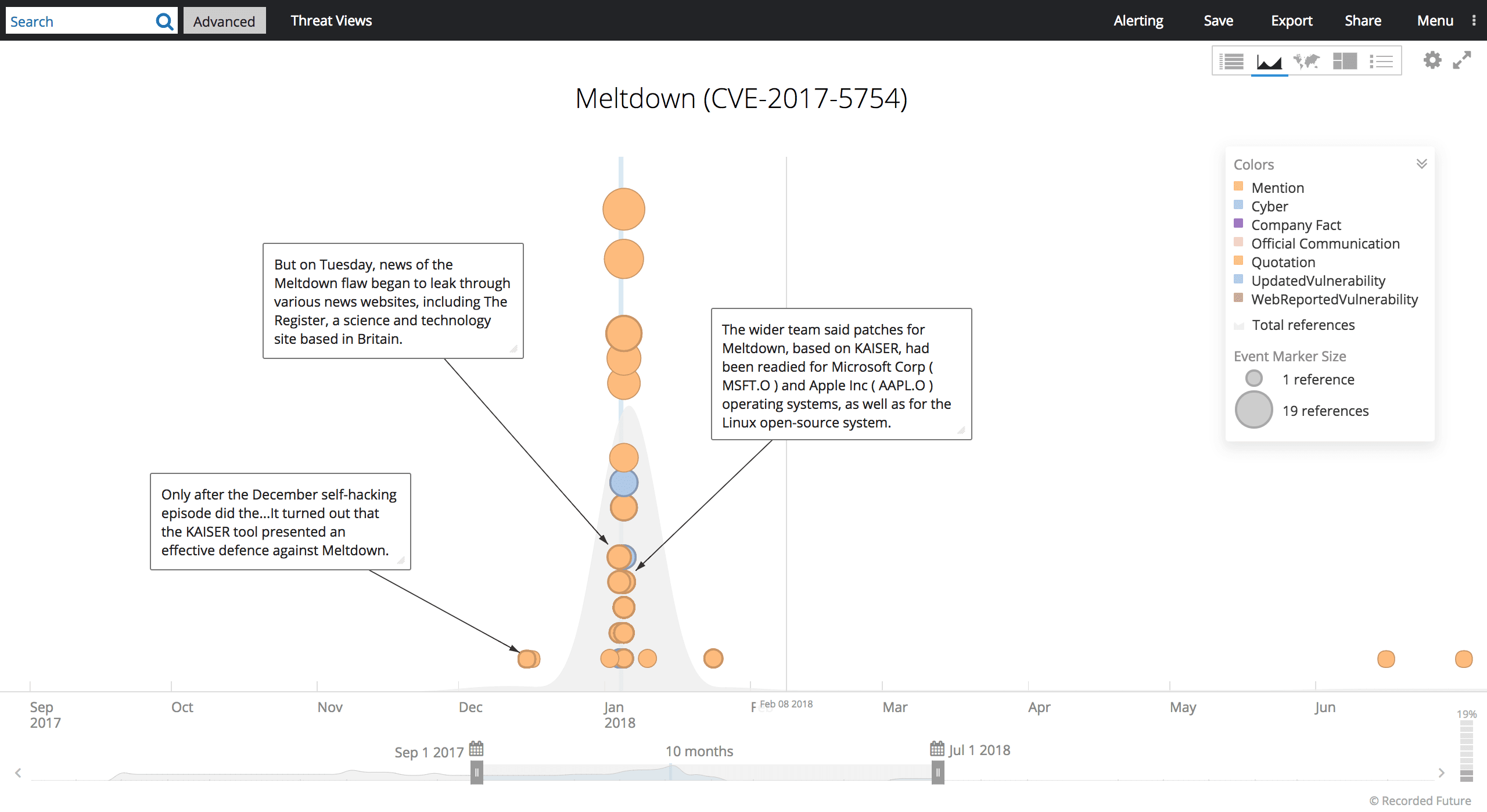
Timeline of Meltdown (CVE-2017-5754) reporting.
Our machine-learning algorithms automatically ingest and combine different threads of these attacks (such as correlating Meltdown with CVE-2017-5754 in the screenshot above) and make it easier for our customers to track new threats and keep updated with the latest information on existing threats.
Concluding Thoughts
These are big vulnerabilities, there is no doubt about that. They have already impacted thousands of organizations around the world and will continue to create a great deal of work as systems are patched and mitigations are put into place. The big question is: what is the risk to your organization? Right now, there doesn’t seem to be a big risk for most companies and organizations, but that might change over time.
Keep in mind that this is a new type of vulnerability, something we haven't seen before. There is a lot of speculation that threat actors can build upon this work to discover new and even more dangerous vulnerabilities. It could take months to determine if this is a blip or the start of a new class of threat that defenders have to address.
To get more information on patching and additional resources, download the appendix.
Related
